The room: “Learn Network Security and Traffic Analysis foundations and take a step into probing network anomalies.”
https://tryhackme.com/room/trafficanalysisessentials
Task 2: Network Security and Network Data
2.1. Which Security Control Level covers contain creating security policies?
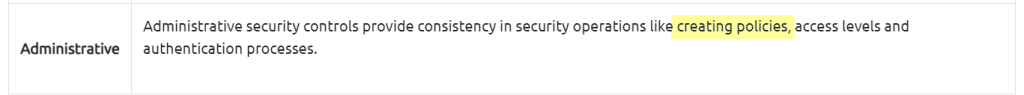
Administrative
2.2. Which Access Control element works with data metrics to manage data flow?
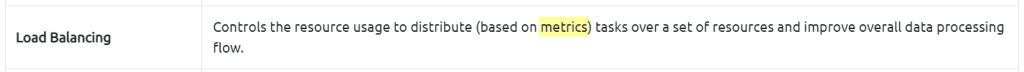
Load Balancing
2.3. Which technology helps correlate different tool outputs and data sources?

SOAR
Task 3: Traffic Analysis
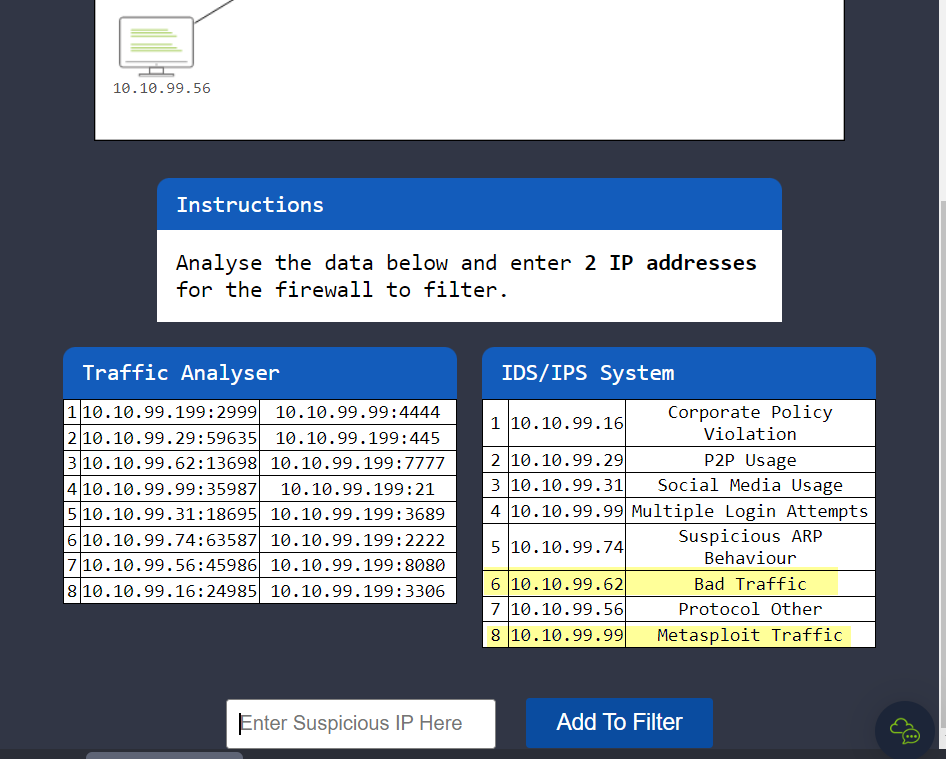
3.1. Level-1 is simulating the identification and filtering of malicious IP addresses.
What is the flag?
IPs 10.10.99.62 and 10.10.99.69 should be blocked.
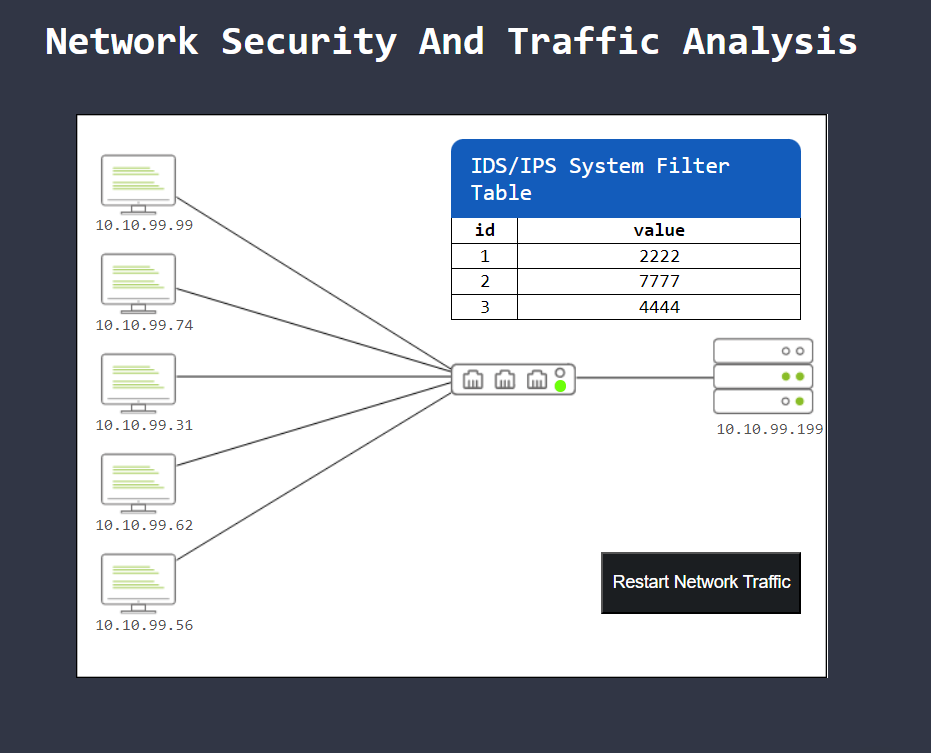
3.2. Level-2 is simulating the identification and filtering of malicious IP and Port addresses.
What is the flag?
Ports 2222, 7777, and 4444 must be blocked. These are the 3 ports that attackers use for trojans.
a

