The room: “The Unified Kill Chain is a framework which establishes the phases of an attack, and a means of identifying and mitigating risk to IT assets.”
https://tryhackme.com/room/ohsint
Task 1: OhSINT
1.1. What is this users avatar of?
ExifTool is a free and open-source software program for reading, writing, and processing image, audio, video, and PDF metadata. Click here for the necessary steps to install Kali linux.
In .jpg, the copyright metadata part is made to protect the copyright of the image. Let’s search for the name in the copyright part of the image on Google.
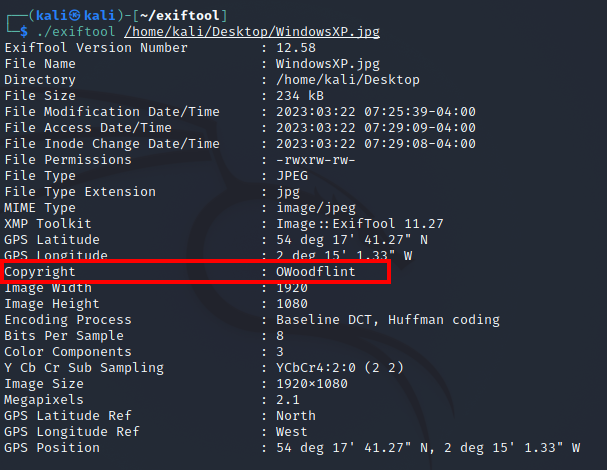
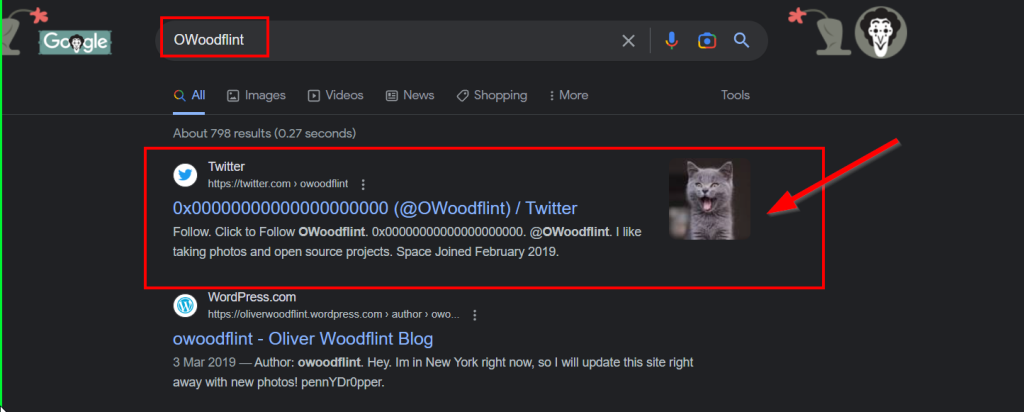
cat
1.2. What city is this person in?
The term BSSID (basic service set identifier) is used to identify the sections of a wireless network (WLAN). BSSID is used to identify multiple access points and associated clients within the WLAN. The MAC address of an access point is used as a BSSID.
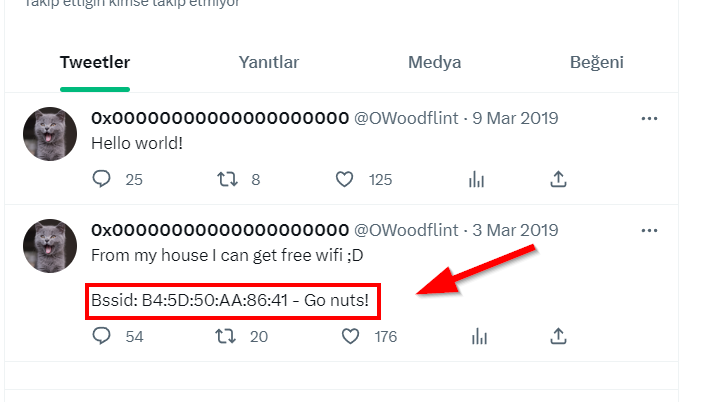
BSSID value was shared in one of the posts on the Twitter account.
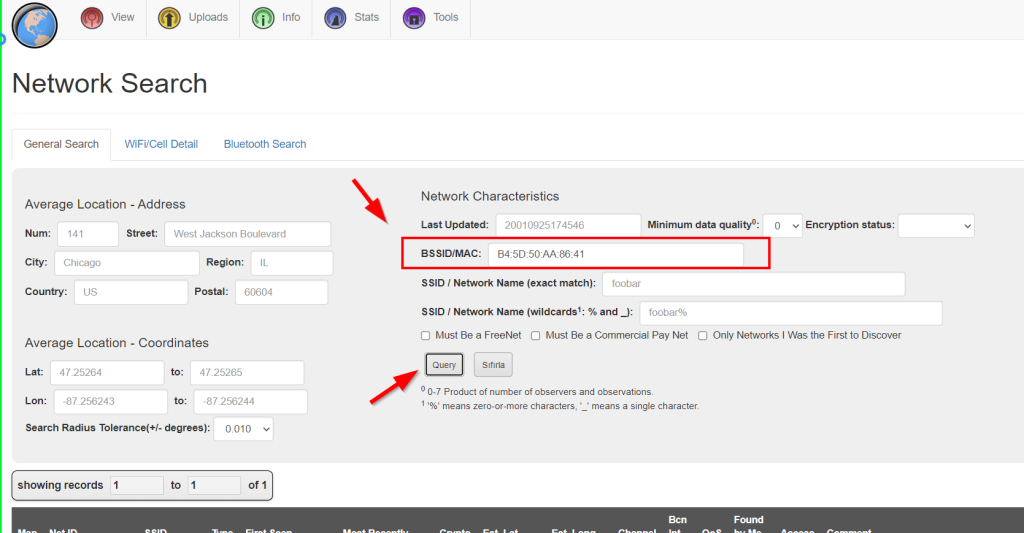
We can find a location using BSSID values. Information about different wireless access points around the world can be collected from wigle.net. It is necessary to be a member of the Wigle.net site. After becoming a member, we come to the “search for networks” section with View > Basic Search steps. Here, in the BSSID / MAC section, we enter the BSSID address shared in the Twitter account and make a Query.
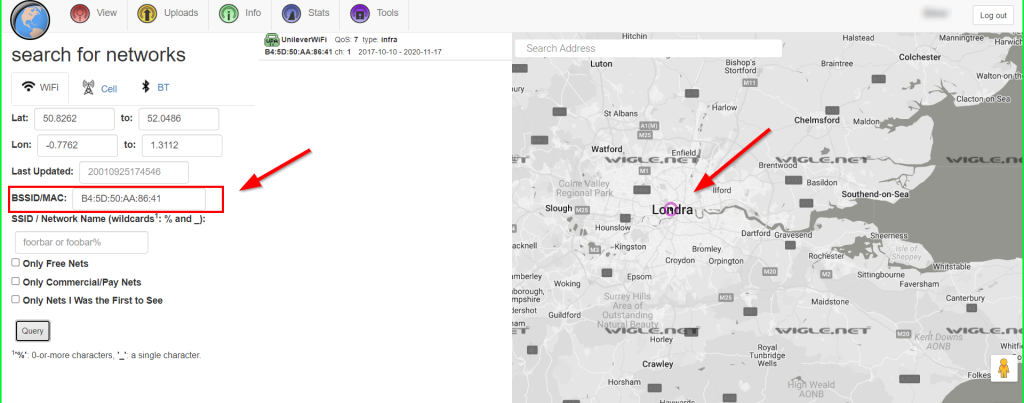
London
1.3. Whats the SSID of the WAP he connected to?
Multiple WLANs may conflict with each other. To avoid this, each WLAN must have a unique name, called SSID (service set ID). Thanks to the SSID, even if there are conflicting WLANs, they are kept in the correct WLAN.
We can find the SSID name from the BSSID address, for this we use wigle.net again. Go to View > Advanced Search. Here we search for our BSSID address and reach our SSID address.
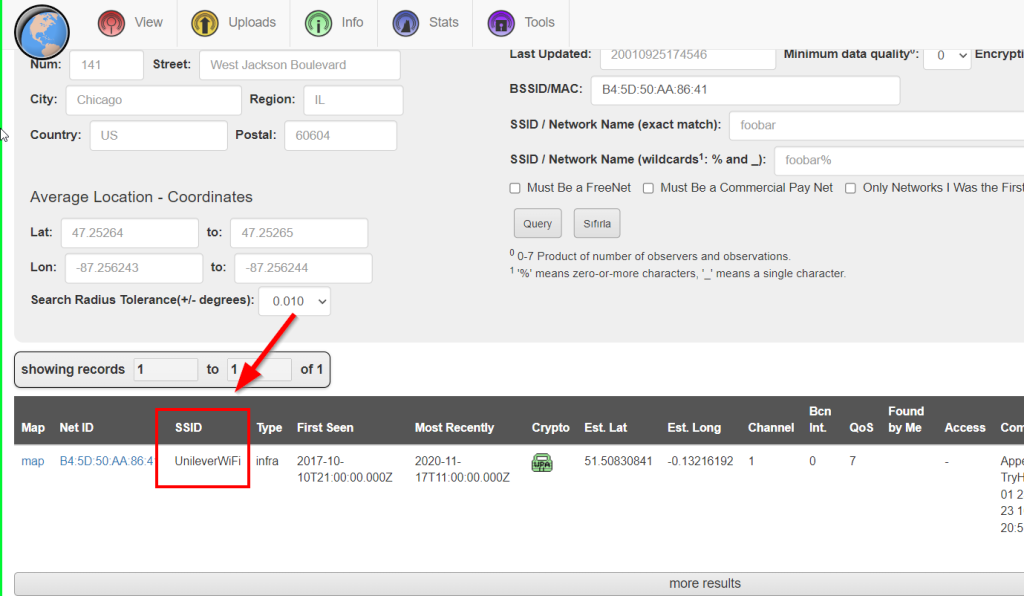
UnileverWiFi
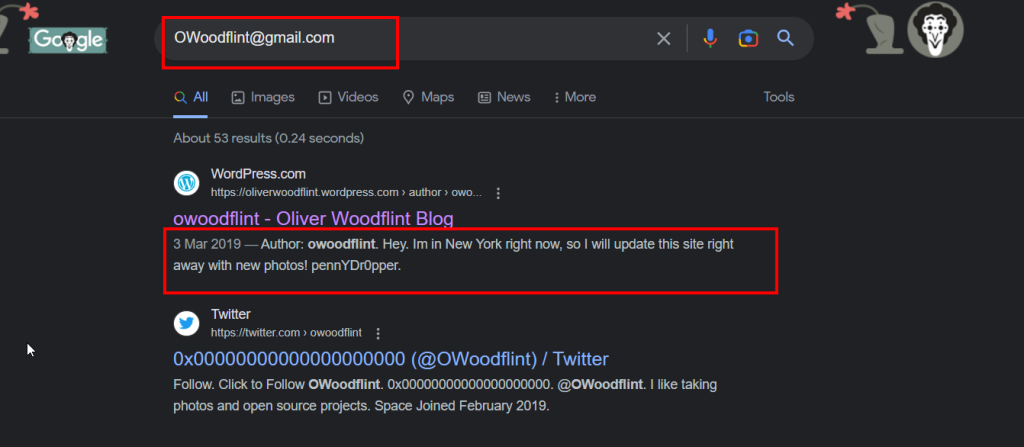
1.4. What is his personal email address?
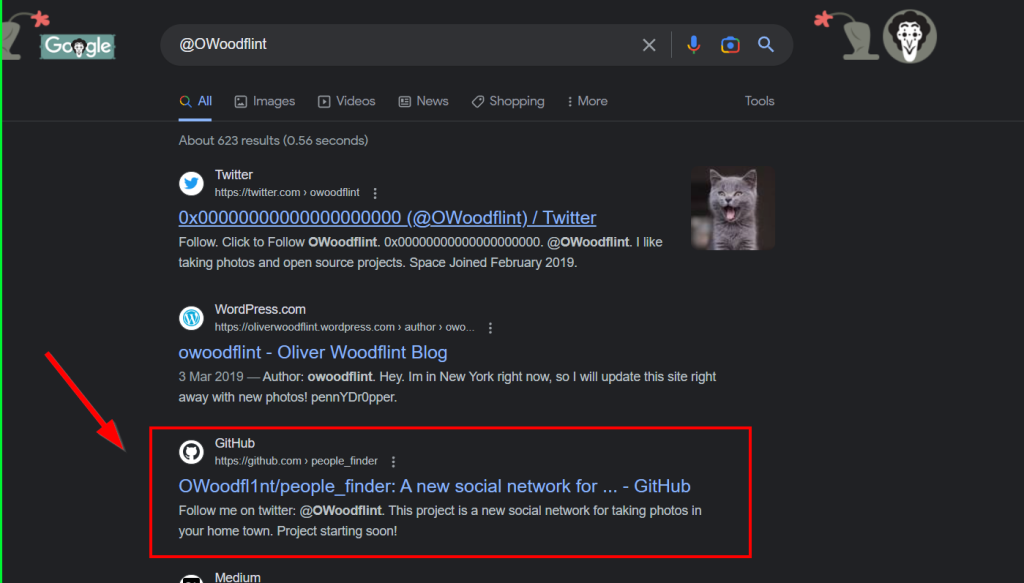
In Google, we search for the username in the Twitter account. We see that the user has a GitHub address with the same username. When we visit the GitHub address, we reach the email address
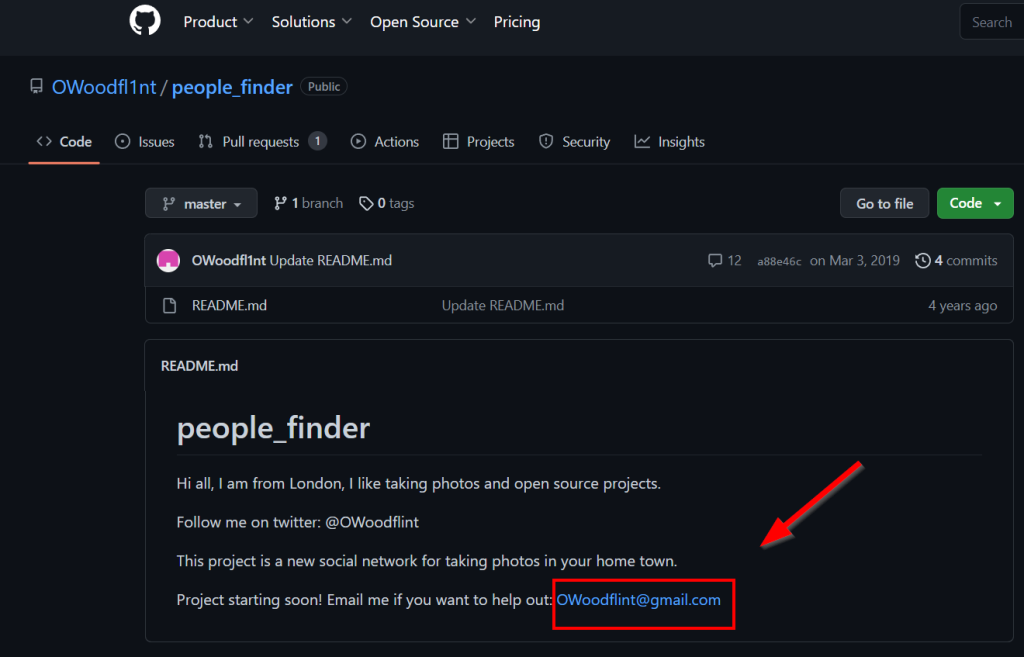
OWoodflint@gmail.com
1.5. What site did you find his email address on?

github
1.6. Where has he gone on holiday?
In Google, we search for the username in the Twitter account. We see that the user has a website, if we enter the site, we can see the information of the place where he went on holiday
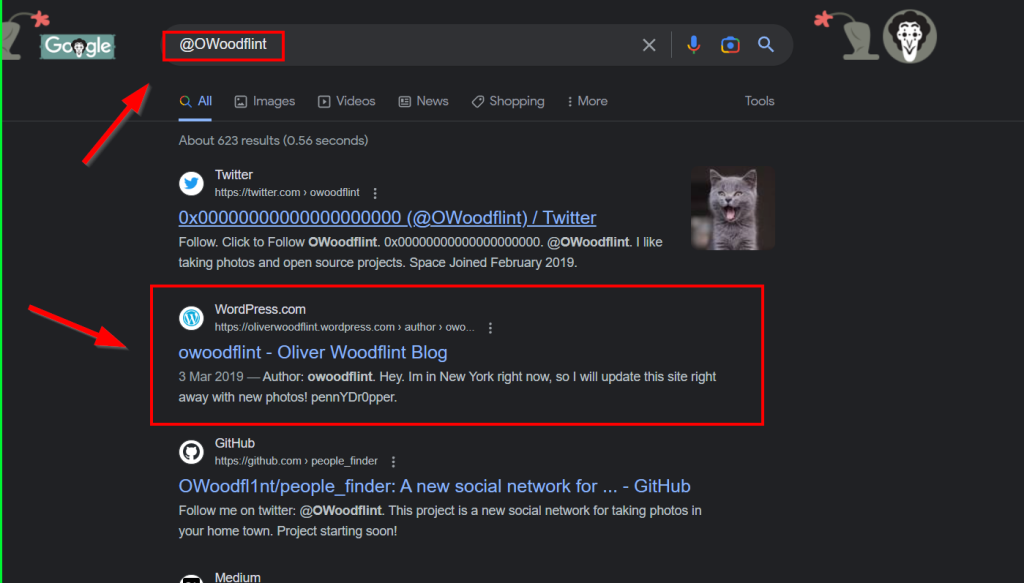

New York
1.7. What is this persons password?
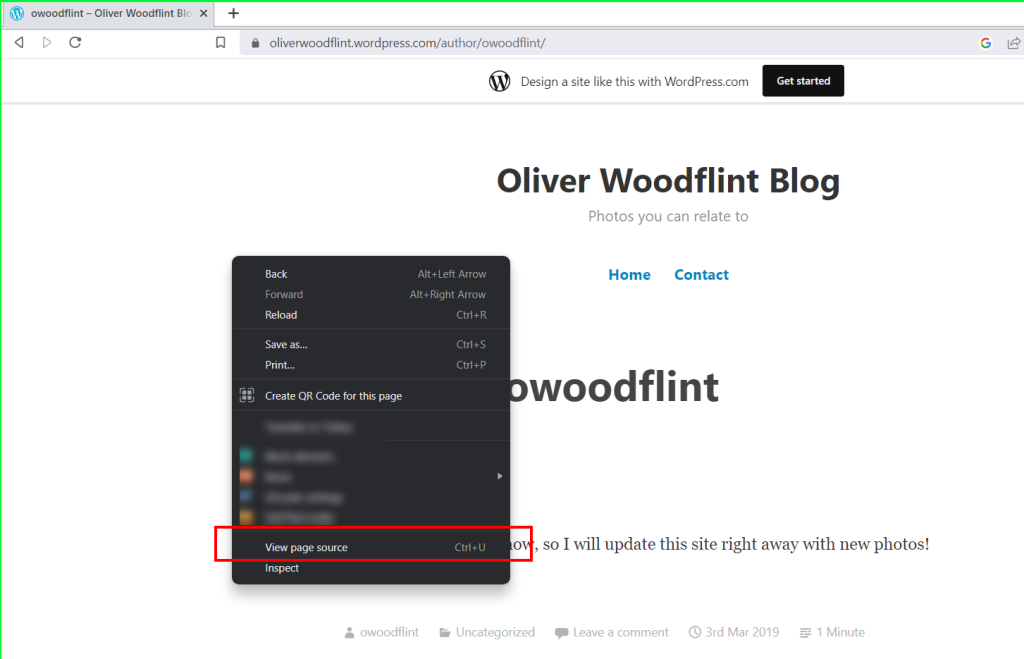
I tried various google searches to find the password. Finally, the meta section in google before entering the user’s website caught my eye. When we visit the site, the “pennYDr0pper.” section in the meta does not appear on the site. When we look at the source code of the site, we see that the colors have been played with so that this part is not visible and this is the password.
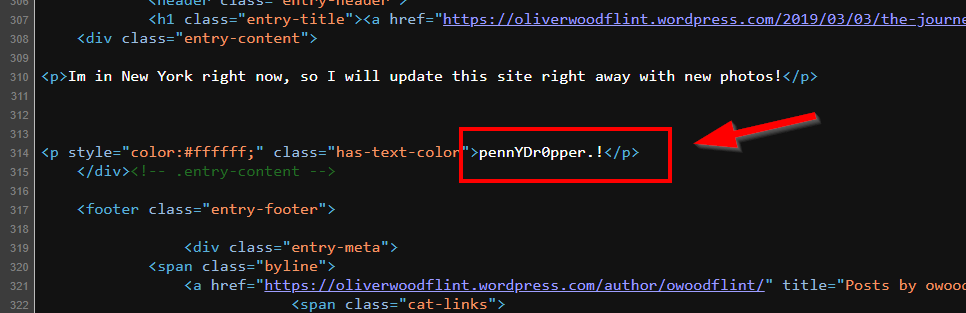
pennYDr0pper.!
a

