Apply threat intelligence to red team engagements and adversary emulation.
Task 5: TTP Mapping
5.2. How many Command and Control techniques are employed by Carbanak?
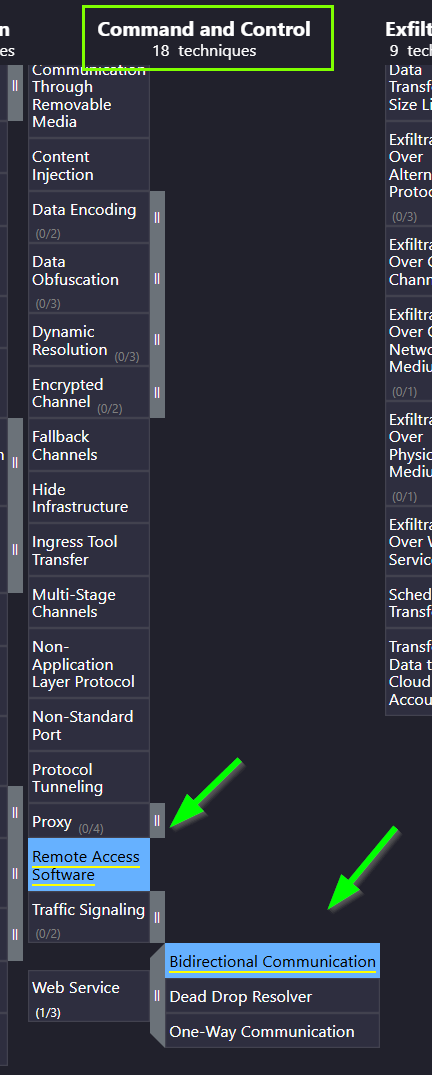
2
5.3. What signed binary did Carbanak use for defense evasion?
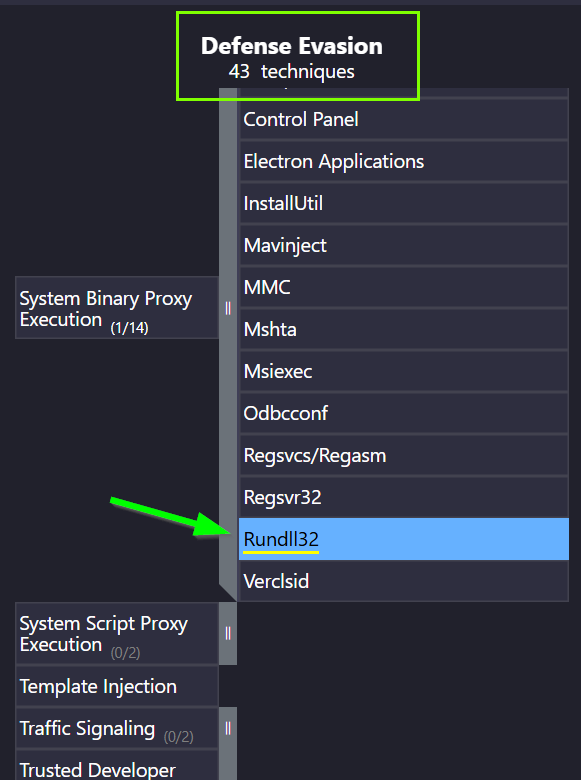
Rundll32
5.4. What Initial Access technique is employed by Carbanak?
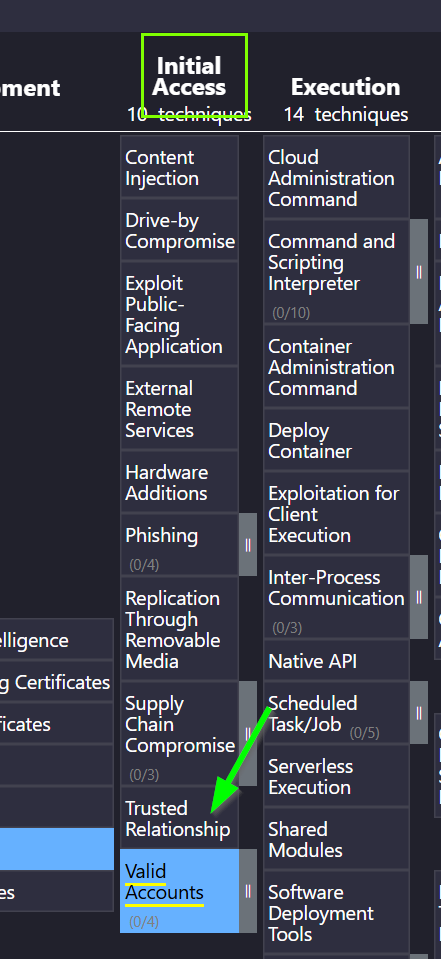
Valid Accounts
Task 7: Creating a Threat Intel Driven Campaign
7.1. Open the provided ATT&CK Navigator layer and identify matched TTPs to the cyber kill chain. Once TTPs are identified, map them to the cyber kill chain in the static site.
To complete the challenge, you must submit one technique name per kill chain section.
Once the chain is complete and you have received the flag, submit it below.
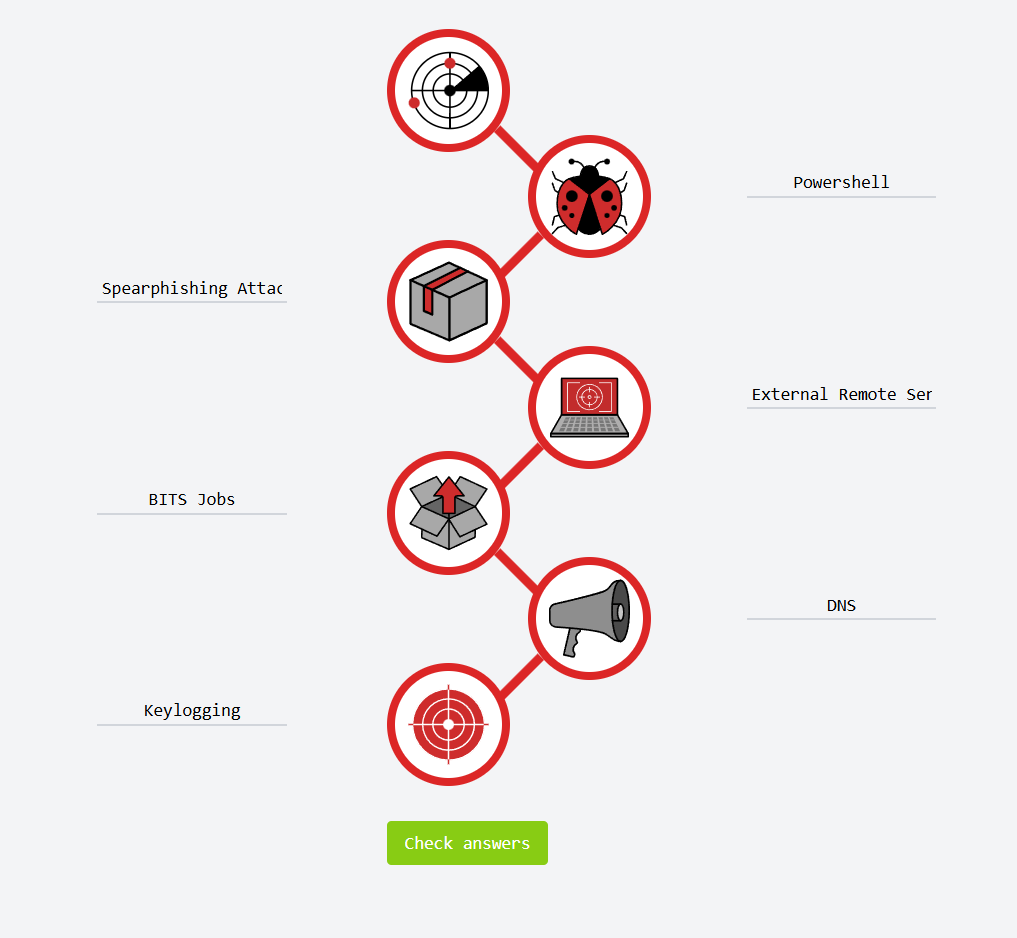
- Powershell
- Spearphishing Attachment
- External Remote Services
- BITS Jobs
- DNS
- Keylogging
7.2. Answer questions below relating to needed engagement resources.
What web shell is APT 41 known to use?
https://attack.mitre.org/groups/G0096
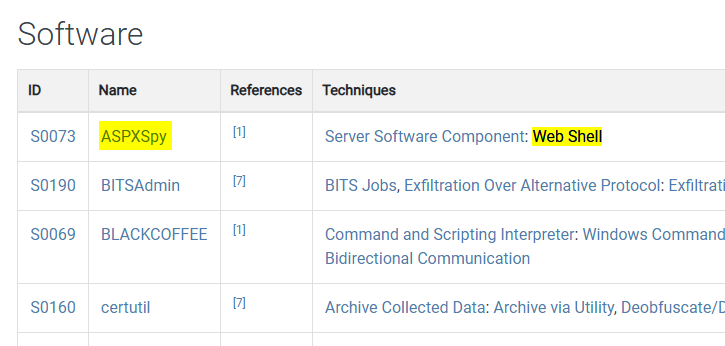
ASPXSpy
7.3. What LOLBAS (Living Off The Land Binaries and Scripts) tool does APT 41 use to aid in file transfers?
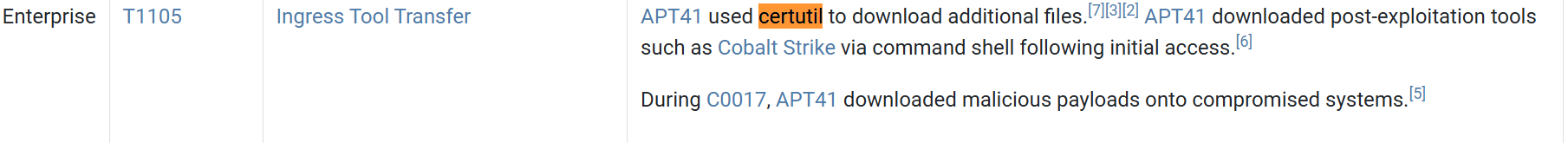
certutil
7.4. What tool does APT 41 use to mine and monitor SMS traffic?
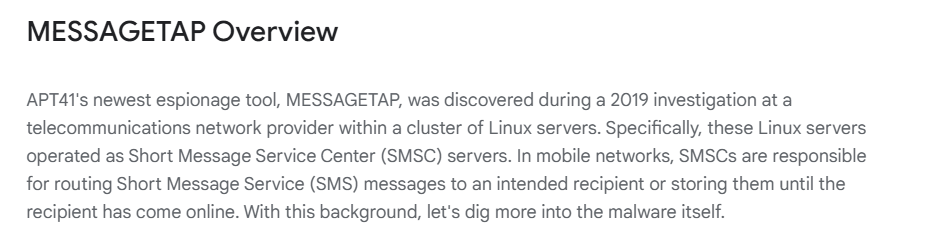
MESSAGETAP

