The room: “Provide an understanding of the OpenCTI Project”
https://tryhackme.com/room/opencti
Task 4: OpenCTI Dashboard 1
4.1. What is the name of the group that uses the 4H RAT malware?
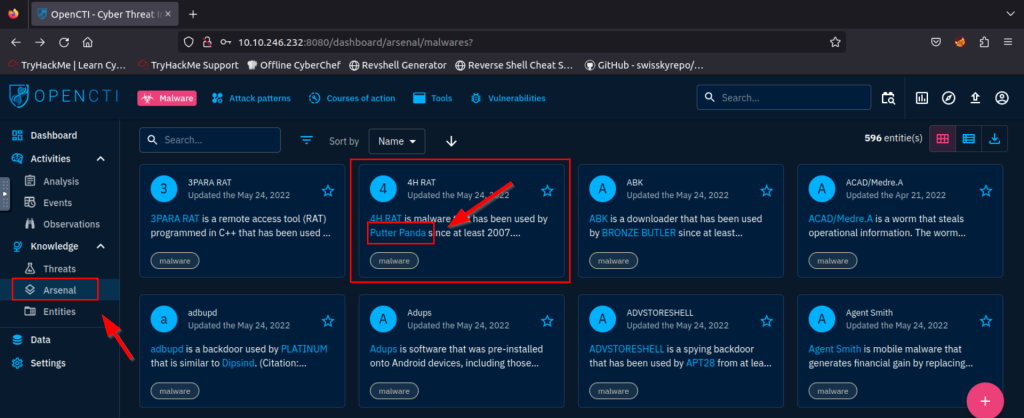
Putter Panda
4.2. What kill-chain phase is linked with the Command-Line Interface Attack Pattern?
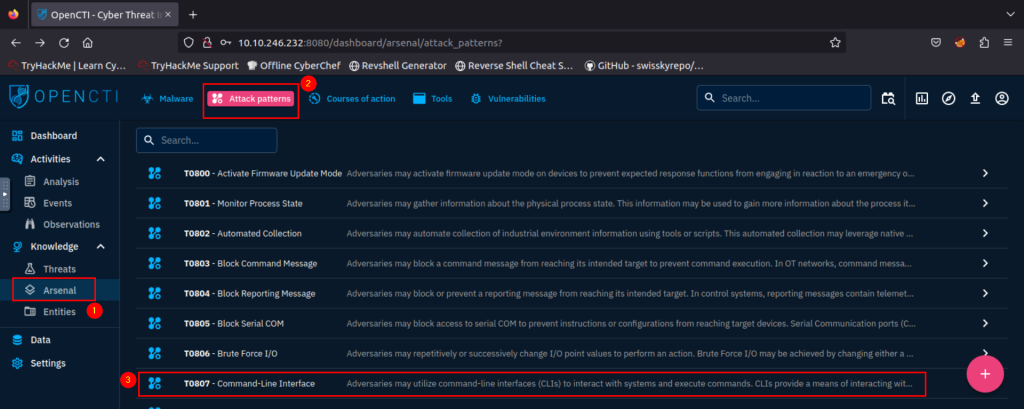
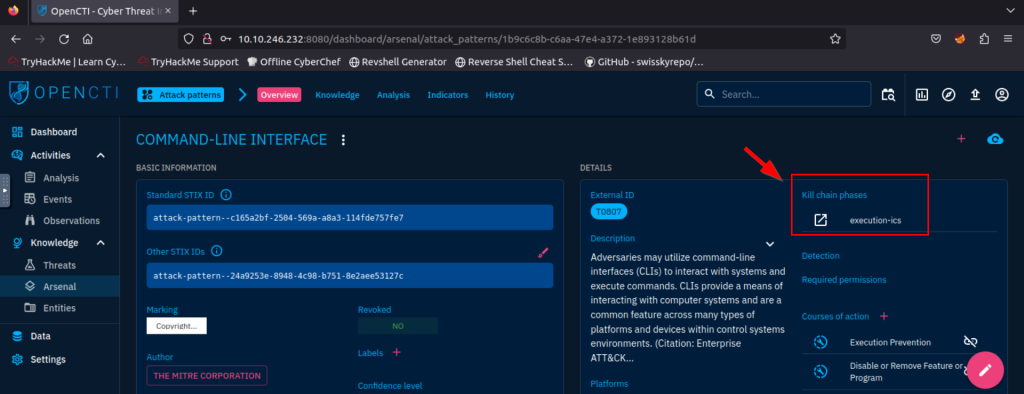
execution-ics
4.3. Within the Activities category, which tab would house the Indicators?
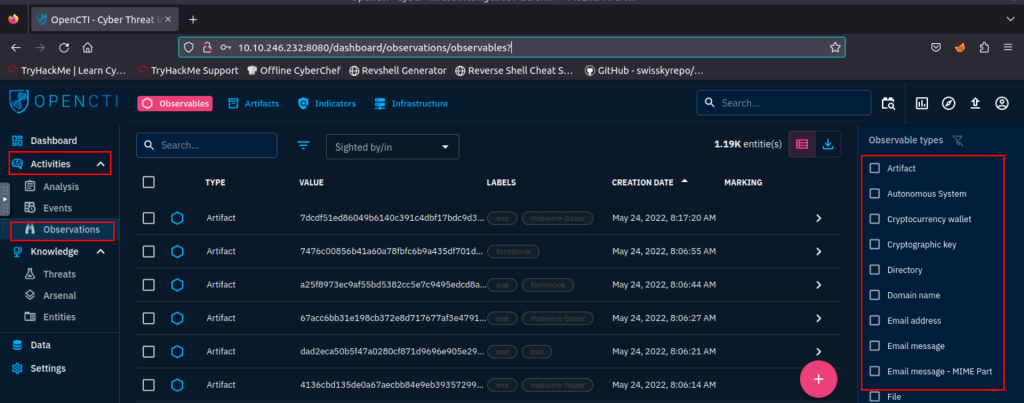
observations
Task 5: OpenCTI Panosu 2
5.1. What Intrusion sets are associated with the Cobalt Strike malware with a Good confidence level? (Intrusion1, Intrusion2)
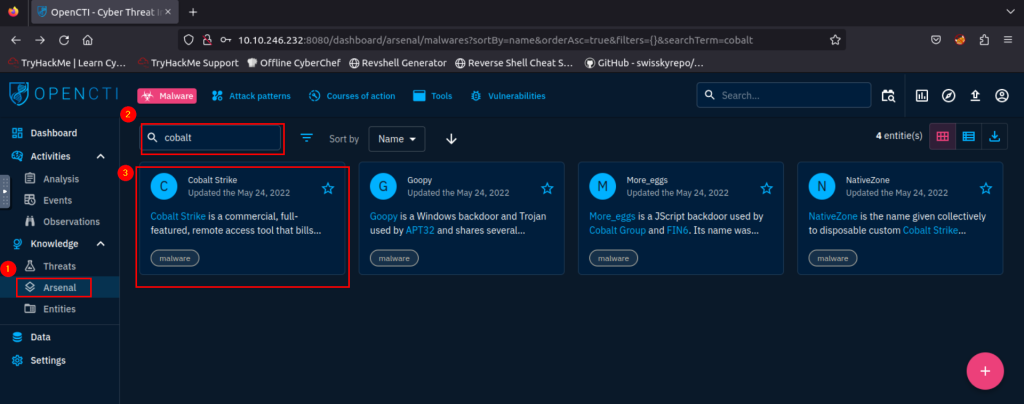
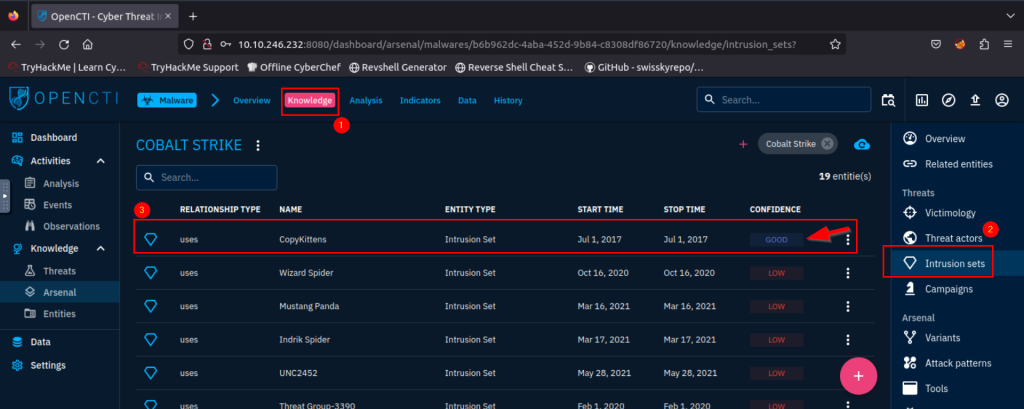
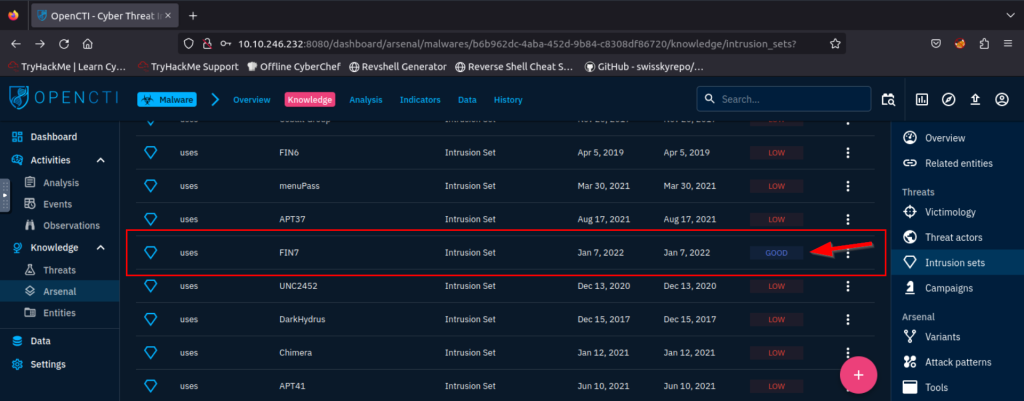
CopyKittens, FIN7
5.2. Who is the author of the entity?
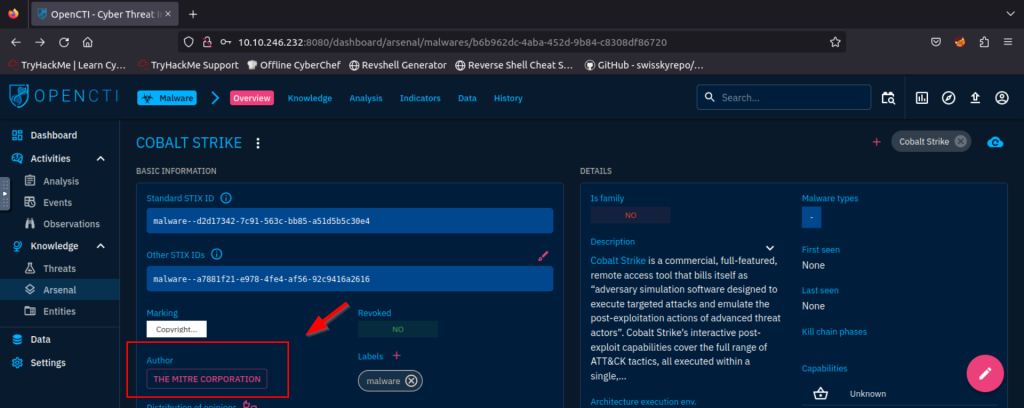
The MITRE Corporation
Task 6: Investigative Scenario
6.1. What is the earliest date recorded related to CaddyWiper? Format: YYYY/MM/DD
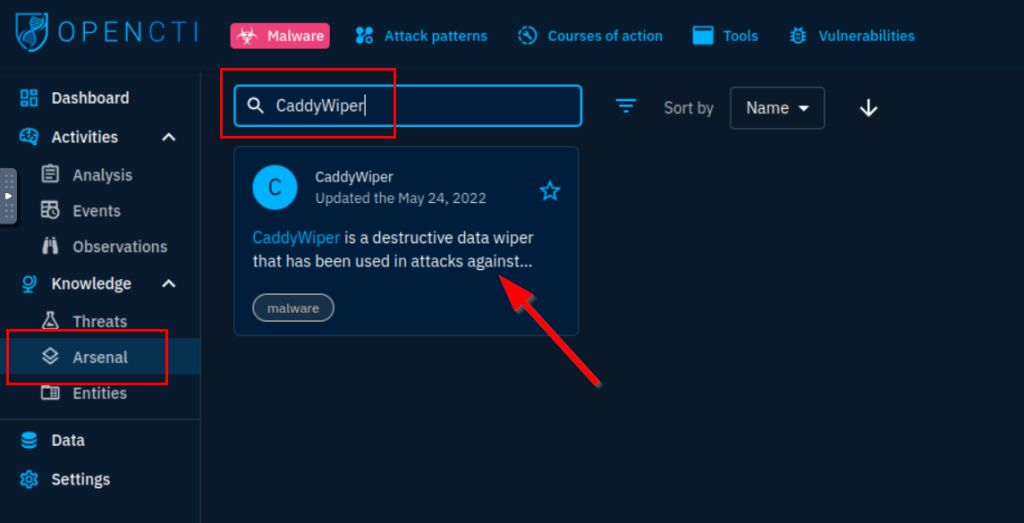
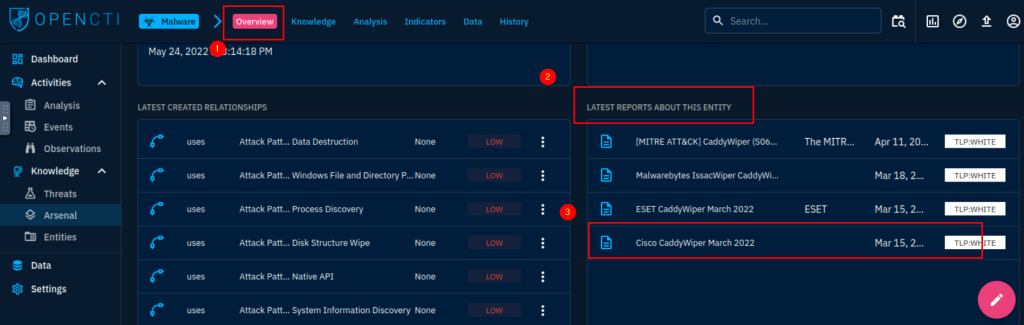
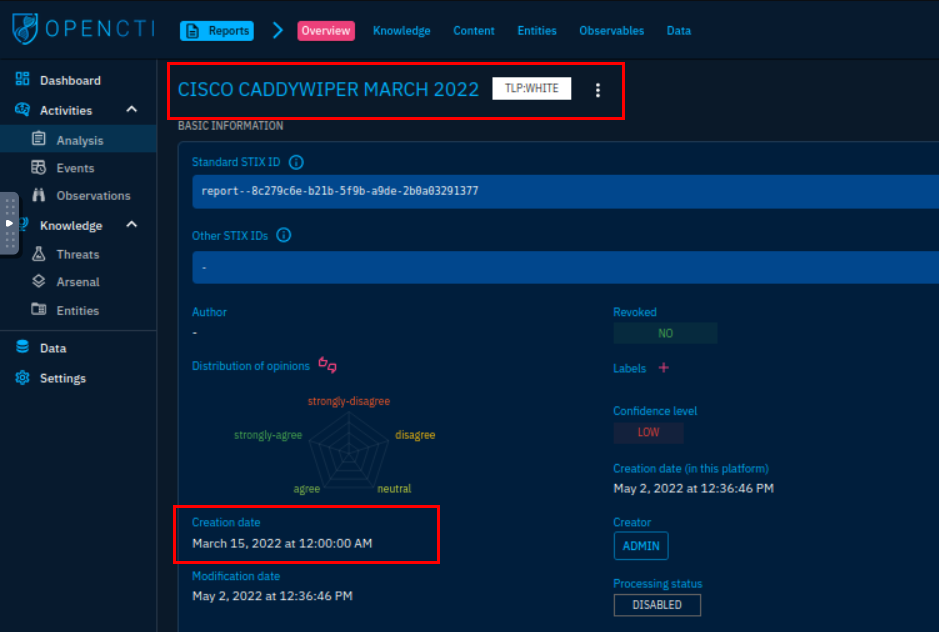
2022/03/15
6.2. Which Attack technique is used by the malware for execution?
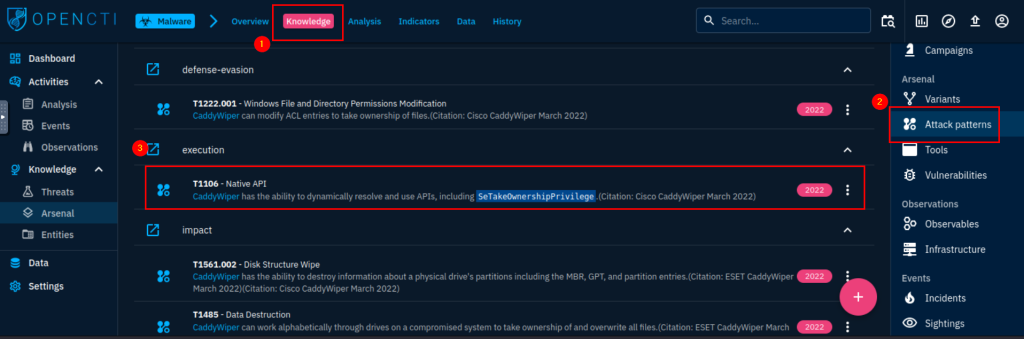
Native API
6.3. How many malware relations are linked to this Attack technique?
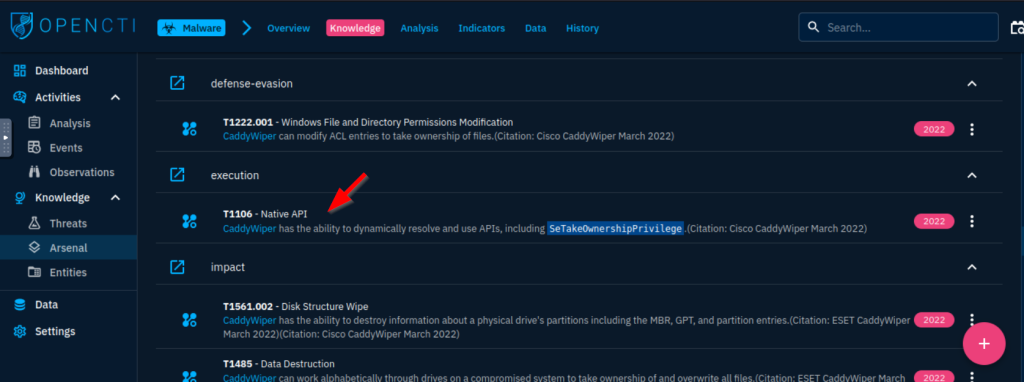
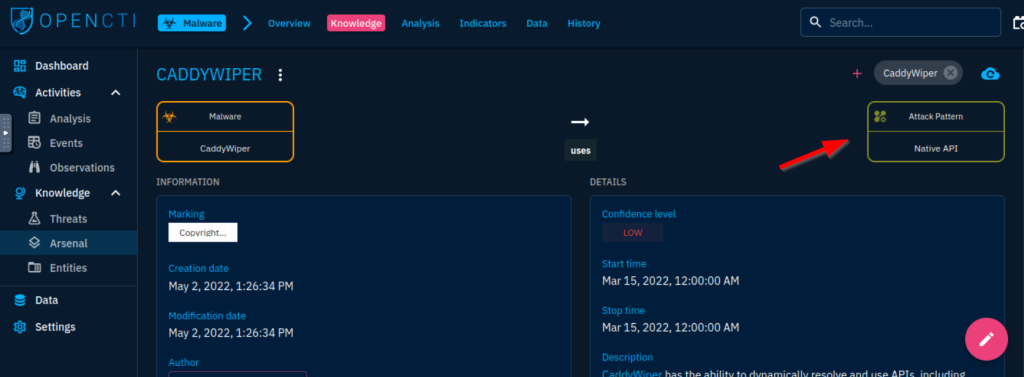
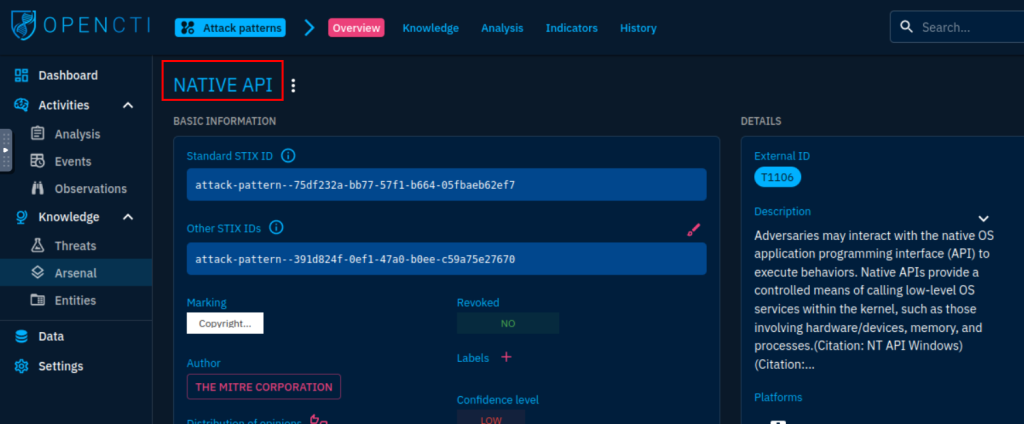
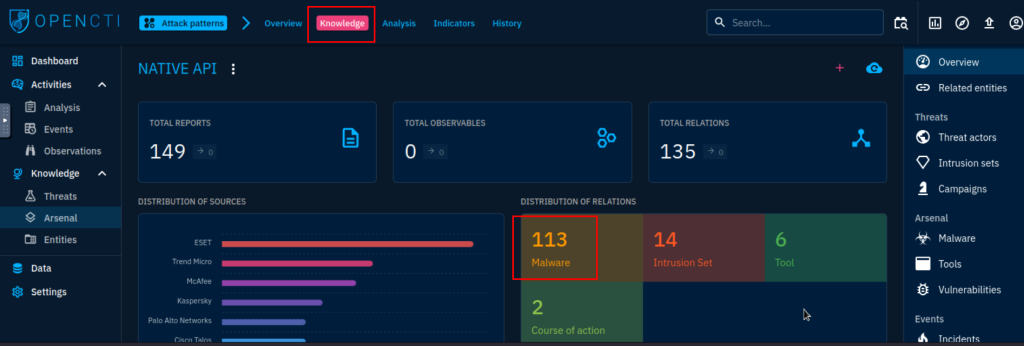
113
6.4. Which 3 tools were used by the Attack Technique in 2016? (Ans: Tool1, Tool2, Tool3)
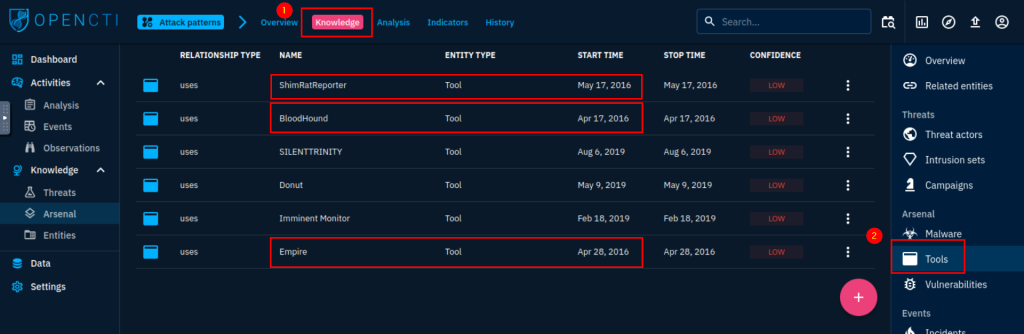
BloodHound, Empire, ShimRatReporter
6.5. What country is APT37 associated with?
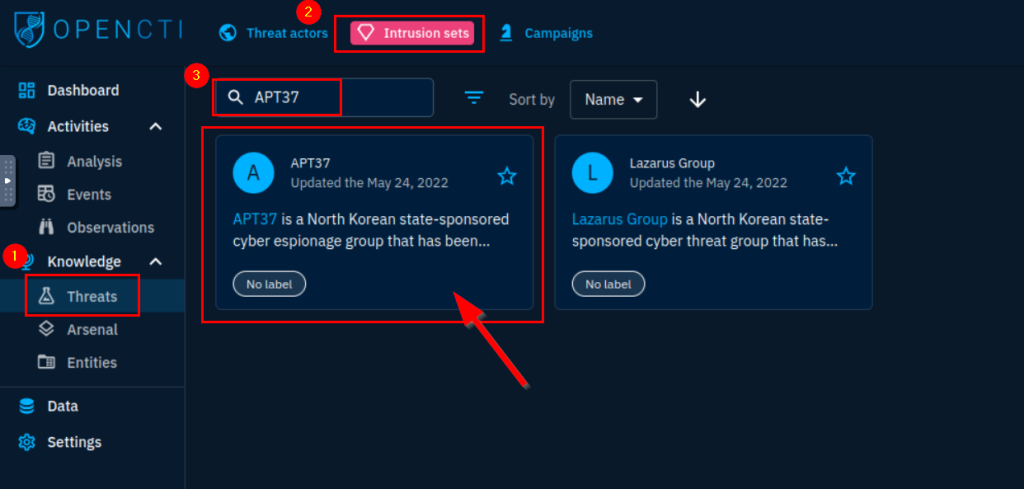
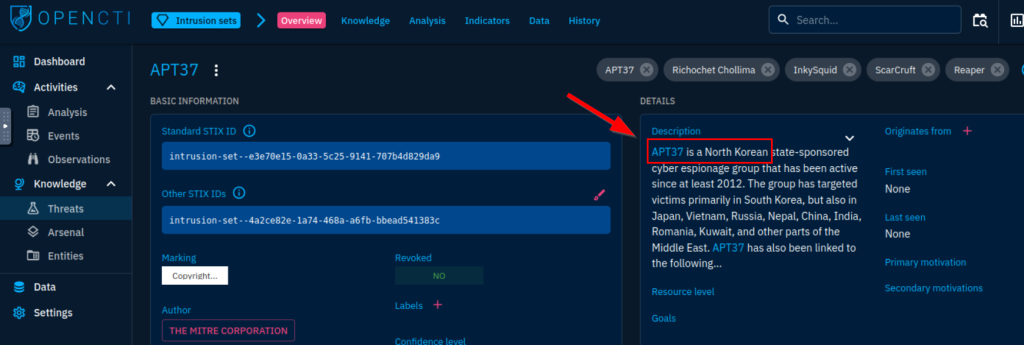
North Korean
6.6. Which Attack techniques are used by the group for initial access? (Ans: Technique1, Technique2)
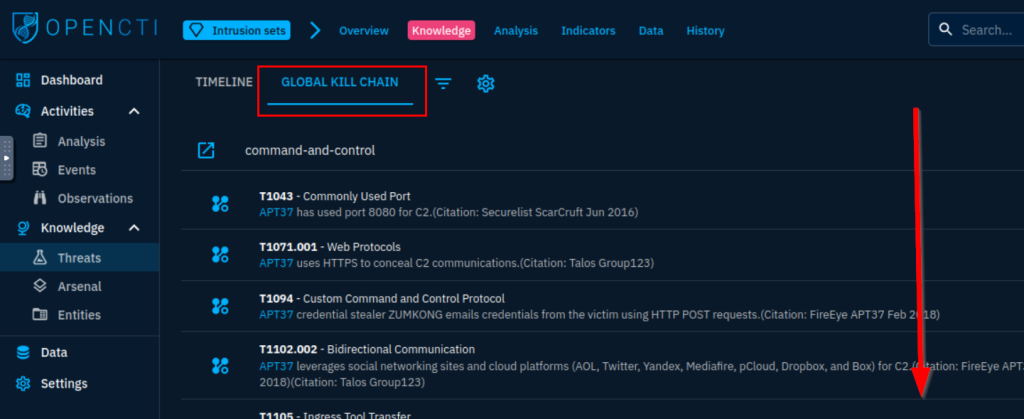
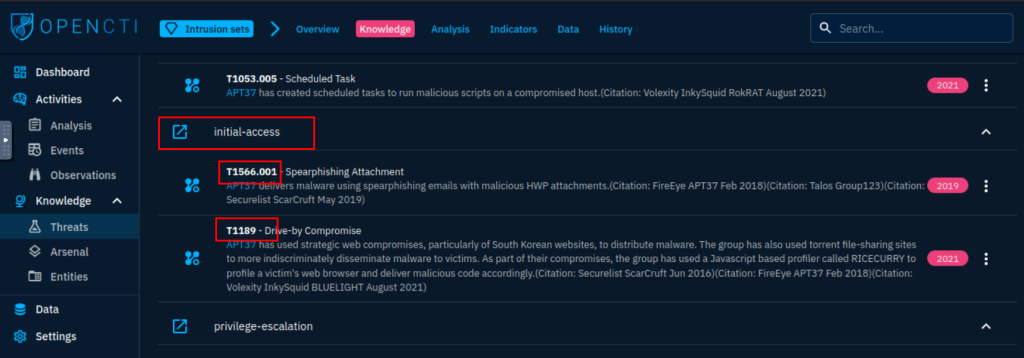
T1189, T1566
a

