The room: This room discusses five of the OWASP API Security Top 10 vulnerabilities.
Task 2: Vulnerability VI – Mass Assignmen
2.1. Is it a good practice to blindly insert/update user-provided data in the database?
nay
2.3. What would be the returned credit value after performing Question#2?
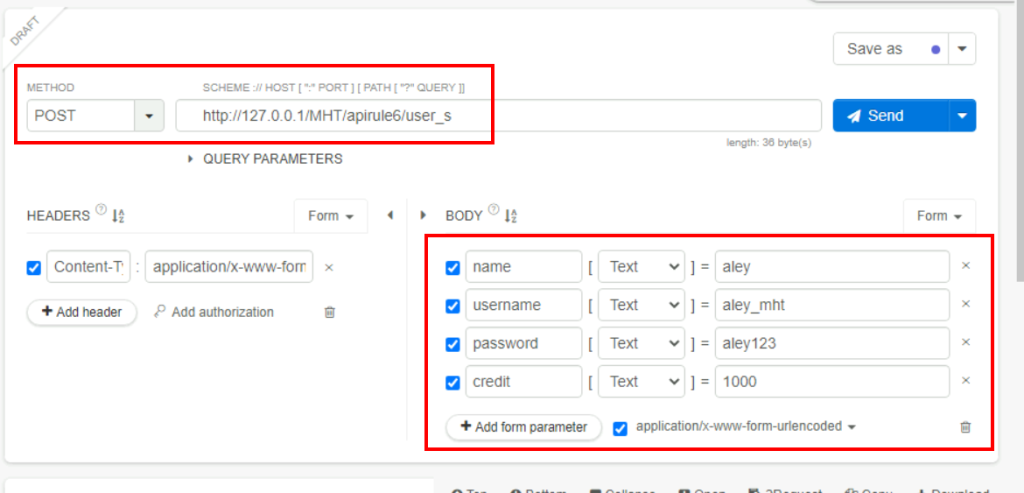
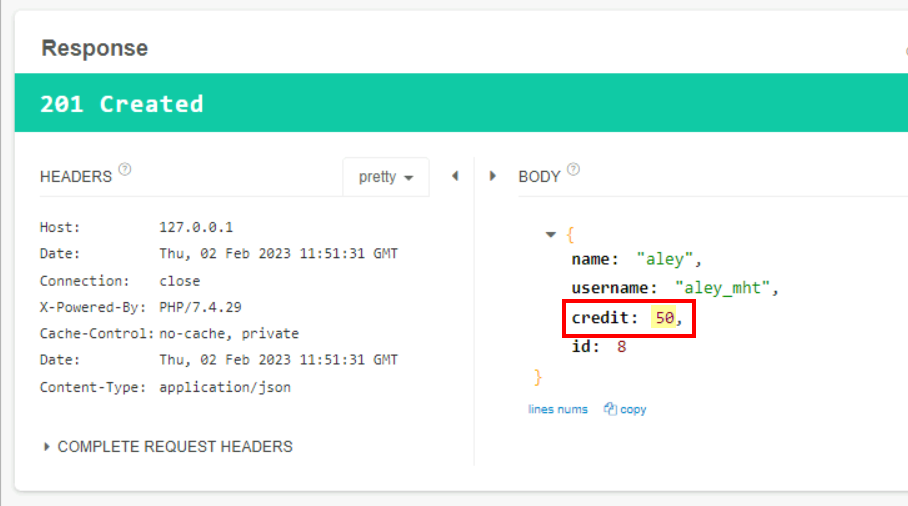
50
Task 3: Vulnerability VII – Security Misconfiguration
3.1. Is it an excellent approach to show error logs from the stack trace to general visitors (yea/nay)?
nay
3.3. What is the HTTP response code?
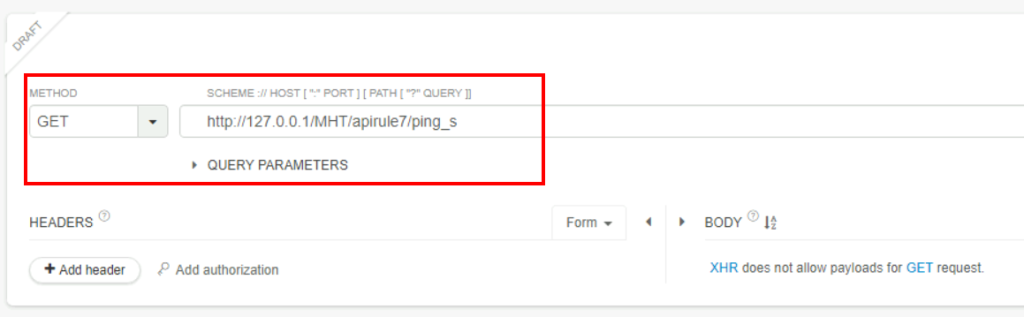
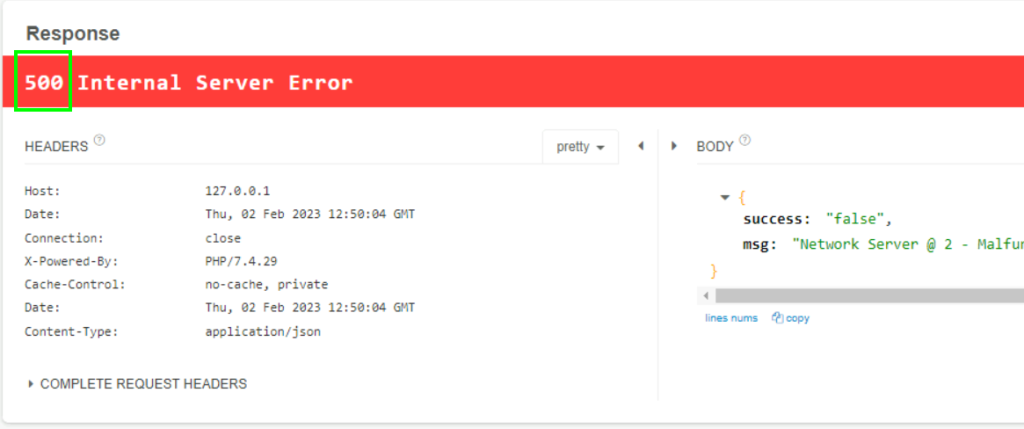
500
3.4. What is the Error ID number in the HTTP response message?

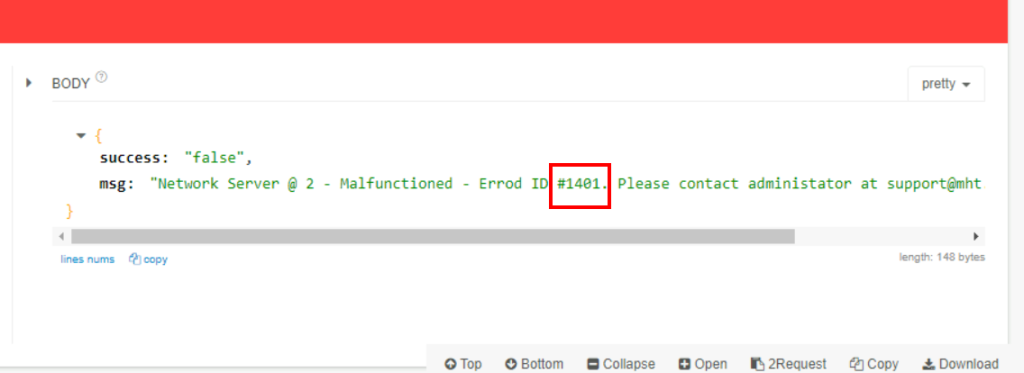
1401
Task 4: Vulnerability VIII – Injection
4.1. Can injection attacks be carried out to extract data from the database?
yea
4.2. Can injection attacks result in remote code execution?
yea
4.3. What is the HTTP response code if a user enters an invalid username or password?
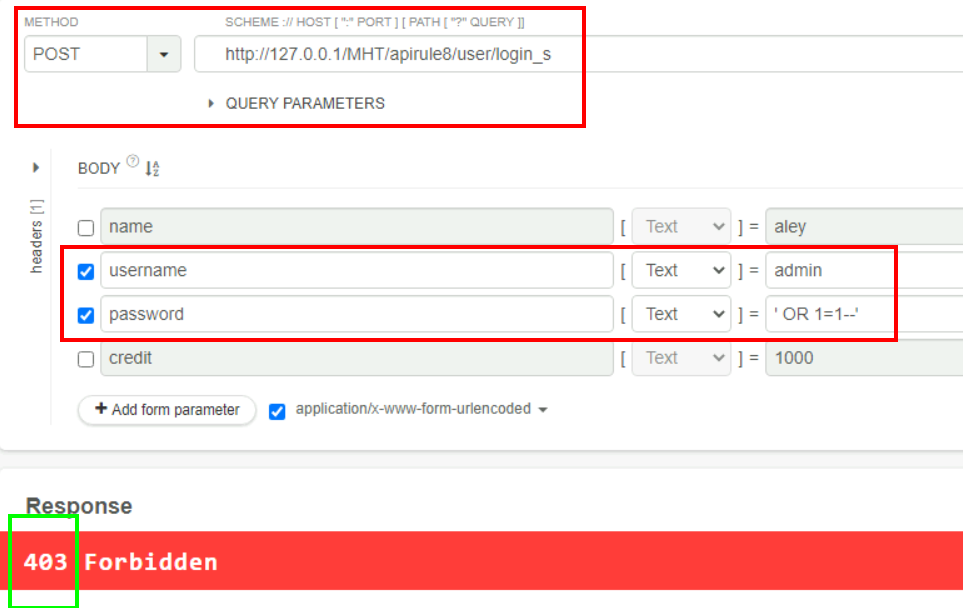
403
Task 5: Vulnerability IX – Improper Assets Management
5.1. Is it good practice to host all APIs on the same server (yea/nay)?
nay
5.3. What is the amount of balance associated with user Alice?
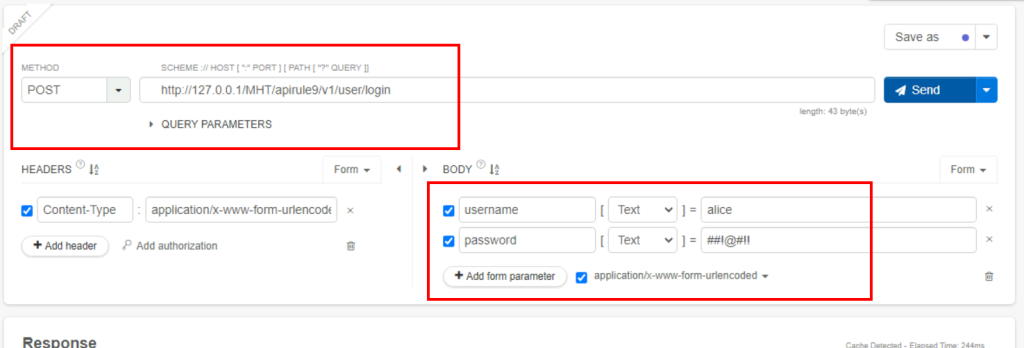
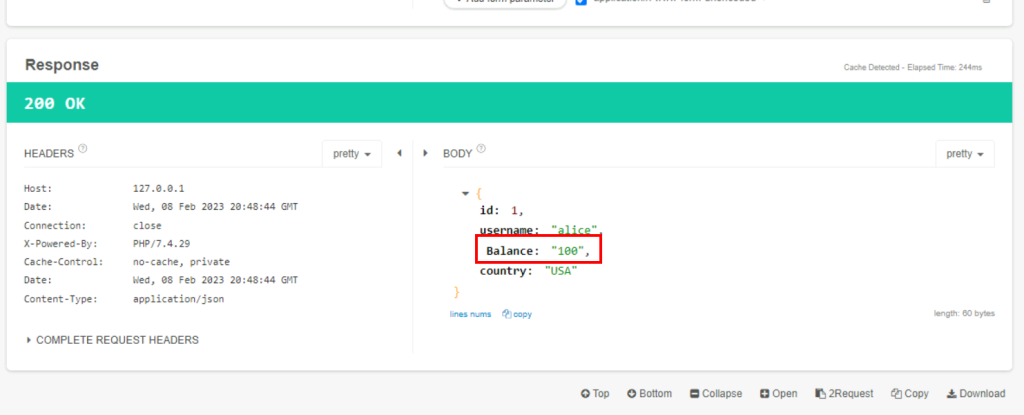
100
5.3. What is the country of the user Alice?
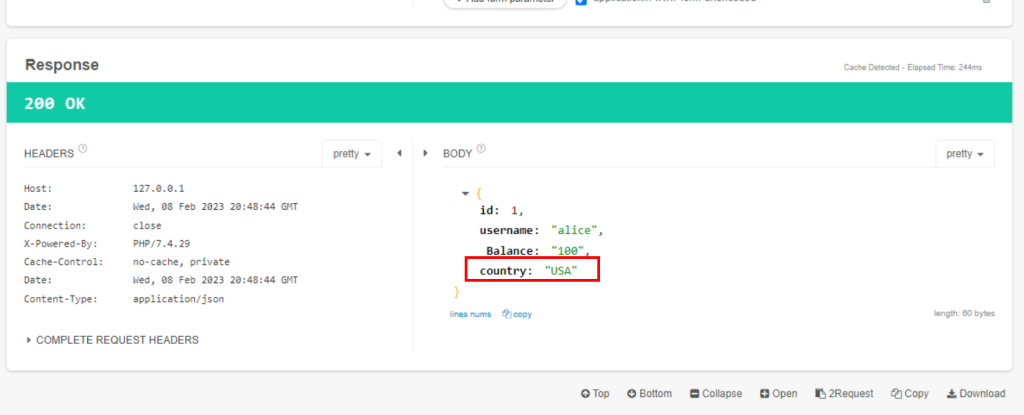
USA
Task 6: Vulnerability X – Insufficient Logging & Monitoring
6.1. Should the API logs be publically accessible so that the attacker must know they are being logged (yea/nay)?
nay
6.2. What is the HTTP response code in case of successful logging of user information?
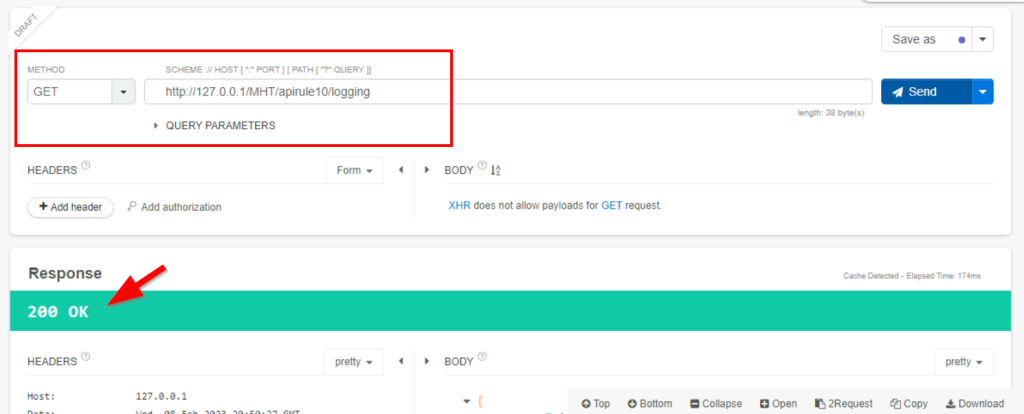
200

