The room: we will look at various tools that will aid us in analyzing phishing emails.
Task 3: Email header analysis
3.1. What is the official site name of the bank that capitai-one[.]com tried to resemble?
Generally, phishing domains similar to the name of the bank are preferred in phishing domains. For this reason, we google the “capitai-one” part of the capitai-one[.]com domain.
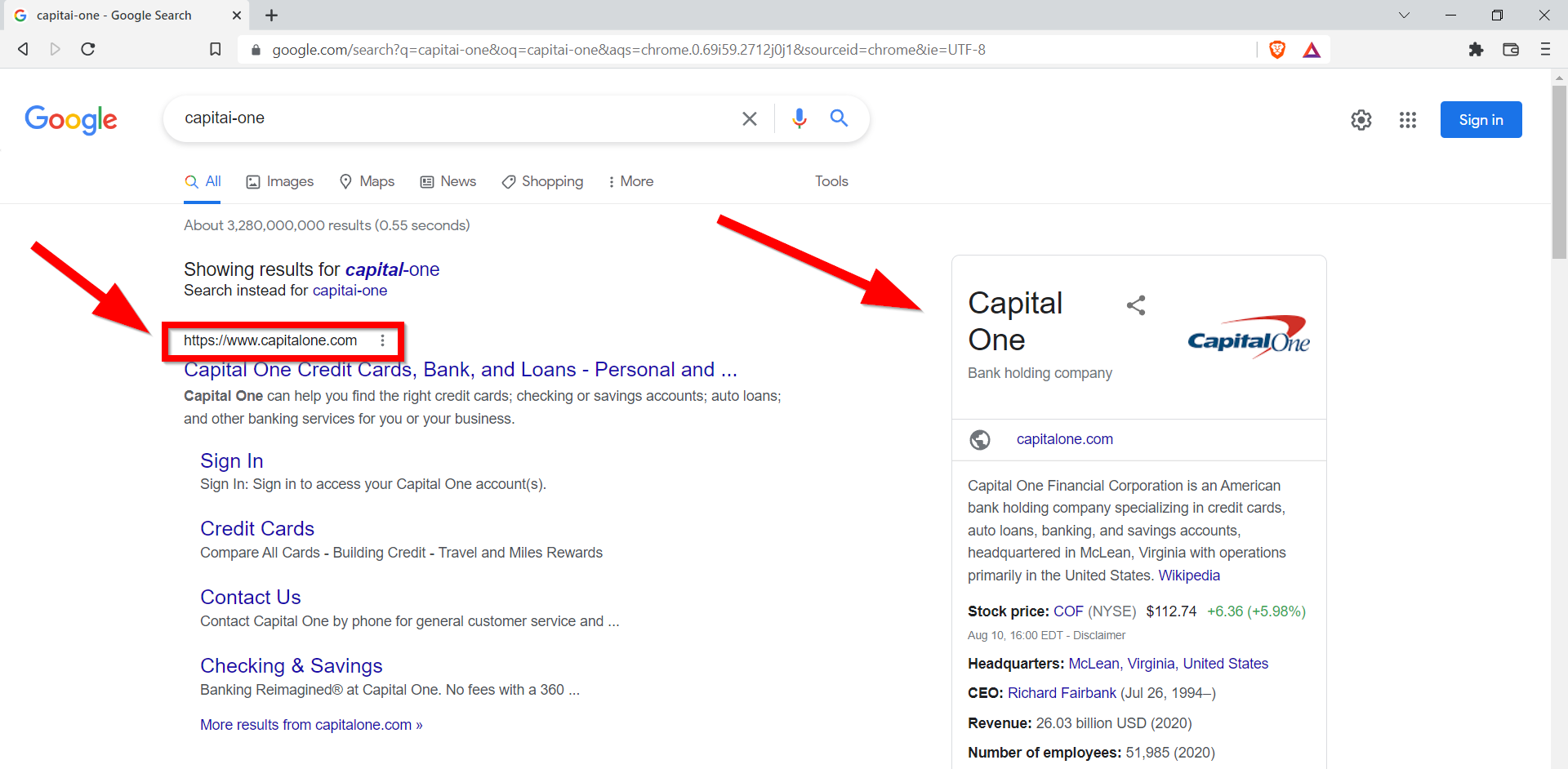
capitalone.com
Task 4: Email body analysis
4.1. How can you manually get the location of a hyperlink?
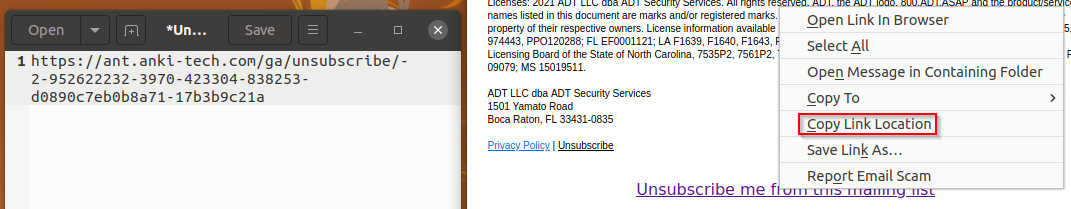
Copy Link Location
Task 6: Email body analysis
6.1. Look at the Strings output. What is the name of the EXE file?
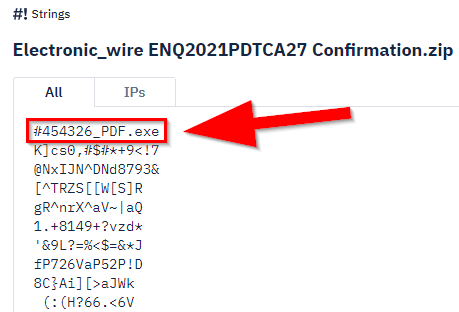
#454326_PDF.exe
Task 7: Phishing Case 1
We need to review the Phish3Case1.eml file given to us on the machine and solve the questions. Firstly we open the file in app.phishtool.com. This tool will make it easier for us to review your email.
We must be a member of the system.
We upload the file from the Analysis section with one of the specified extensions.
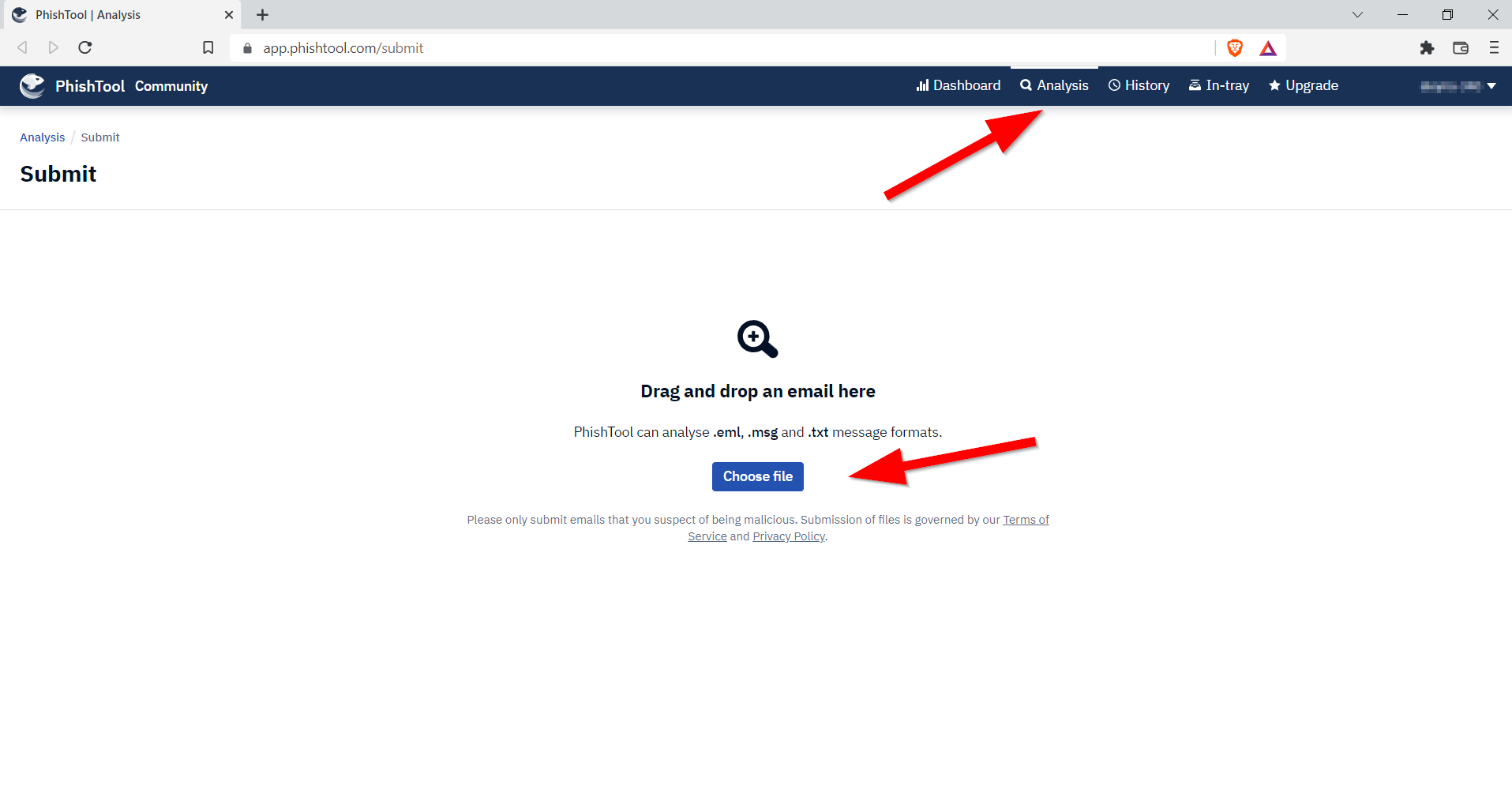
A detailed analytics page appears about our email. We can easily answer questions on this page.
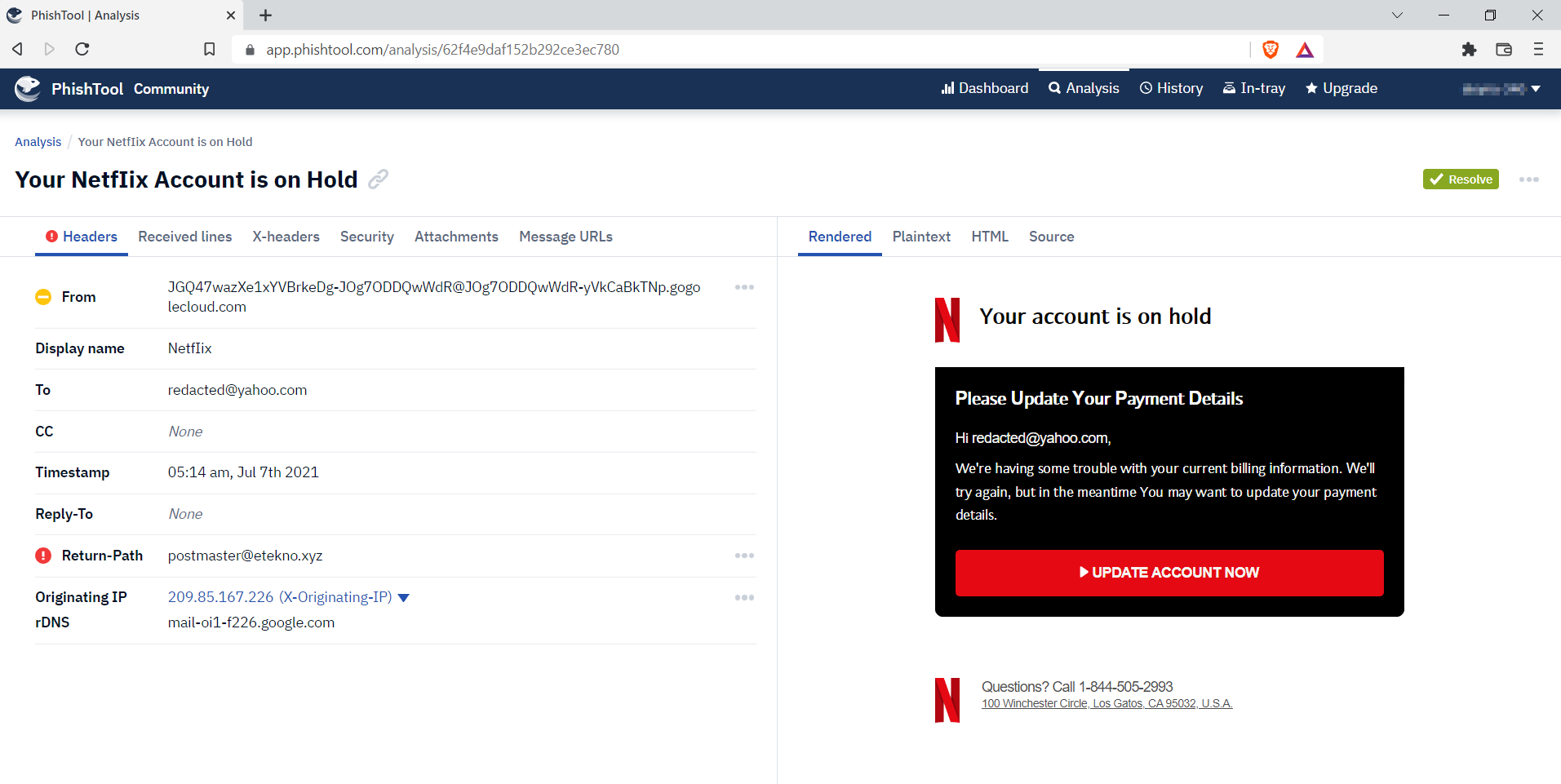
7.1. What brand was this email tailored to impersonate?
Netflix
7.2. What is the From email address?
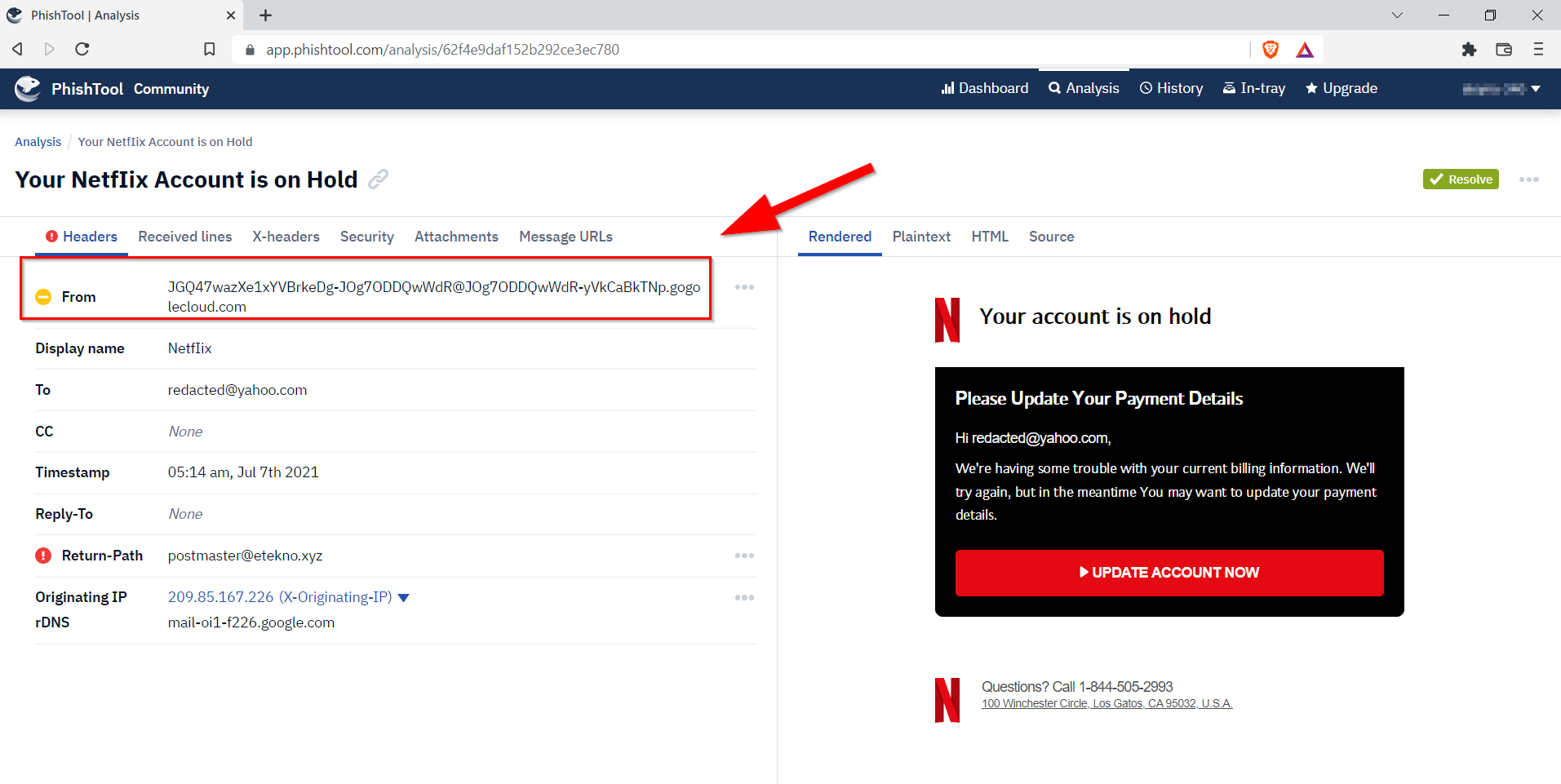
JGQ47wazXe1xYVBrkeDg-JOg7ODDQwWdR@JOg7ODDQwWdR-yVkCaBkTNp.gogolecloud.com
7.3. What is the originating IP? Defang the IP address.
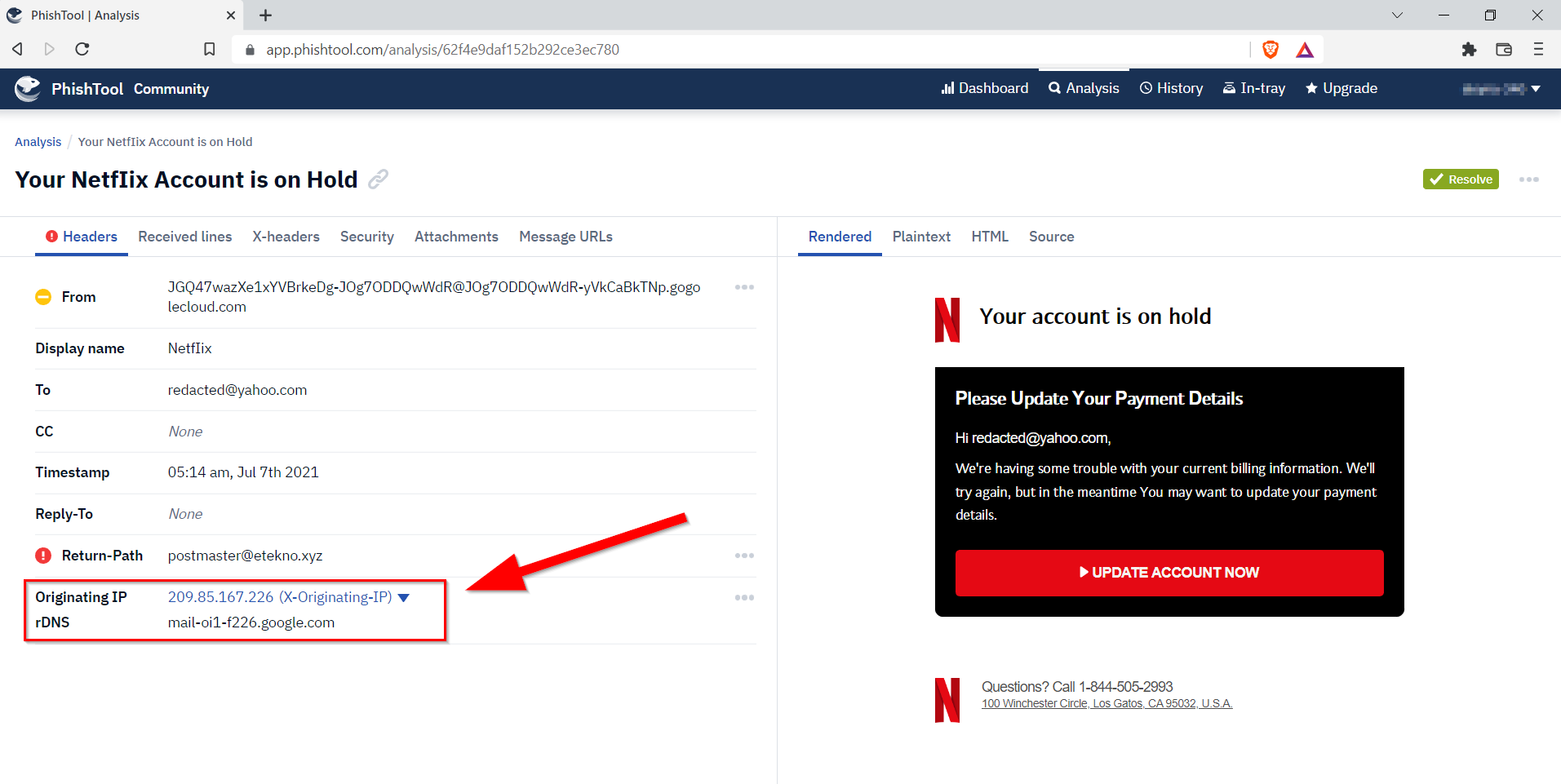
209[.]85[.]167[.]226
7.4. From what you can gather, what do you think will be a domain of interest? Defang the domain.
Return-Path defines how and where bounced emails will be processed. For this reason, the domain in the email address is the requested domain.
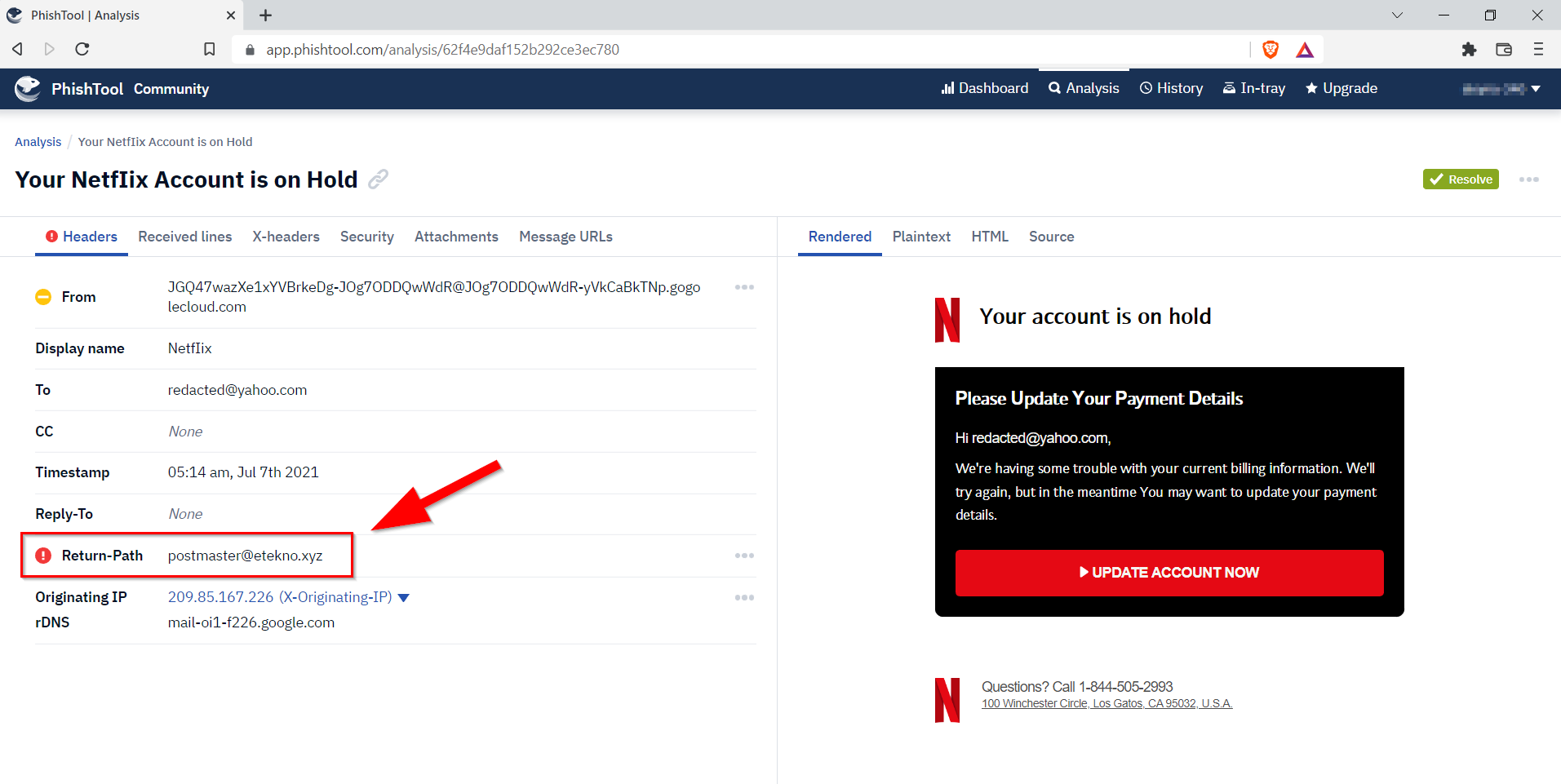
etekno[.]xyz
7.5. What is the shortened URL? Defang the URL.
Another feature PhishTool offers is that if there is a URL in the email, it provides us with information about this URL. This way, we don’t need to open a URL.
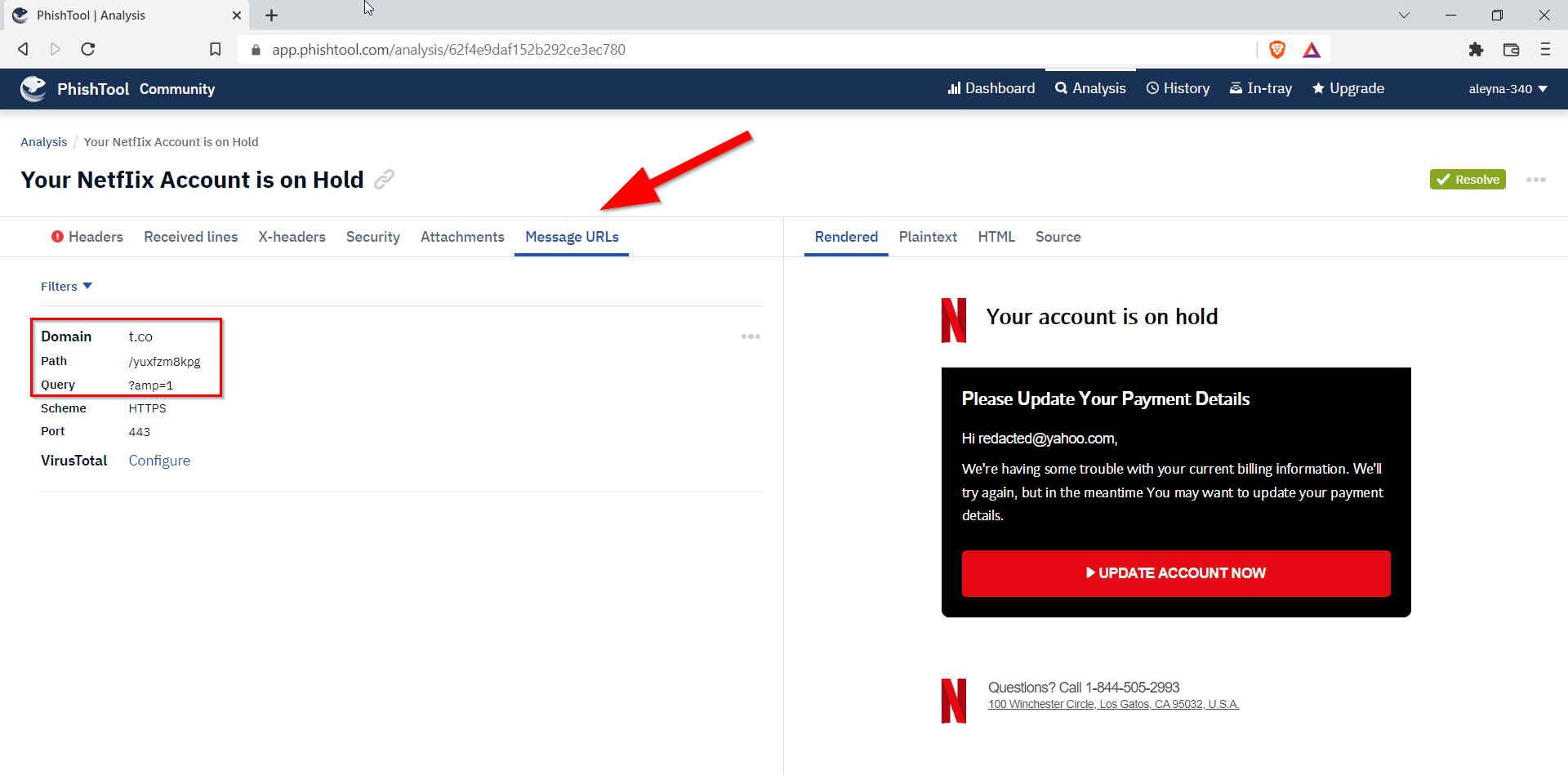
hxxps[://]t[.]co/yuxfZm8KPg?amp=1
Task 8: Phishing Case 2
We will answer the questions according to the any.run link given to us.
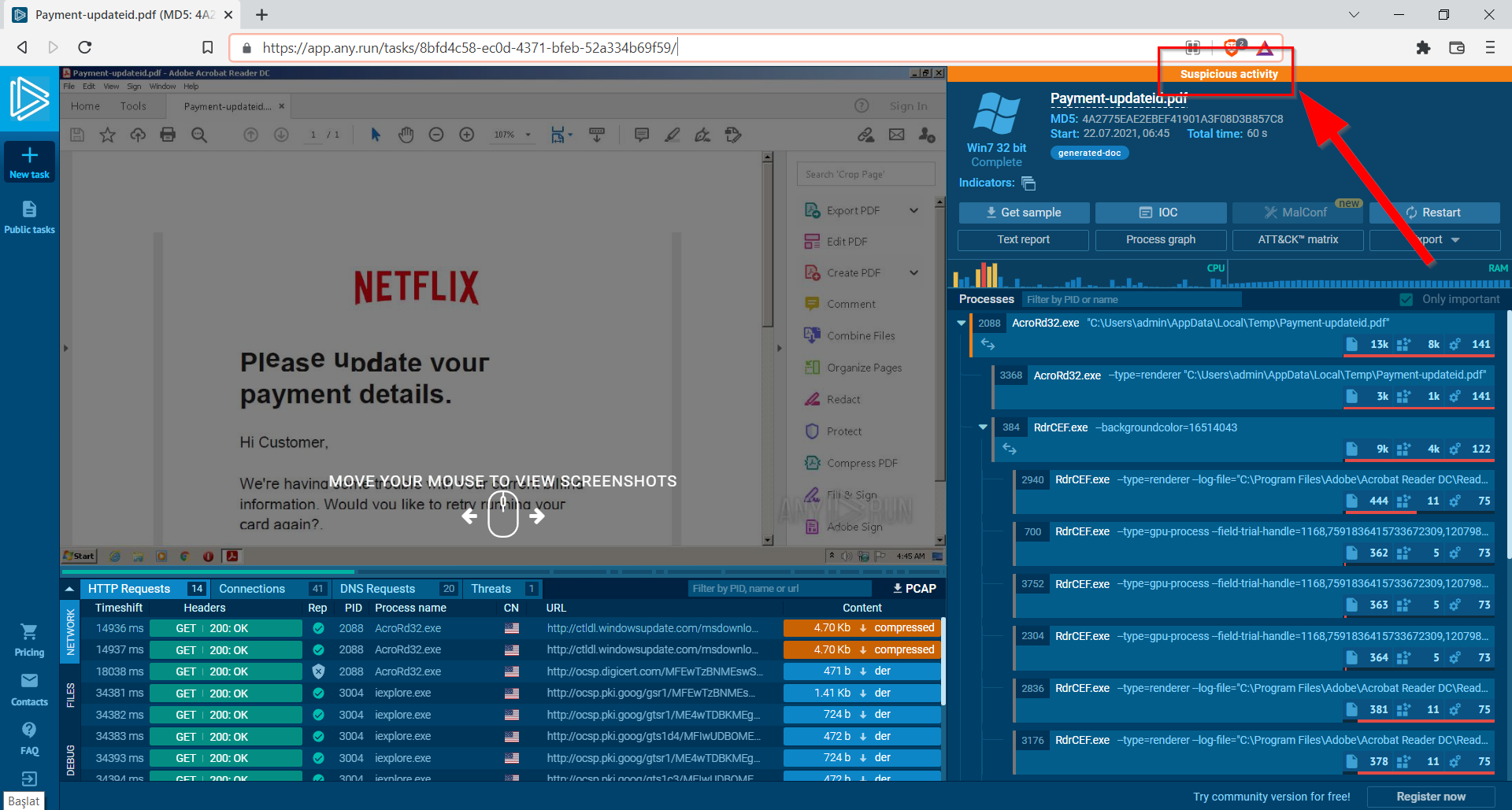
8.1. What does AnyRun classify this email as?
Suspicious activity
8.2. What is the name of the PDF file?
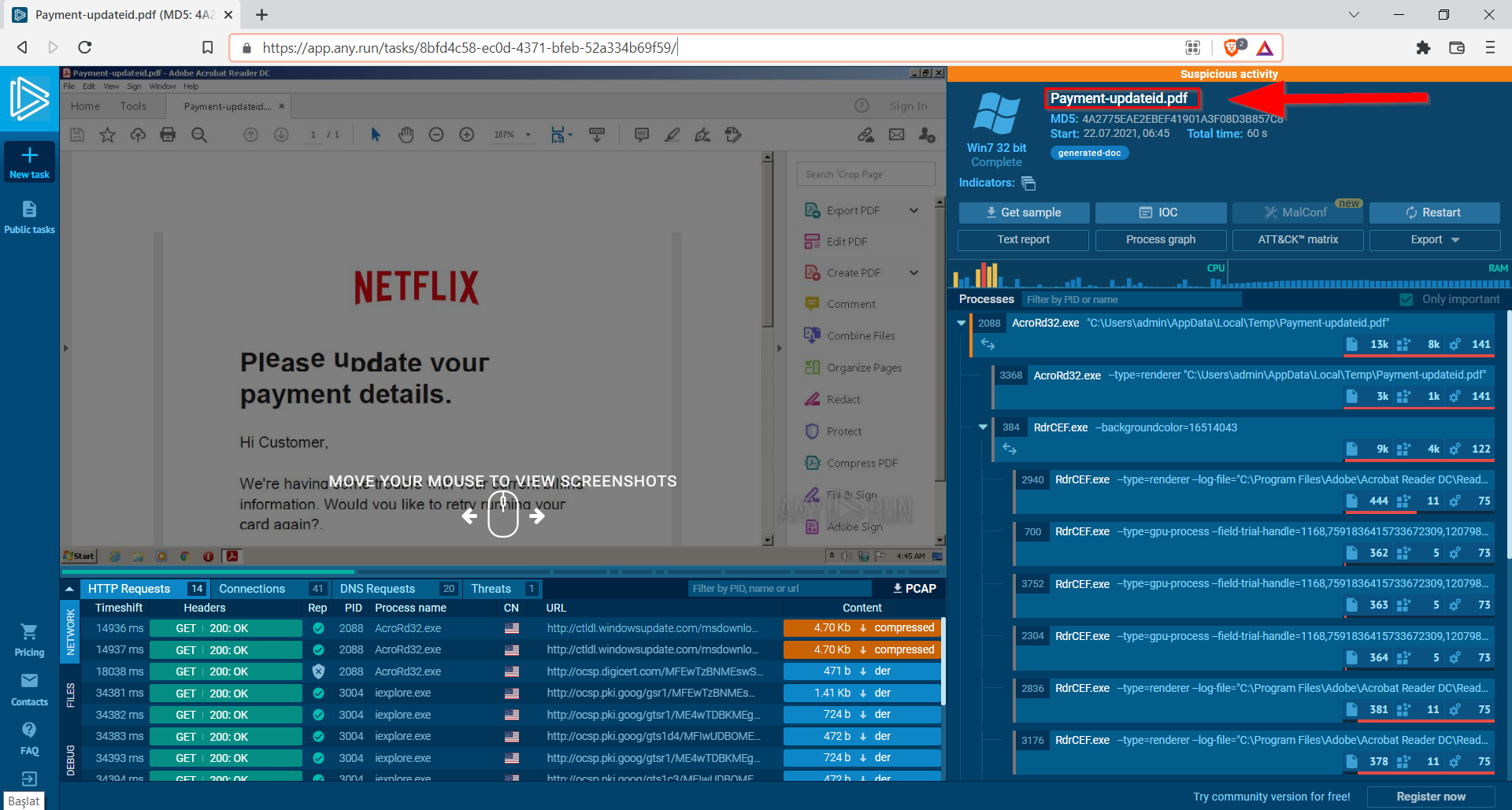
Payment-updateid.pdf
8.3. What is the SHA 256 hash for the PDF file?
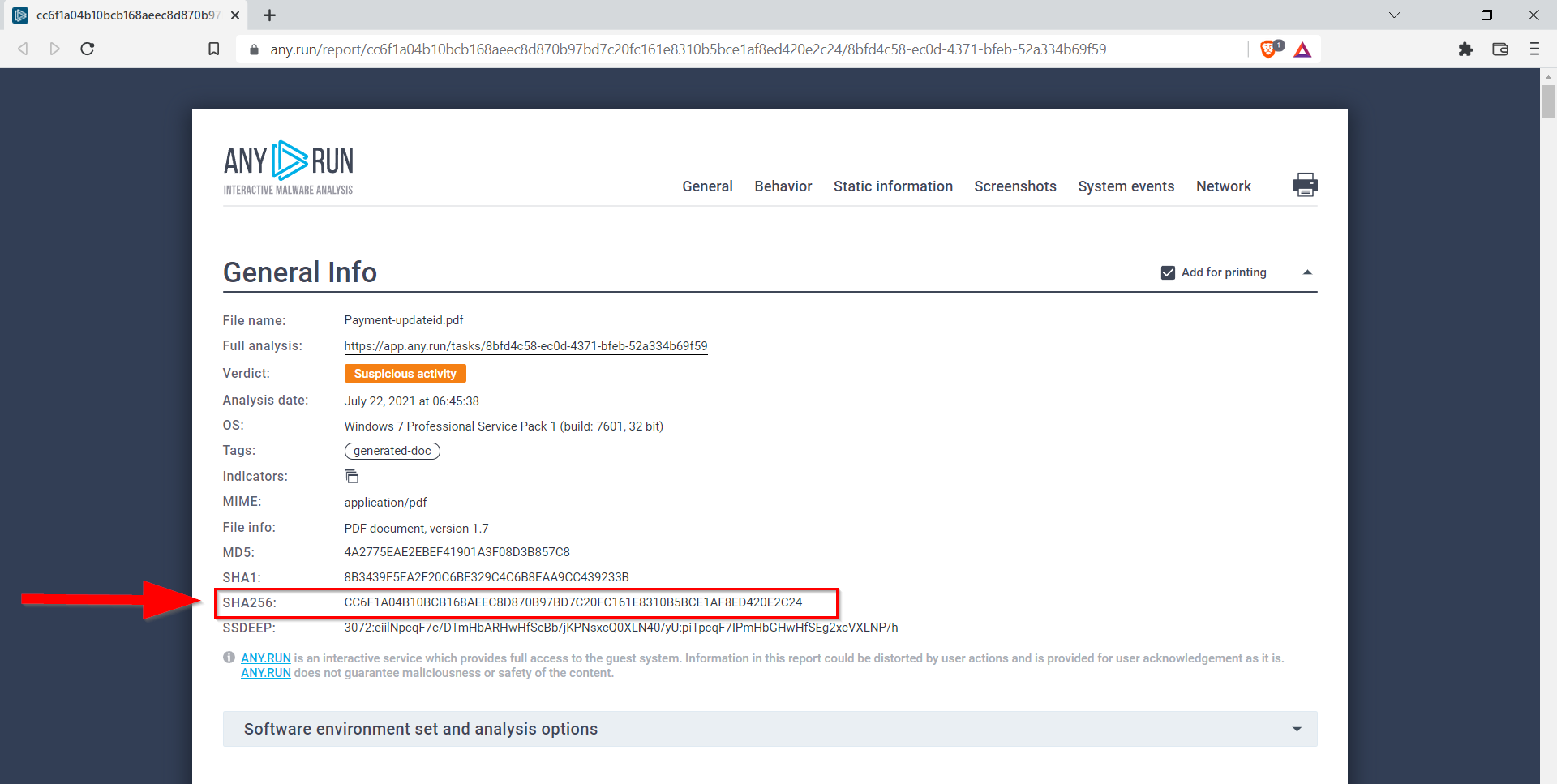
CC6F1A04B10BCB168AEEC8D870B97BD7C20FC161E8310B5BCE1AF8ED420E2C24
8.4. What two IP addresses are classified as malicious? Defang the IP addresses. (answer: IP_ADDR,IP_ADDR)
We open the document in the “text report” section.
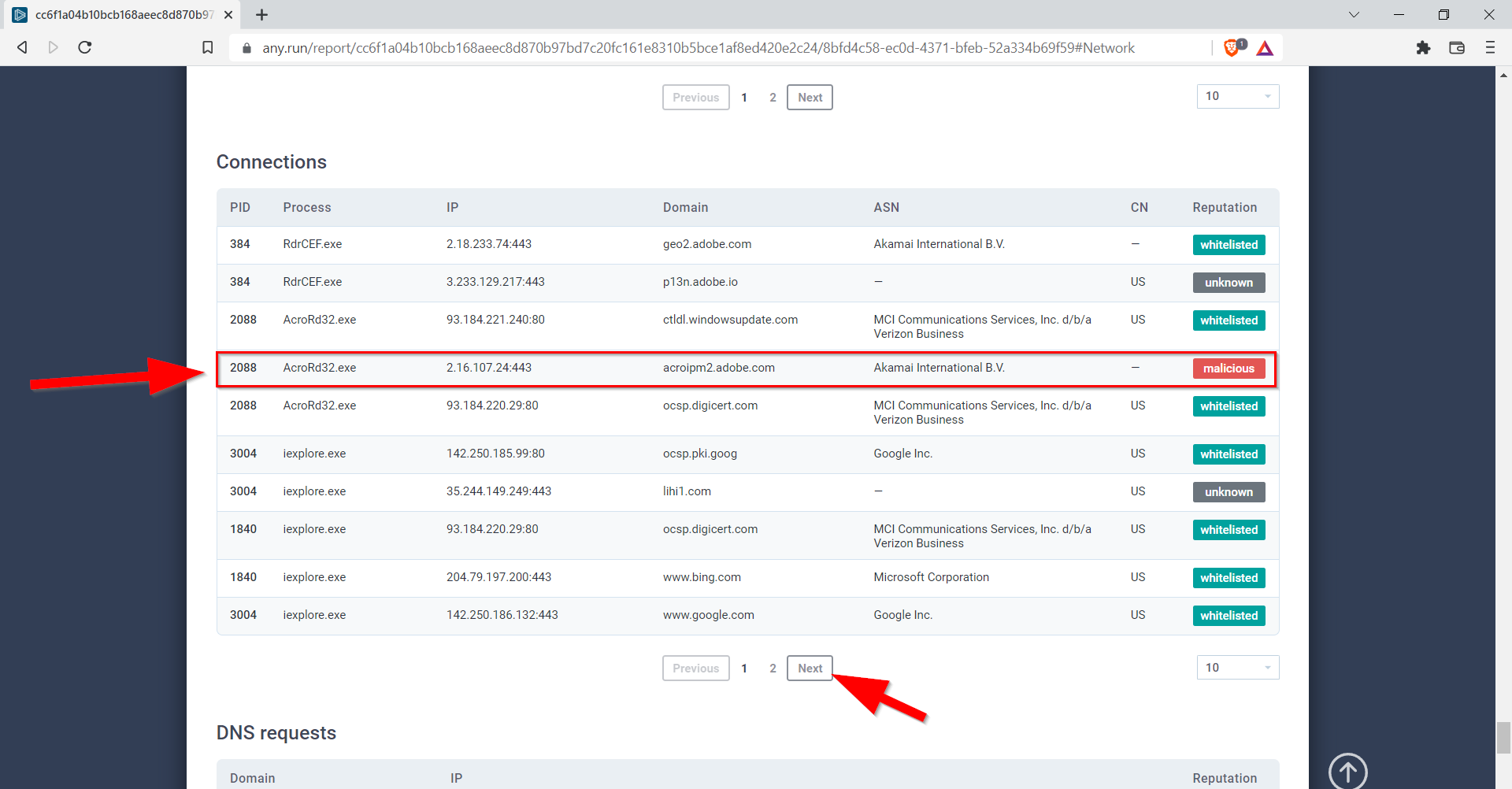
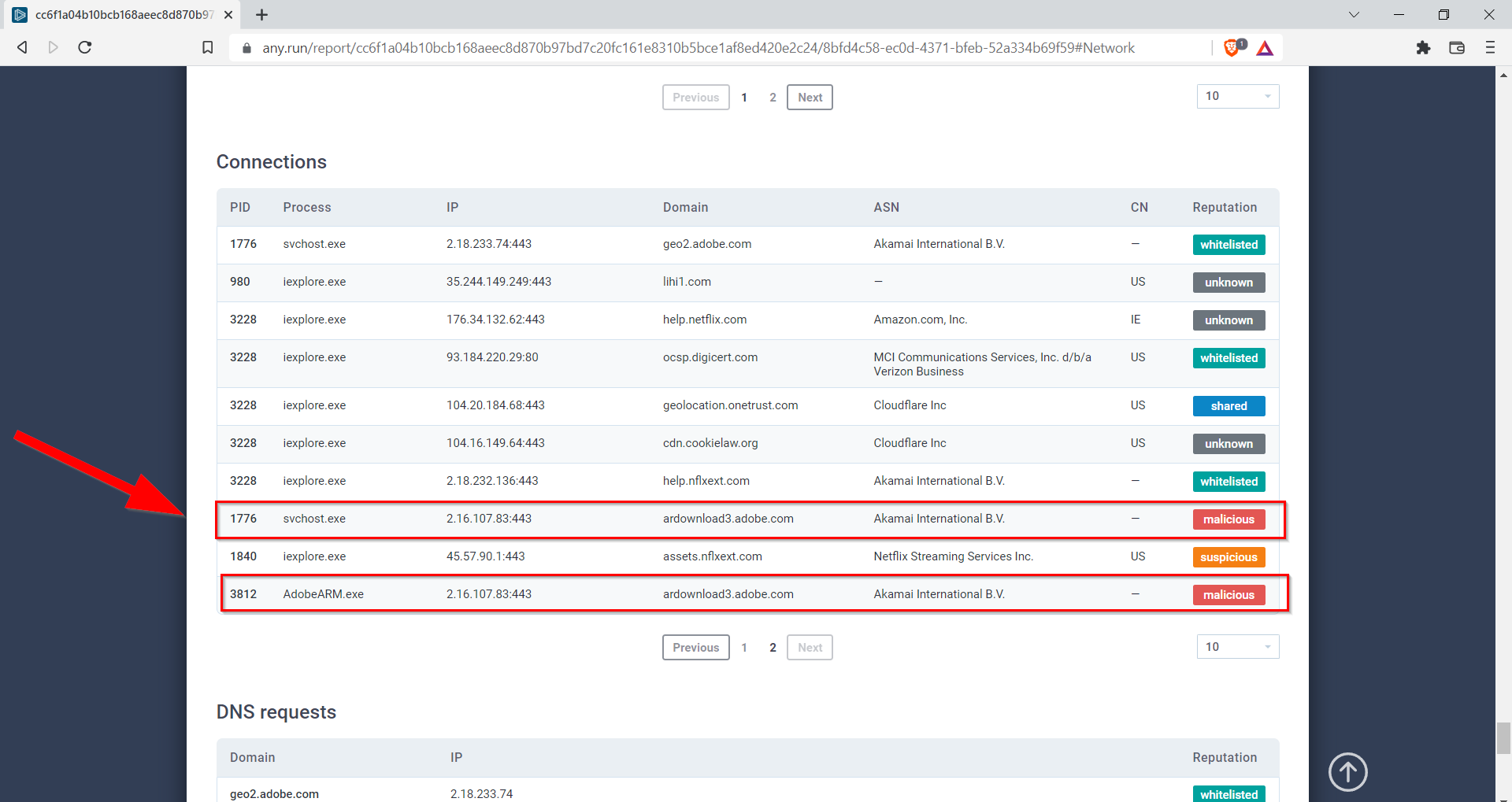
2[.]16[.]107[.]83,2[.]16[.]107[.]24
8.5. What Windows process was flagged as Potentially Bad Traffic?
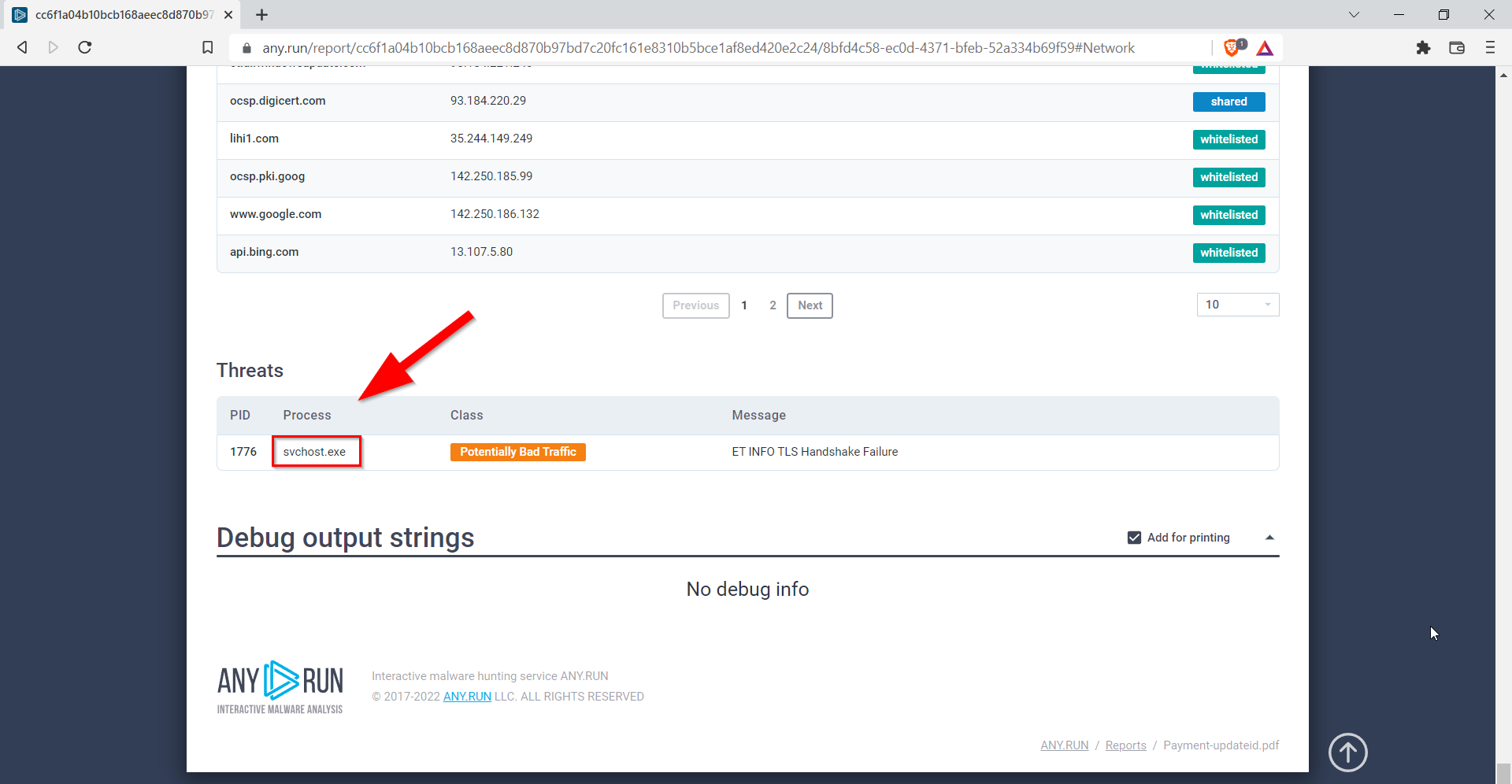
svchost.exe
Task 9: Phishing Case 3
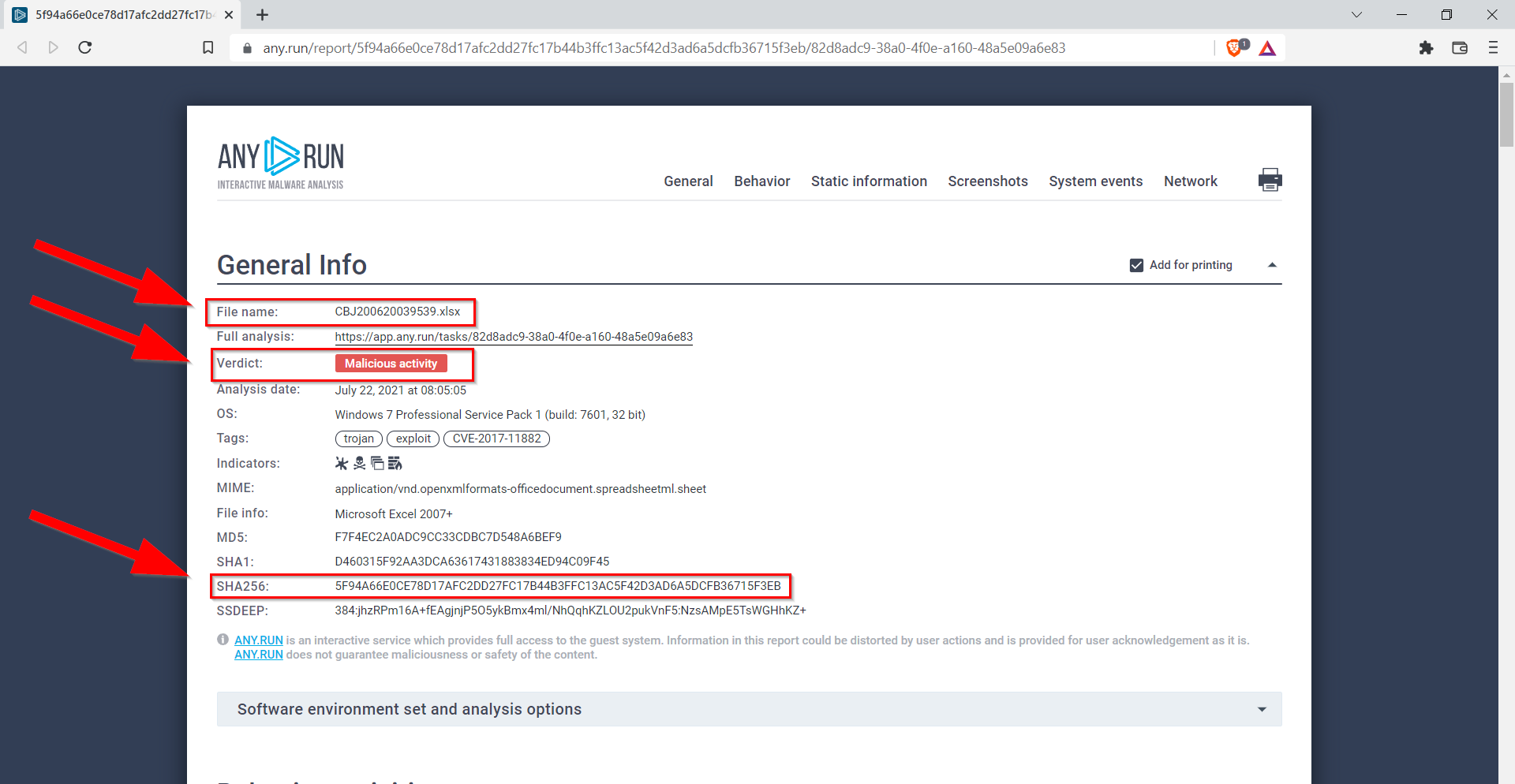
9.1. What is this analysis classified as?
Malicious activity
9.2. What is the name of the Excel file?
CBJ200620039539.xlsx
9.3. What is the SHA 256 hash for the file?
5F94A66E0CE78D17AFC2DD27FC17B44B3FFC13AC5F42D3AD6A5DCFB36715F3EB
9.4. What domains are listed as malicious? Defang the URLs & submit answers in alphabetical order. (answer: URL1,URL2,URL3)
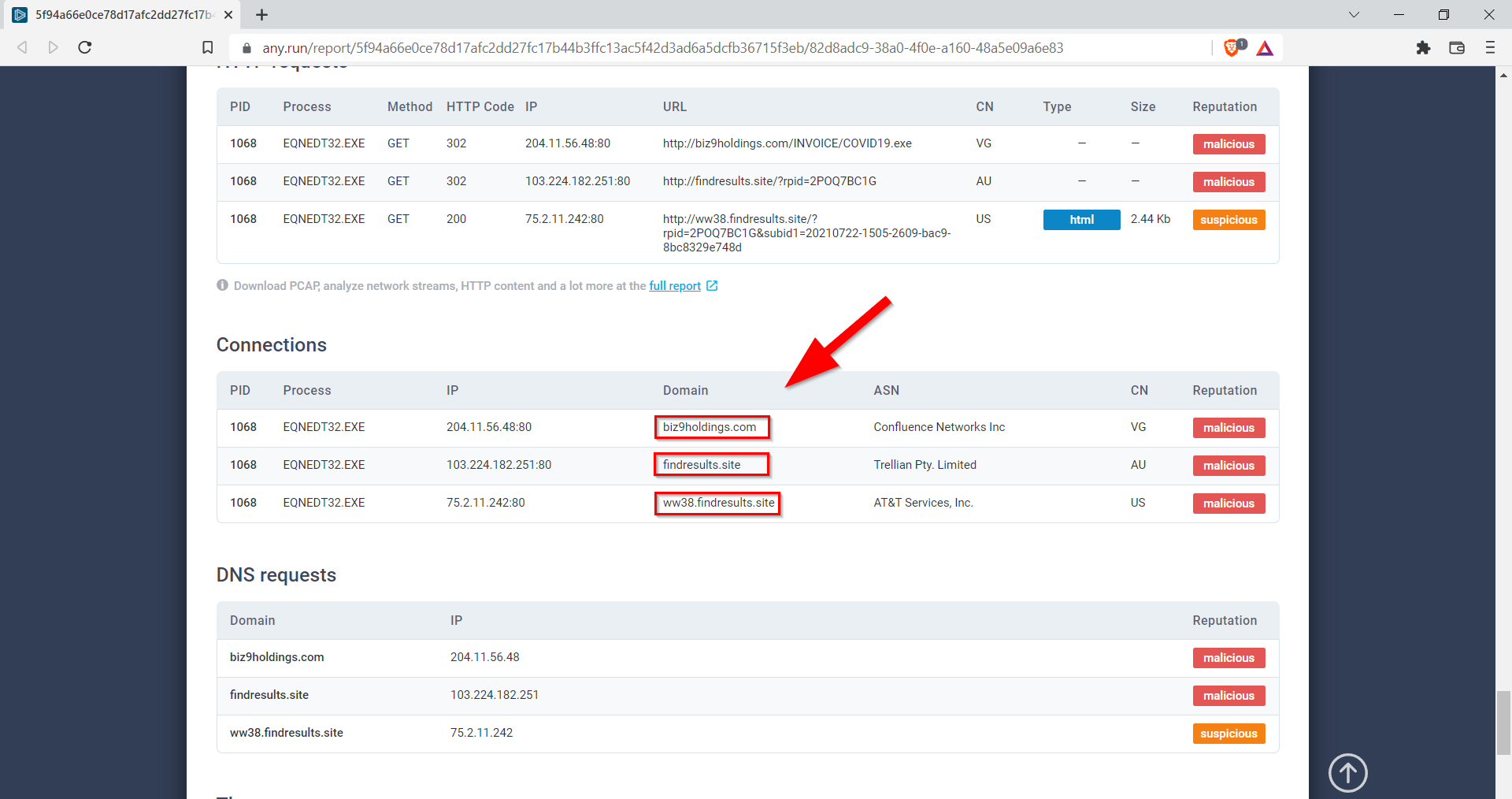
biz9holdings[.]com,findresults[.]site, ww38[.]findresults[.]site
9.5. What IP addresses are listed as malicious? Defang the IP addresses & submit answers from lowest to highest. (answer: IP1,IP2,IP3)
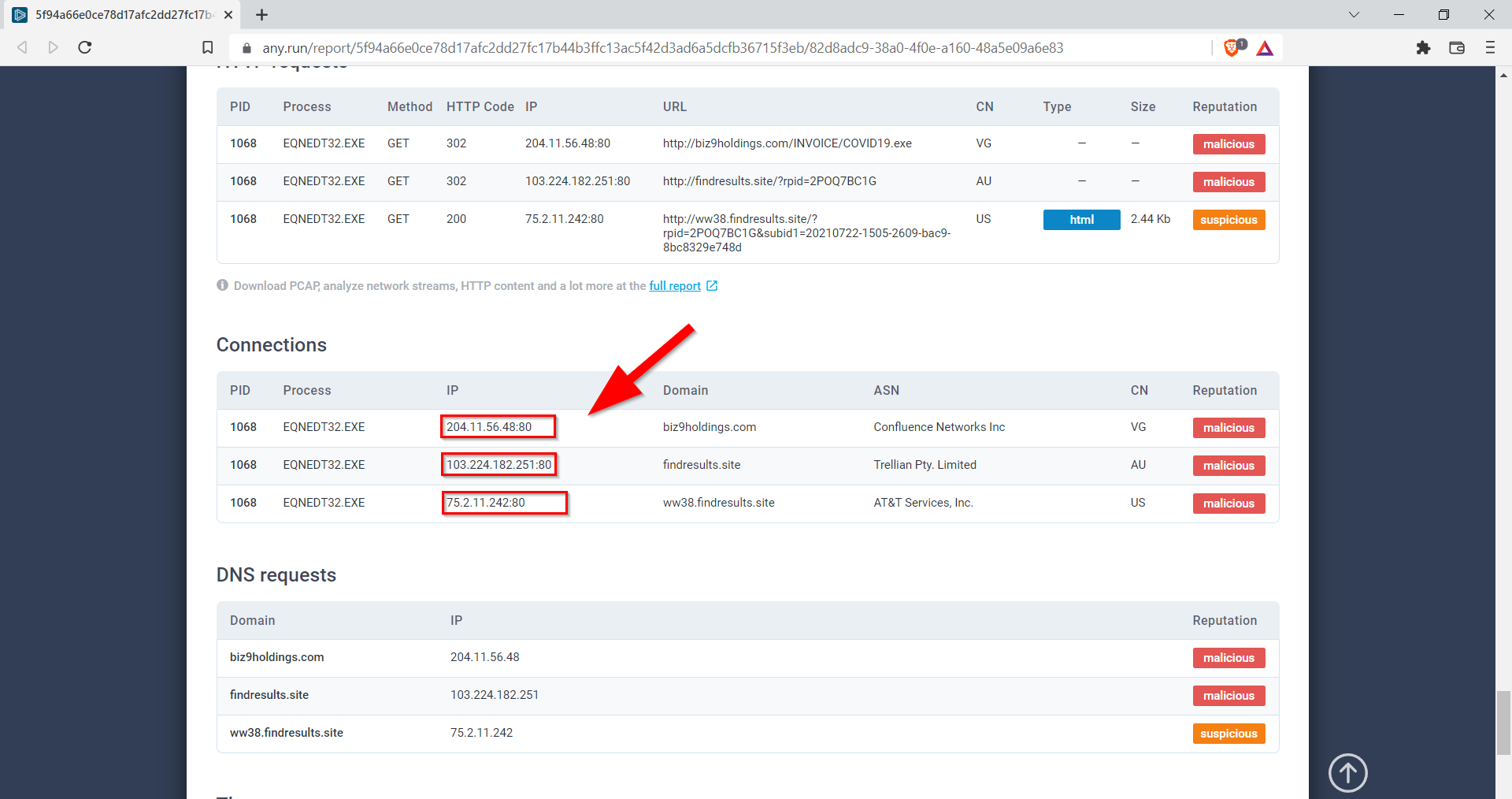
204[.]11[.]56[.]48,103[.]224[.]182[.]251,75[.]2[.]11[.]242,
9.6. What vulnerability does this malicious attachment attempt to exploit?
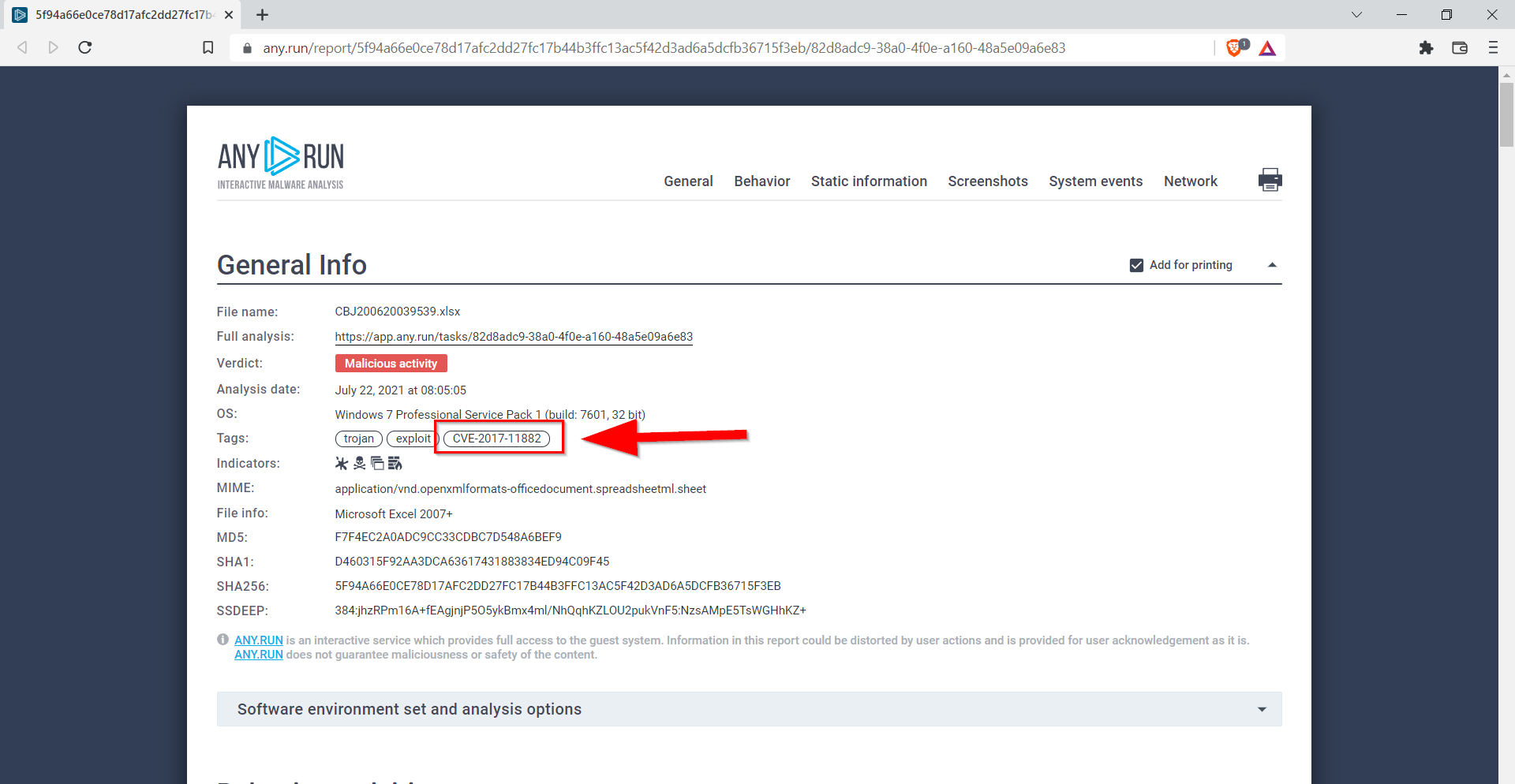
CVE-2017-11882

