The room: “The Unified Kill Chain is a framework which establishes the phases of an attack, and a means of identifying and mitigating risk to IT assets.”
https://tryhackme.com/room/unifiedkillchain
Task 2: What is a “Kill Chain”
2.1. Where does the term “Kill Chain” originate from?
For this answer, you must fill in the blank!: The ********
military
Task 3: What is “Threat Modelling”
3.1. What is the technical term for a piece of software or hardware in IT (Information Technology?)
“An IT asset is a piece of software or hardware within an information technology environment”
asset
Task 4: Introducing the Unified Kill Chain
4.1. In what year was the Unified Kill Chain framework released?
2017
4.2. According to the Unified Kill Chain, how many phases are there to an attack?
18
4.3. What is the name of the attack phase where an attacker employs techniques to evade detection?
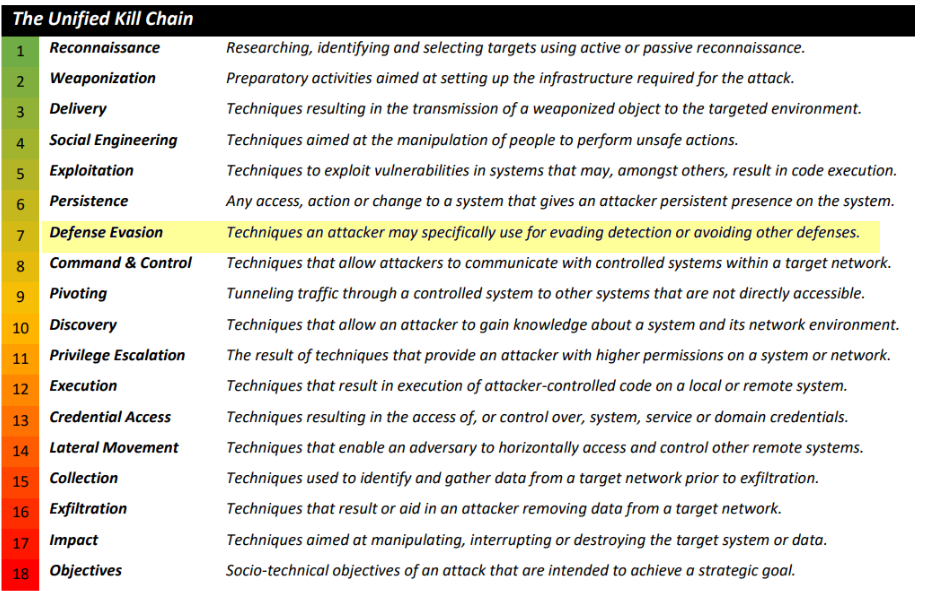
Defense Evasion
4.4. What is the name of the attack phase where an attacker employs techniques to remove data from a network?
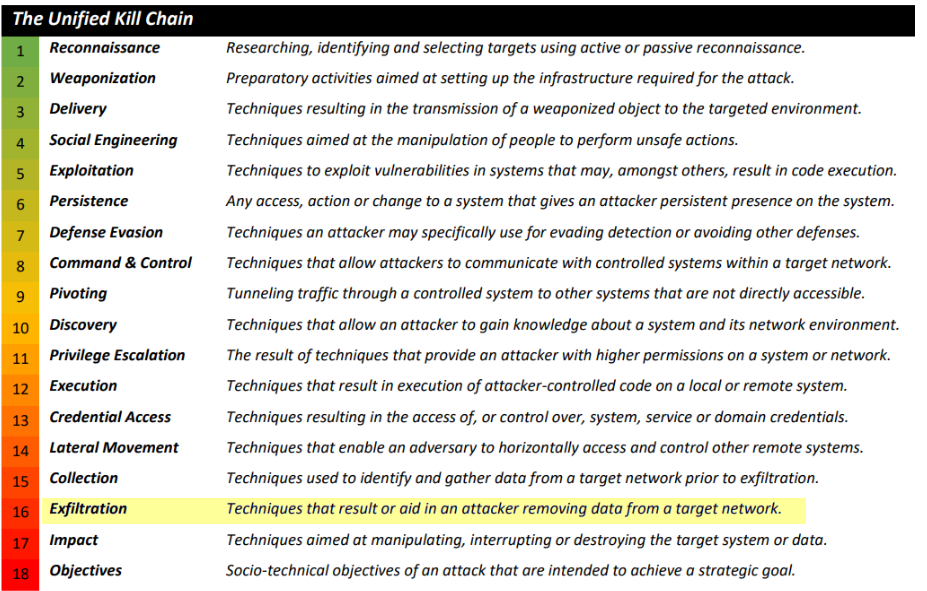
Exfiltration
4.5. What is the name of the attack phase where an attacker achieves their objectives?
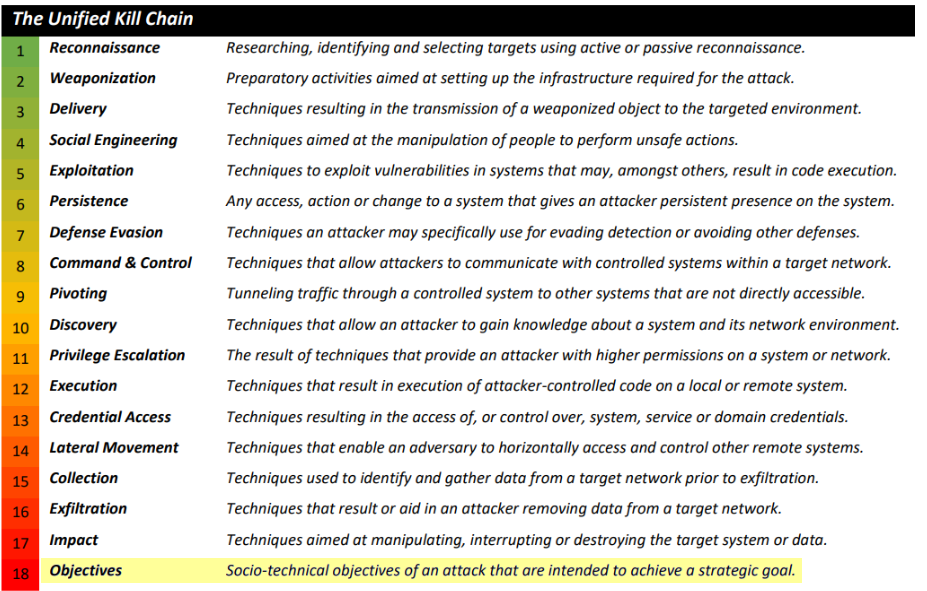
Objectives
Task 5: Phase: In (Initial Foothold)
5.1. What is an example of a tactic to gain a foothold using emails?
Phishing
5.2. Impersonating an employee to request a password reset is a form of what?
Social Engineering
5.3. An adversary setting up the Command & Control server infrastructure is what phase of the Unified Kill Chain?
Weaponization
5.4. Exploiting a vulnerability present on a system is what phase of the Unified Kill Chain?
Exploitation
5.5. Moving from one system to another is an example of?
Pivoting
5.6. What is an example of a tactic to gain a foothold using emails?
Persistence
Task 6: Phase: Through (Network Propagation)
6.1. As a SOC analyst, you pick up numerous alerts pointing to failed login attempts from an administrator account. What stage of the kill chain would an attacker be seeking to achieve?
Privilege Escalation
6.2. Mimikatz, a known attack tool, was detected running on the IT Manager’s computer. What is the mission of the tool?
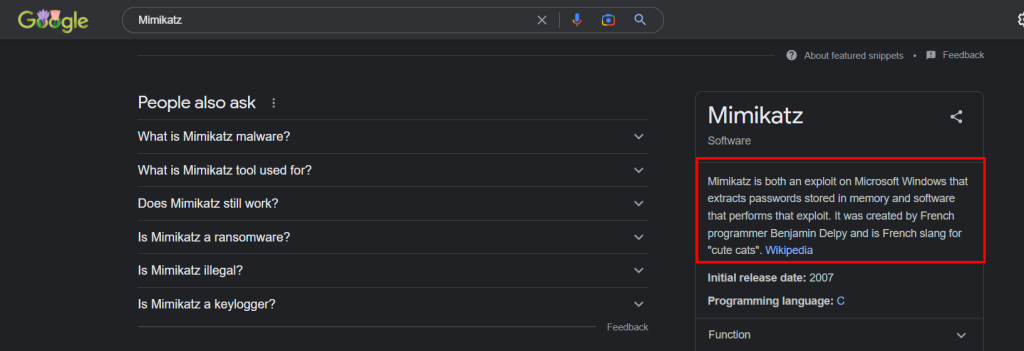

credential dumping
Task 7: Phase: Out (Action on Objectives)
7.1. While monitoring the network as a SOC analyst, you realise that there is a spike in the network activity, and all the traffic is outbound to an unknown IP address. What stage could describe this activity?
Exfiltration
7.2. Personally identifiable information (PII) has been released to the public by an adversary, and your organisation is facing scrutiny for the breach. What part of the CIA triad would be affected by this action?
Confidentiality
Task 8: Practical
8.1. The Attacker uses tools to gather information about a system
What phase of the Unified Kill Chain is this?

Reconnaissance
8.2. The Attacker installs a malicious script to allow them remote access at a later date
What phase of the Unified Kill Chain is this?
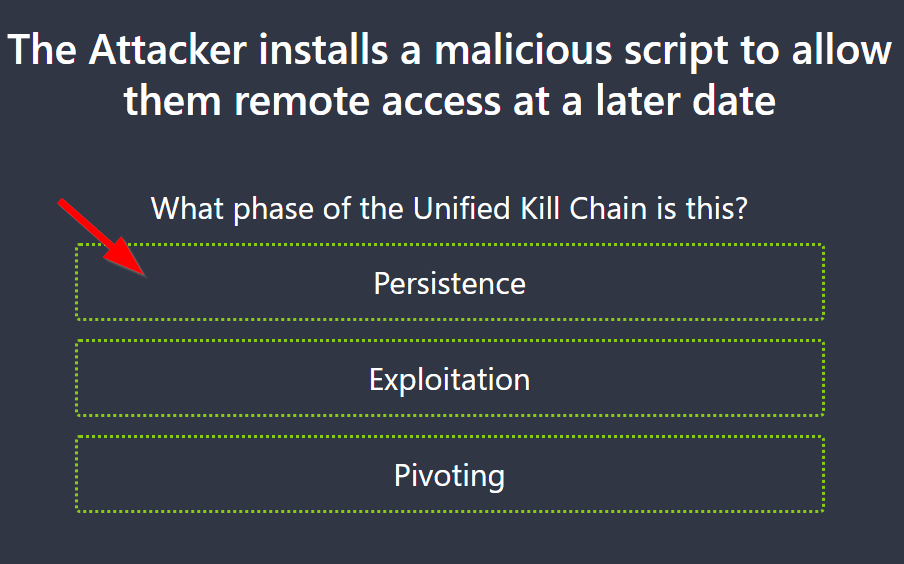
Persistence
8.3. The hacked machine is being controlled from an Attacker’s own server
What phase of the Unified Kill Chain is this?
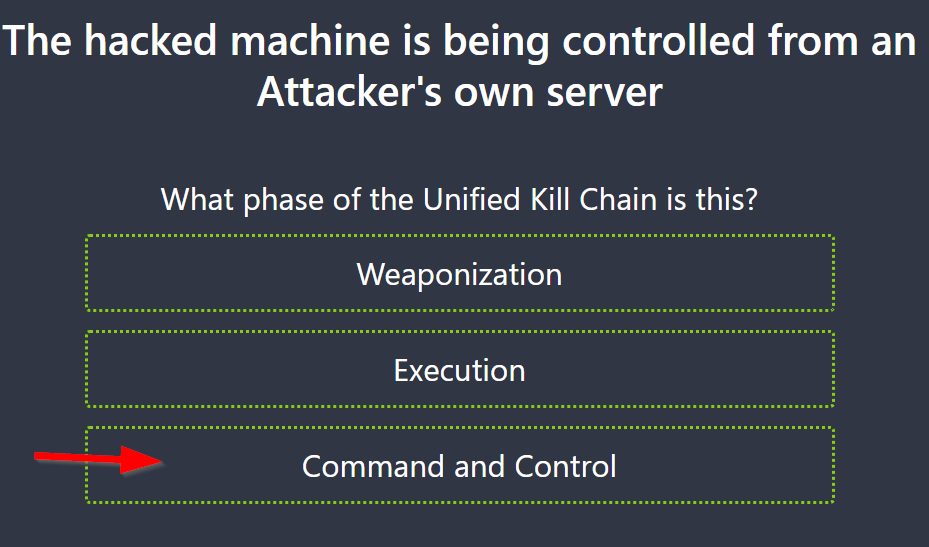
Command & Control
8.4. The Attacker uses the hacked machine to access other servers on the same network
What phase of the Unified Kill Chain is this?
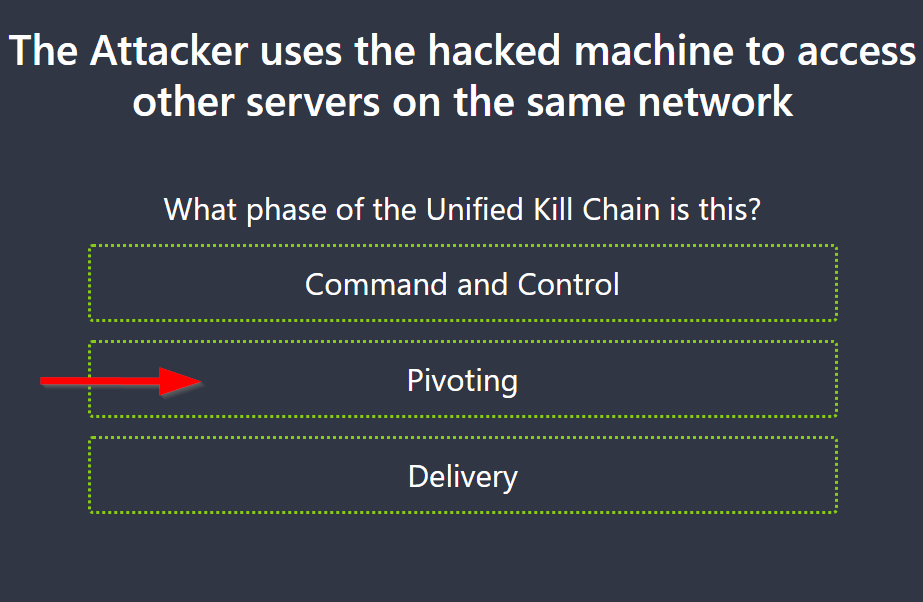
Pivoting
8.5. The Attacker steals a database and sells this to a 3rd party
What phase of the Unified Kill Chain is this?
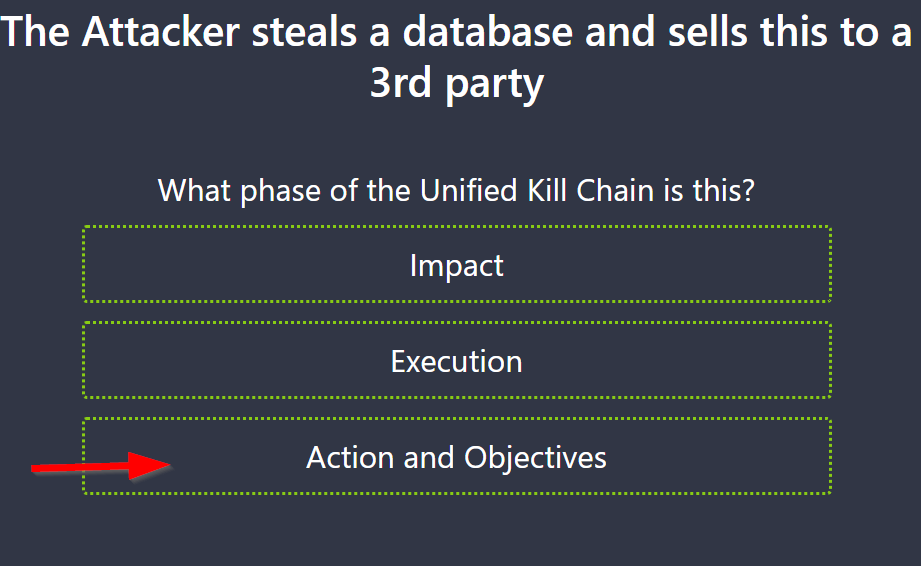
Action on Objectives
8. Match the scenario prompt to the correct phase of the Unified Kill Chain to reveal the flag at the end. What is the flag?
THM{UKC_SCENARIO}

