The room: “Learn the applications and language that is Yara for everything threat intelligence, forensics, and threat hunting!“
https://tryhackme.com/room/yara
Task 2: What is Yara?
2.1. What is the name of the base-16 numbering system that Yara can detect?
hex
2.2. Would the text “Enter your Name” be a string in an application? (Yay/Nay)
Yay
Task 8: Using LOKI and its Yara rule set
8.1. Scan file 1. Does Loki detect this file as suspicious/malicious or benign?
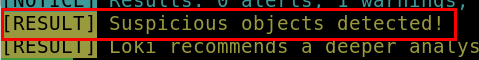
suspicious
8.2. What Yara rule did it match on?
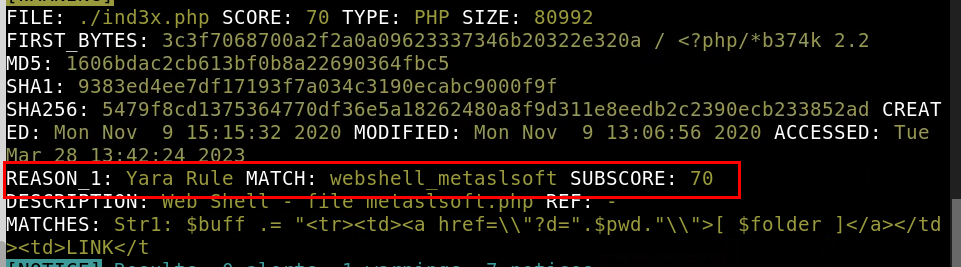
webshell_metaslsoft
8.3. What does Loki classify this file as?
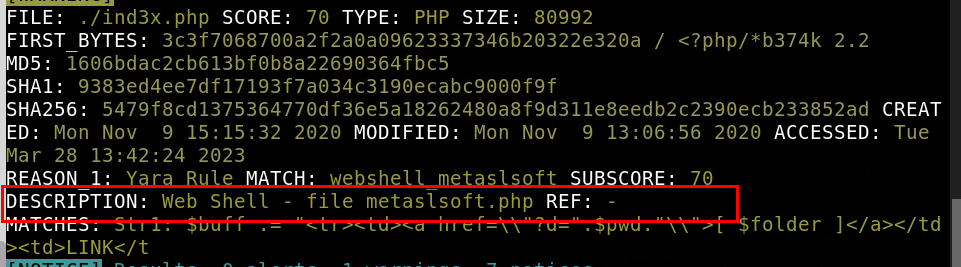
web shell
8.4. Based on the output, what string within the Yara rule did it match on?
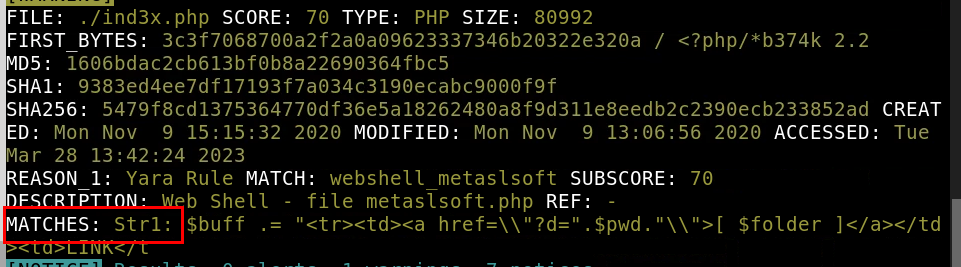
Str1
8.5. What is the name and version of this hack tool?
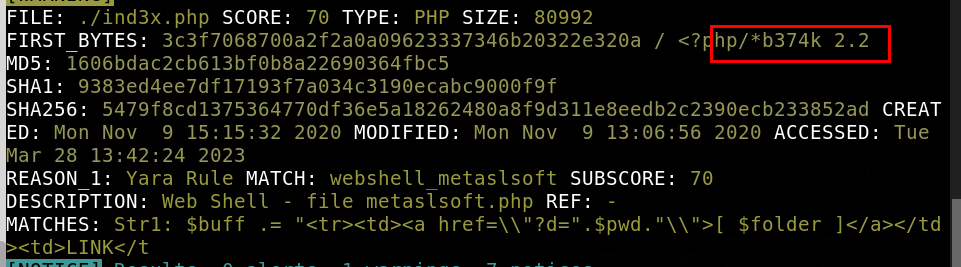
b374k 2.2
8.6. Inspect the actual Yara file that flagged file 1. Within this rule, how many strings are there to flag this file?
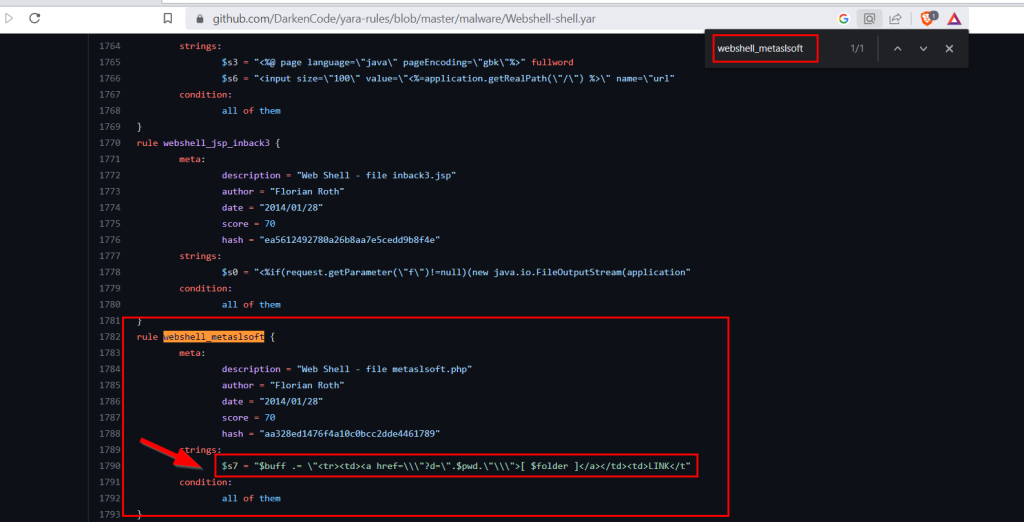
1
8.7. Scan file 2. Does Loki detect this file as suspicious/malicious or benign?
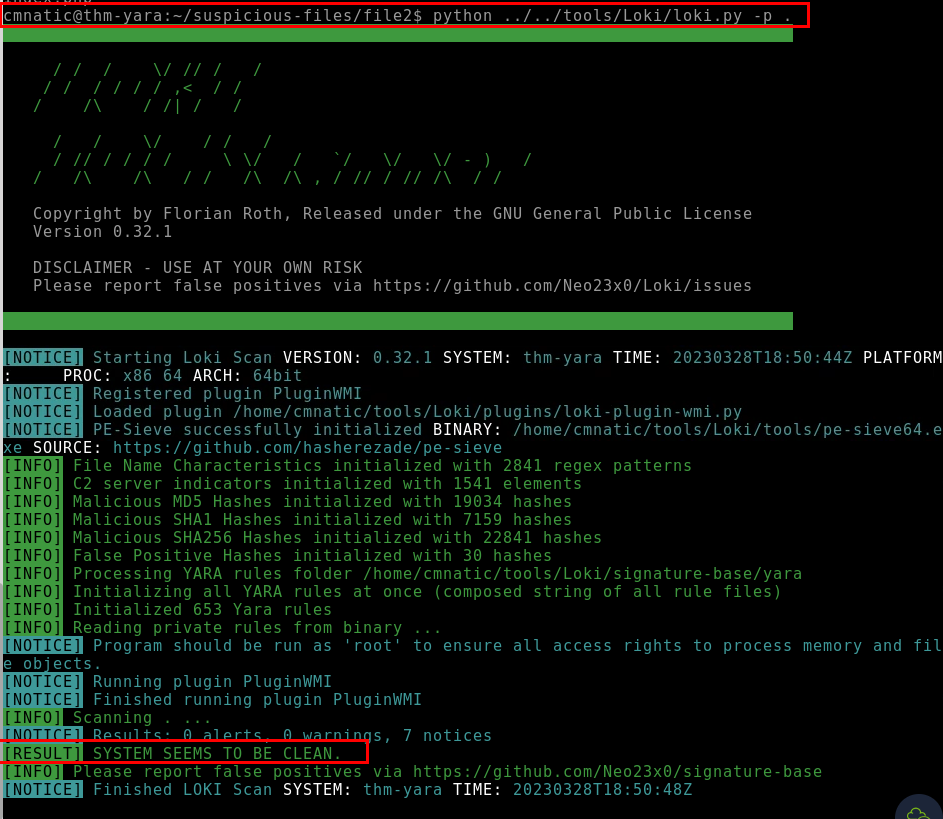
benign
8.8. Inspect file 2. What is the name and version of this web shell?
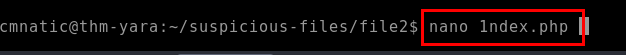
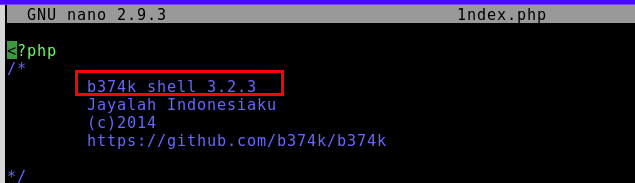
b374k 3.2.3
Task 9: Creating Yara rules with yarGen
9.1. From within the root of the suspicious files directory, what command would you run to test Yara and your Yara rule against file 2?
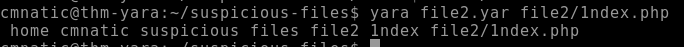
yara file2.yar file2/1ndex.php
9.2. Did Yara rule flag file 2? (Yay/Nay)
yay
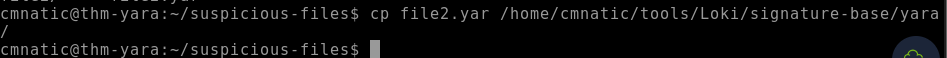
9.3. Copy the Yara rule you created into the Loki signatures directory.
cp file2.yar /home/cmnatic/tools/Loki/signature-base/yara/
9.4. Test the Yara rule with Loki, does it flag file 2? (Yay/Nay)
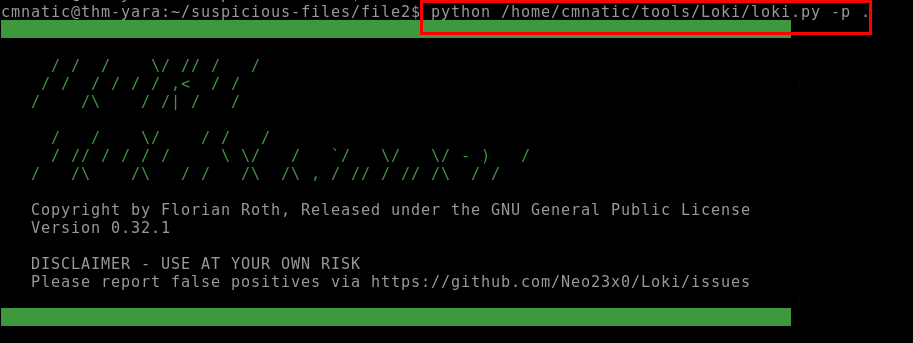
yay
9.5. What is the name of the variable for the string that it matched on?
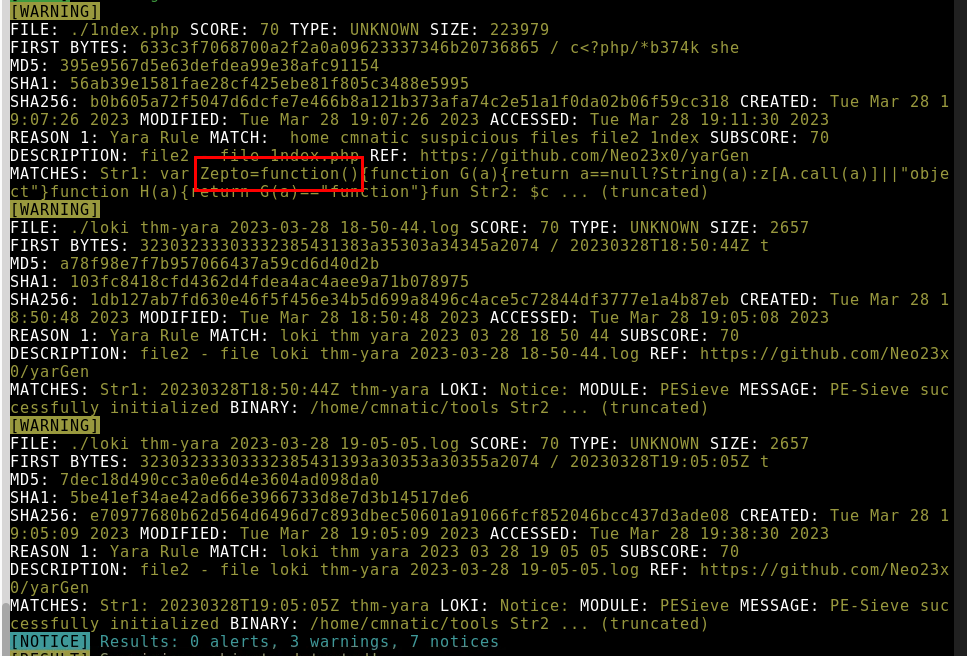
Zepto
9.6. Inspect the Yara rule, how many strings were generated?
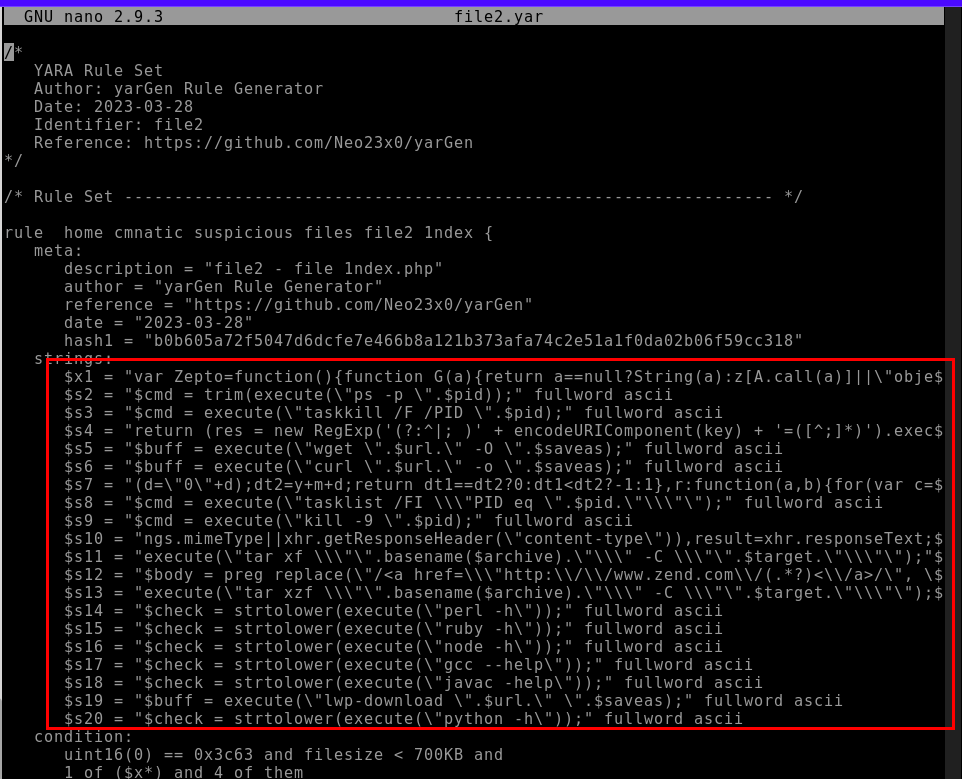
20
9.7. One of the conditions to match on the Yara rule specifies file size. The file has to be less than what amount?
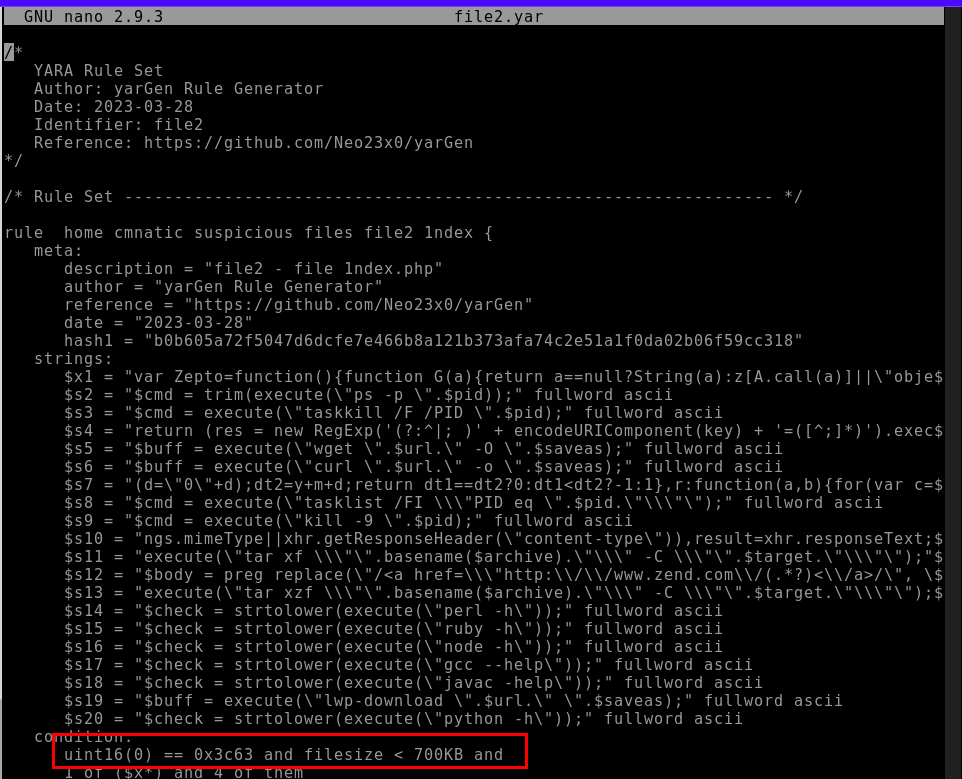
700KB
Task 10: Valhalla
10.1. Enter the SHA256 hash of file 1 into Valhalla. Is this file attributed to an APT group? (Yay/Nay)
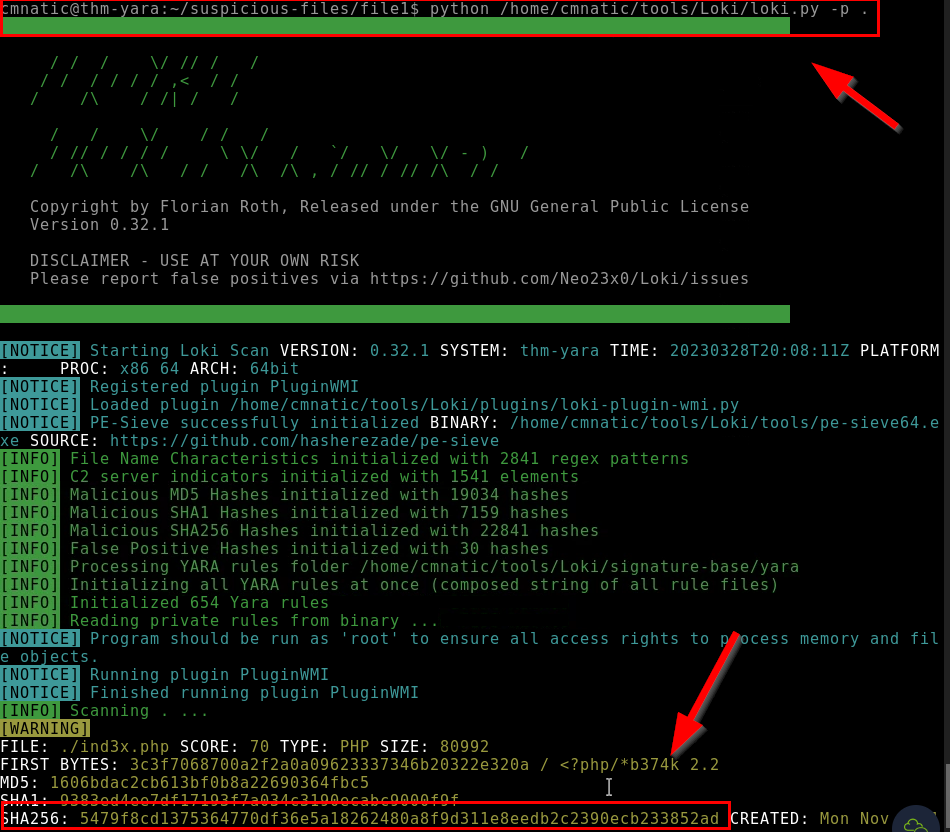
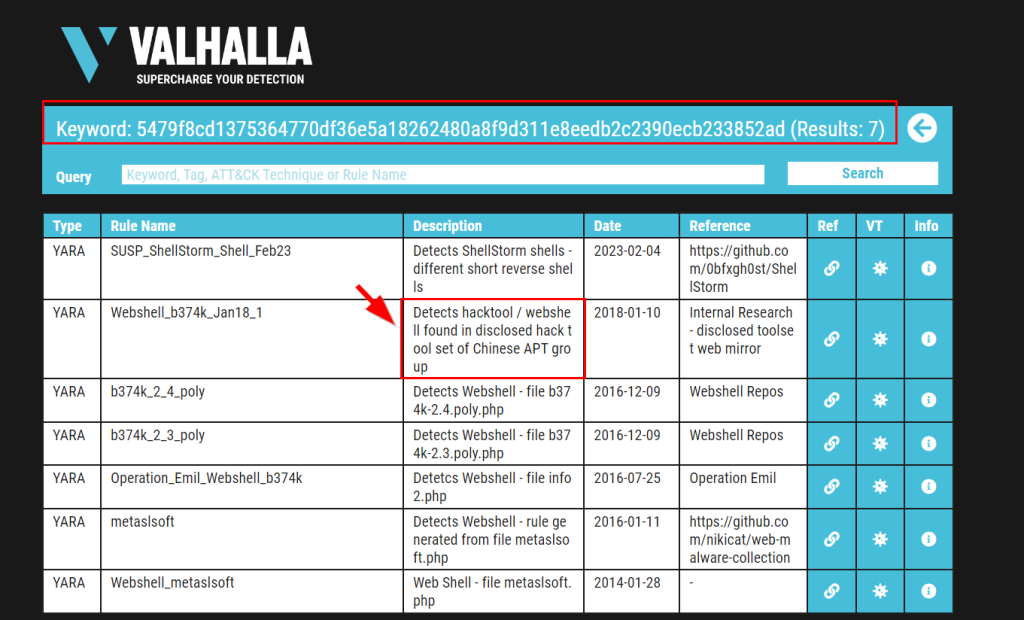
yay
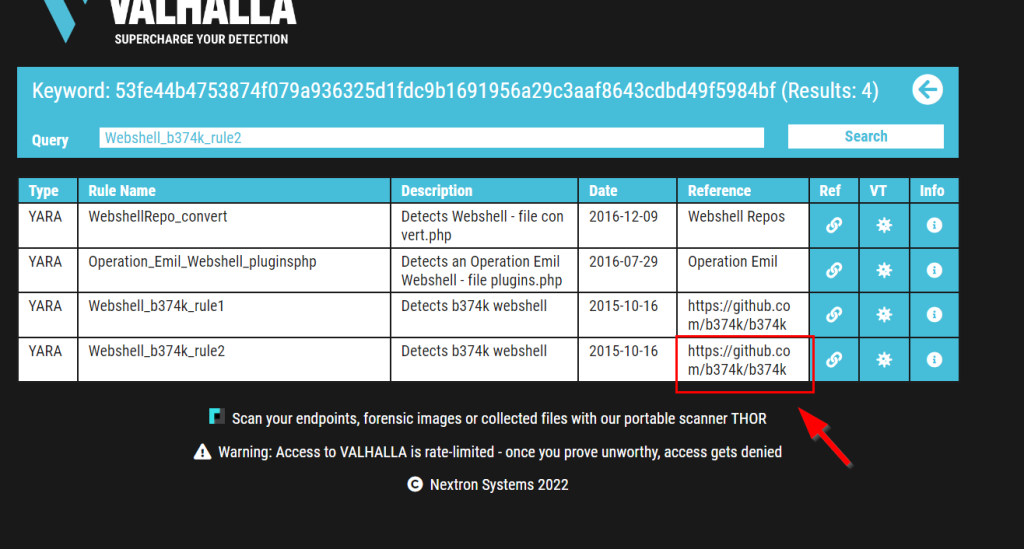
10.2. Do the same for file 2. What is the name of the first Yara rule to detect file 2?
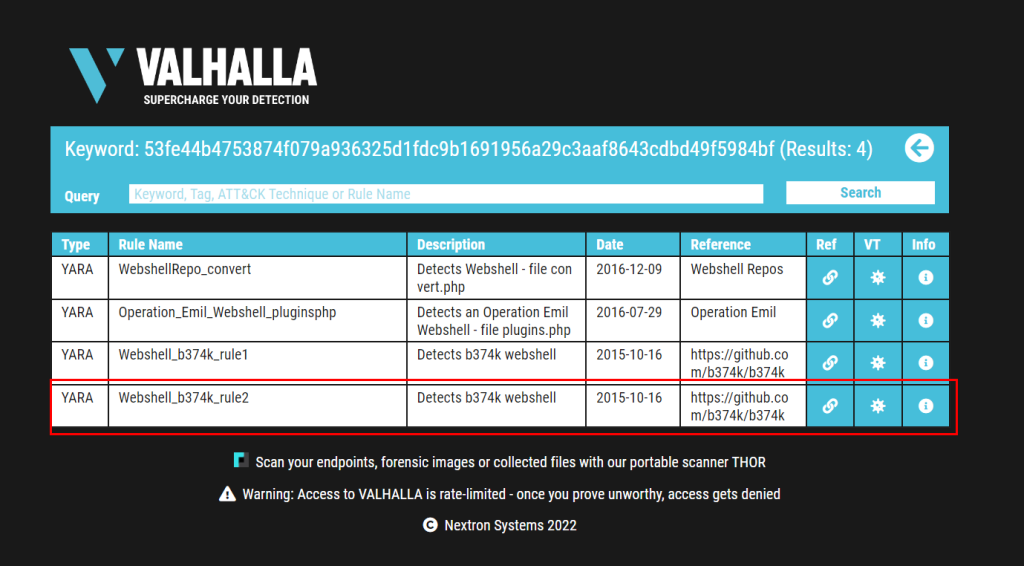
Webshell_b374k_rule2
10.3. Examine the information for file 2 from Virus Total (VT). The Yara Signature Match is from what scanner?
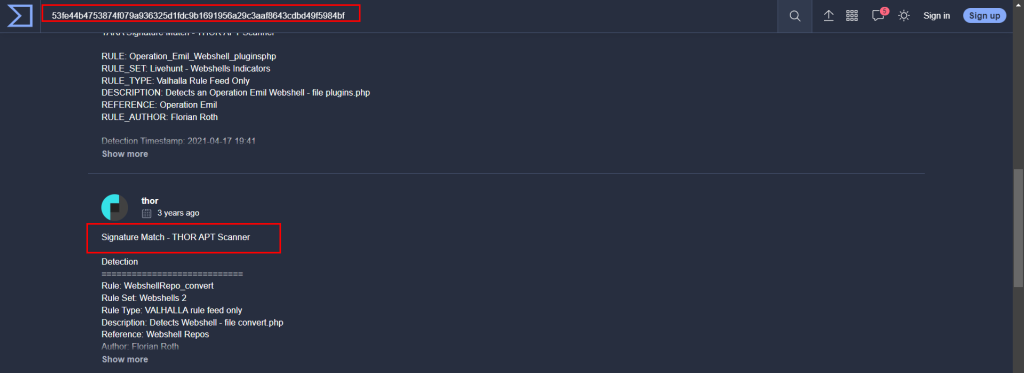
THOR APT Scanner
10.4. Enter the SHA256 hash of file 2 into Virus Total. Did every AV detect this as malicious? (Yay/Nay)
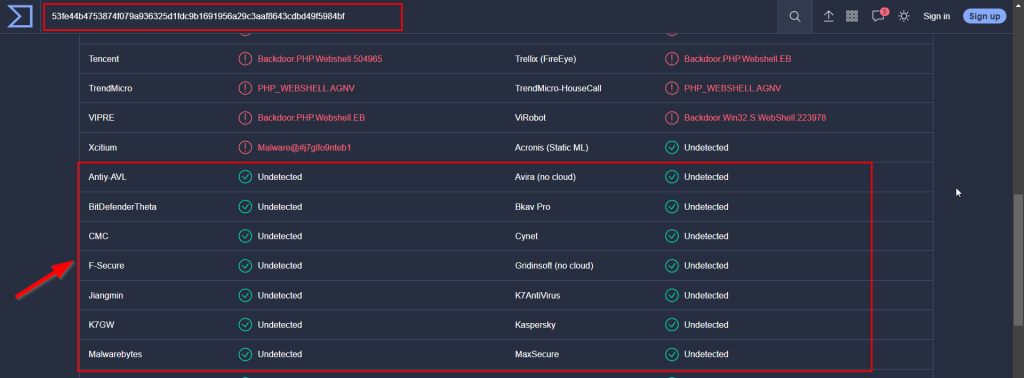
nay
10.5. Besides .PHP, what other extension is recorded for this file?
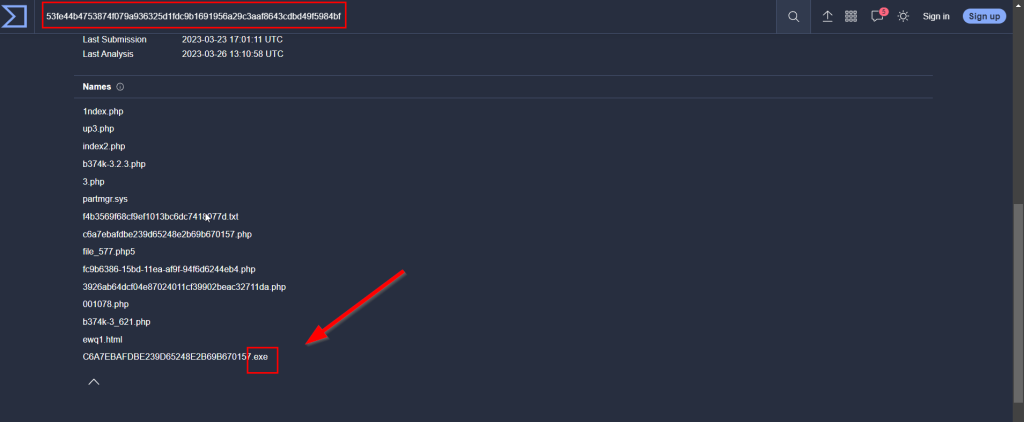
exe
10.6. What JavaScript library is used by file 2?
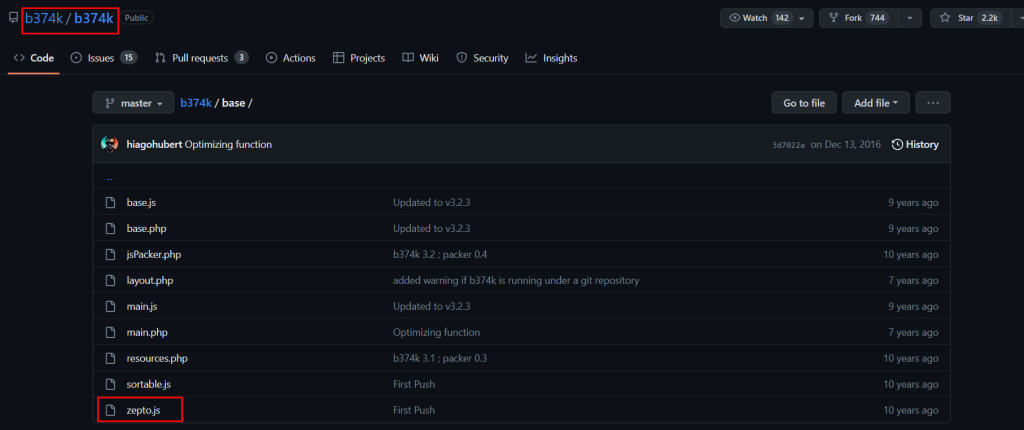
zepto
10.7. Is this Yara rule in the default Yara file Loki uses to detect these type of hack tools? (Yay/Nay)
nay
a

