The room: “Learn what is the Pyramid of Pain and how to utilize this model to determine the level of difficulty it will cause for an adversary to change the indicators associated with them, and their campaign.”
Task 2: Hash Values (Trivial)
2.1. Provide the ransomware name for the hash ‘63625702e63e333f235b5025078cea1545f29b1ad42b1e46031911321779b6be’ using open-source lookup tools
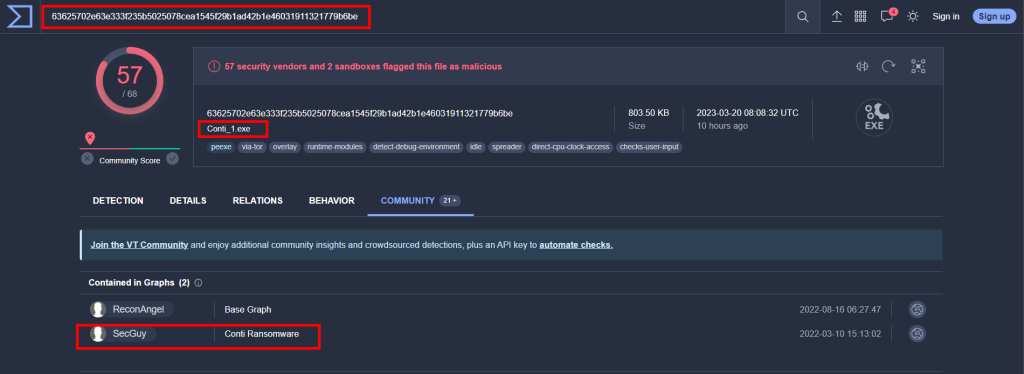
Conti
Task 3: IP Address (Easy)
3.1. What is the ASN for the third IP address observed?
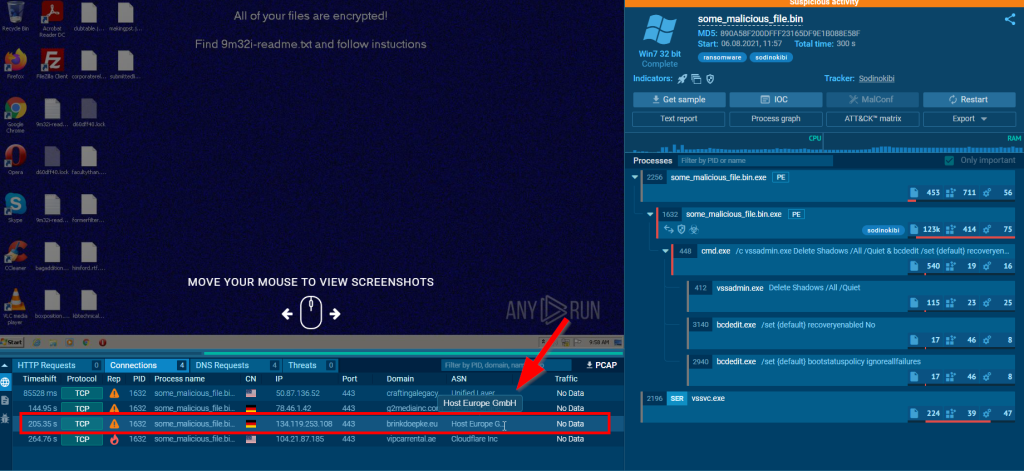
Host Europe GmbH
3.2. What is the domain name associated with the first IP address observed?
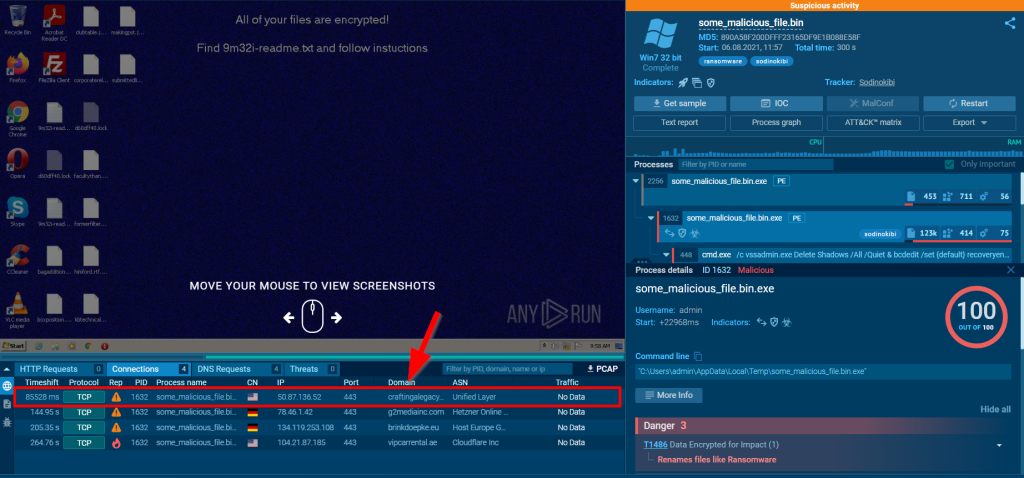
craftingalegacy.com
Task 4: Domain Names (Simple)
4.1. Go to this report on app.any.run and provide the first malicious URL request you are seeing, you will be using this report to answer the remaining questions of this task.
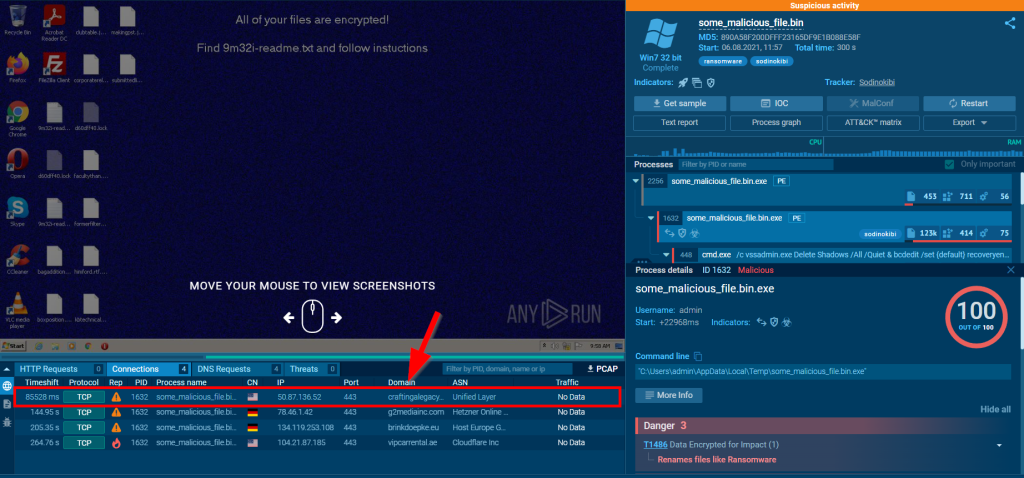
craftingalegacy.com
4.2. What term refers to an address used to access websites?
Domain Name
4.3. What type of attack uses Unicode characters in the domain name to imitate the a known domain?
Punycode attack
4.4. Provide the redirected website for the shortened URL using a preview: https://tinyurl.com/bw7t8p4u
https://tryhackme.com/
Task 5: Host Artifacts (Annoying)
5.1. What is the suspicious IP the victim machine tried to connect to in the screenshot above?
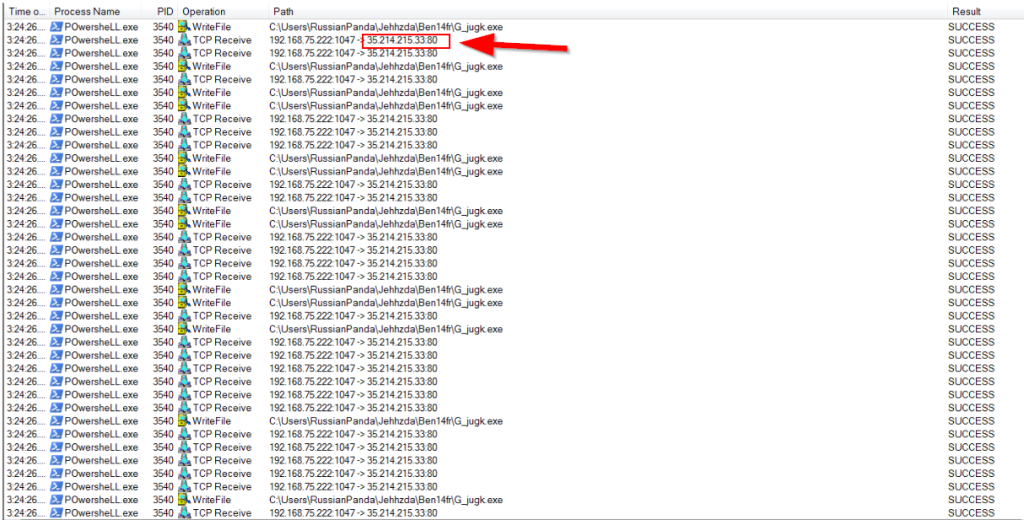
35.214.215.33
5.2. Use the tools introduced in task 2 and provide the name of the malware associated with the IP address
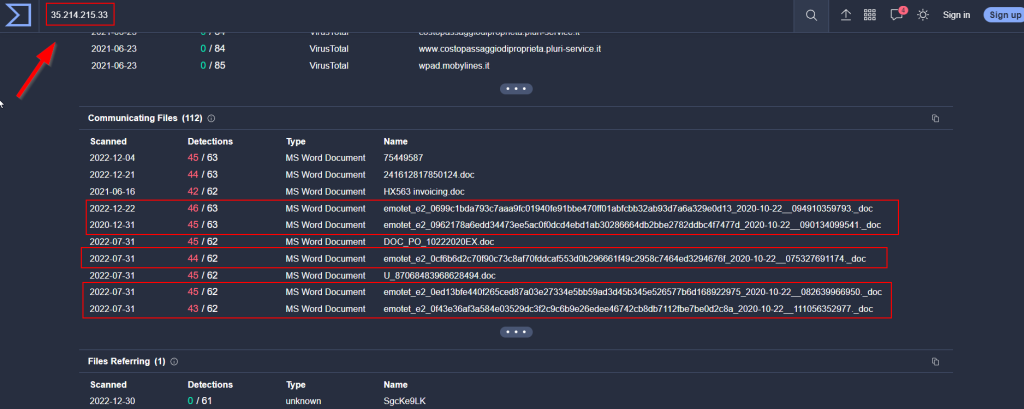
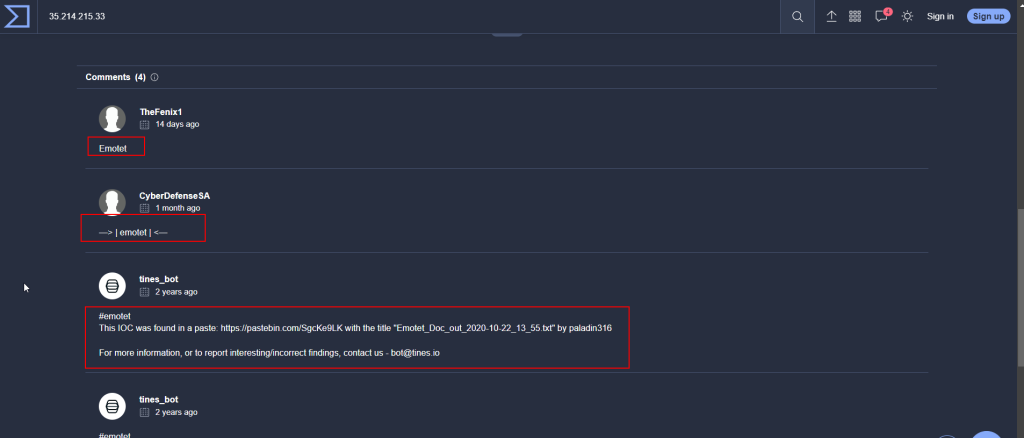
Emotet
5.3. Using your OSINT skills, what is the name of the malicious document associated with the dropped binary?
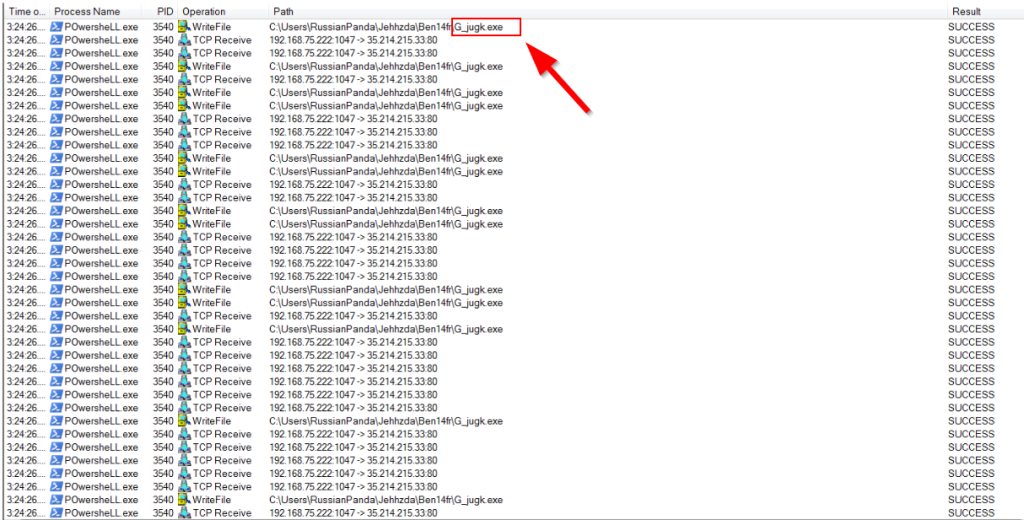
G_jugk.exe
5.4. Use your OSINT skills and provide the name of the malicious document associated with the dropped binary
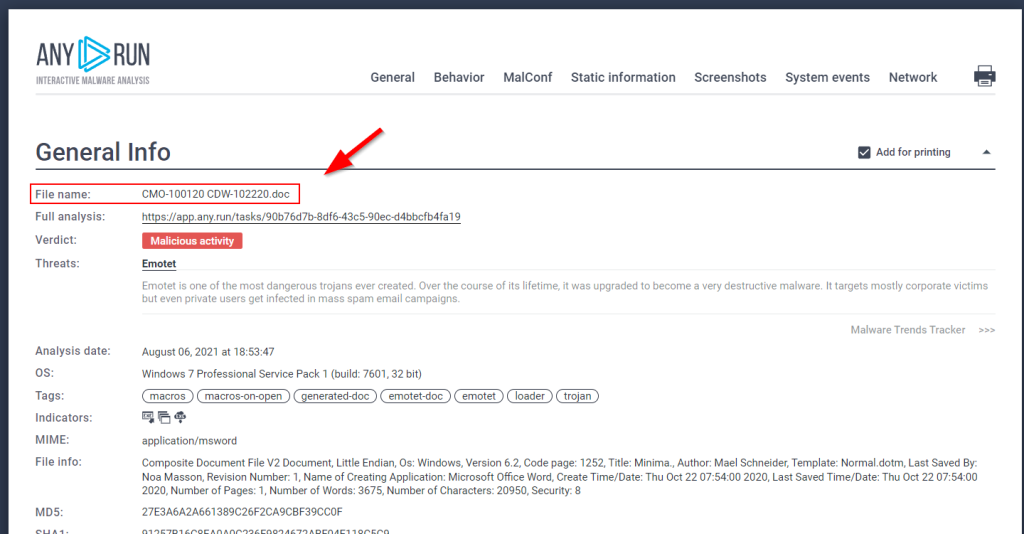
CMO-100120 CDW-102220.doc
Task 6: Network Artifacts (Annoying)
6.1. What browser uses the User-Agent string shown in the screenshot above?
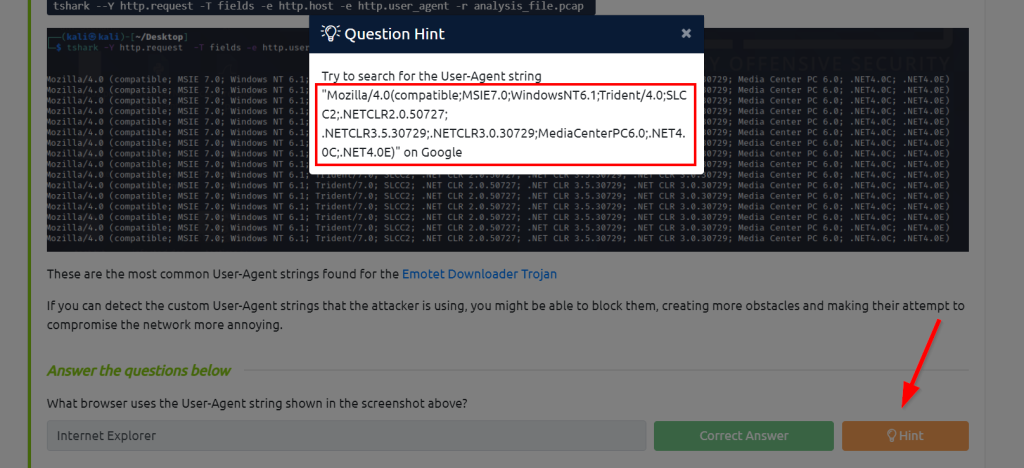
The user-agent in the question: Mozilla/4.0(compatible;MSIE7.0;WindowsNT6.1;Trident/4.0;SLCC2;.NETCLR2.0.50727; .NETCLR3.5.30729;.NETCLR3.0.30729;MediaCenterPC6.0;.NET4.0C;.NET4.0E)
A tool that can be used in browser detection with user-agent: https://gs.statcounter.com/detect
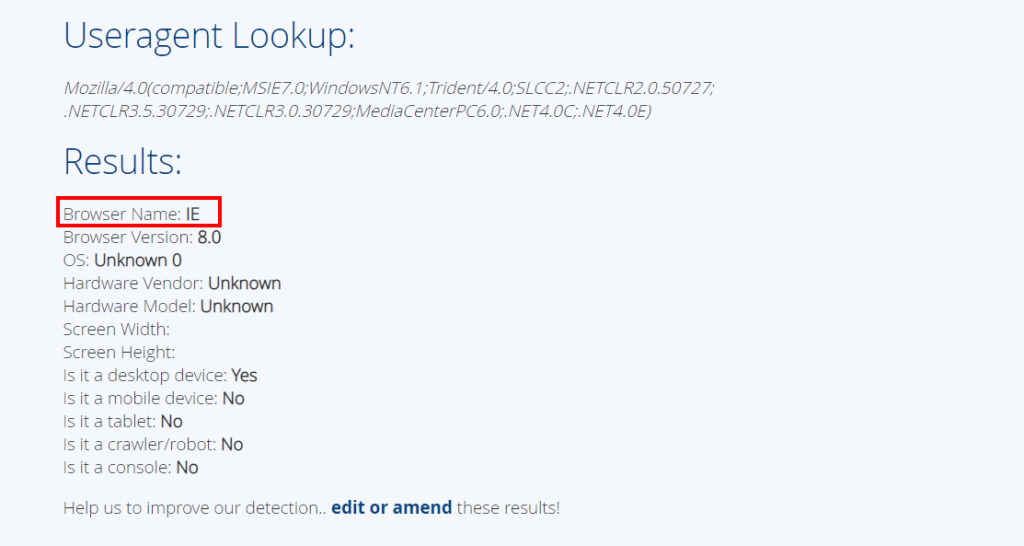
Internet Explorer
6.2. How many POST requests are in the screenshot from the pcap file?
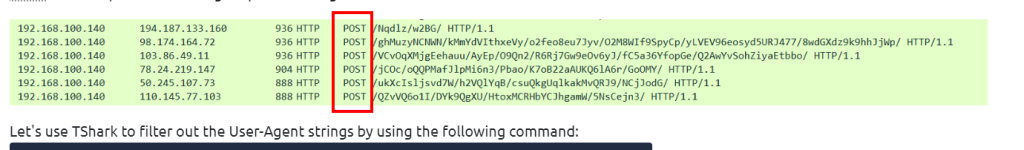
6
Task 7: Tools (Challenging)
7.1. Provide the method used to determine similarity between the files
Fuzzy hashing
7.2. Provide the alternative name for fuzzy hashes without the abbreviation
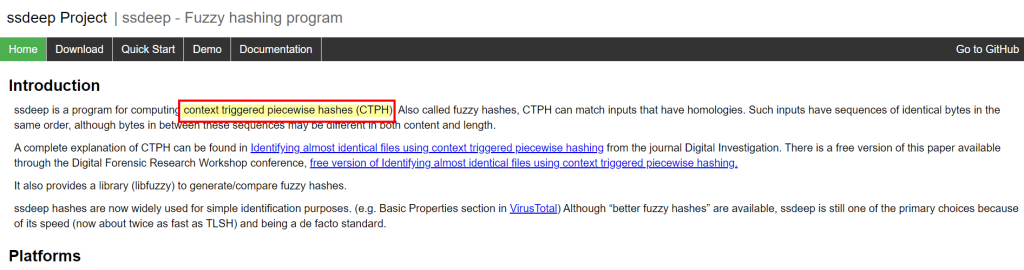
context triggered piecewise hashes
Task 8: TTPs (Tough)
8.1. Navigate to ATT&CK Matrix webpage. How many techniques fall under the Exfiltration category?
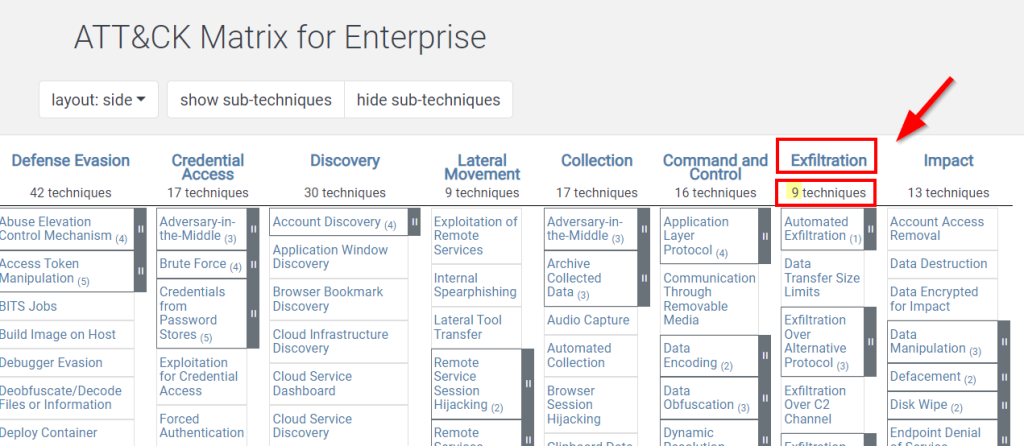
9
8.2. Chimera is a China-based hacking group that has been active since 2018. What is the name of the commercial, remote access tool they use for C2 beacons and data exfiltration?
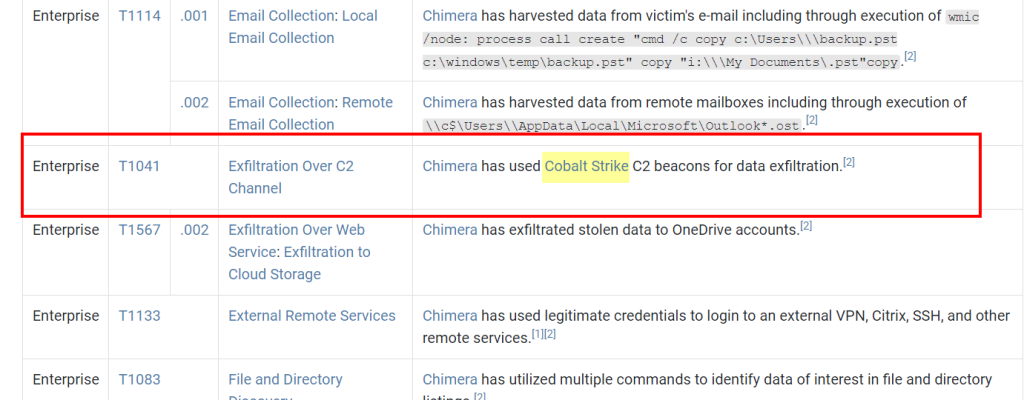
Cobalt Strike
Task 9: Practical: The Pyramid of Pain
- “The attacker has utilised these to accomplish their objective.”
➡️ Tools
- “The attackers plans and objectives.”
➡️ TTPs (Tactics, Techniques & Procedures)
- “These signatures can be used to attribute payloads and artefacts to an actor.”
➡️ File Hashes
- “An attacker has purchased this and used it in a typo-squatting campaign.”
➡️ Domain Names
- “These addresses can be used to identify the infrastructure an attacker is using for their campaign.”
➡️ IP Addresses
- “These artefacts can present themselves as C2 traffic for example.”
➡️ Network/Host Artifacts
a

