The Room: “Learn about the security triad and common security models and principles.”
https://tryhackme.com/room/securityprinciples
Task 2: CIA
2.1. Click on “View Site” and answer the five questions. What is the flag that you obtained at the end?

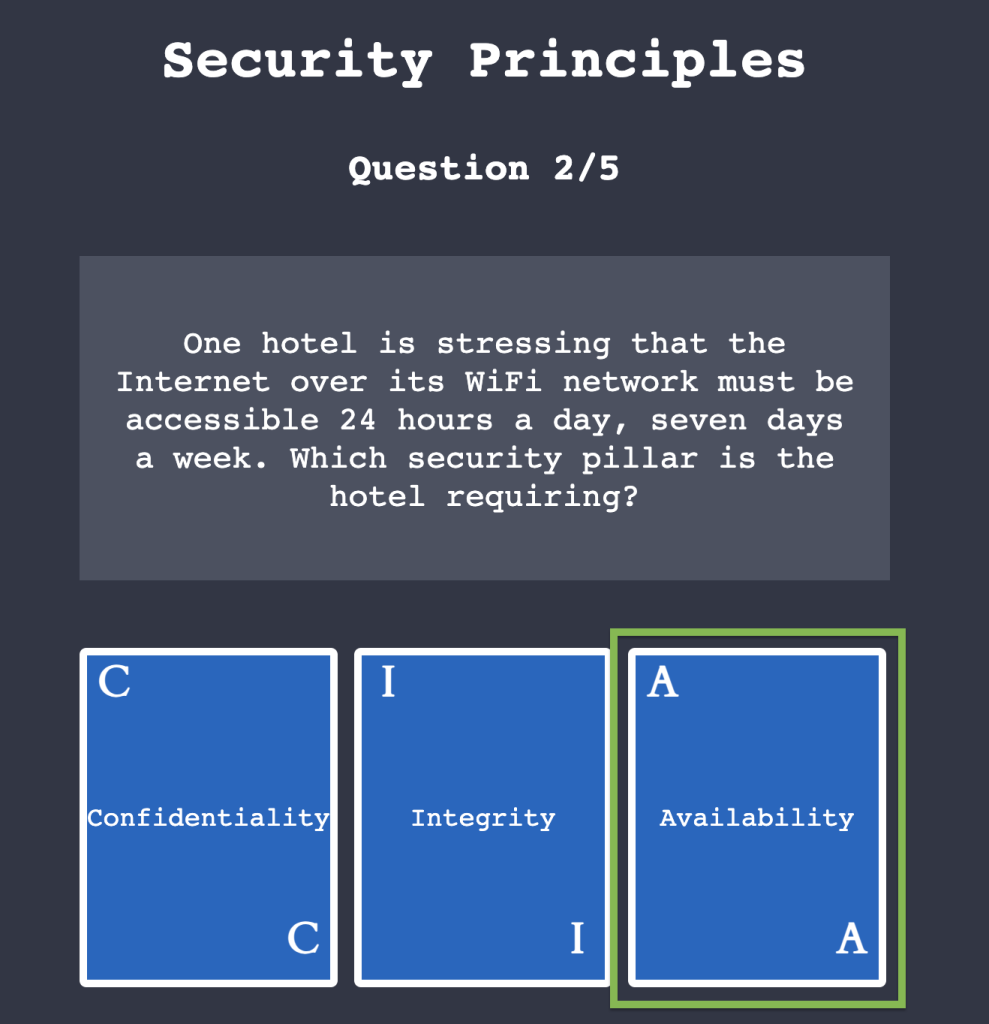

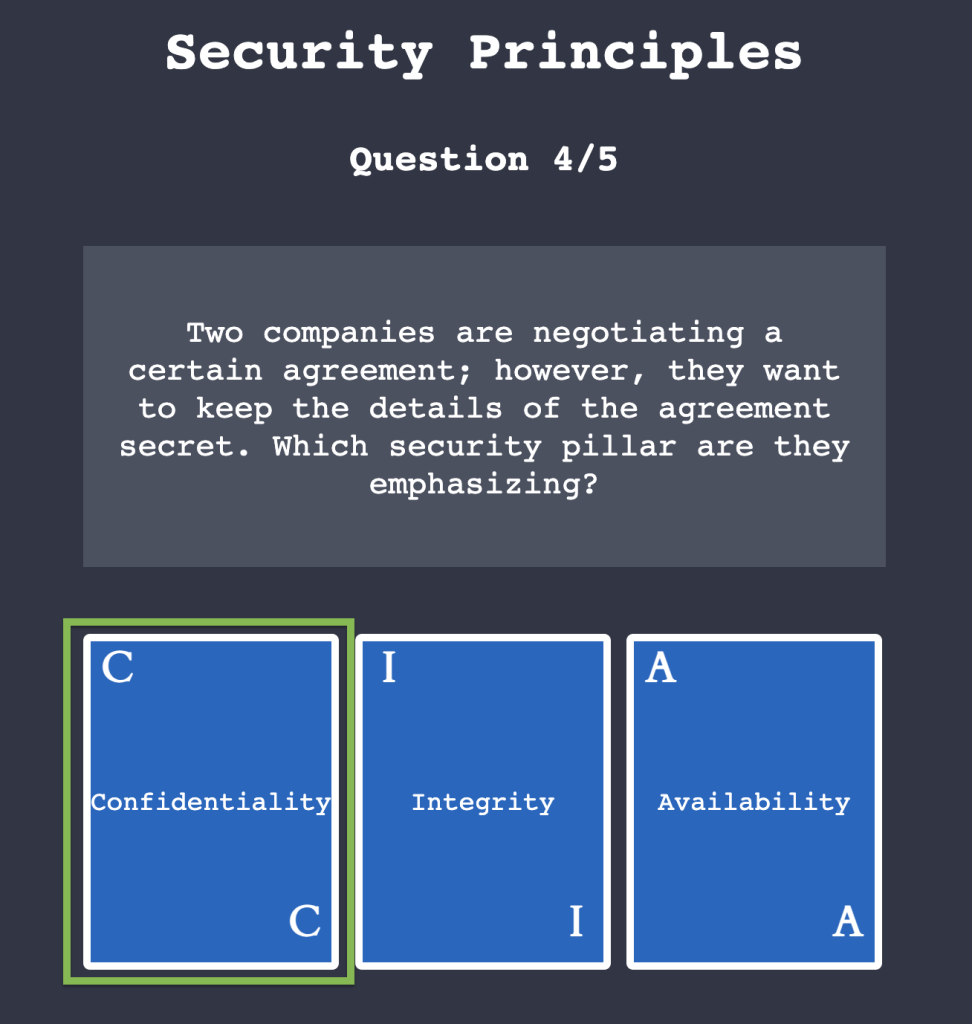
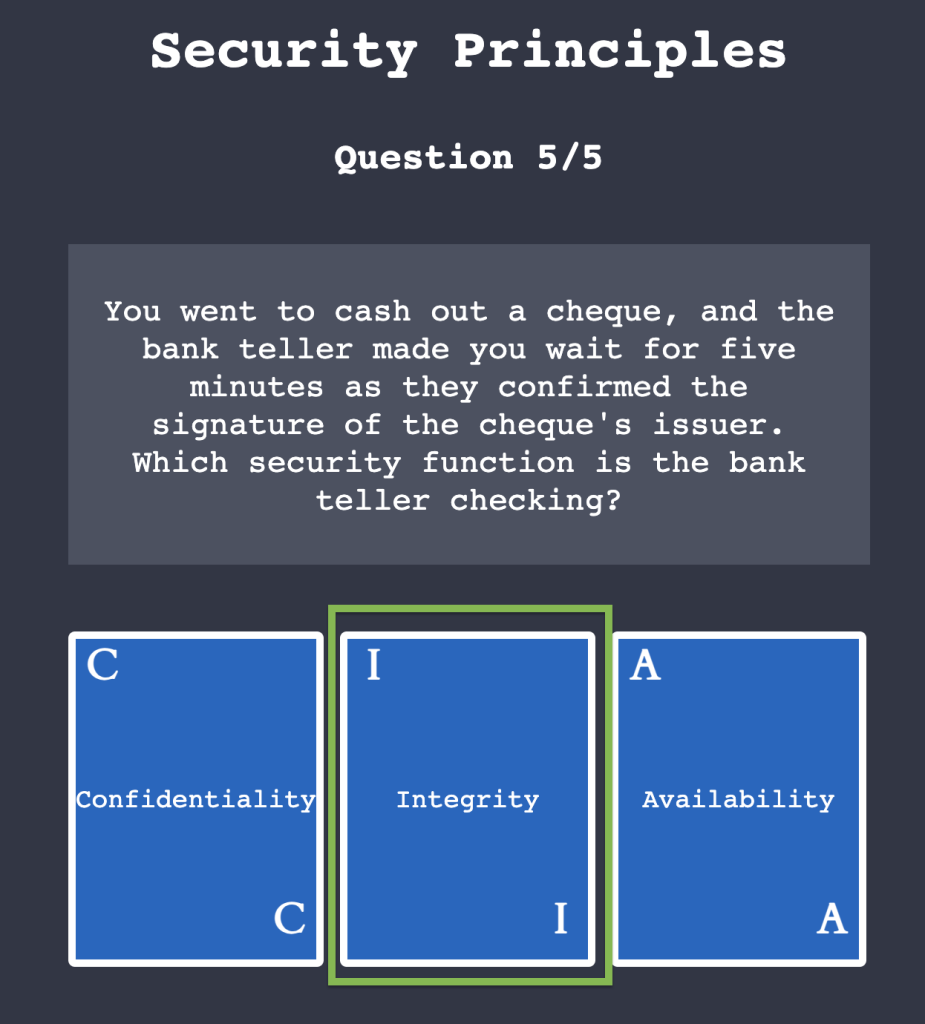
THM{CIA_TRIAD}
Task 3: DAD
3.1. The attacker managed to gain access to customer records and dumped them online. What is this attack?
Disclosure
3.2. A group of attackers were able to locate both the main and the backup power supply systems and switch them off. As a result, the whole network was shut down. What is this attack?
Destruction/Denial
Task 4: Fundamental Concepts of Security Models
4.1. Click on “View Site” and answer the four questions. What is the flag that you obtained at the end?
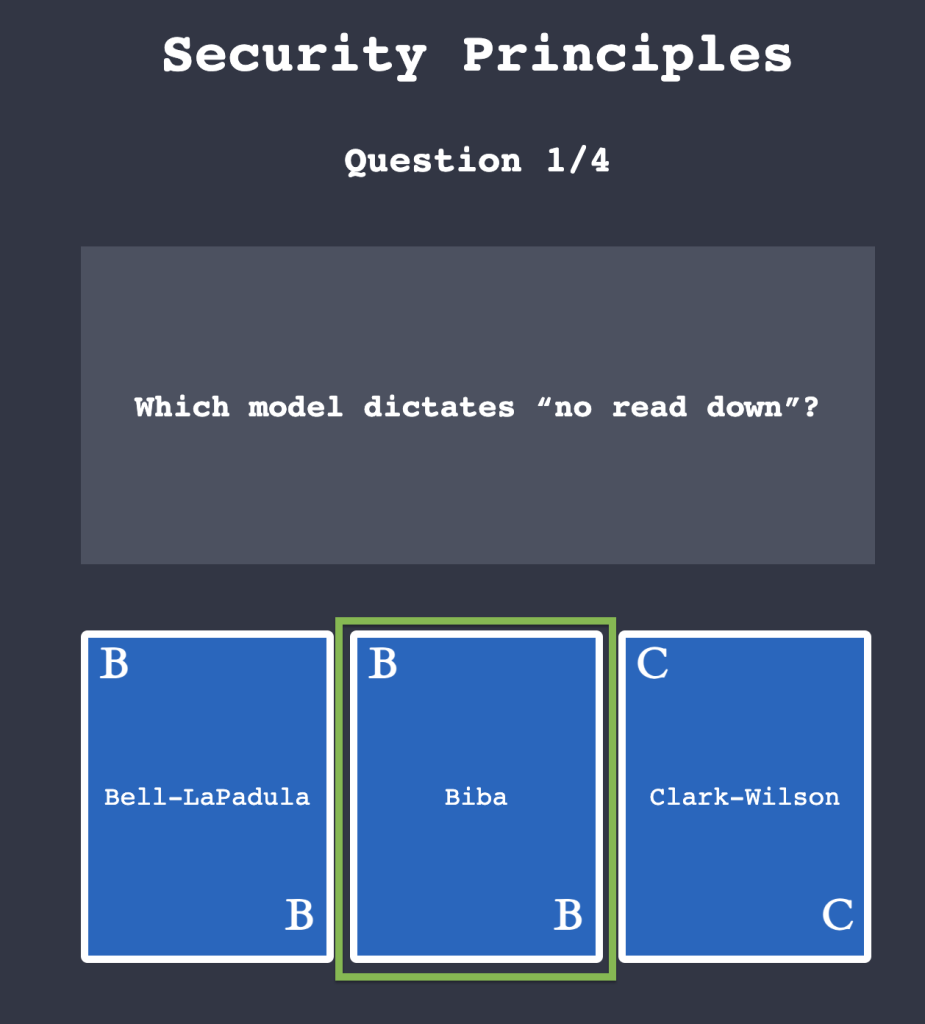
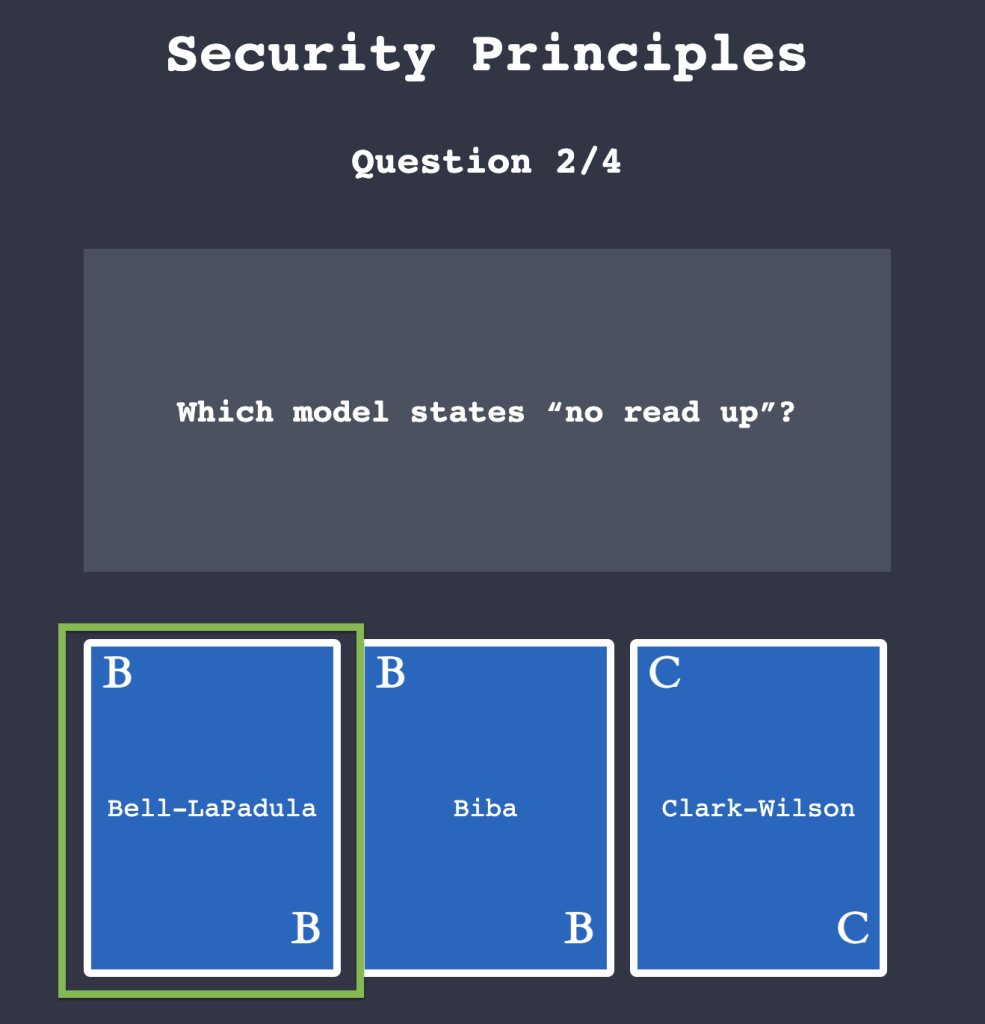
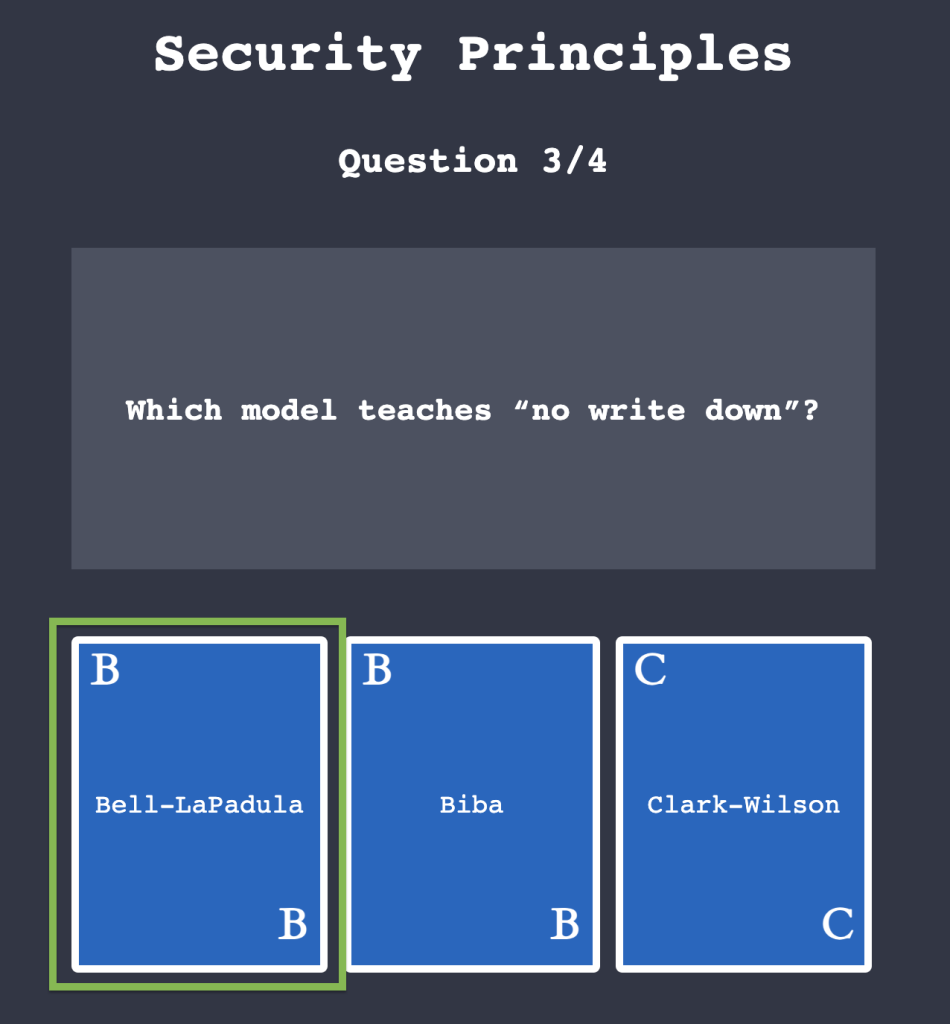
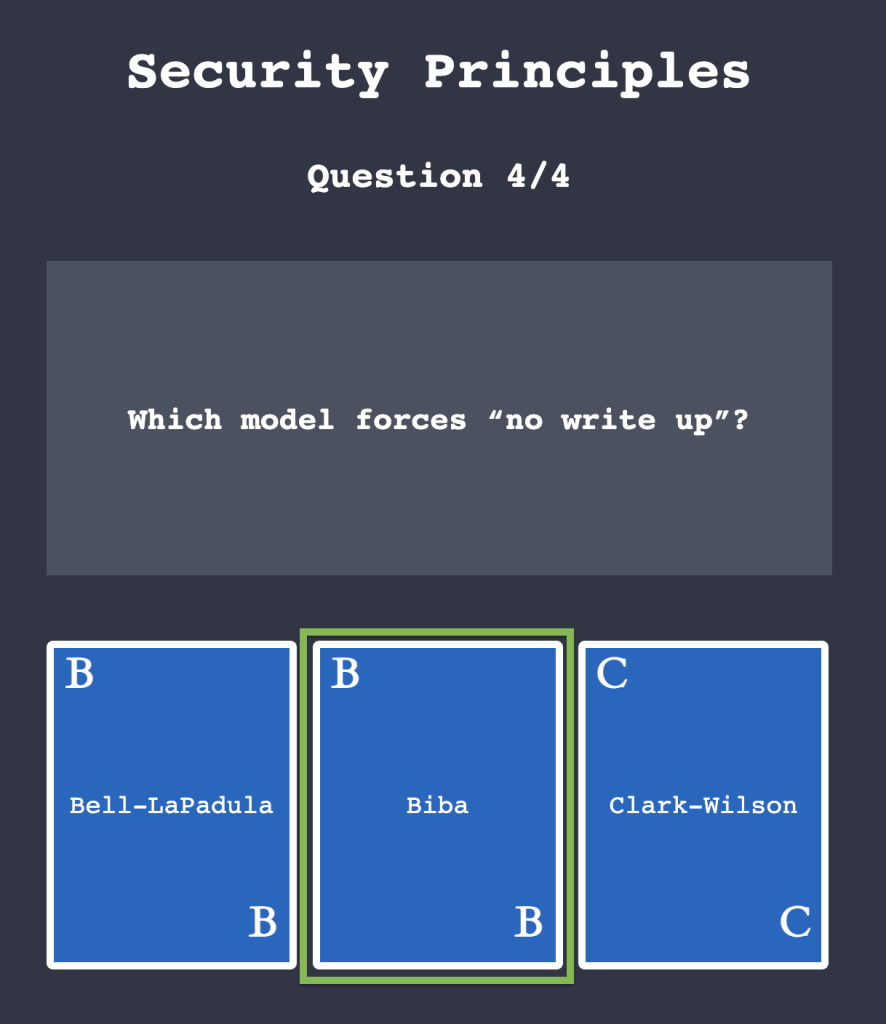
THM{SECURITY_MODELS}
Task 6: ISO/IEC 19249
6.1. Which principle are you applying when you turn off an insecure server that is not critical to the business?
2
6.2. Your company hired a new sales representative. Which principle are they applying when they tell you to give them access only to the company products and prices?
1
6.3. While reading the code of an ATM, you noticed a huge chunk of code to handle unexpected situations such as network disconnection and power failure. Which principle are they applying?
5

