Use Cyber Threat Intelligence knowledge and skills to identify a threat based on a report.
1. What kind of phishing campaign does APT X use as part of their TTPs?
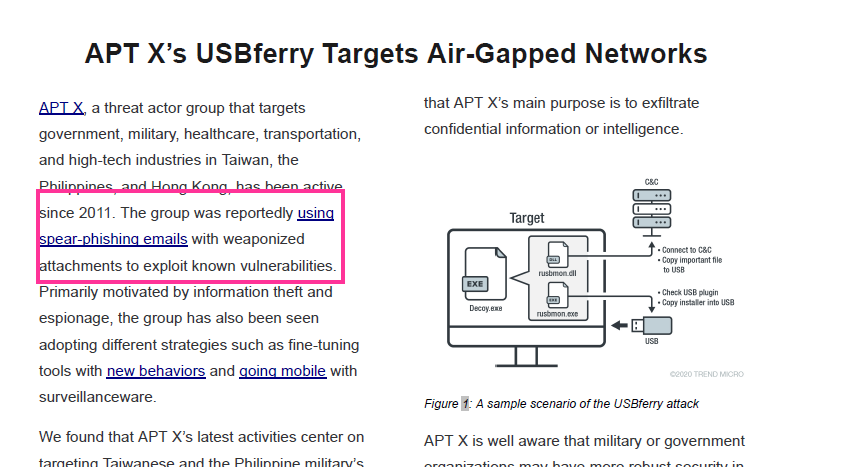
spear-phishing emails
2. What is the name of the malware used by APT X?
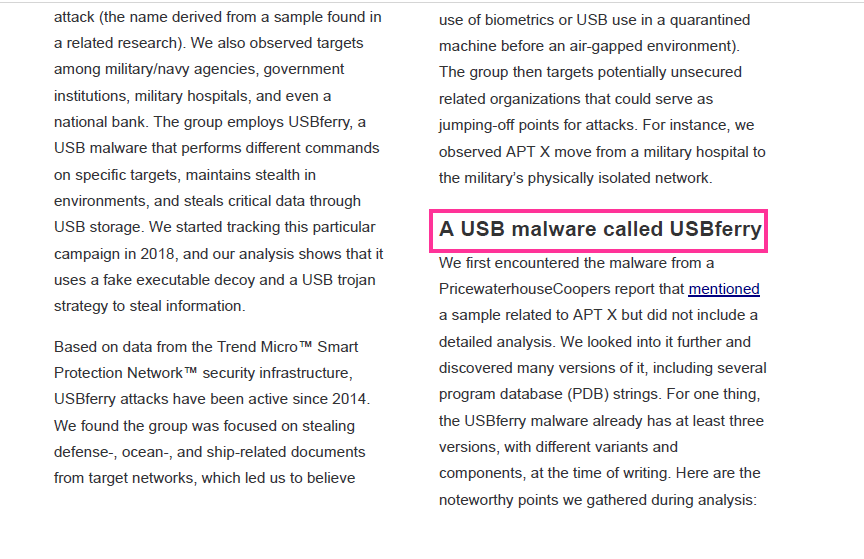
USBferry
3. What is the malware’s STIX ID?
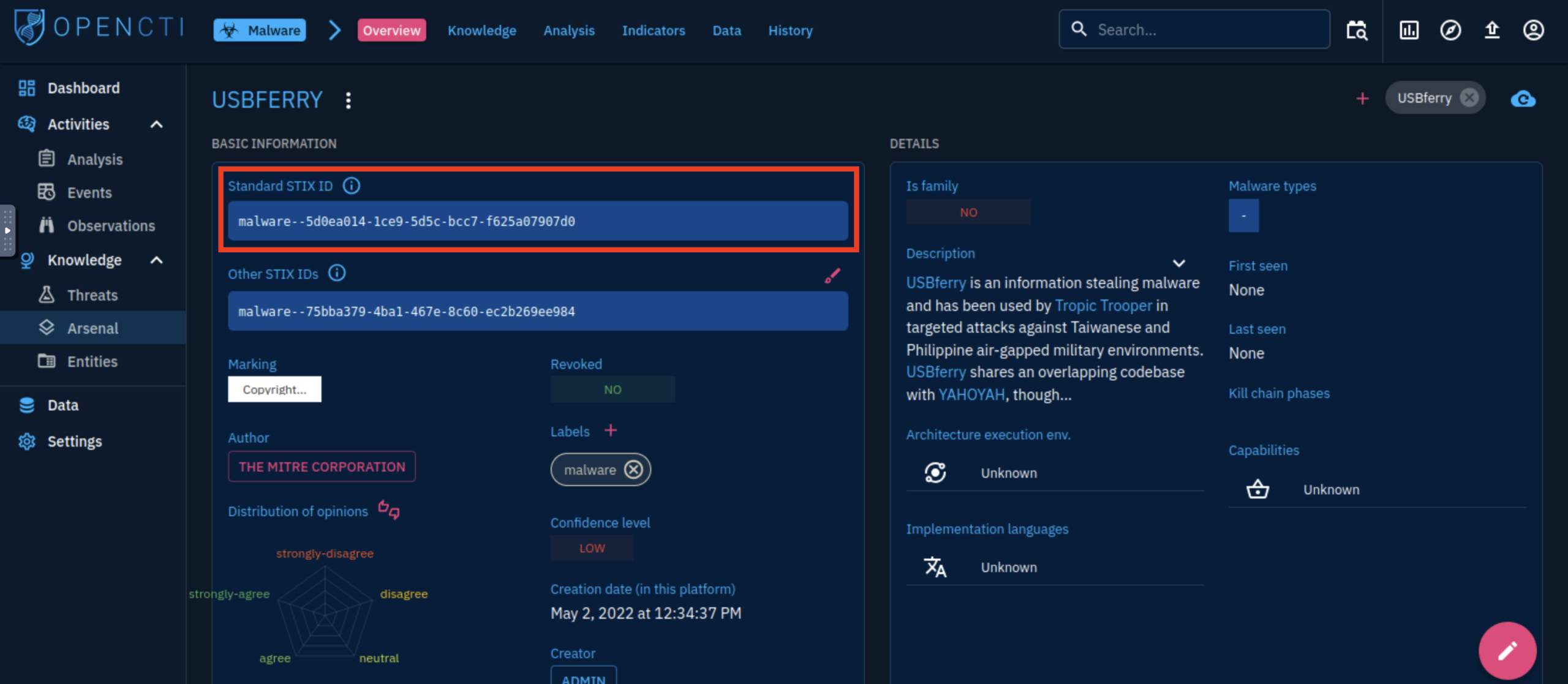
malware–5d0ea014-1ce9-5d5c-bcc7-f625a07907d0
4. With the use of a USB, what technique did APT X use for initial access?
Accessed the OpenCTI platform using the provided credentials and navigated to the “Malware” > USBferry section to gather information about the malware used by APT X.
In the “External References” section, I noticed a relevant threat intelligence report titled “TrendMicro Tropic Trooper May 2020”. I clicked the link to open the full PDF document hosted by TrendMicro.
I scanned through the PDF and found a key table on page 28, which lists Tactics, Techniques, and IDs.
Under the “Initial Access” tactic, I found the technique T1091 – Replication Through Removable Media clearly highlighted.
This technique matches our context perfectly, as it describes copying malware to USB devices to spread across air-gapped environments—just like APT X did.
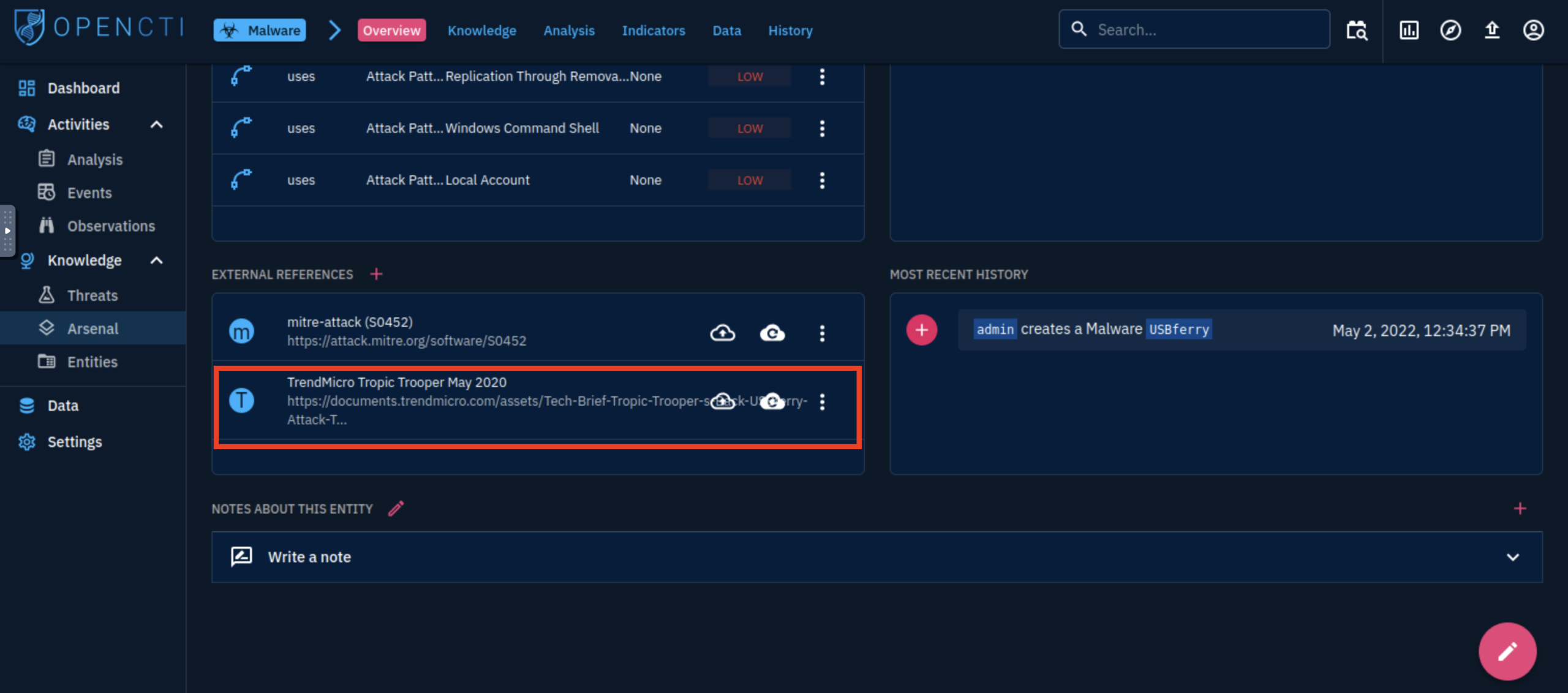
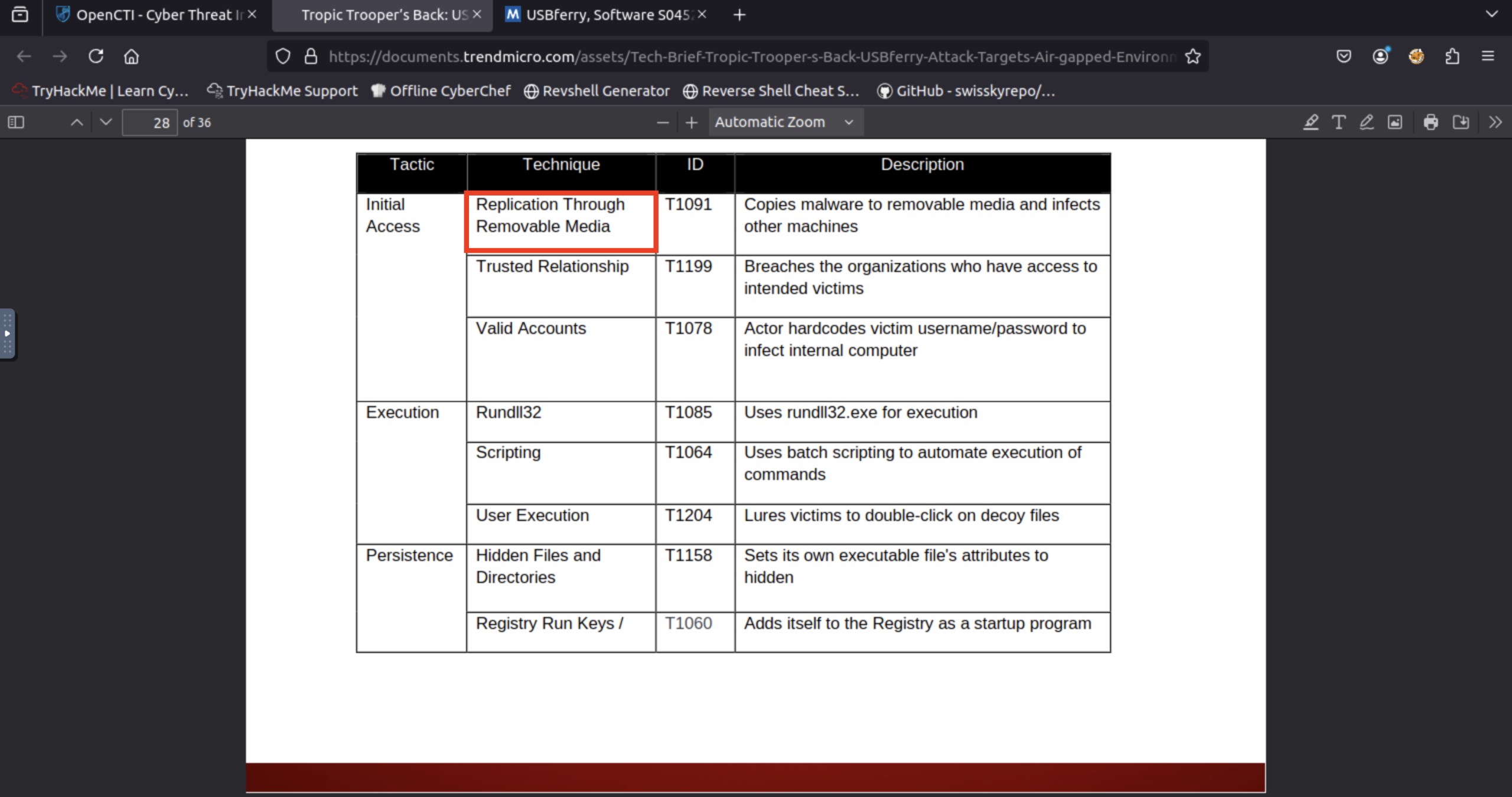
Replication through removable media
5. What is the identity of APT X?
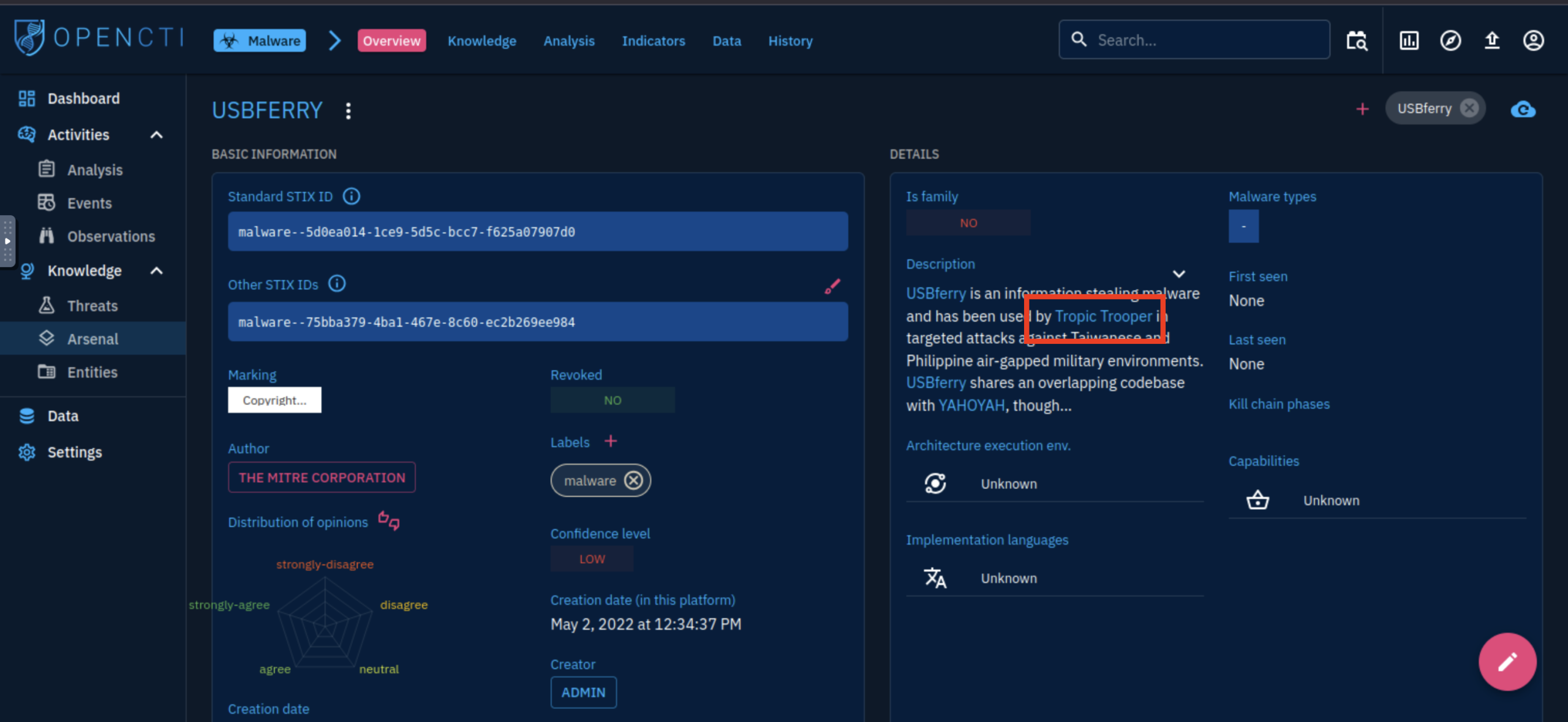
Tropic Trooper
6. On OpenCTI, how many Attack Pattern techniques are associated with the APT?
How I found it:
- I logged into the OpenCTI platform and navigated to the left-hand menu.
- Under Knowledge, I clicked on Threats and then selected the Intrusion Sets section at the top.
- I searched for Tropic Trooper (which is the true identity of APT X) using the search bar.
- I clicked on the Tropic Trooper profile to open the detailed view.
- From the top menu, I selected the Knowledge tab.
- On the right side of the screen, under the Distribution of Relations, I saw that 39 Attack Pattern techniques are associated with this threat group.
That’s how I was able to confidently find and verify the answer.
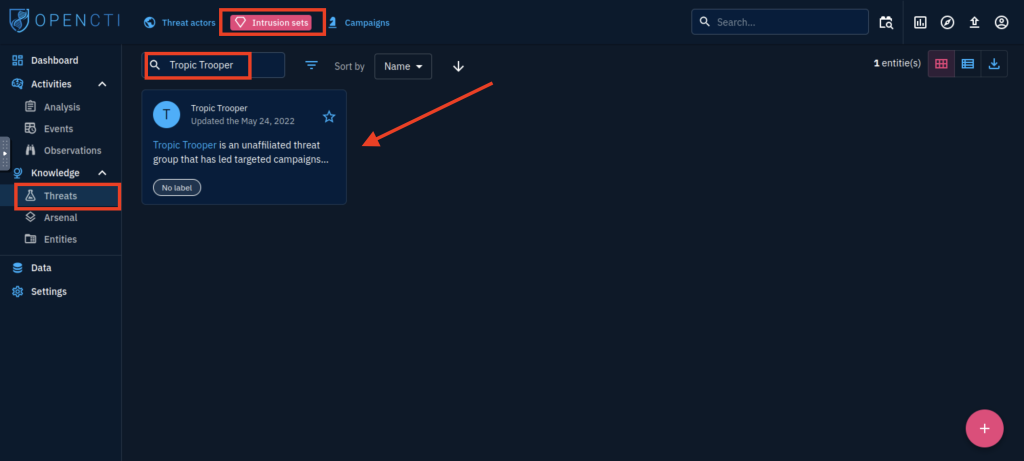
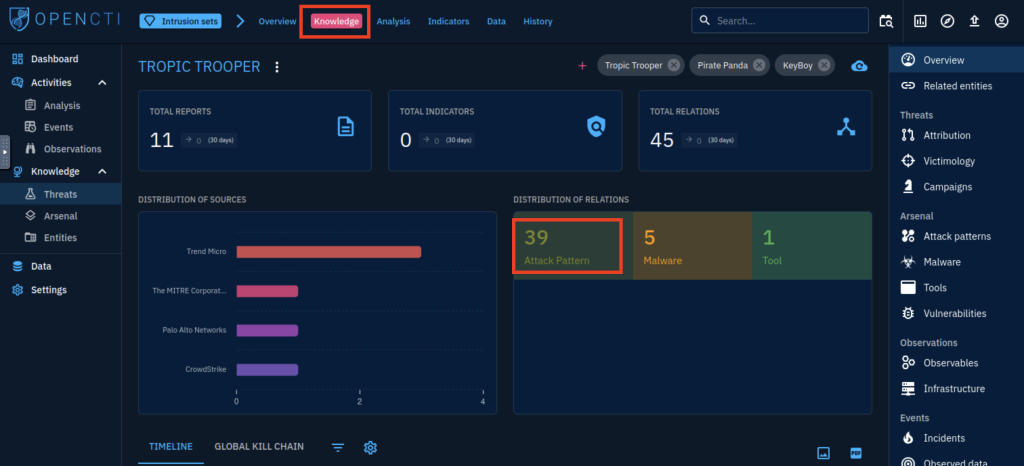
39
7. What is the name of the tool linked to the APT?
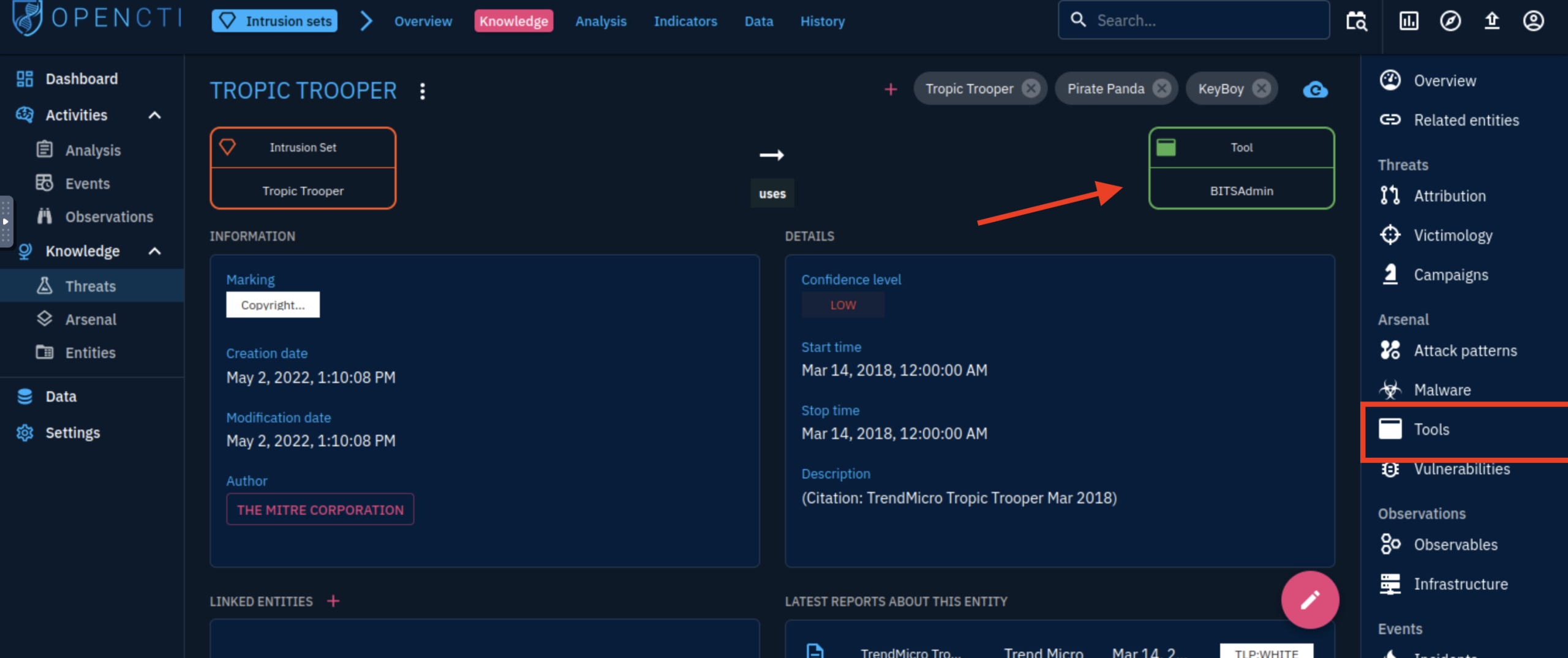
BITSAdmin
8. Load up the Navigator. What is the sub-technique used by the APT under Valid Accounts?
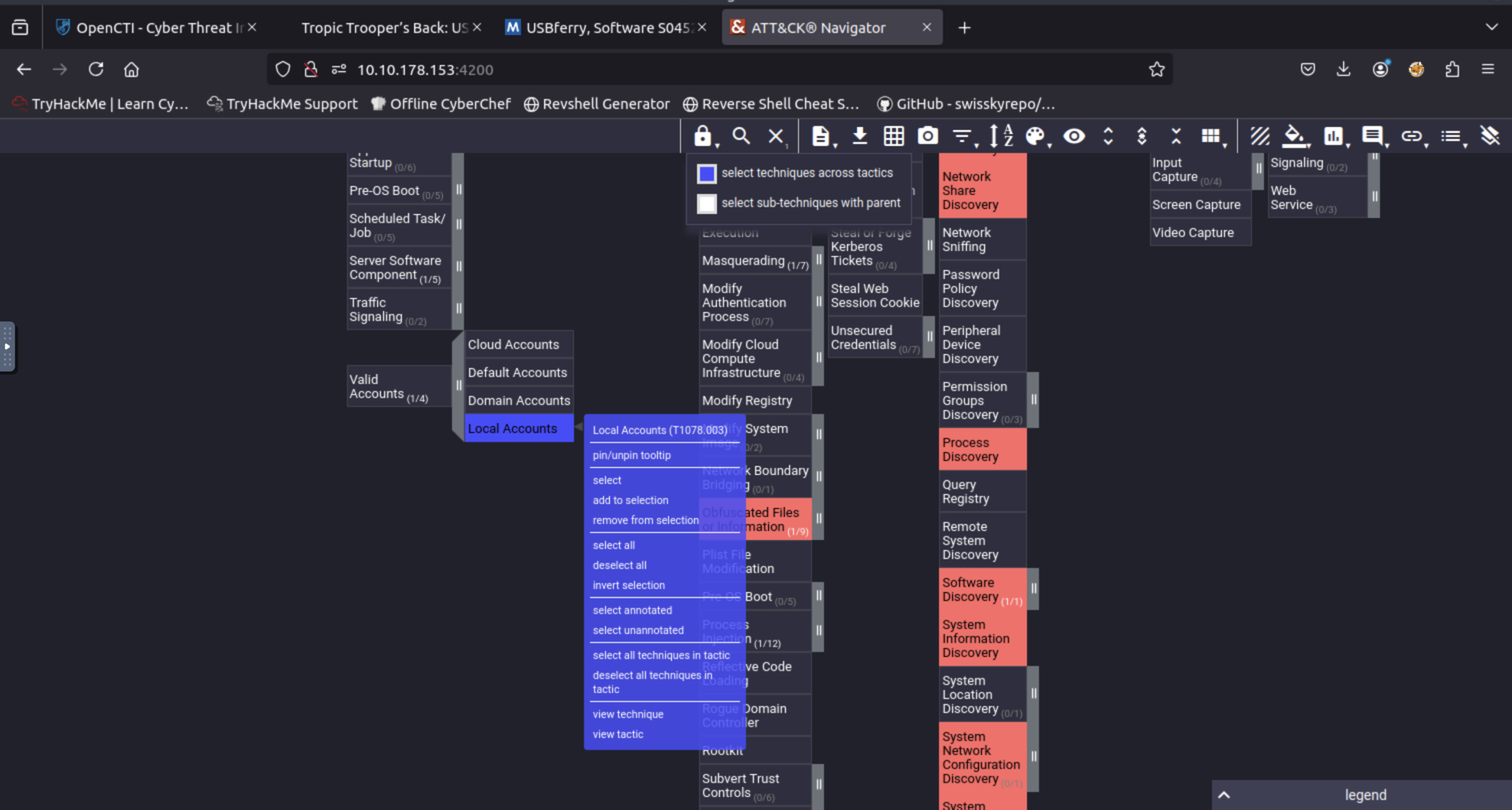
Local Accounts
9. Under what Tactics does the technique above fall?
Initial Access, Persistence, Defense Evasion and Privilege Escalation
10. What technique is the group known for using under the tactic Collection?
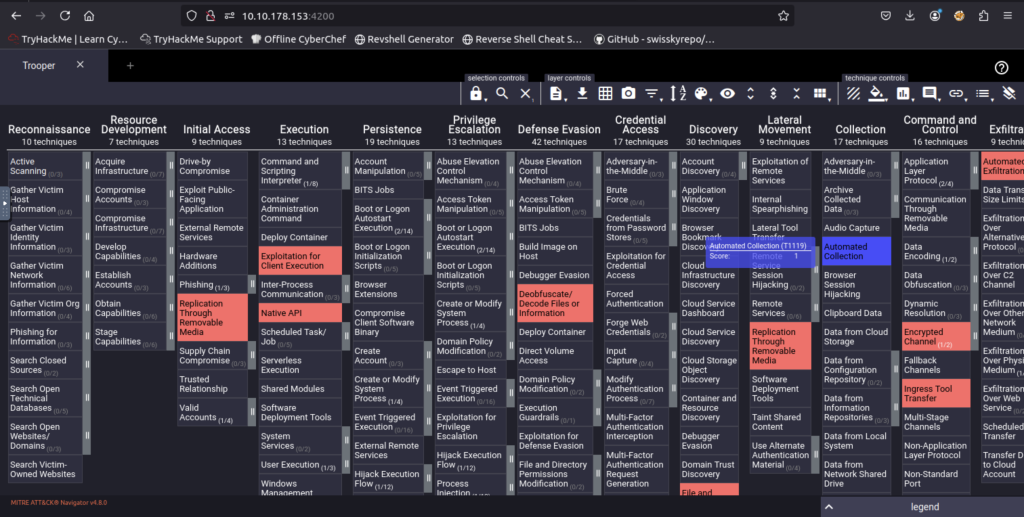
Automated Collection

