Learn the basics of TShark and take your protocol and PCAP analysis skills a step further.
Lab link.
Task 2: Command-Line Packet Analysis Hints | TShark and Supplemental CLI Tools
2.2. View the details of the demo.pcapng file with “capinfos”.
What is the “RIPEMD160” value?
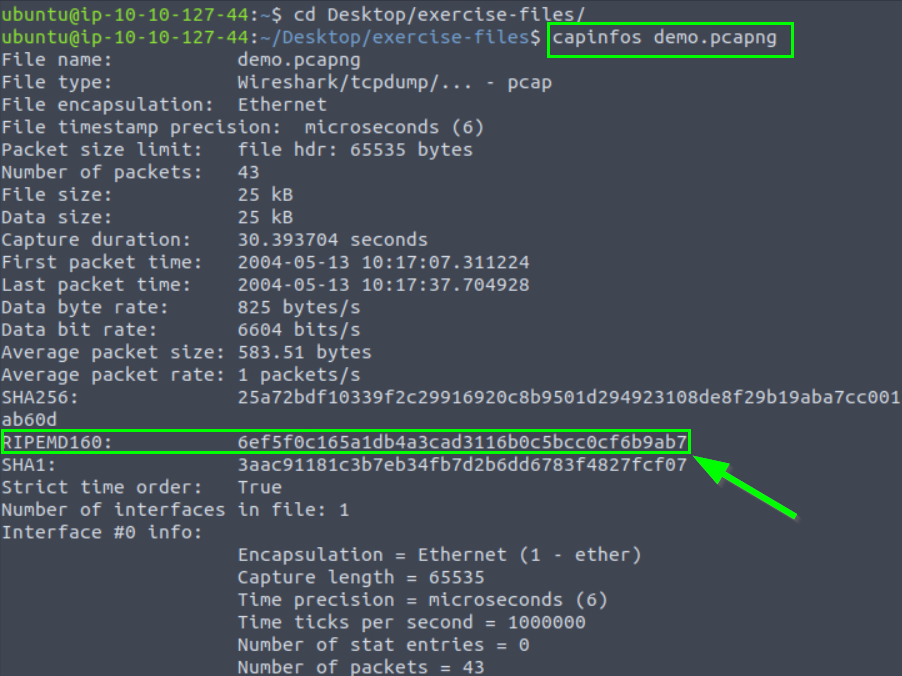
6ef5f0c165a1db4a3cad3116b0c5bcc0cf6b9ab7
Task 3: TShark Fundamentals I | Main Parameters I
3.1. What is the installed TShark version in the given VM?
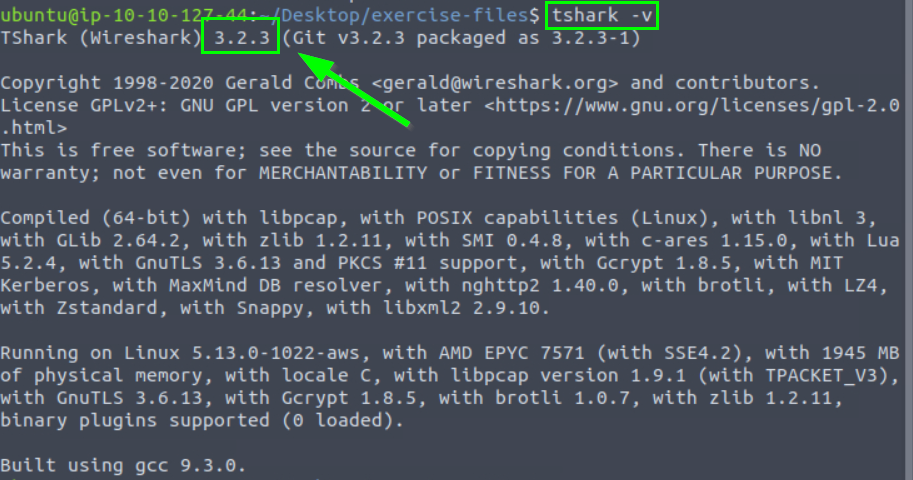
3.2.3
3.2. List the available interfaces with TShark.
What is the number of available interfaces in the given VM?
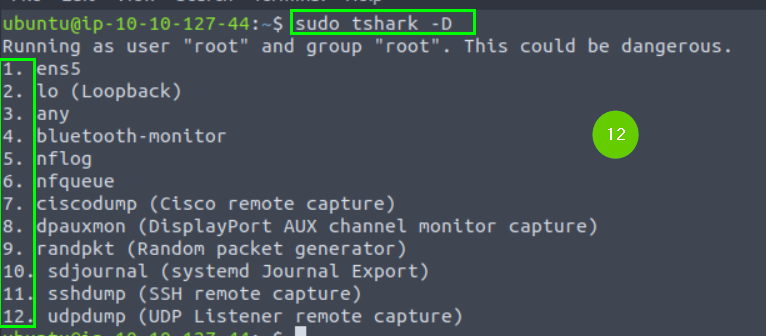
12
Task 4: TShark Fundamentals I | Main Parameters II
4.1. Read the “demo.pcapng” file with TShark.
What are the assigned TCP flags in the 29th packet?

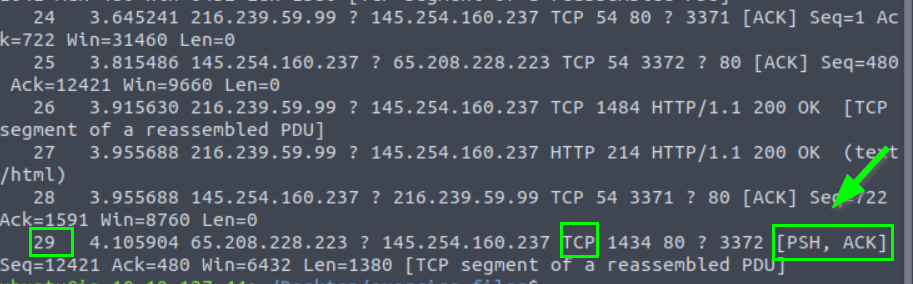
PSH, ACK
4.2. What is the “Ack” value of the 25th packet?
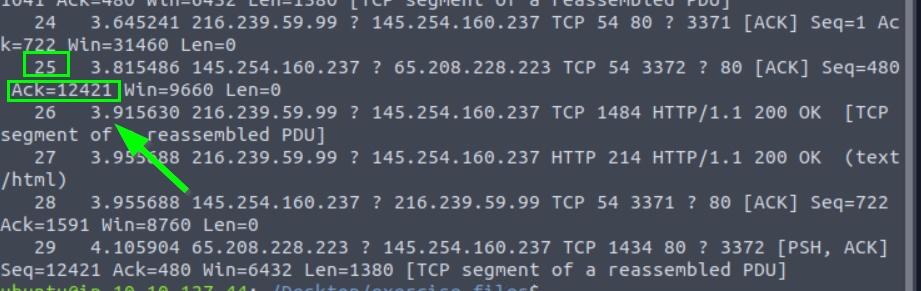
12421
4.3. What is the “Window size value” of the 9th packet?
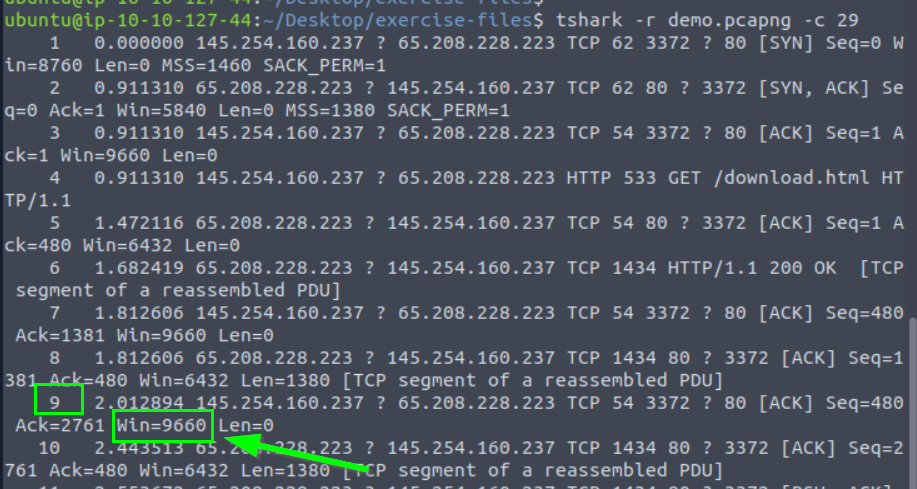
9660
Task 5: TShark Fundamentals II | Capture Conditions
5.1. Which parameter can help analysts to create a continuous capture dump?
-b
5.2. Can we combine autostop and ring buffer parameters with TShark? y/n
y
Task 6: TShark Fundamentals III | Packet Filtering Options: Capture vs. Display Filters
6.1. Which parameter is used to set “Capture Filters”?
-f
6.2. Which parameter is used to set “Display Filters”?
-Y
Task 7: TShark Fundamentals IV | Packet Filtering Options: Capture Filters
In the first terminal we execute the following command.
tshark -f "host 10.10.10.10",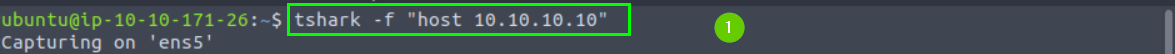
In the second terminal we execute the following command.
curl -v 10.10.10.10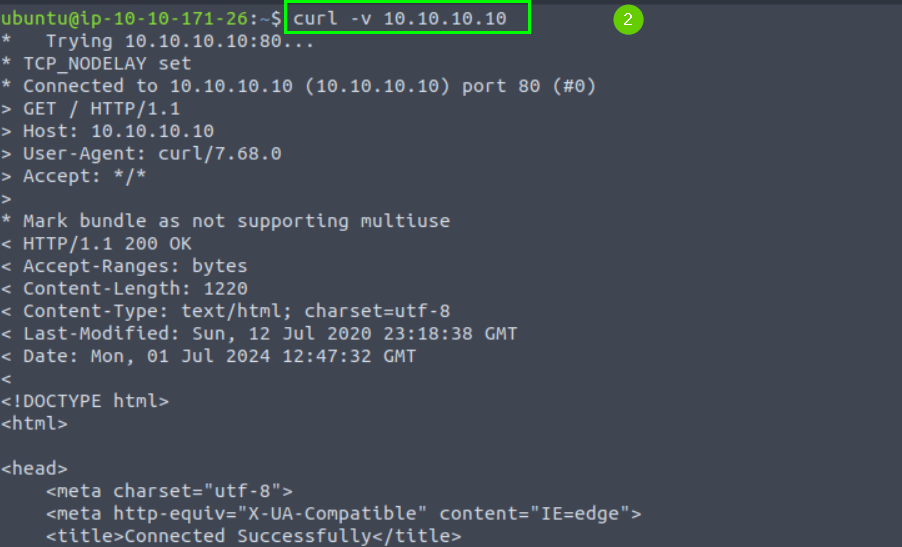
After the command in the second terminal, sniffing happens in the first terminal.
7.1. What is the number of packets with SYN bytes?
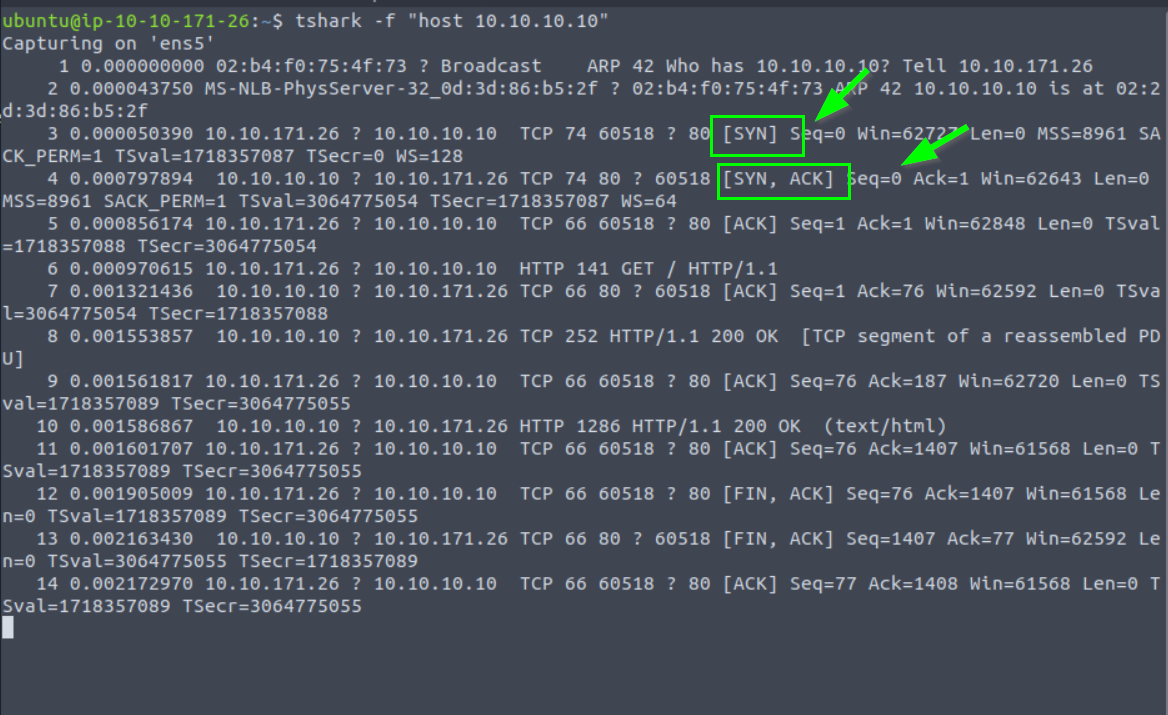
2
7.2. What is the number of packets sent to the IP address “10.10.10.10”?
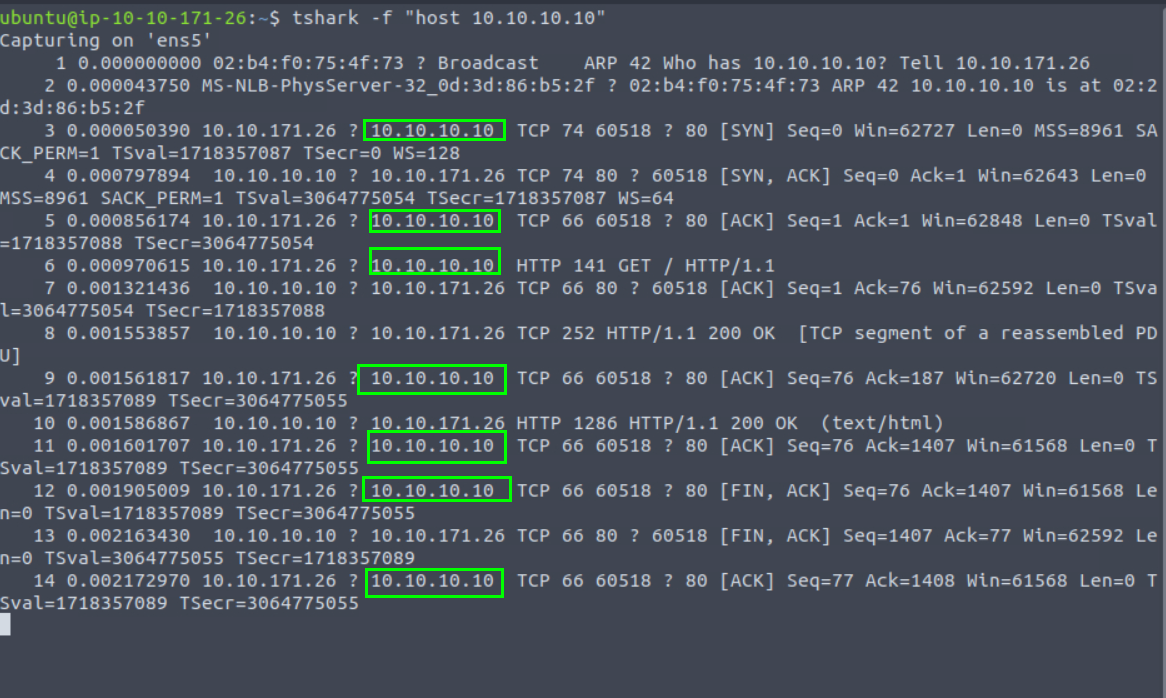
7
7.3. What is the number of packets with ACK bytes?
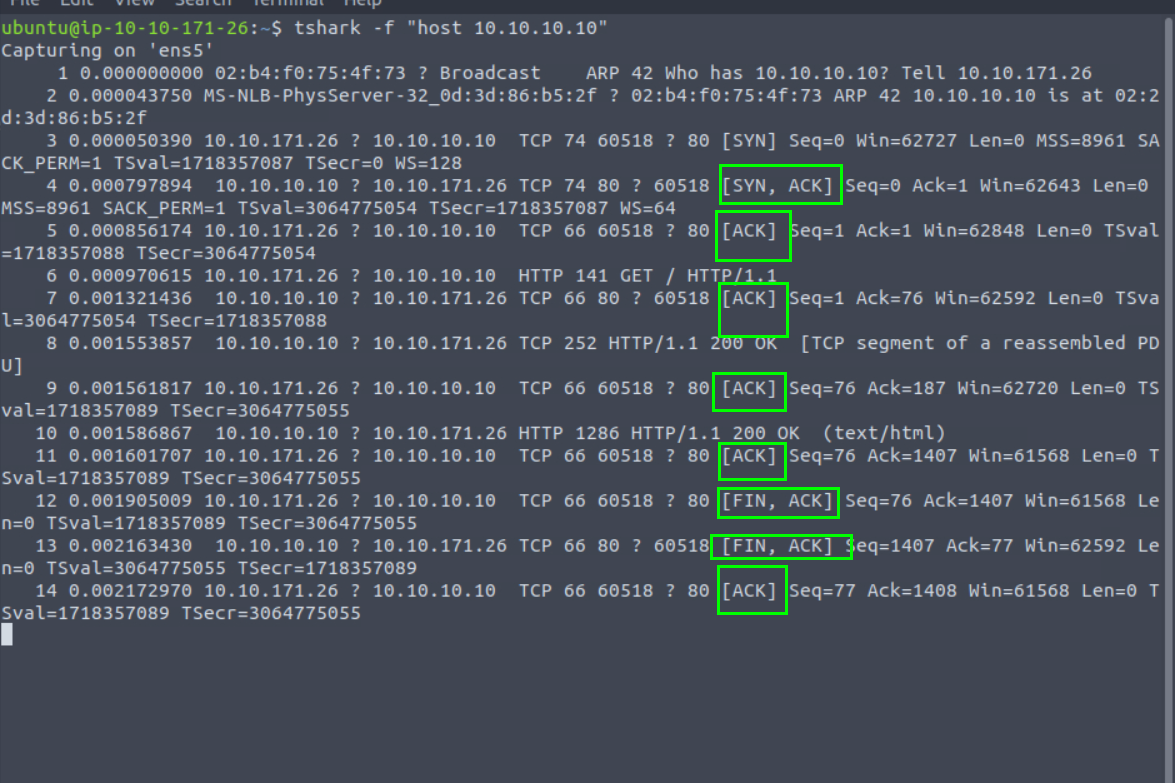
8
Task 8: TShark Fundamentals V | Packet Filtering Options: Display Filters
Use the “demo.pcapng” file to answer the questions.
8.1. What is the number of packets with a “65.208.228.223” IP address?

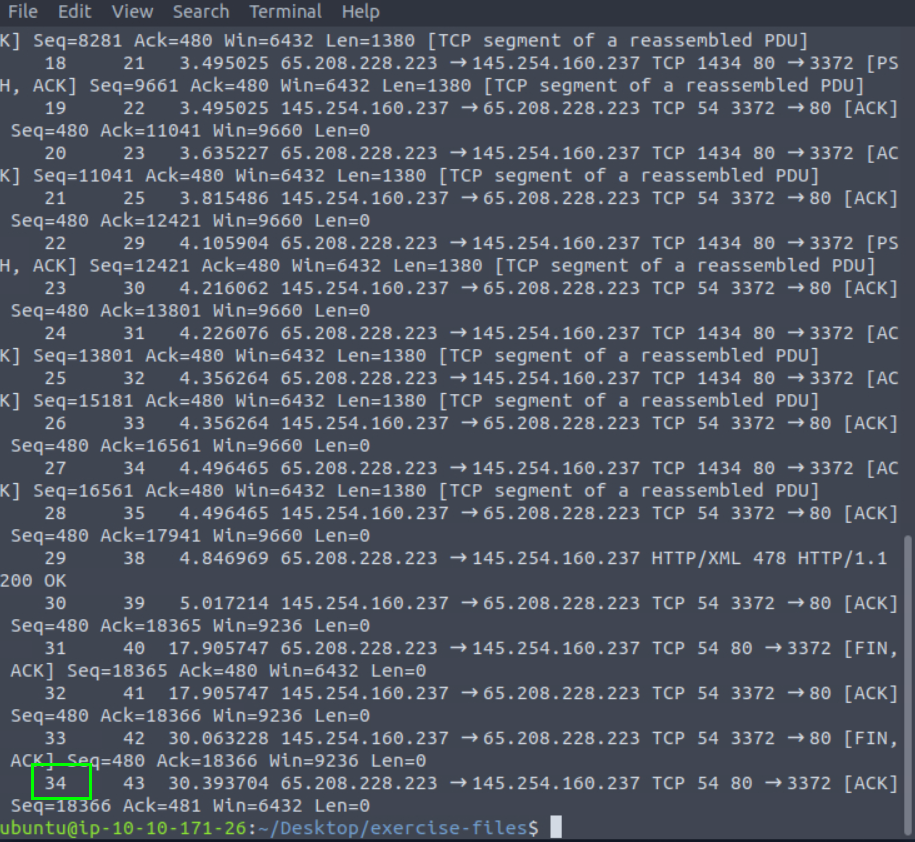
34
8.2. What is the number of packets with a “TCP port 3371”?
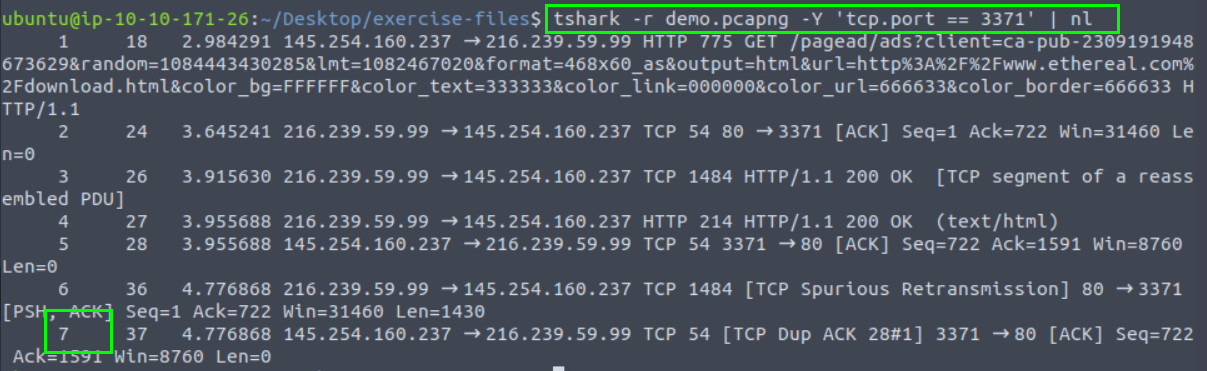
7
8.3. What is the number of packets with a “145.254.160.237” IP address as a source address?
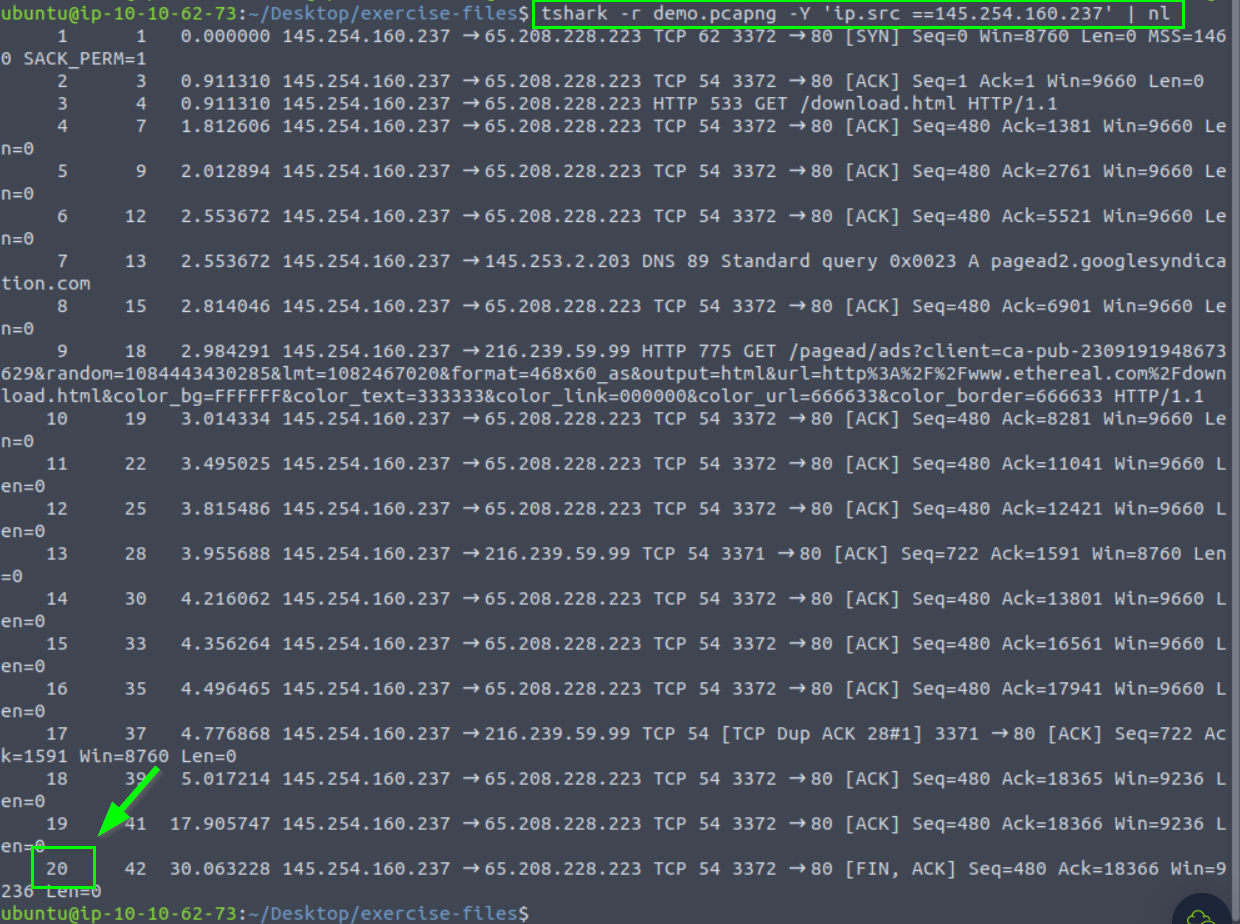
20
8.4. Rerun the previous query and look at the output.
What is the packet number of the “Duplicate” packet?

37

