CTF link.
A long web question awaits us 😊
To access the flag on our first page, we need to view the source of the page.
At the very end of the page source we will reach a URL again.
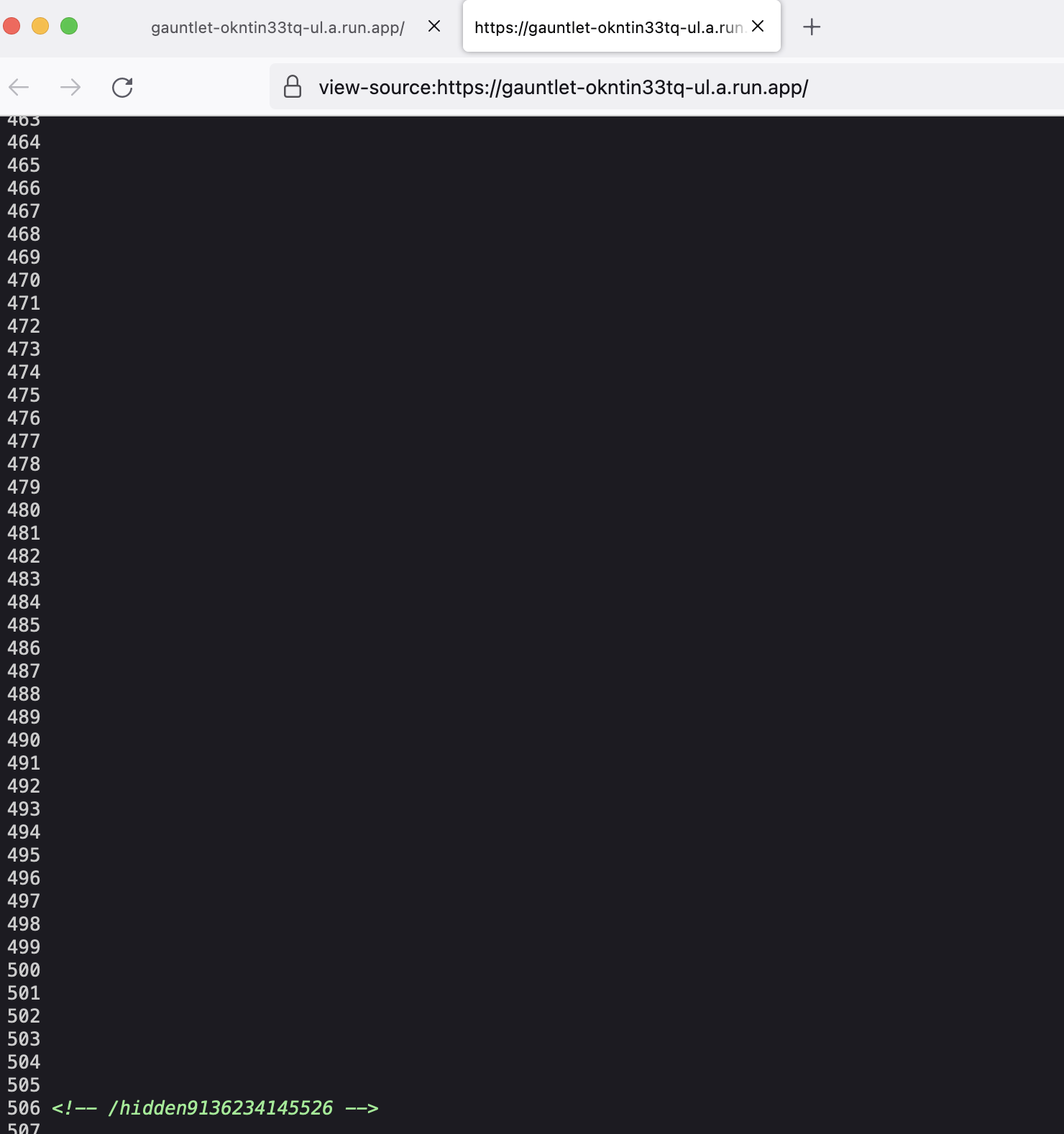
Page 1
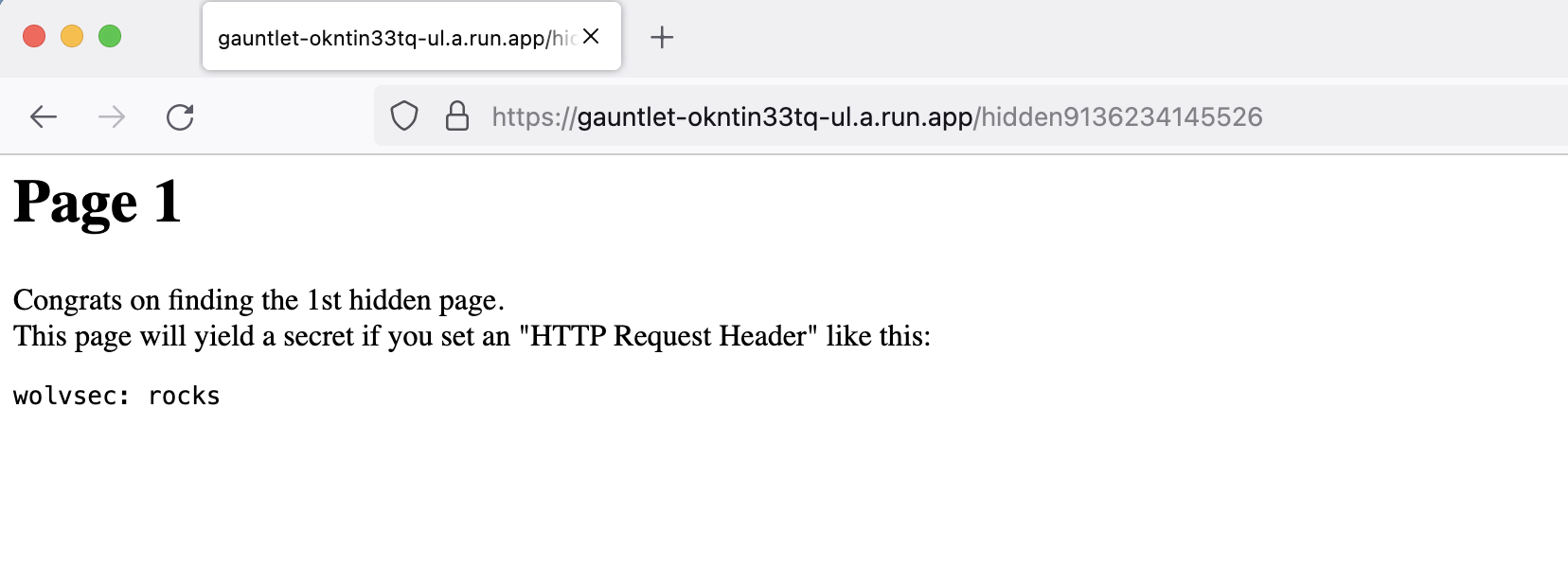
When we go to the URL, we get the following result:
We edit the HTTP header with burp suite and get the new URL.
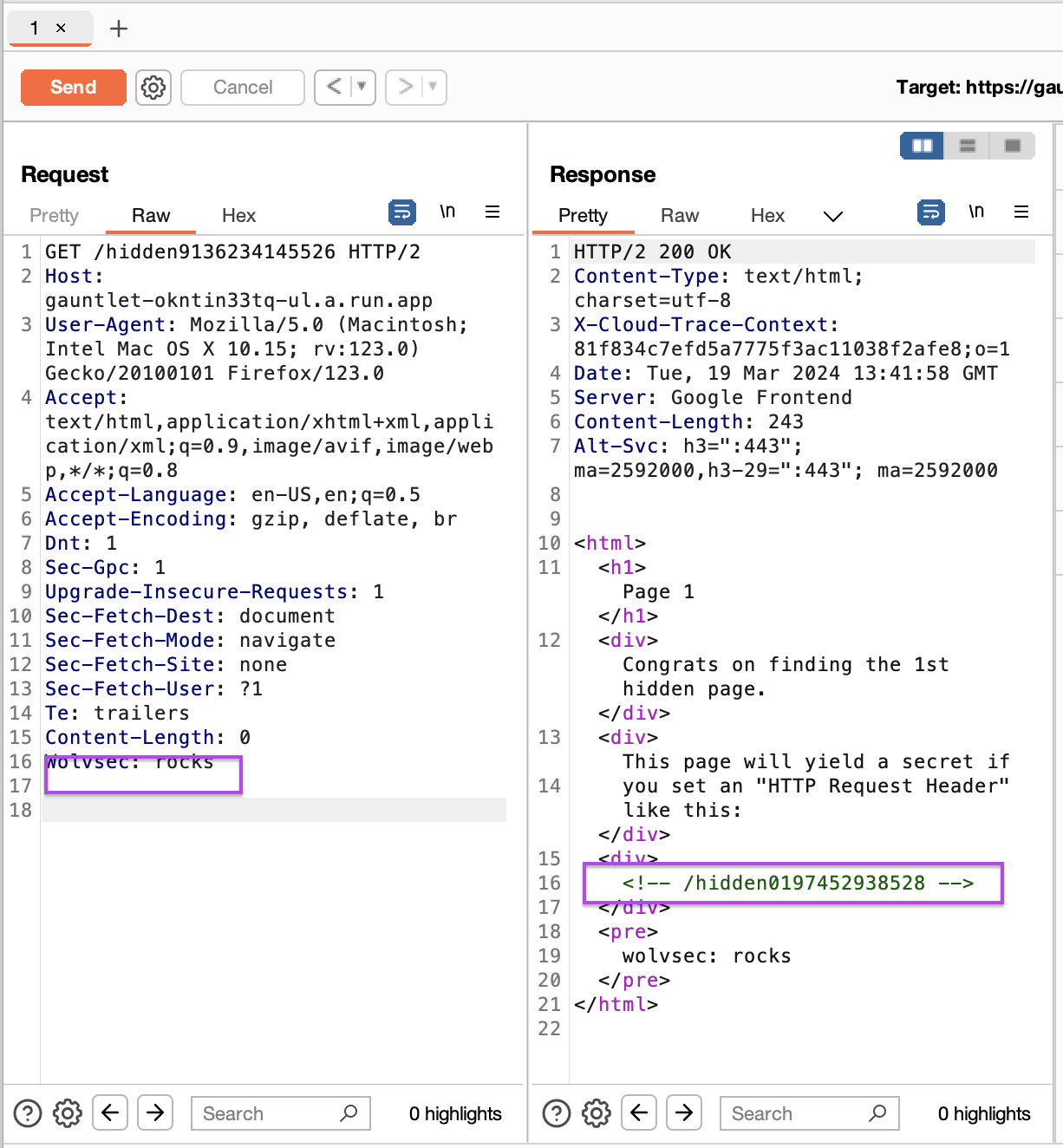
Page 2
The new URL also tells us to change our HTTP method and even includes a link to help us.
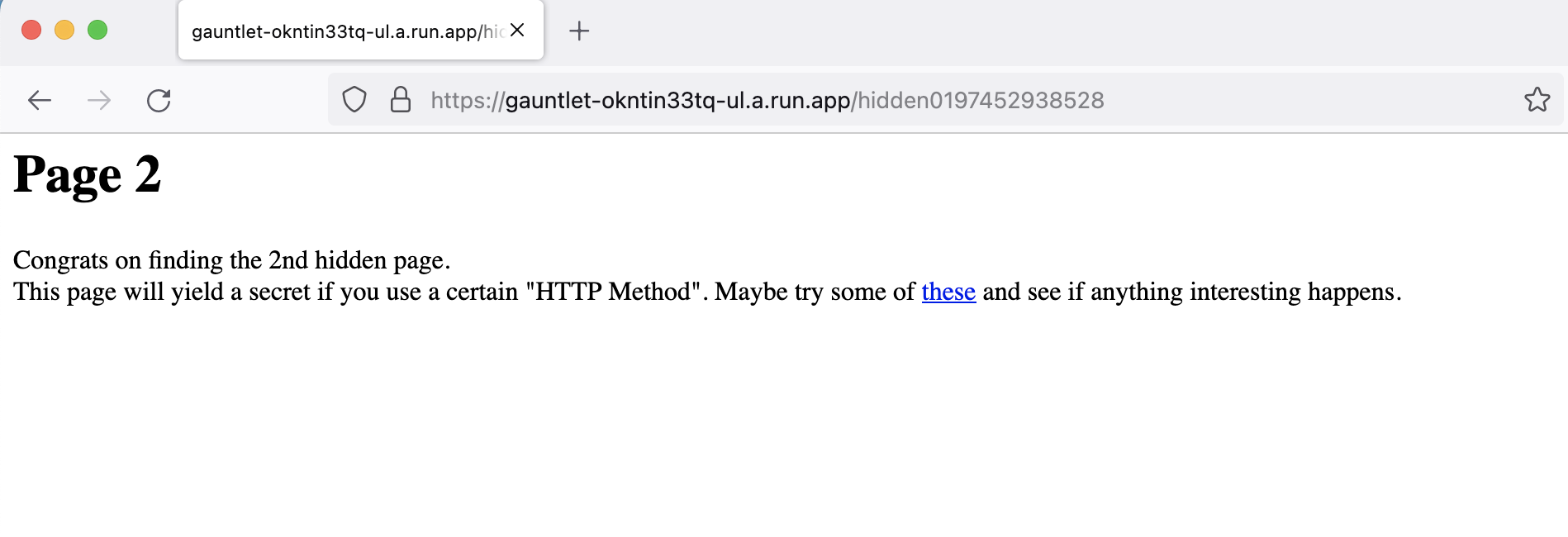
If we make our method OPTIONS, we will reach the new URL.
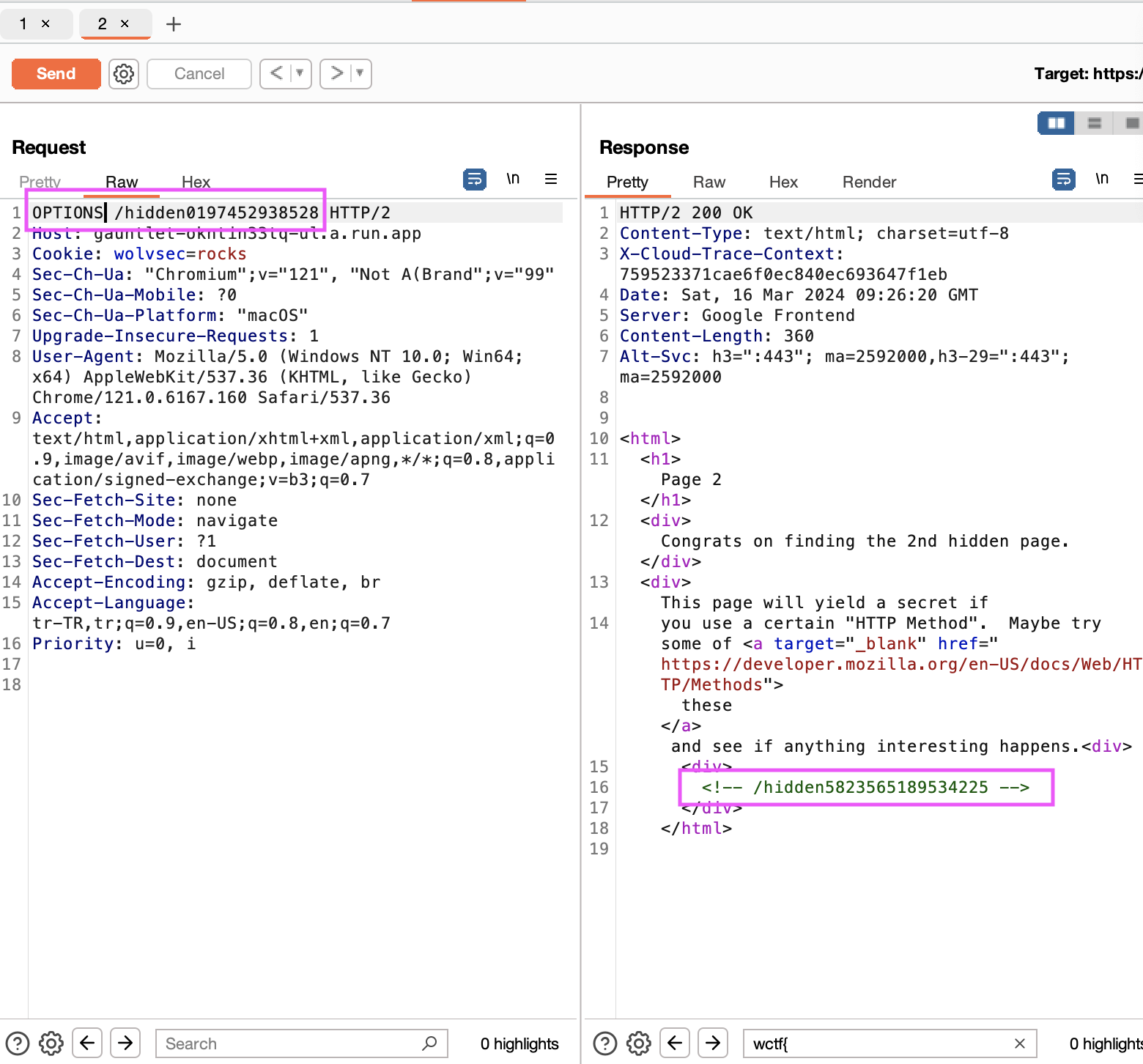
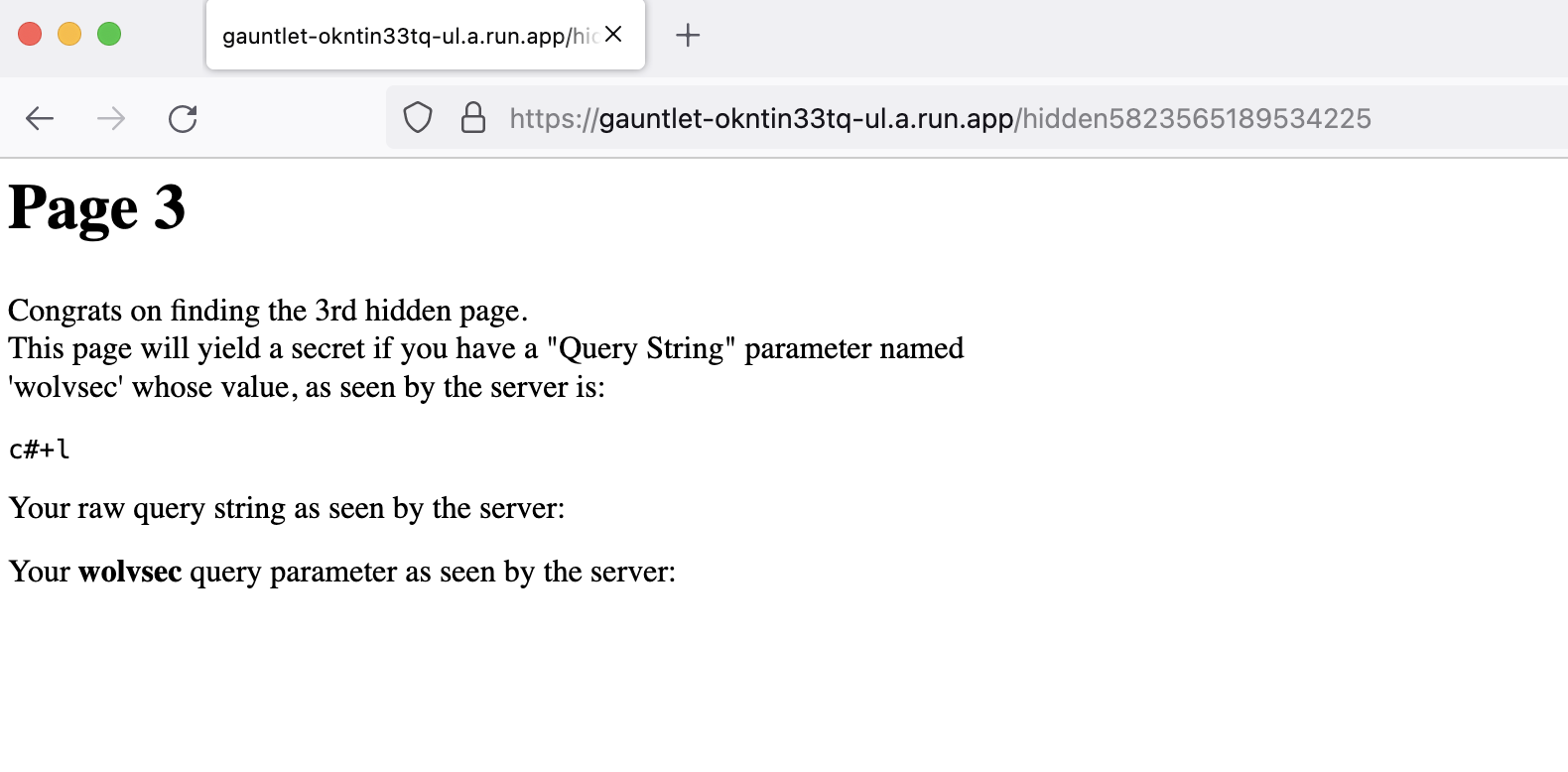
Page 3
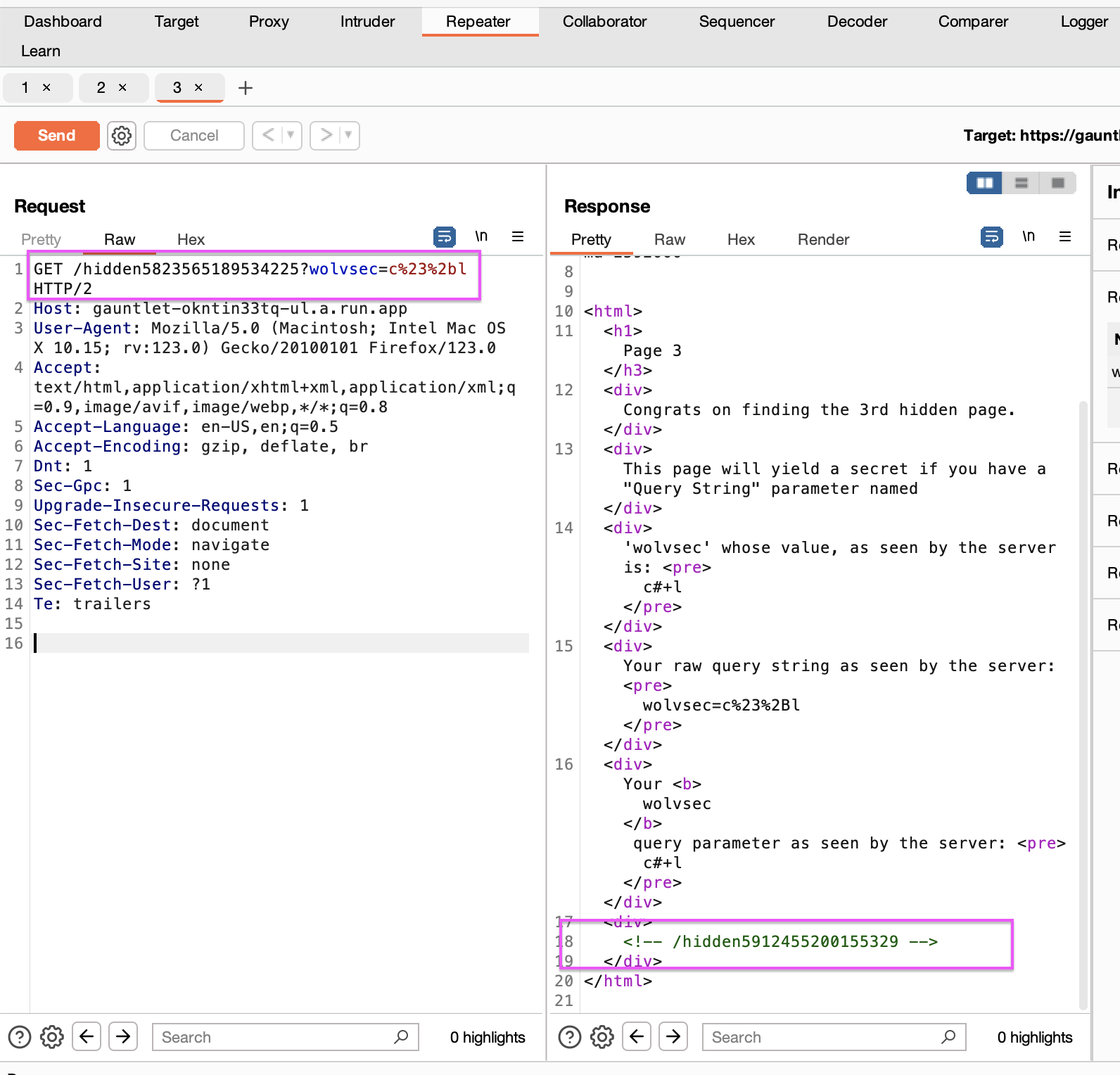
We need to edit the Query String according to the value it gives, attention should be paid to URL encoding here.
Edited HTTP request:
Page 4
We need to convert our GET request into a POST request and make certain changes.
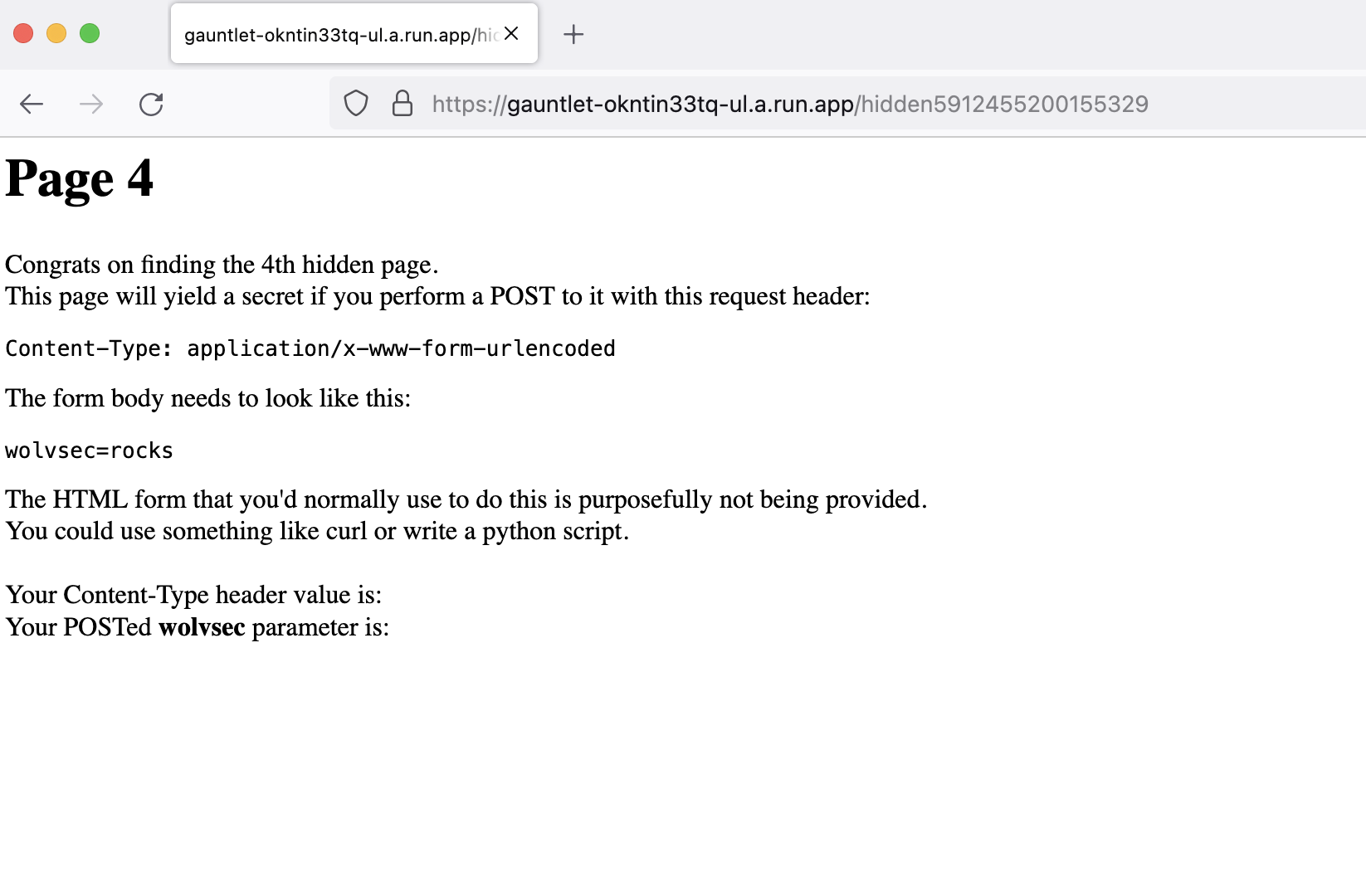
We can do this either from burp or from curl, I am attaching both visually.
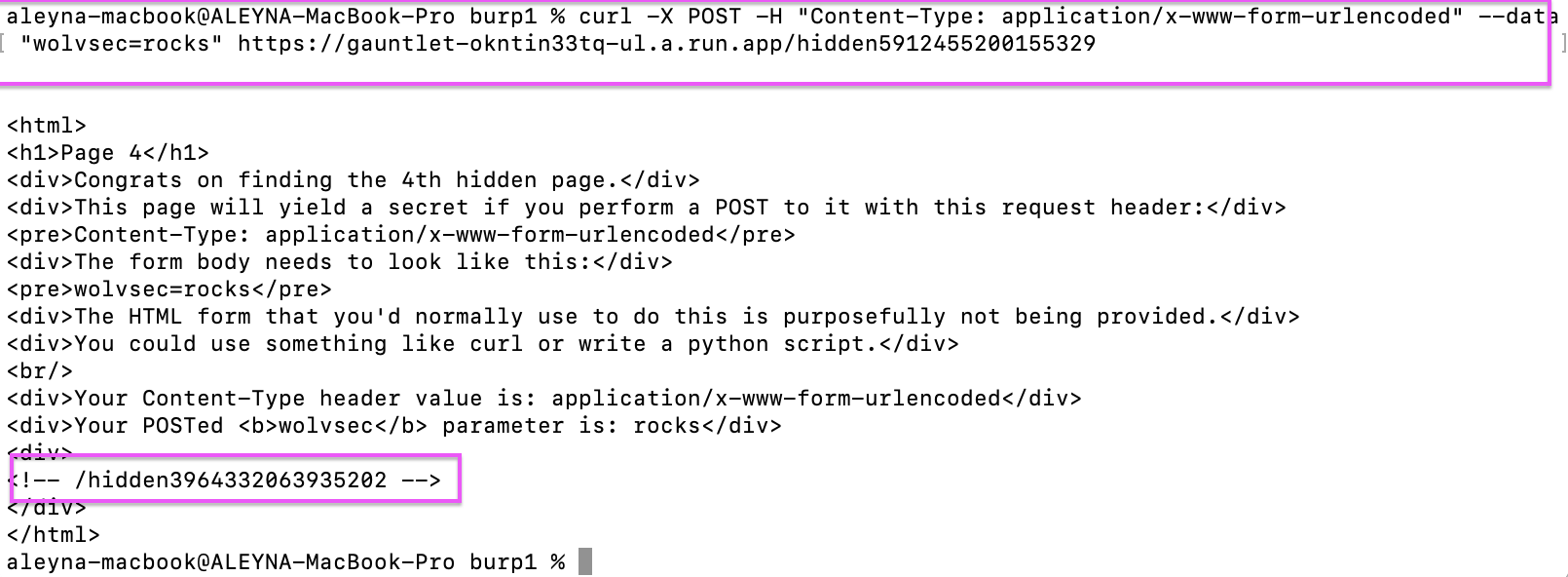
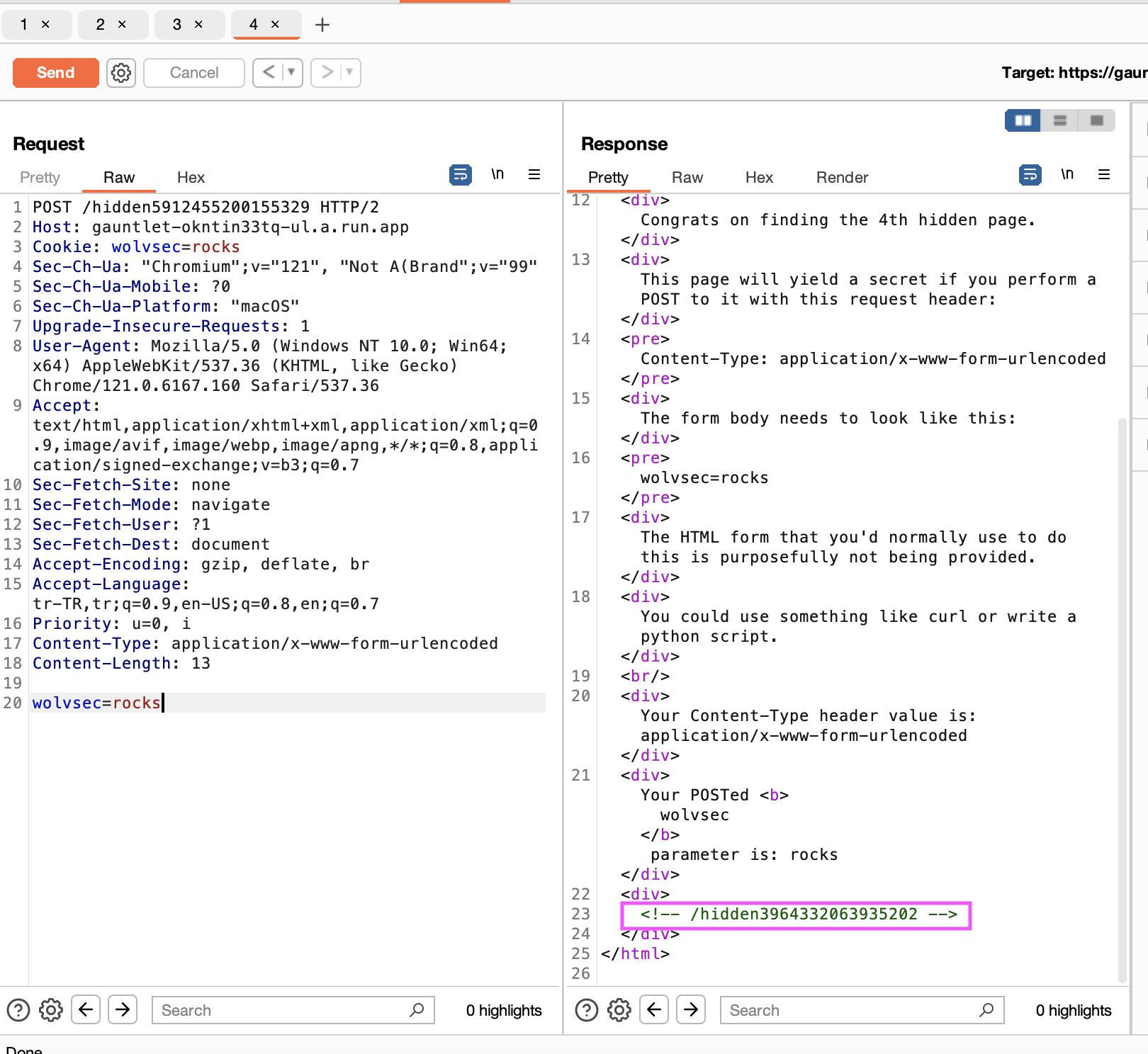
Page 5
Our new URL talks about understanding JavaScript.
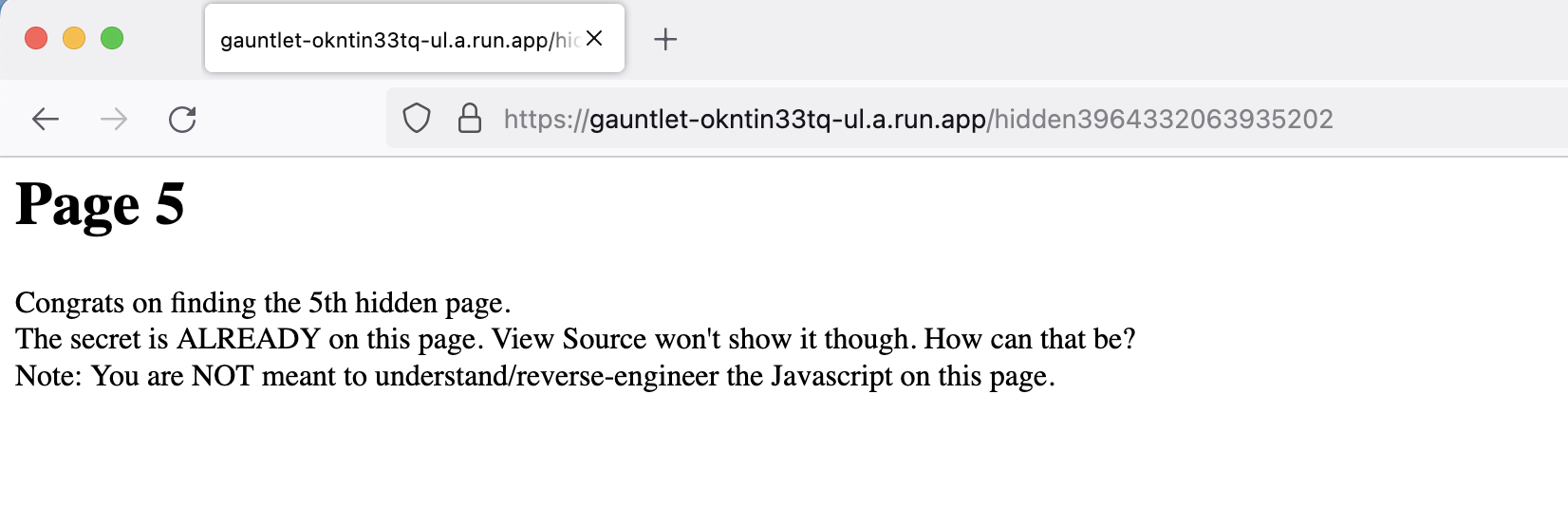
We can make our HTML file and edit the source code to get the flag. There is no javascript result, so we make the necessary additions to the code in the result.
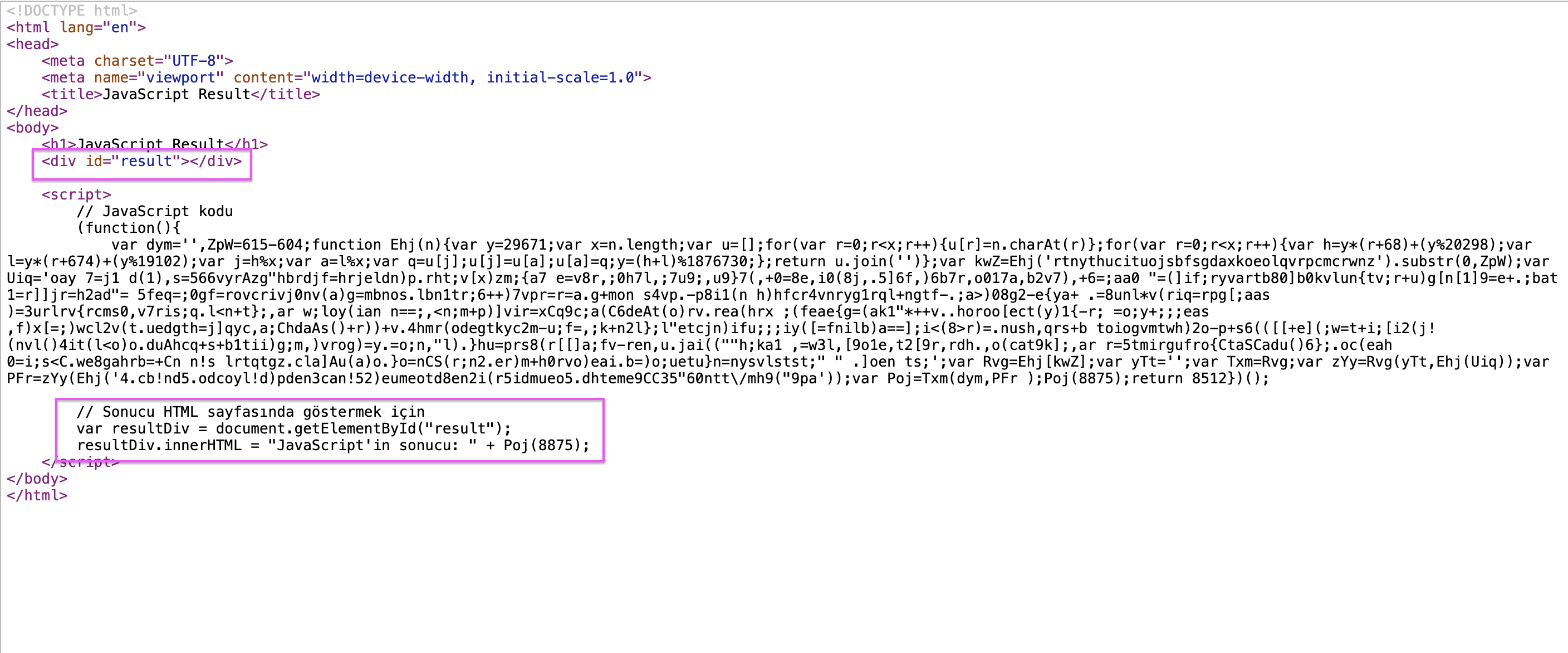
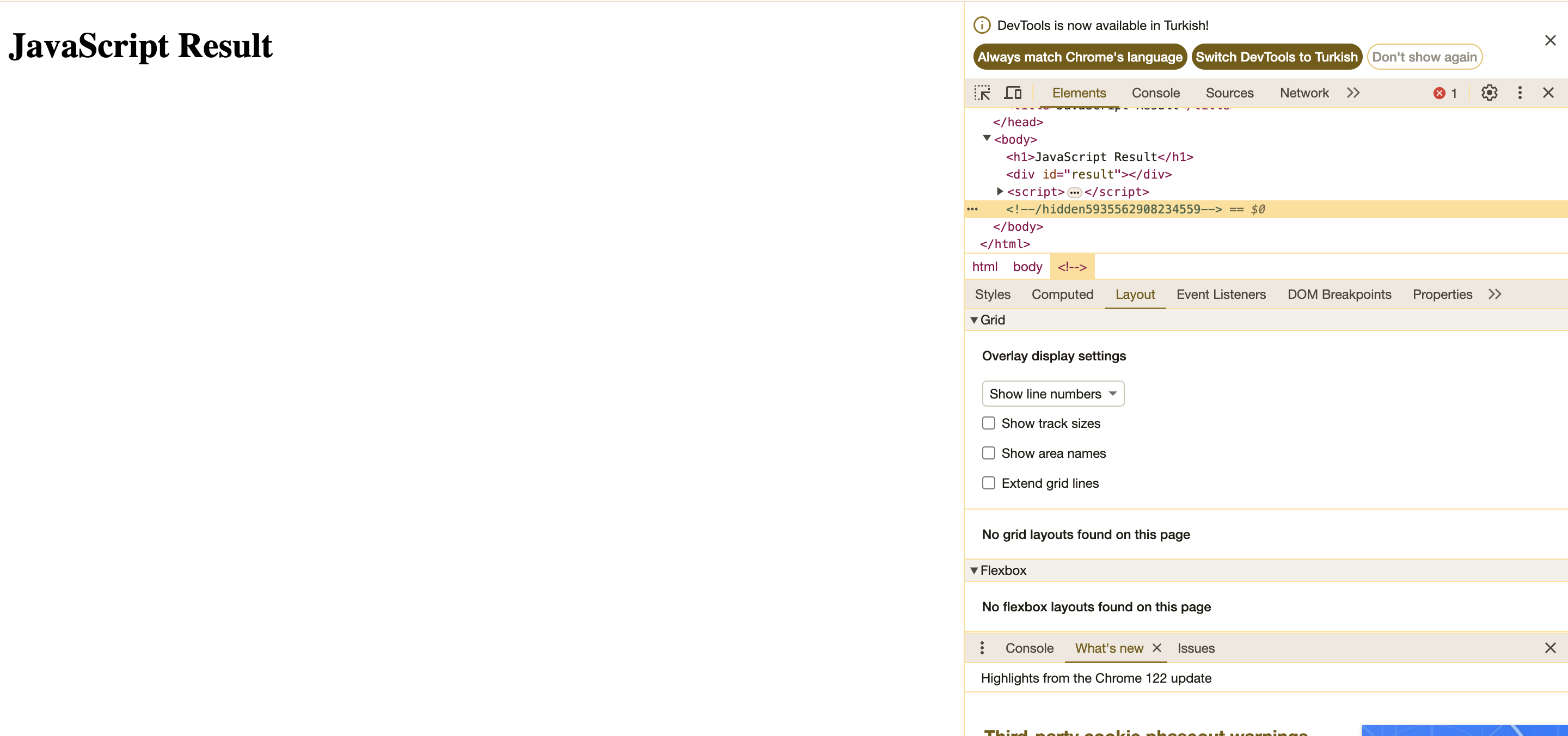
Page 6
The new URL says that this URL is not the URL we found. The URL made a redirect if you follow it with burp while running the URL we found. you can see that there are extra requests.
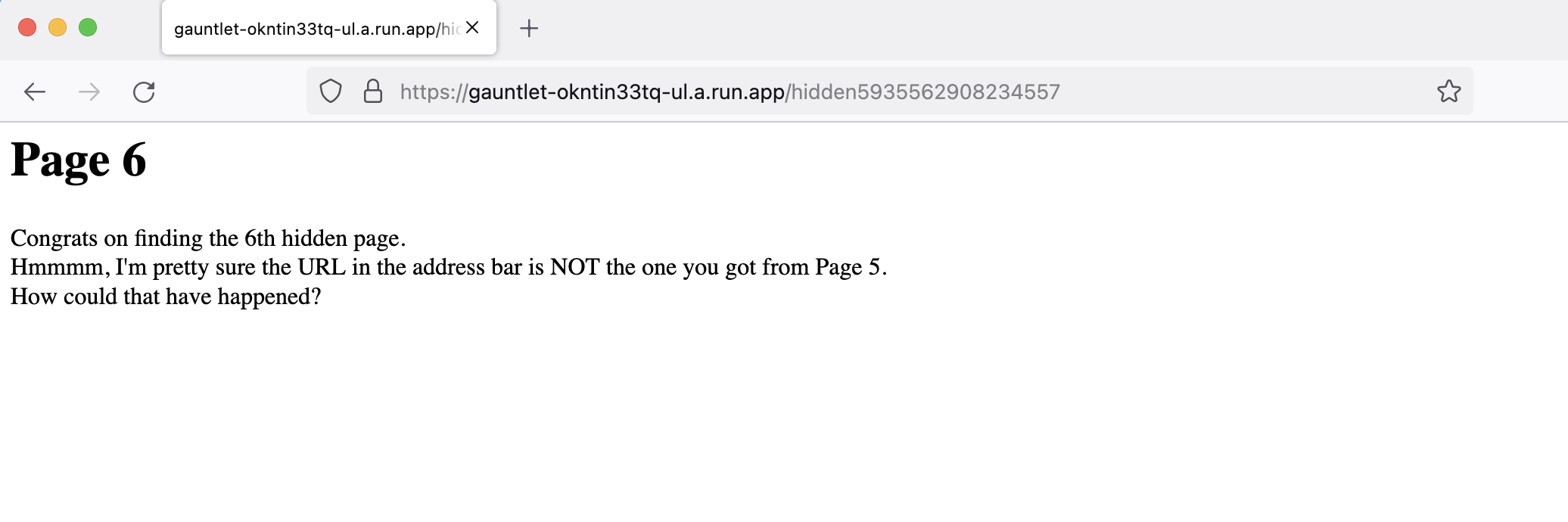
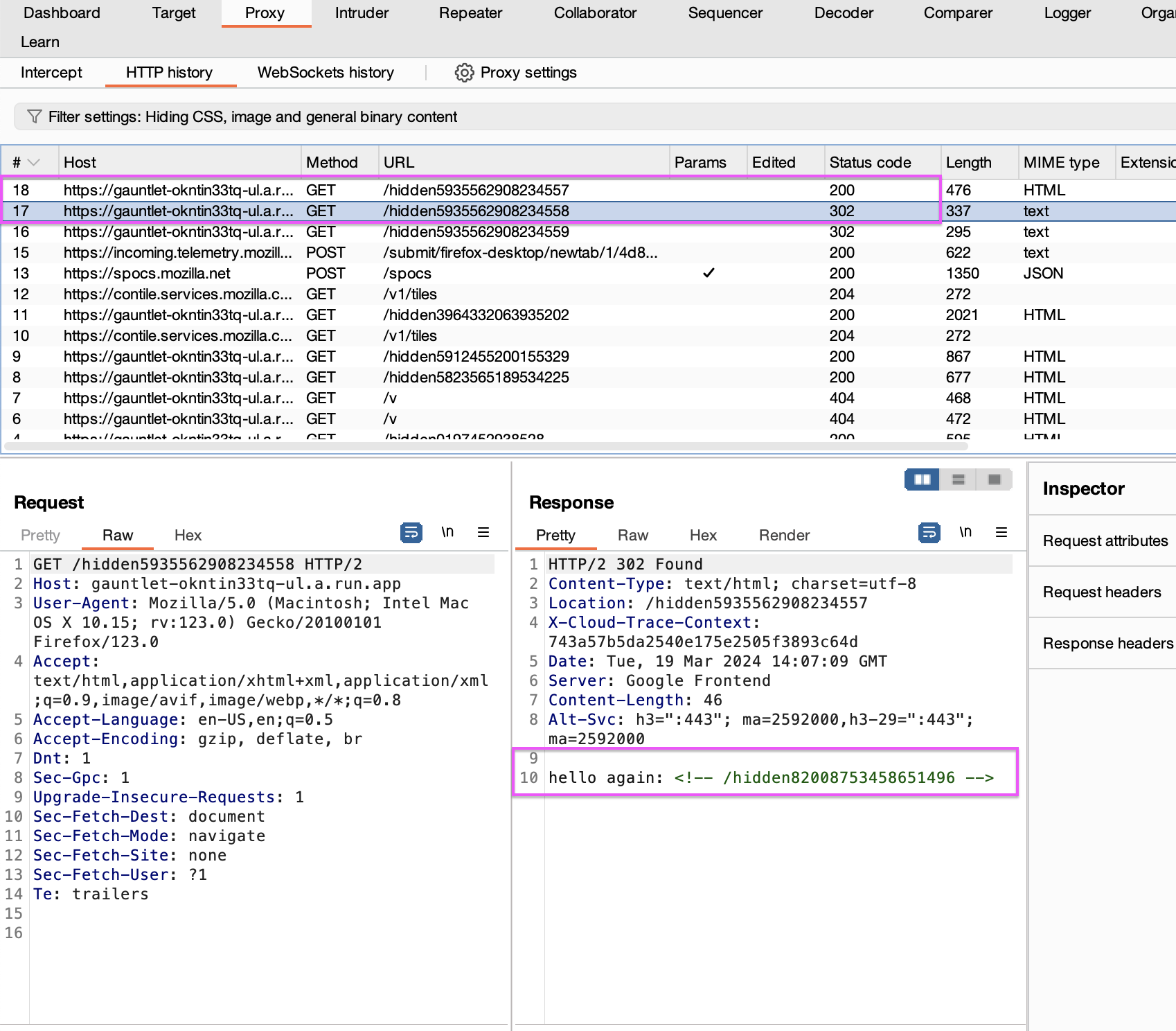
Page 7
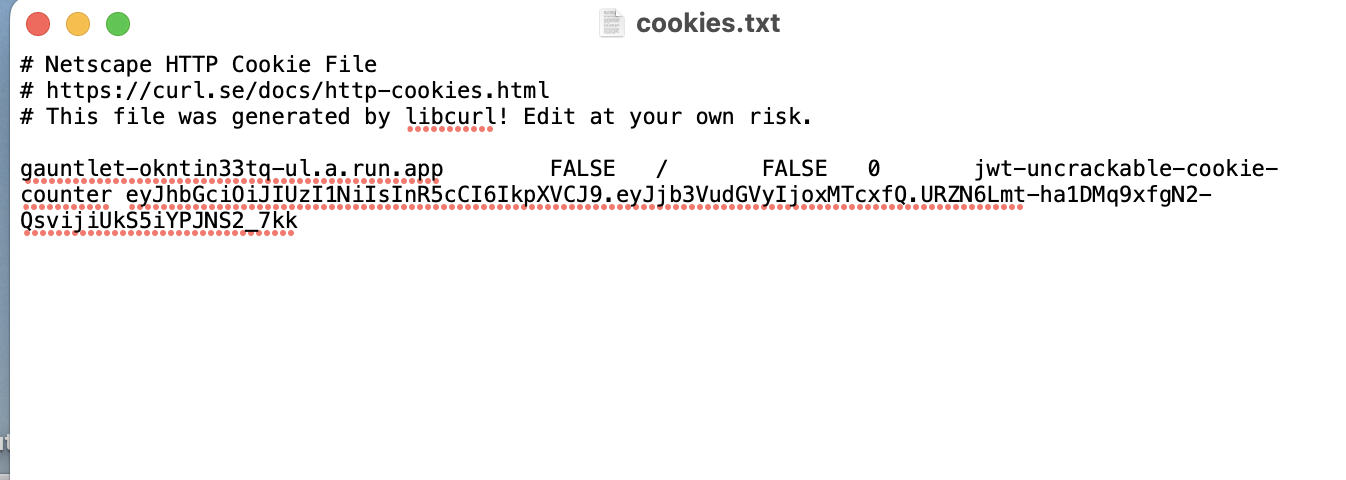
In the new URL, we need to visit the page 500 times. We can handle this with cookies.
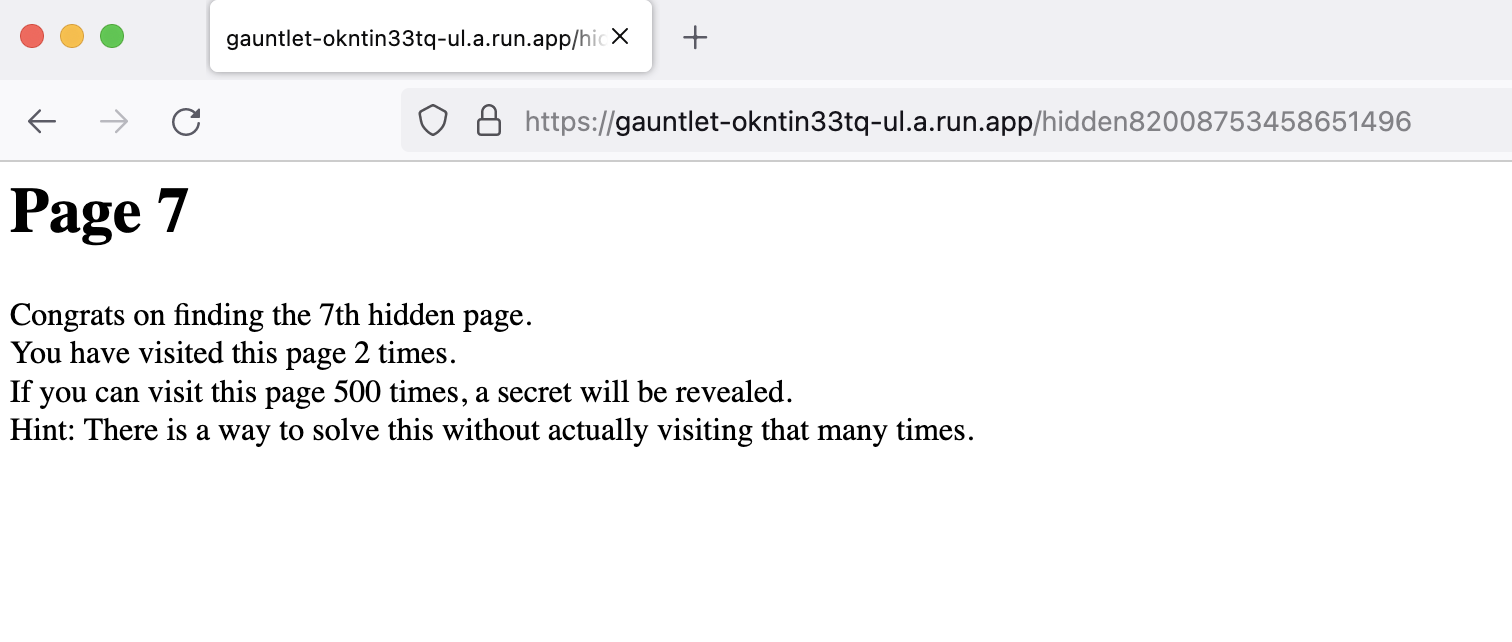
We set the cookie value to 500 and we can access the new URL from the page source code.
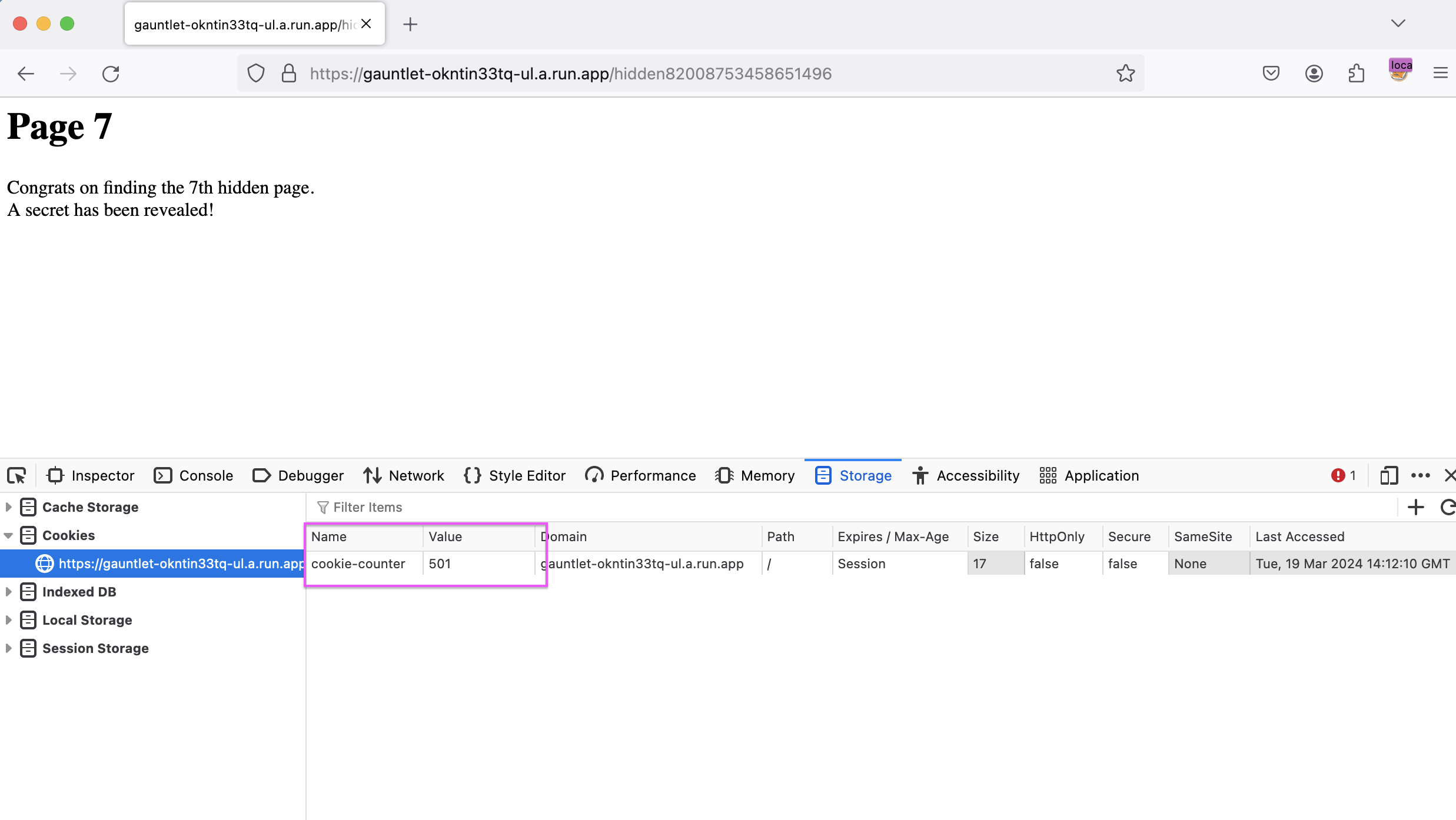
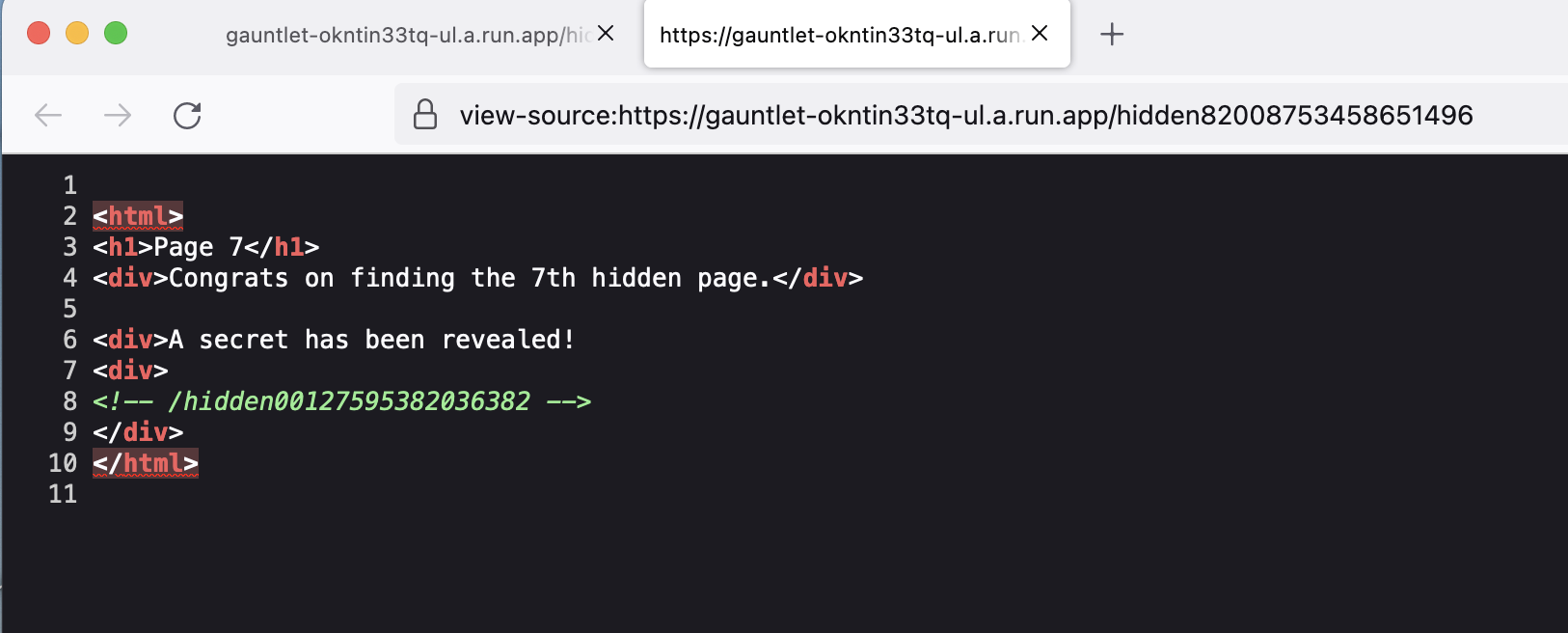
Page 8
We perform the solution using jwt.io. and the rules given in the question
Video solution:
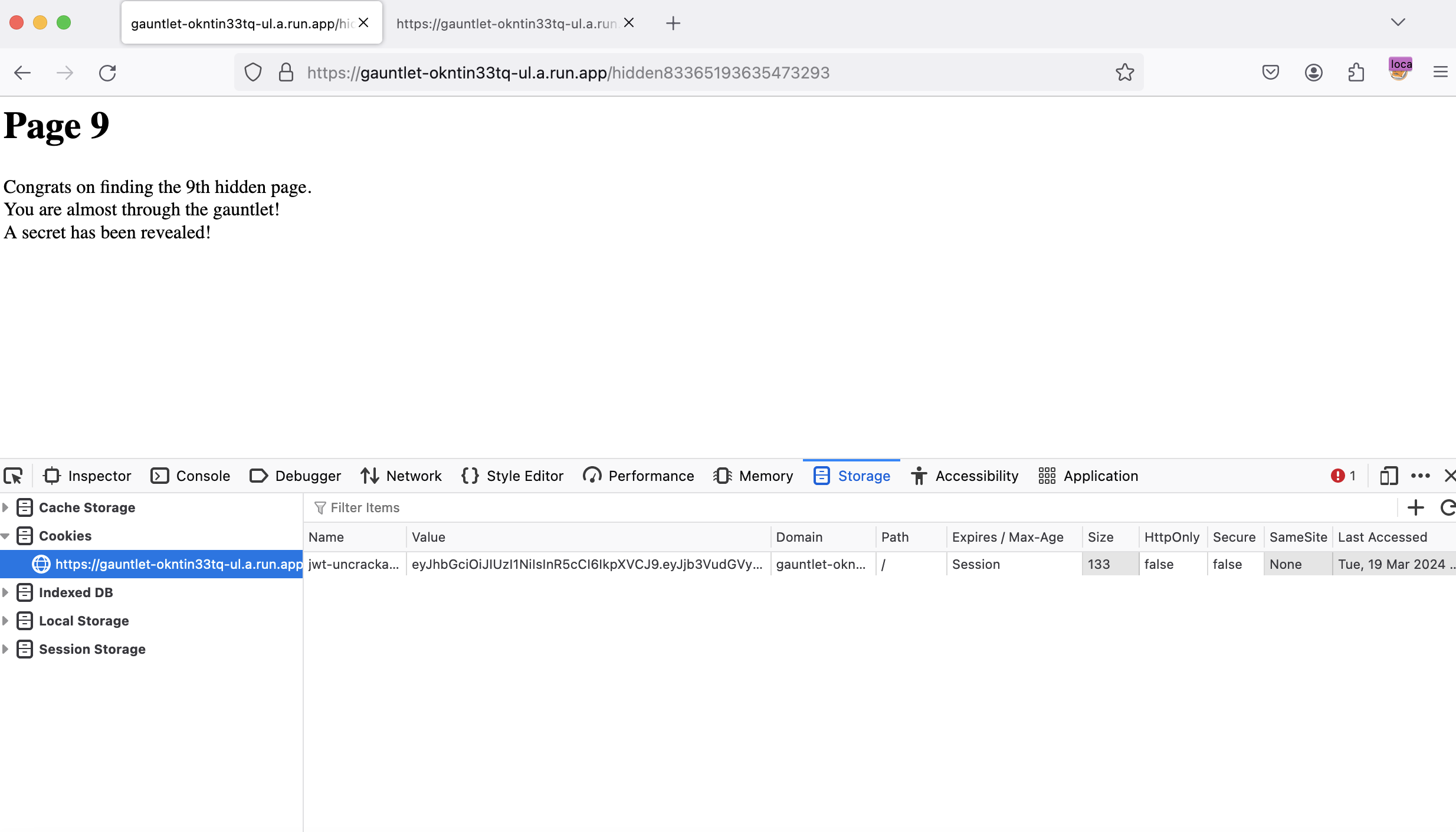
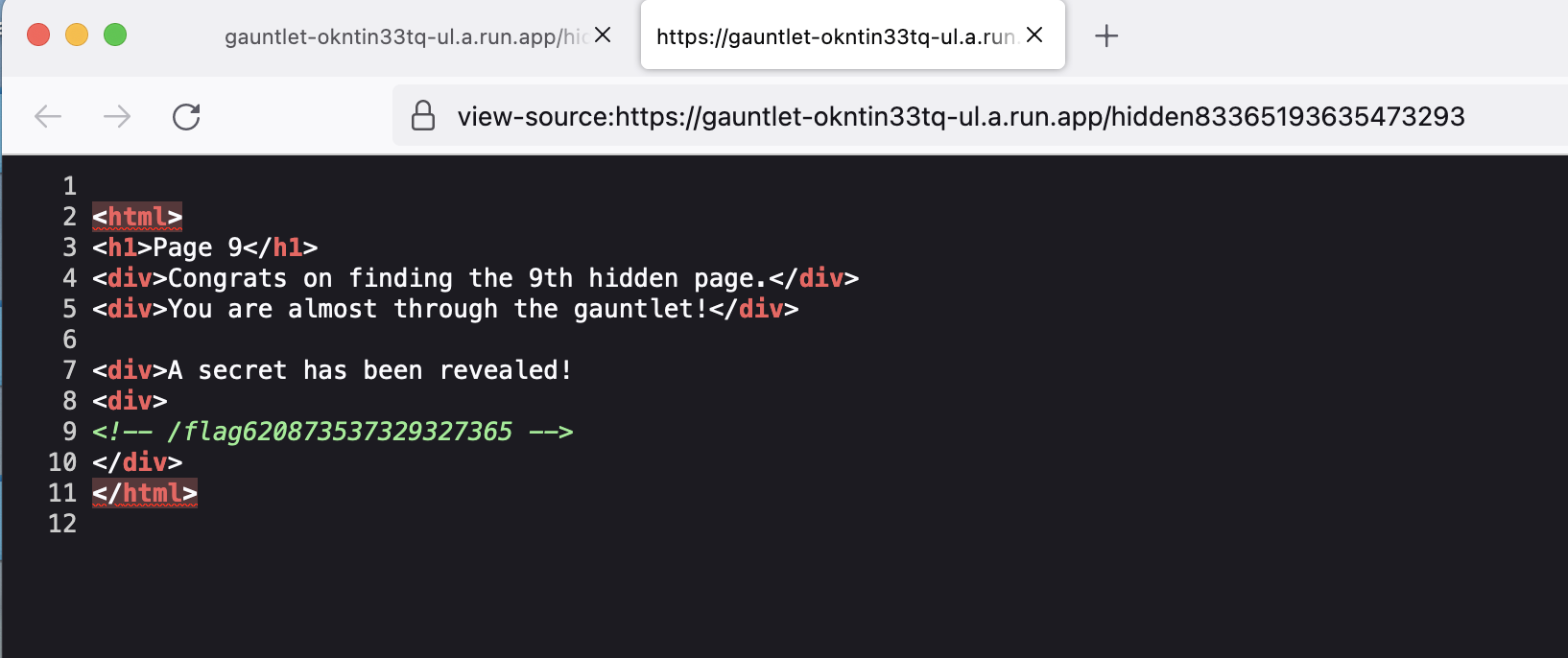
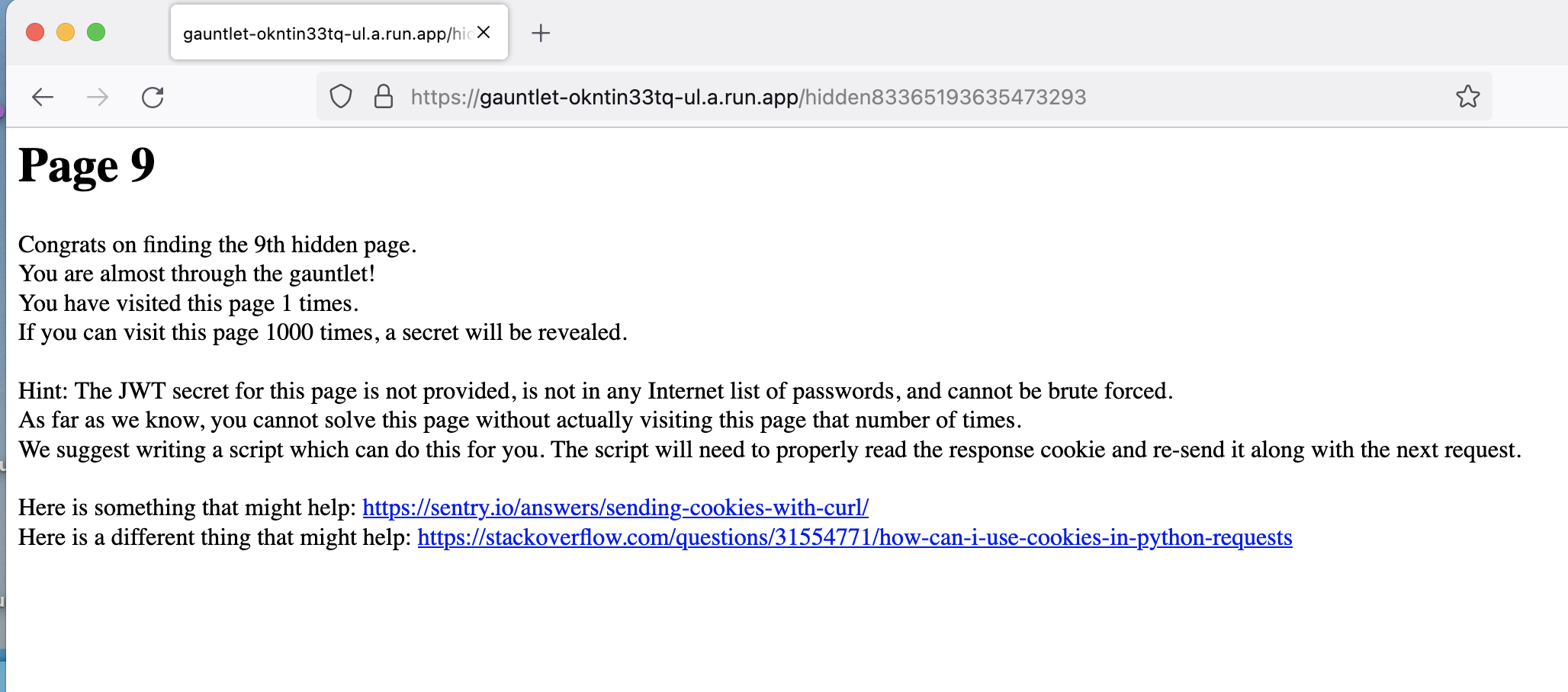
Page 9
The script we will write needs to read the response cookie and resend it with the next request, the code I use for this is below:
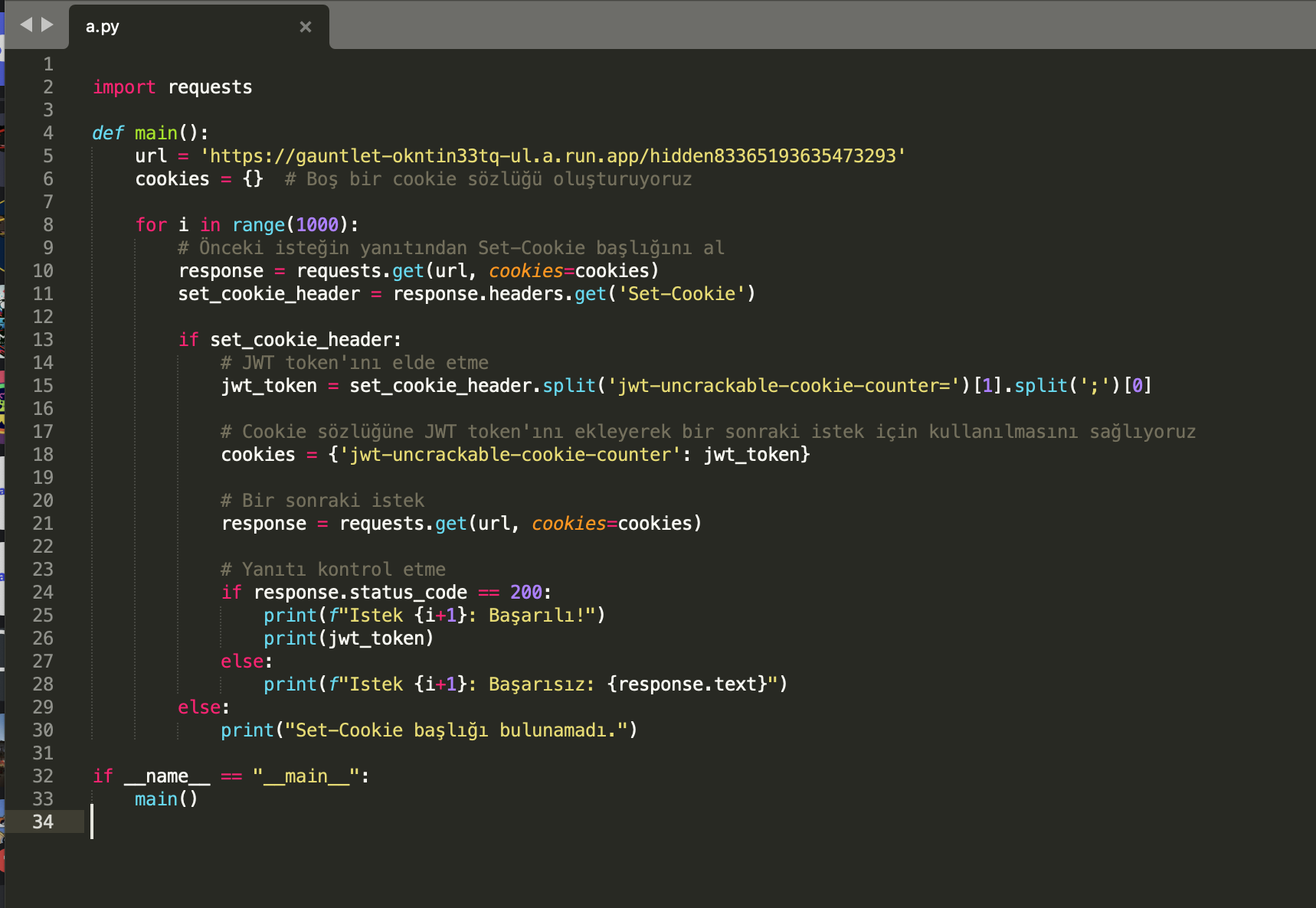
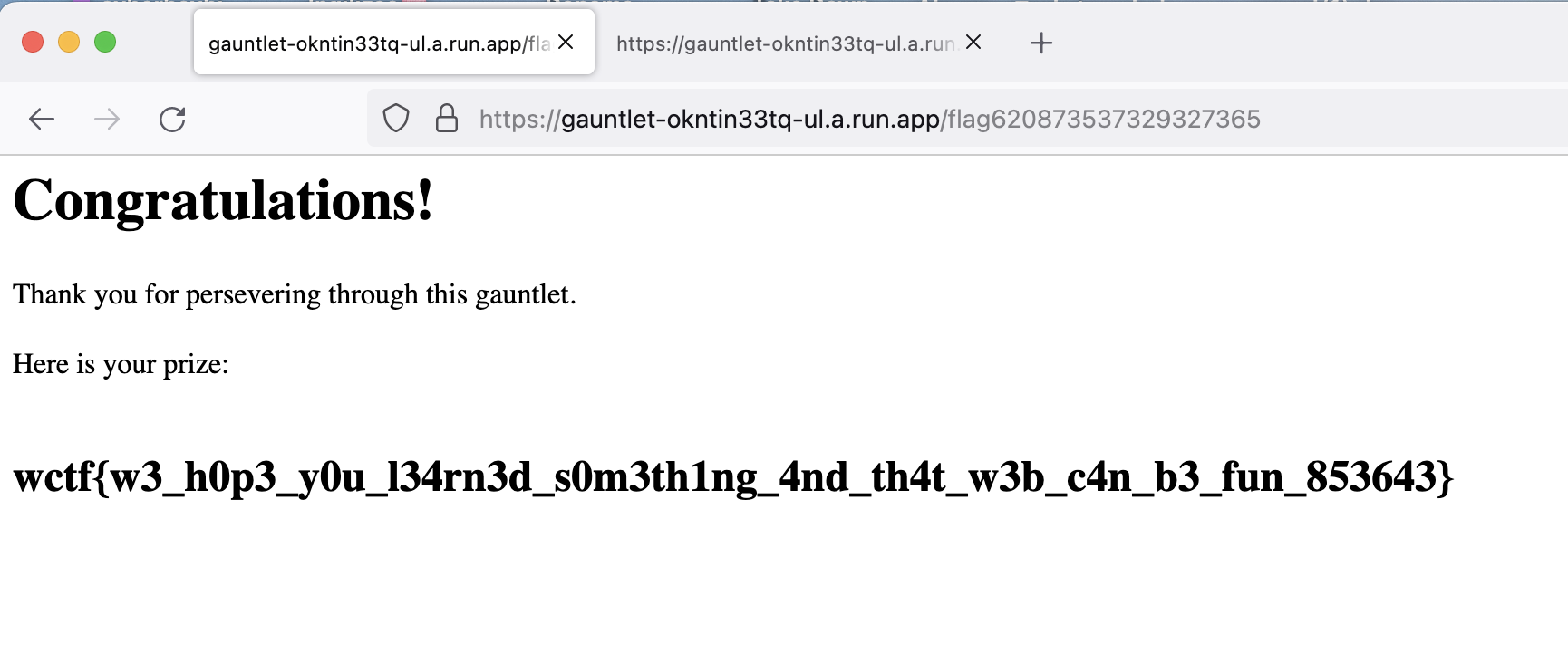
If we place the jwt we get as a result of the code in the cookie, we get the flag.