CTF link.
In the wake of recent security breaches, it has become paramount to ensure the integrity and safety of our systems. A routine audit of our admin activity logs has revealed several anomalies that could suggest a breach or an attempted breach. These logs are critical to understanding the actions taken by users with administrative privileges and identifying any that could have jeopardized our network’s security. Your task is to analyze the provided admin activity logs to identify any suspicious activities.
If we delete the generic HTML pages (index.html) in the log file, we are left with one different URL.
192.168.0.8 – – [26/Feb/2024:08:46:37 -0500] “GET /admin/ufile.io/y8ls94tu HTTP 1.1” 401 2048
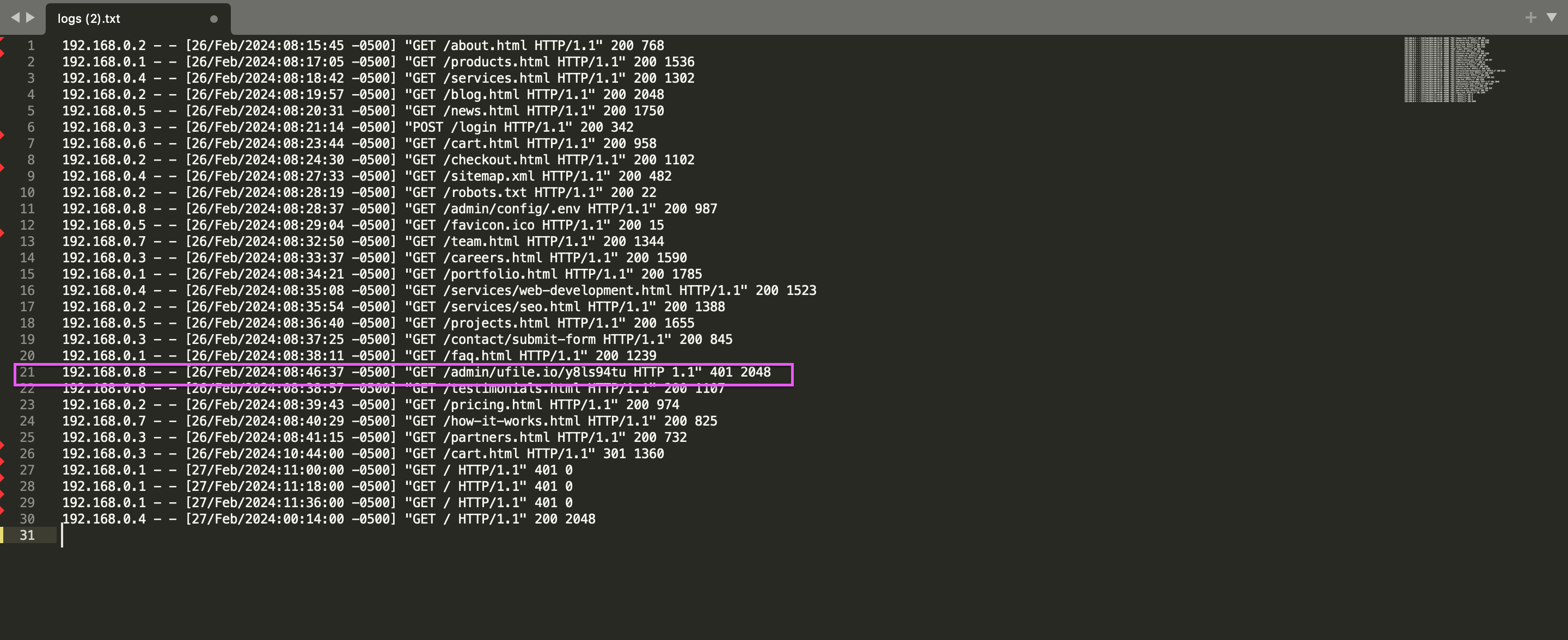
We go to this ufile.io/y8ls94tu URL
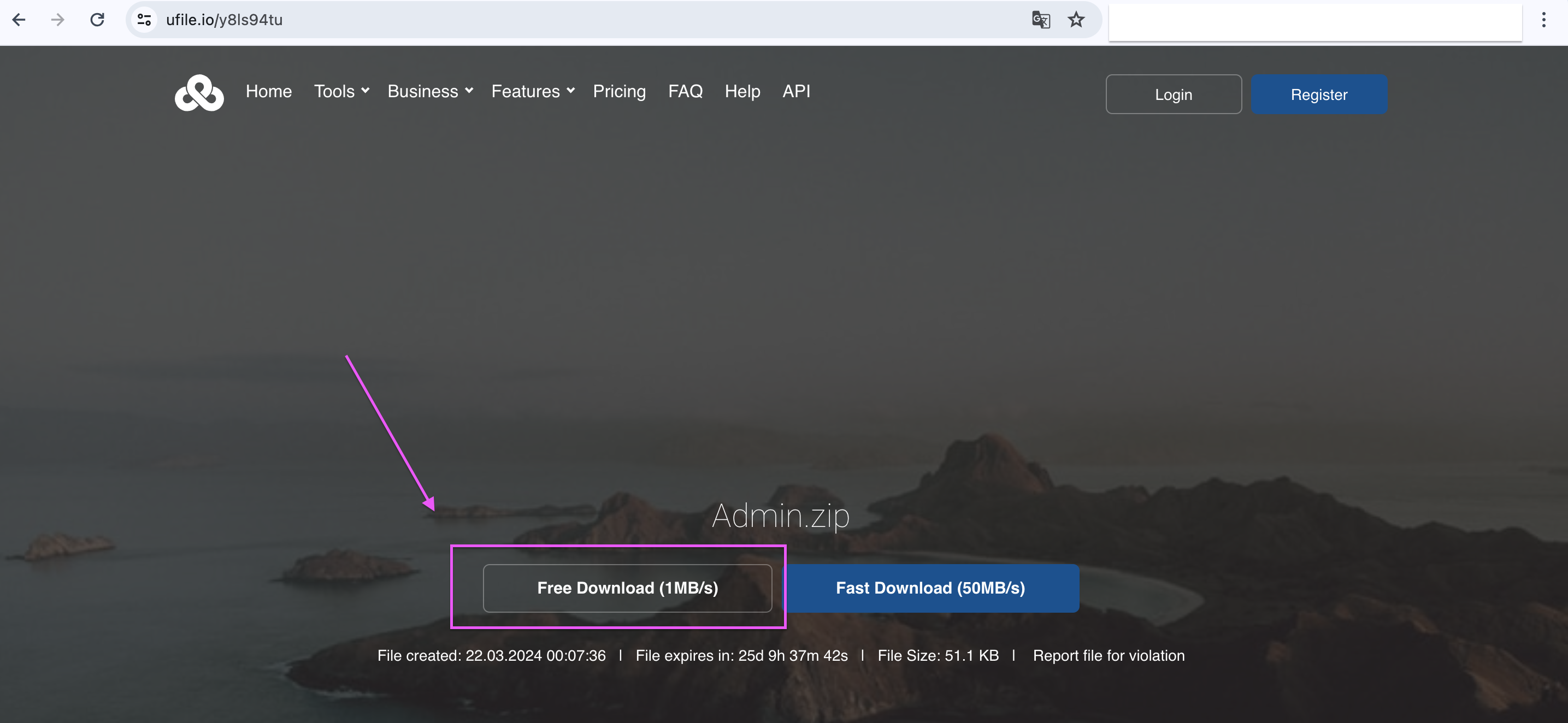
We download the file in the URL and there are many CSV files in it, if you want you can search for texsaw{ flag in the content of the files with the grep command. user.csv contains flag.
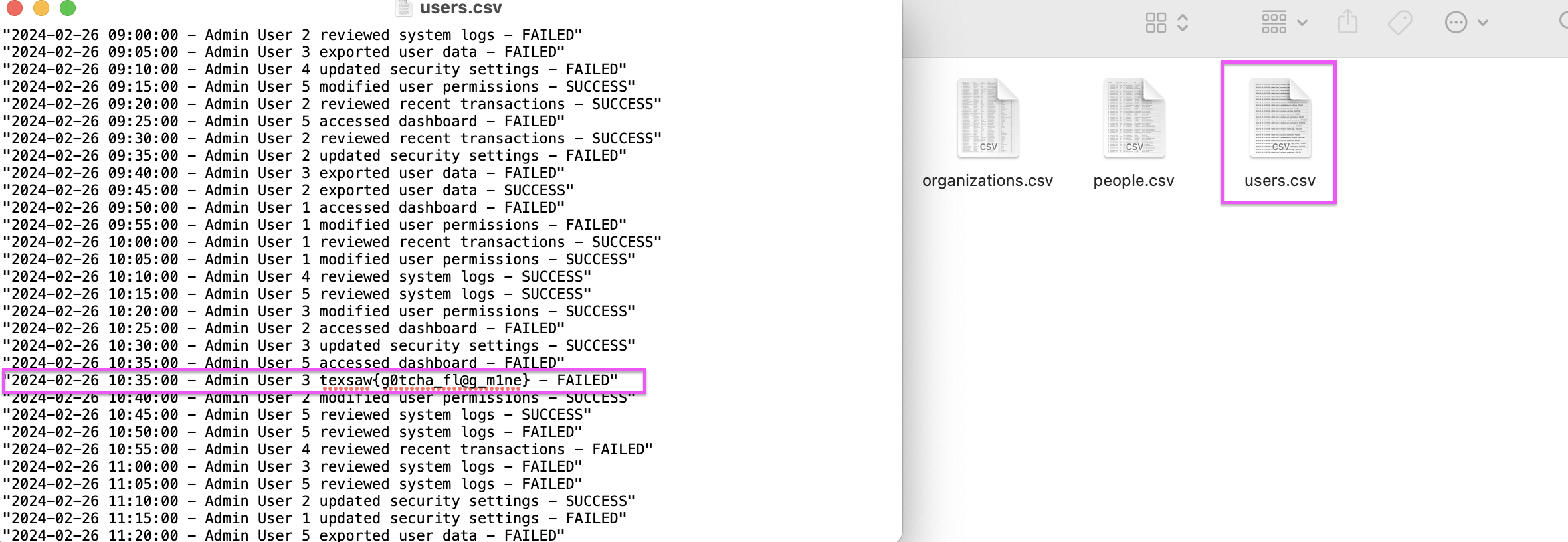
texsaw{g0tcha_fl@g_m1ne}
