Acquire the basic skills to analyze a memory dump in a practical scenario.
Task 2: Memory Forensics
2.1. What type of memory is analyzed during a forensic memory task?
RAM
2.2. In which phase will you create a memory dump of the target system?
Memory Acquisition
Task 3: Environment & Setup
3.1. Which plugin can help us to get information about the OS running on the target machine?

Windows.info
3.2. Which tool referenced above can help us take a memory dump on a Linux OS?
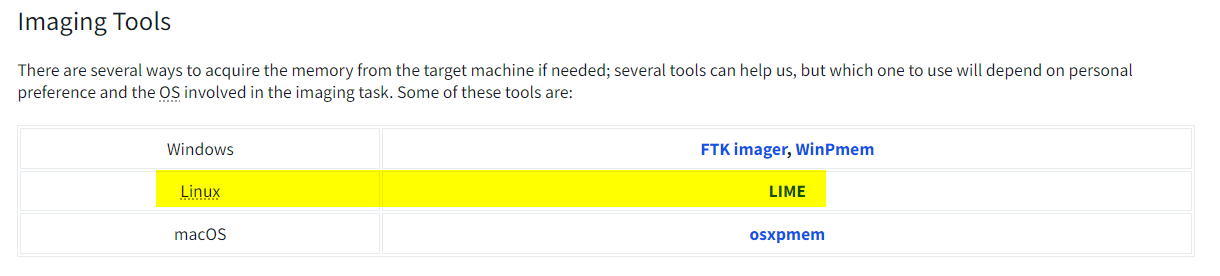
LIME
3.3. Which command will display the help menu using Volatility on the target machine?
vol -h
Task 4: Gathering Target Information
4.1. Is the architecture of the machine x64 (64bit) Y/N?
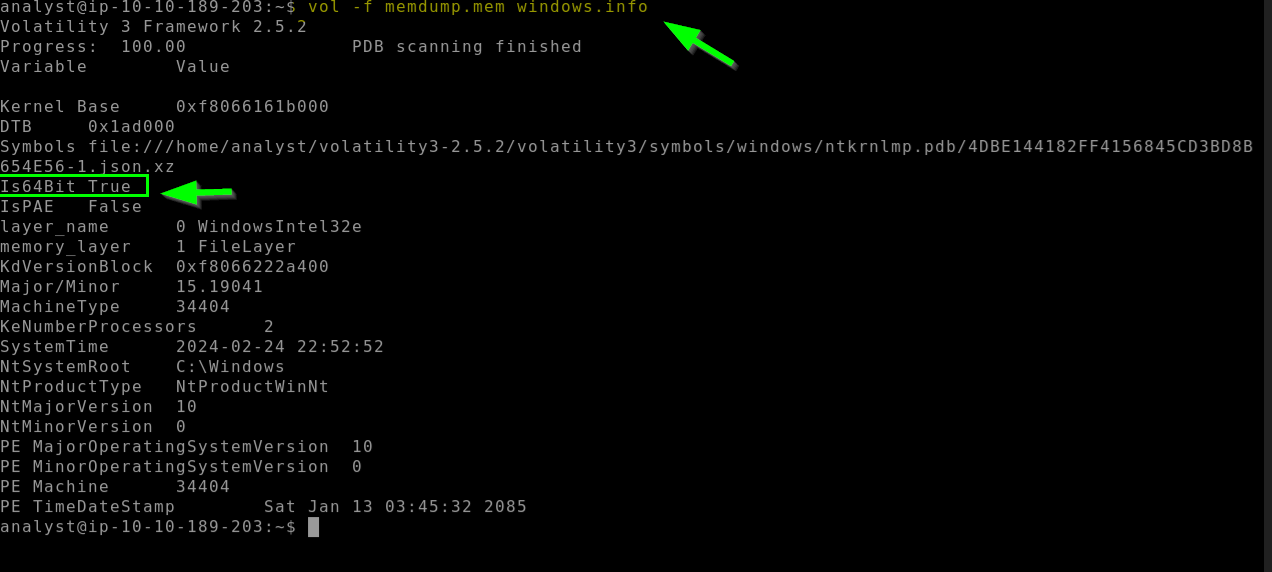
Y
4.2. What is the Verison of the Windows OS
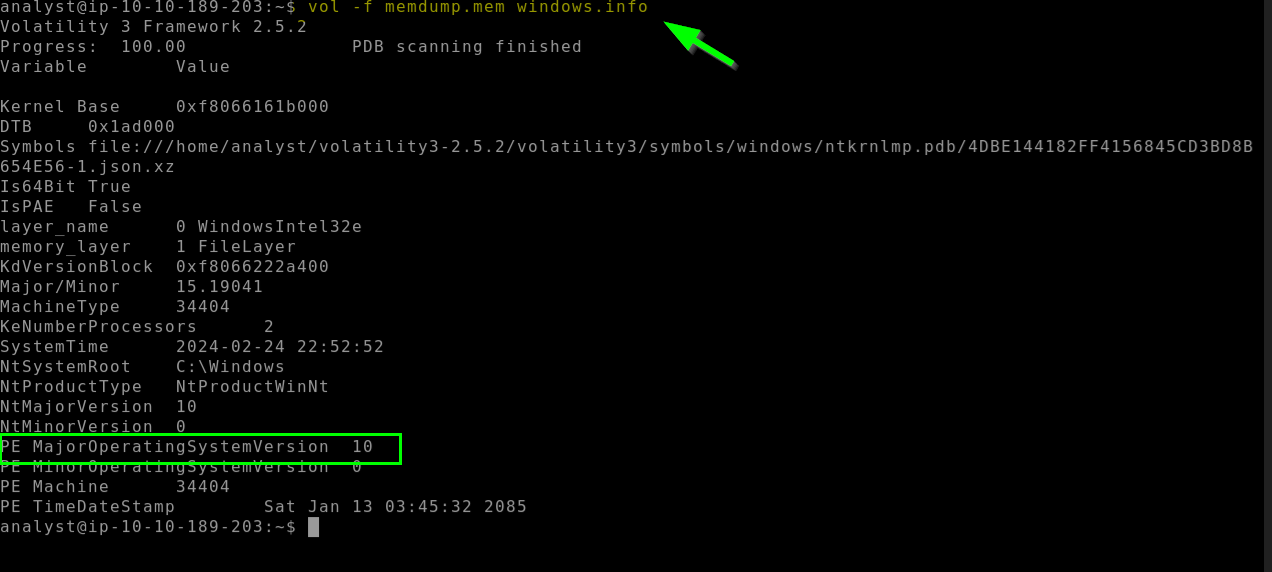
10
4.3. What is the base address of the kernel?
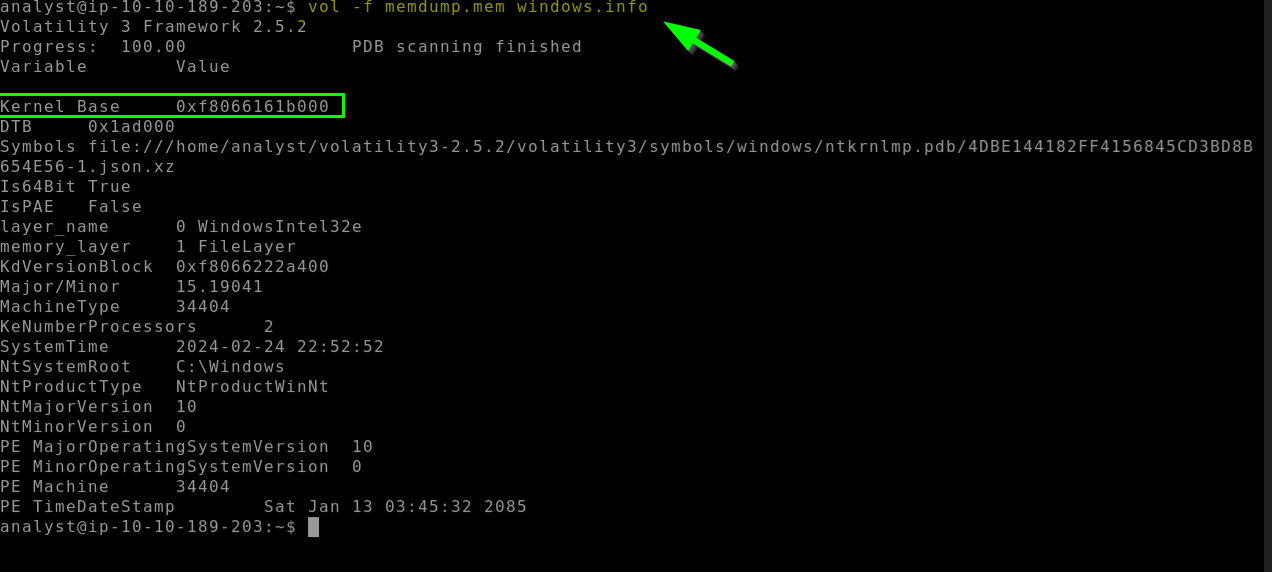
0xf8066161b000
Task 5: Searching for Suspicious Activity
5.1. Using the plugin “windows.netscan” can you identify the IP address that establish a connection on port 80?
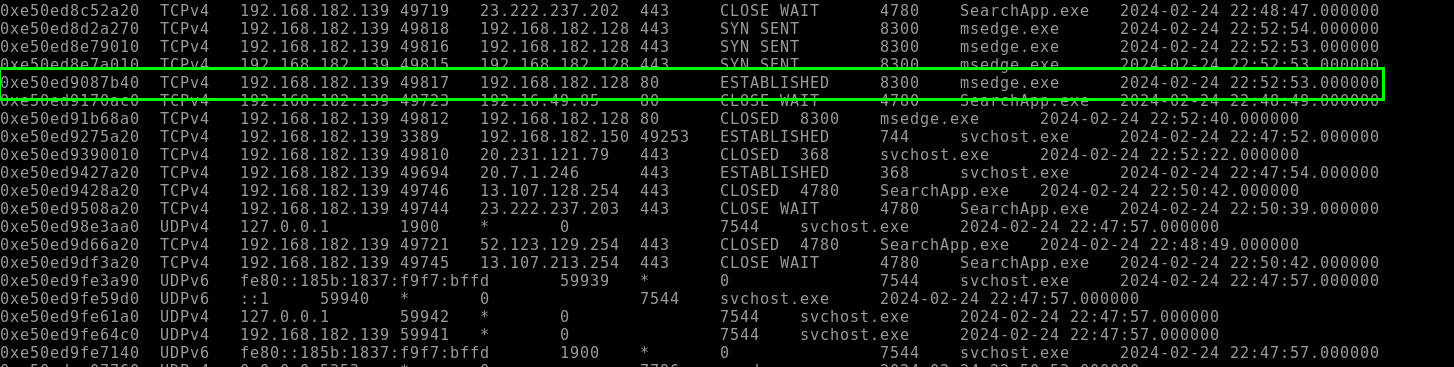
192.168.182.128
5.2. Using the plugin “windows.netscan,” can you identify the program (owner) used to access through port 80?
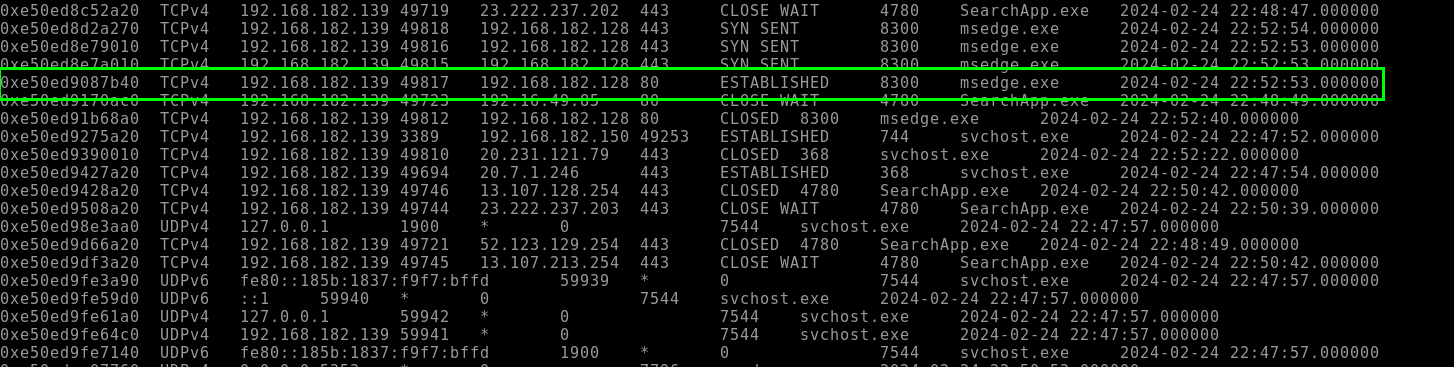
msedge.exe
5.3. Analyzing the process present on the dump, what is the PID of the child process of critical_updat?
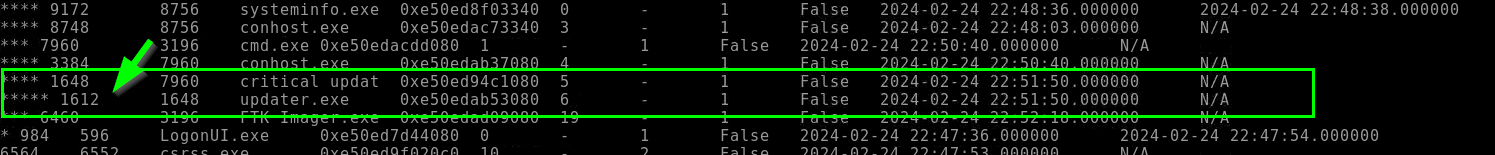
1612
5.4. What is the time stamp time for the process with the truncated name critical_updat?
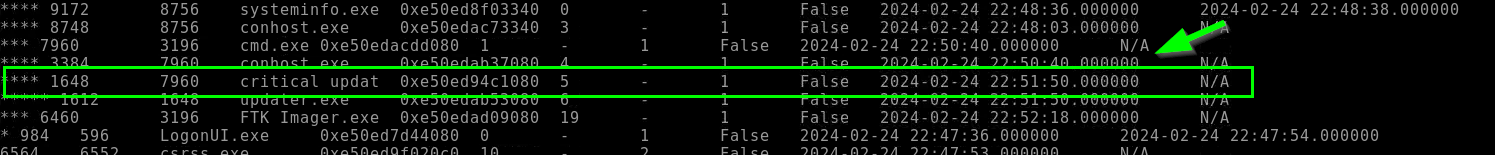
2024-02-24 22:51:50.000000
Task 6: Finding Interesting Data
6.1. Analyzing the “windows.filescan” output, what is the full path and name for critical_updat?
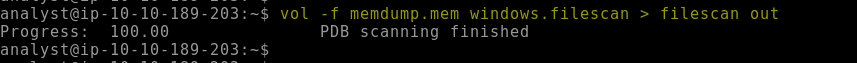
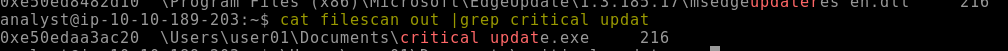
\Users\user01\Documents\critical_update.exe
6.2. Analyzing the “windows.mftscan.MFTScan” what is the Timestamp for the created date of important_document.pdf?
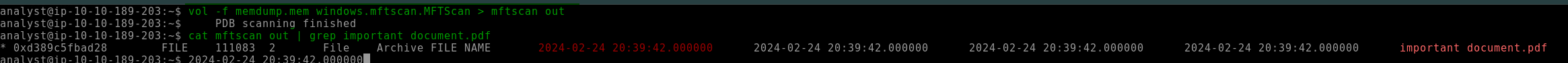
2024-02-24 20:39:42.000000
6.3. Analyzing the updater.exe memory output, can you observe the HTTP request and determine the server used by the attacker?
SimpleHTTP/0.6 Python/3.10.4

