Lab link.
This lab has a “Check stock” feature that parses XML input but does not display the result.
You can detect the blind XXE vulnerability by triggering out-of-band interactions with an external domain.
To solve the lab, use an external entity to make the XML parser issue a DNS lookup and HTTP request to Burp Collaborator.
Blind XXE attacks can be found in two ways, the first way is by leaking sensitive data through out-of-band interactions. In this lab, we will provide a solution to this path.
Let’s examine the check stock request in the system.
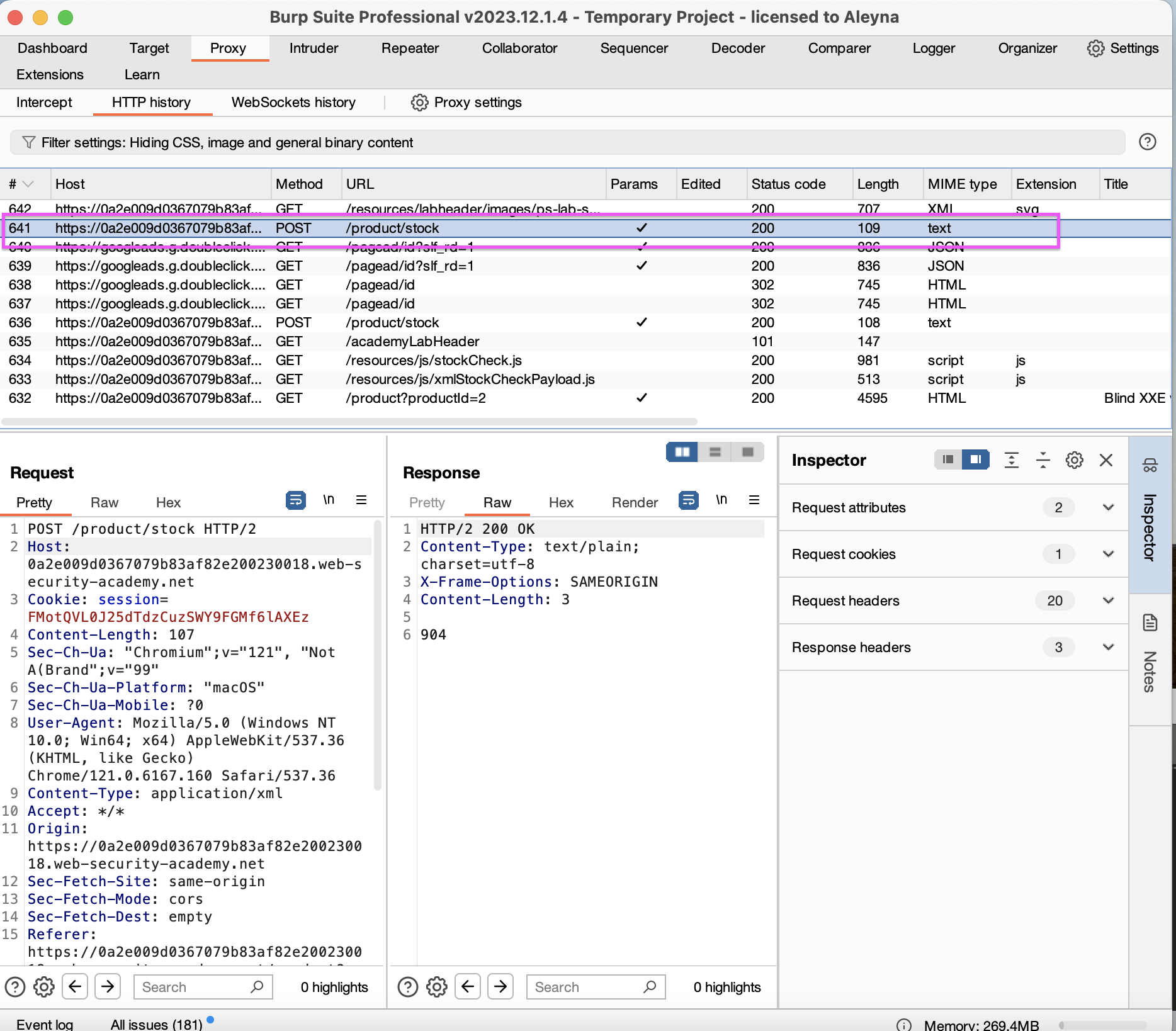
We are trying to define an object in the xml used in the request and we do not get an error.
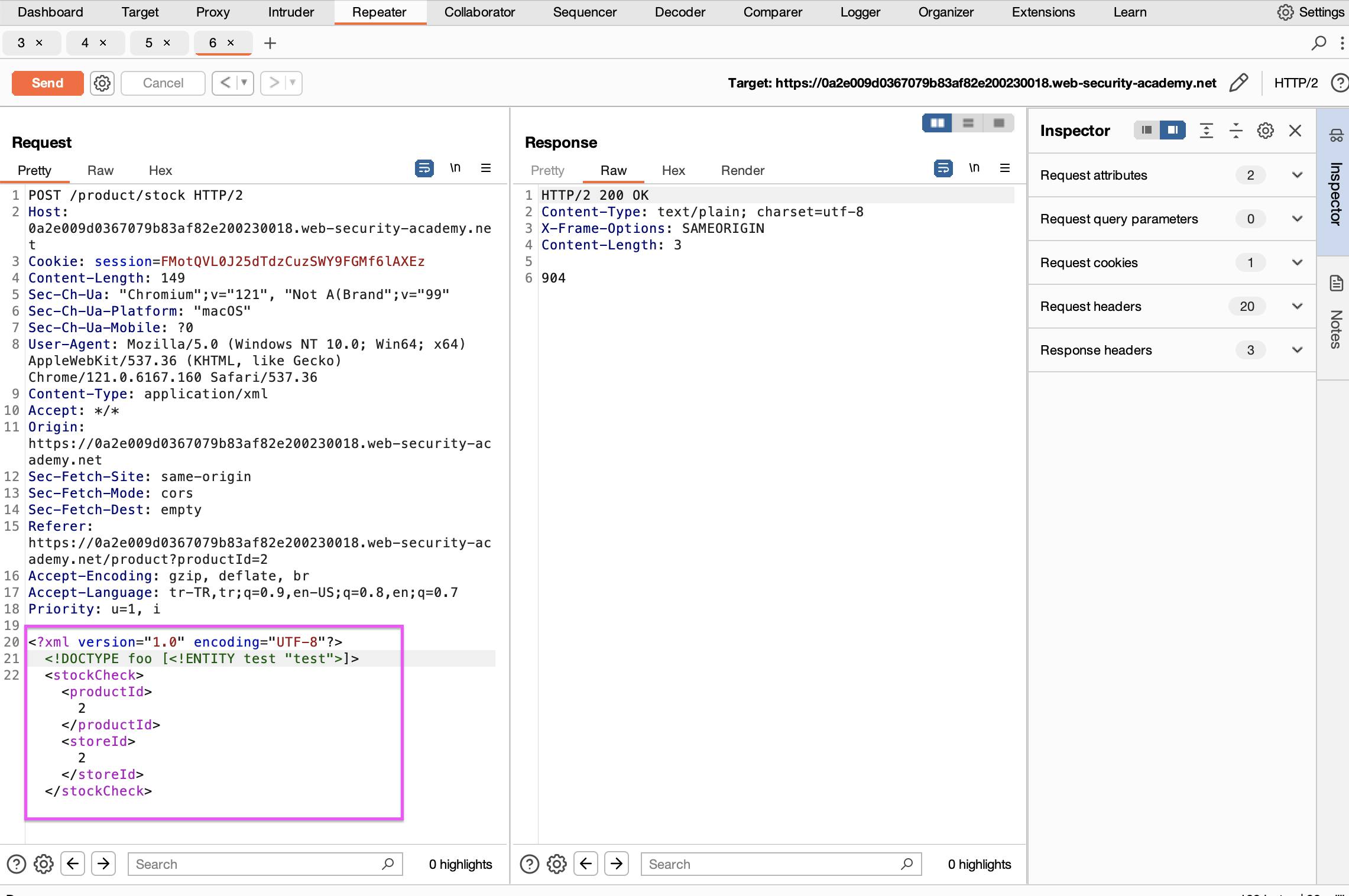
If we try to use a reference we get an error and what we should do is try to get results with out-of-band.
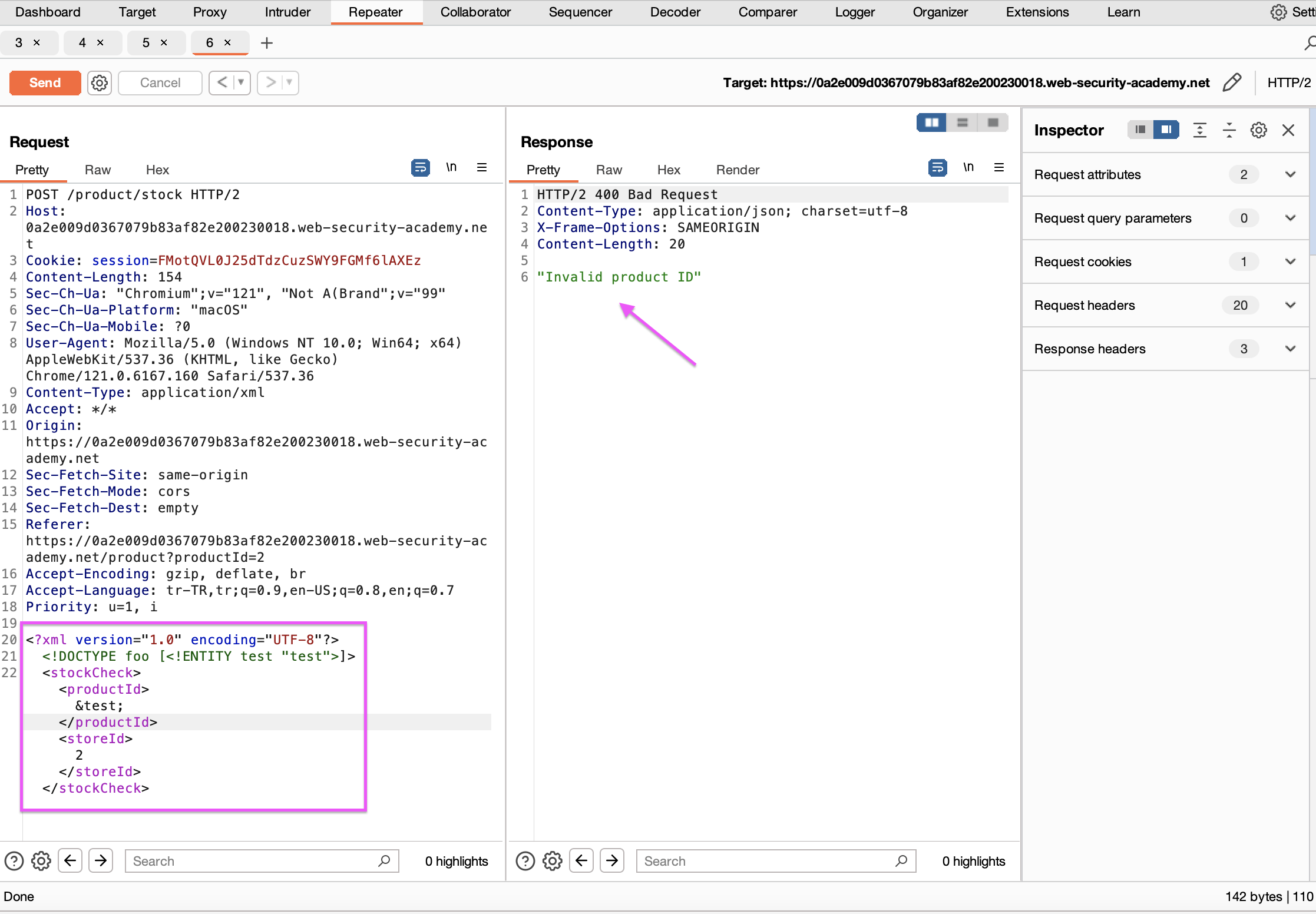
We edit our payload and manage to get an HTTP request. This means that the attacker has control over the application server.

Hello, I am Aleyna Doğan. I work as a Cyber Threat Intelligence Analyst. In my blog, we write blog posts that my friends and I want to share. Have a good read.