McSkidy suspects that an attacker simulated an intrusion using the T1566.001 Spearphishing with an attachment technique defined in the MITRE ATT&CK framework. We will recreate this attack and analyze the artifacts left behind.
PowerShell Usage
1. Running the Help Command in PowerShell
First, the Get-Help Invoke-AtomicTest command is run to get information about what the command does and what parameters are available.
Sample output:
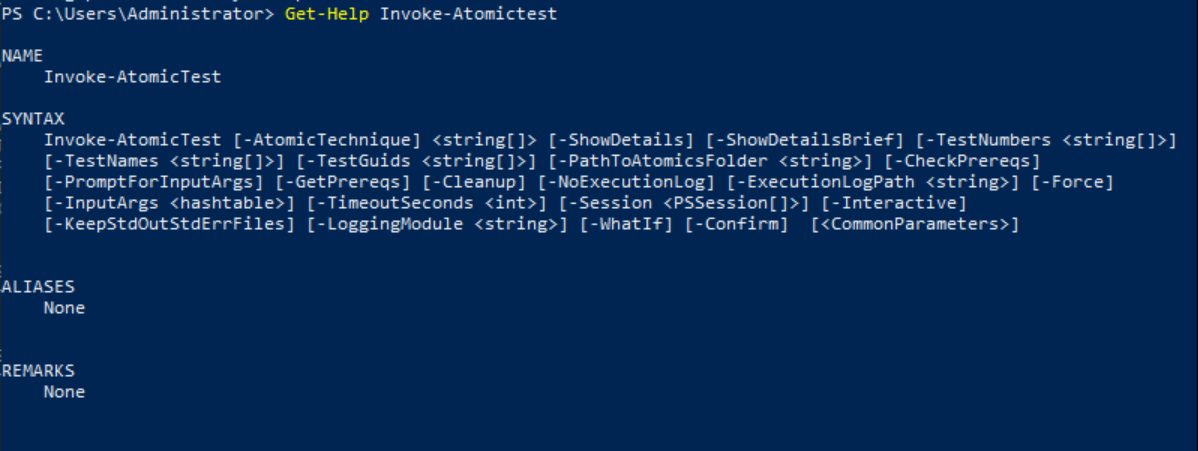
This output lists all parameters that can be used in the Invoke-AtomicTest command and their format.
Step-by-Step Process
Step 1: Defining the Technique and Viewing Test Details:
First, we select the technique we want to test. In this example, we are testing the T1566.001 technique: “Spearphishing with an attachment.”
Invoke-AtomicTest -AtomicTechnique T1566.001 -ShowDetails
This command helps us understand how the test works and what it does.
Step 2: Checking Prerequisites
Before running a test, ensure all dependencies are met using the -CheckPrereq flag. For example:
Invoke-AtomicTest T1566.001 -TestNumbers 1 -CheckPrereq
- Invoke-AtomicTest: The main command used to start the Atomic Red Team’s attack simulations.
- T1566.001: MITRE ATT&CK technique to be tested. In this case, “Spearphishing with an attachment”.
- -TestNumbers 1: Selects test number one within the technique. This test simulates the download of an Excel file containing a malicious macro.
- -CheckPrereq: Checks if the necessary components are present to run the test.
If prerequisites are missing, the output will provide guidance, such as installing necessary software.
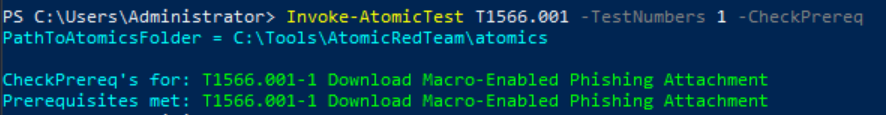
- PathToAtomicsFolder: Where Atomic Red Team test files are located. In this case C:\Tools\AtomicRedTeam\atomics directory.
- CheckPrereq’s for: Indicates that all prerequisites for the test have been checked.
- Prerequisites met: Indicates that all required components are present and the test is executable.
Step 3: Running the Emulation
To execute a specific test, use the -TestNumbers parameter:
Invoke-AtomicTest T1566.001 -TestNumbers 1
- Example Output: Confirms that a macro-enabled phishing attachment was successfully downloaded. The file is saved in the system’s
%TEMP%directory. - Logs are generated, which can later be analyzed for attack indicators.
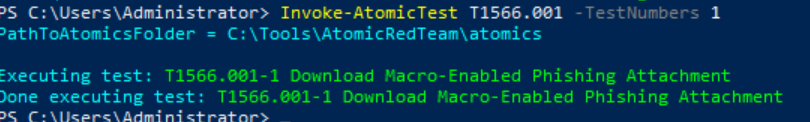
PathToAtomicsFolder: This shows the directory where the Atomic Red Team test files are located. Here the files are located in the C:\Tools\AtomicRedTeam\atomics directory.
- Executing test:
Indicates that the test is being started. In this case:
Test name: “Download Macro-Enabled Phishing Attachment”.
Test: Downloads an Excel file containing a malicious macro. This simulates a scenario in phishing attacks where a user downloads a file via email attachment.
- Done executing test:
Indicates successful completion of the test. The specified attack was executed during the simulation:
File Download: A macro-enabled Excel file was downloaded from a specific URL using PowerShell. This file is usually saved in the %TEMP% directory.
Step 4: Analyzing Indicators of Compromise (IoCs)
After the emulation, analyze logs for signs of the simulated attack. Windows Event Viewer and Sysmon (System Monitor) are used to identify events like:
- Process Creation: Logs that show PowerShell executing the
Invoke-WebRequestcommand. - File Creation: Logs indicating the creation of
PhishingAttachment.xlsm.
Steps for analysis:
- Open Event Viewer and navigate to
Applications and Services > Microsoft > Windows > Sysmon > Operational. - Sort logs by Date and Time and look for events related to the emulation.
- Focus on:
- PowerShell execution of
Invoke-WebRequest. - Creation of the file
PhishingAttachment.xlsm
- PowerShell execution of
Step 5: Cleanup
To revert the system to its original state:
- Remove created files using the
-CleanupflagInvoke-AtomicTest T1566.001 -TestNumbers 1 -Cleanup
- Clear Sysmon logs:
- Open Event Viewer.
- Right-click Operational and select Clear Log.
Step 6: Creating Detection Rules
Using the artifacts from the emulation, detection rules can be created in formats like Sigma, Yara, or Snort. Example Sigma rule for detecting T1566.001:
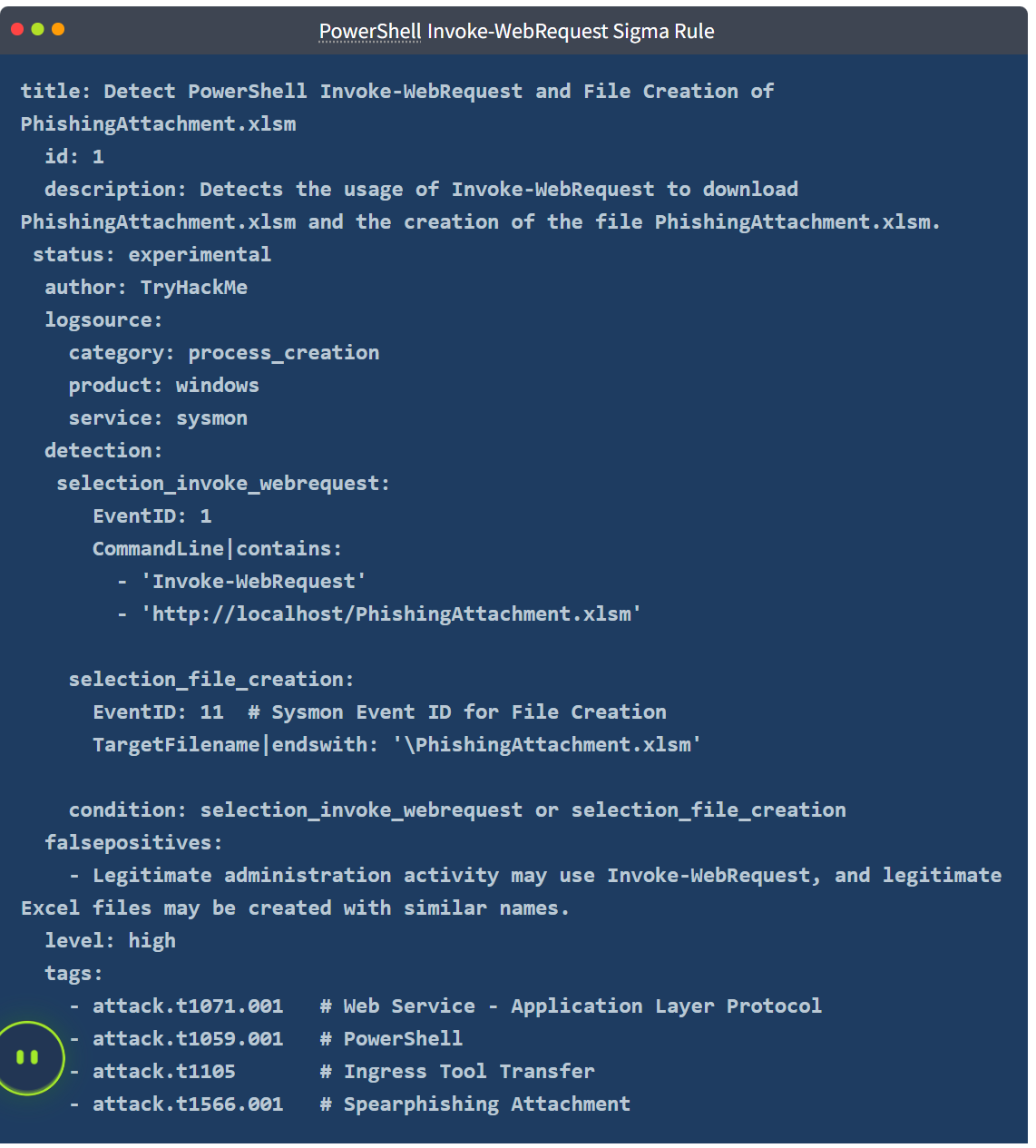
Key Detection Points:
- Invoke-WebRequest Command: Not typical in standard usage; often linked to malicious activity.
- Malicious URL:
http://localhost/PhishingAttachment.xlsm. - Payload Filename:
PhishingAttachment.xlsm.
Questions
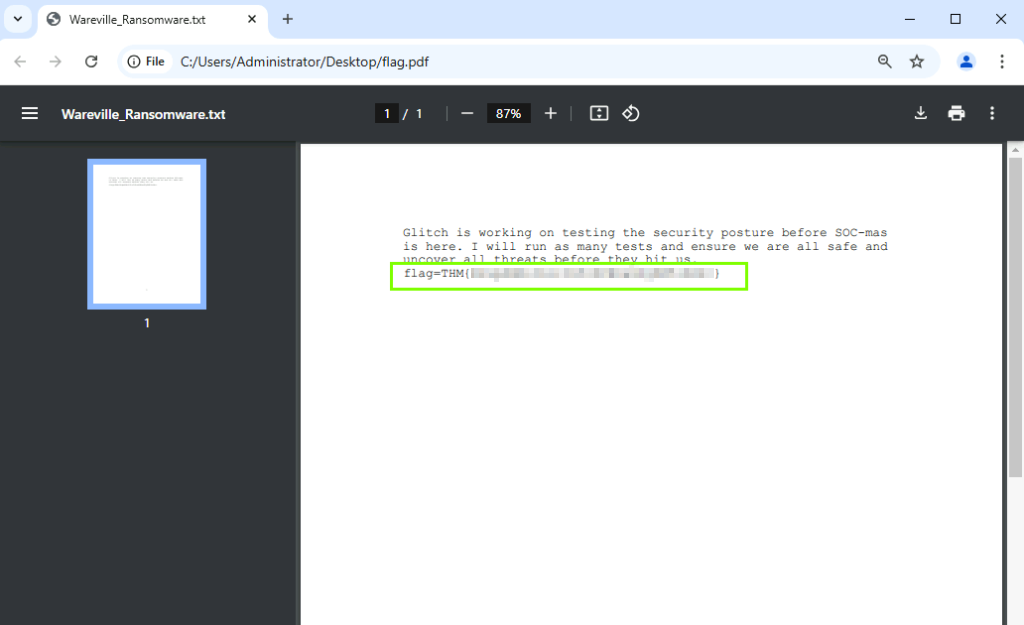
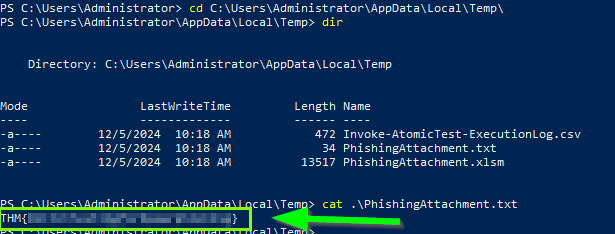
1. What was the flag found in the .txt file that is found in the same directory as the PhishingAttachment.xslm artefact?
2. What ATT&CK technique ID would be our point of interest?
T1059
3. What ATT&CK subtechnique ID focuses on the Windows Command Shell?
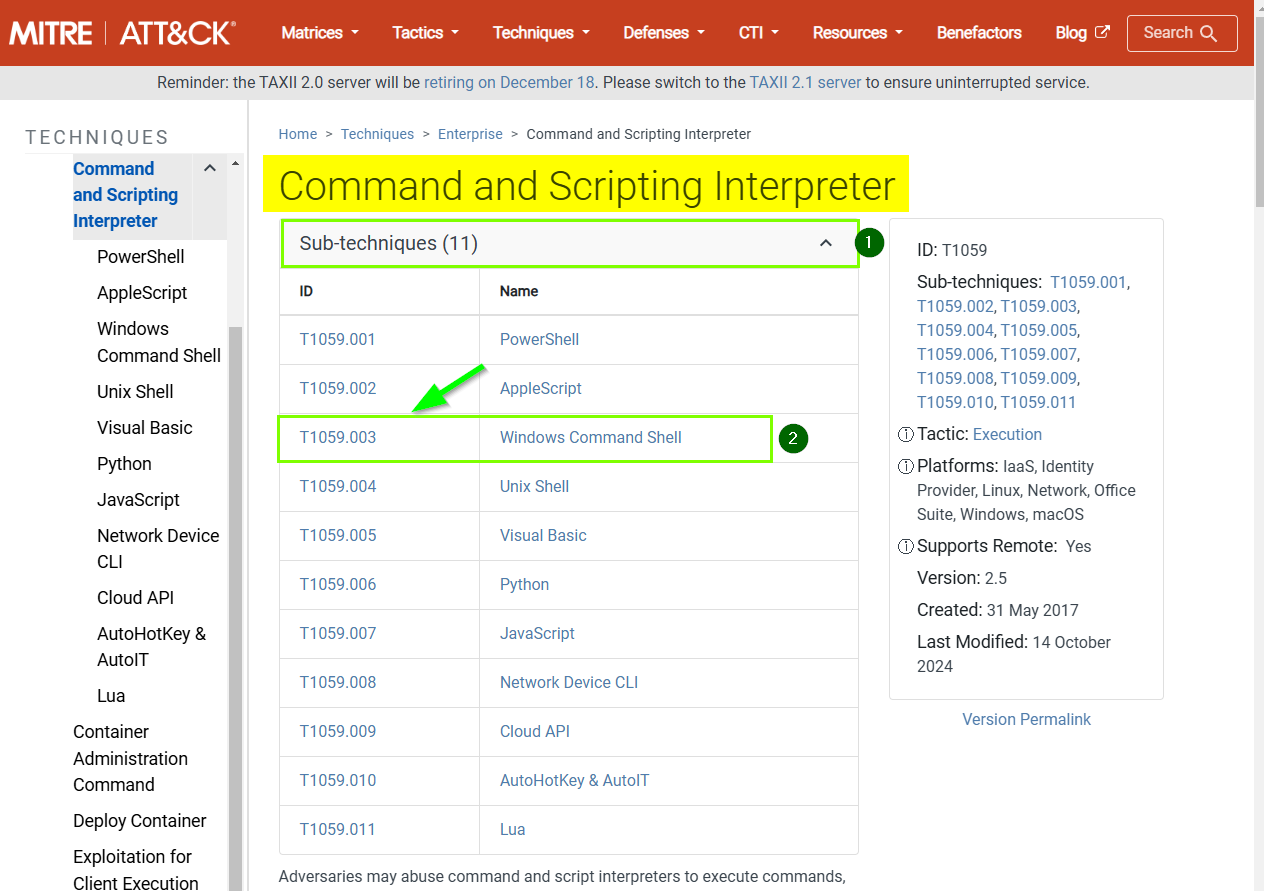
T1059.003
4. What is the name of the Atomic Test to be simulated?
Invoke-AtomicTest T1059.003 -ShowDetails
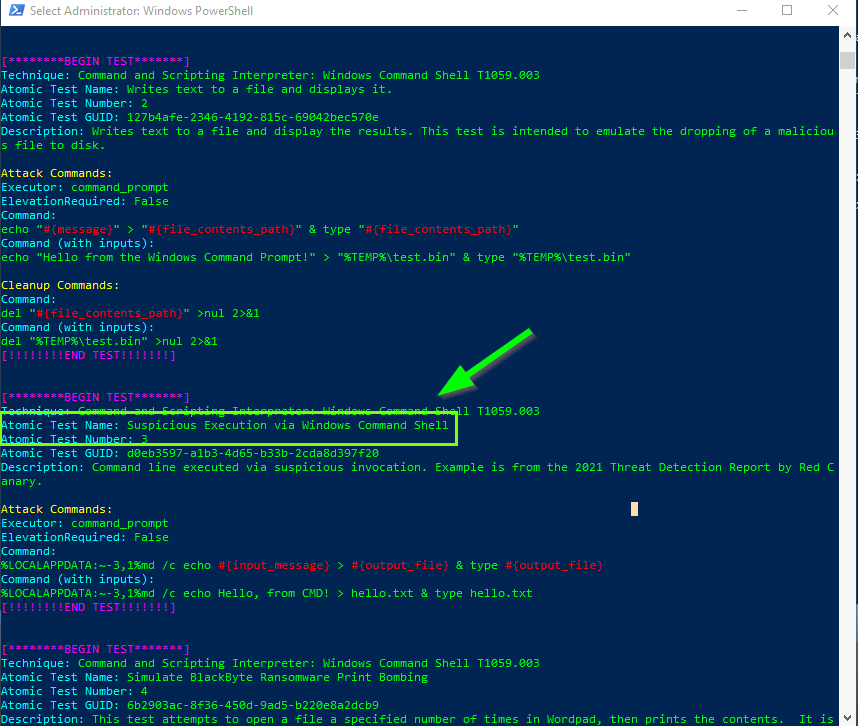
Simulate BlackByte Ransomware Print Bombing
5. What is the name of the file used in the test?
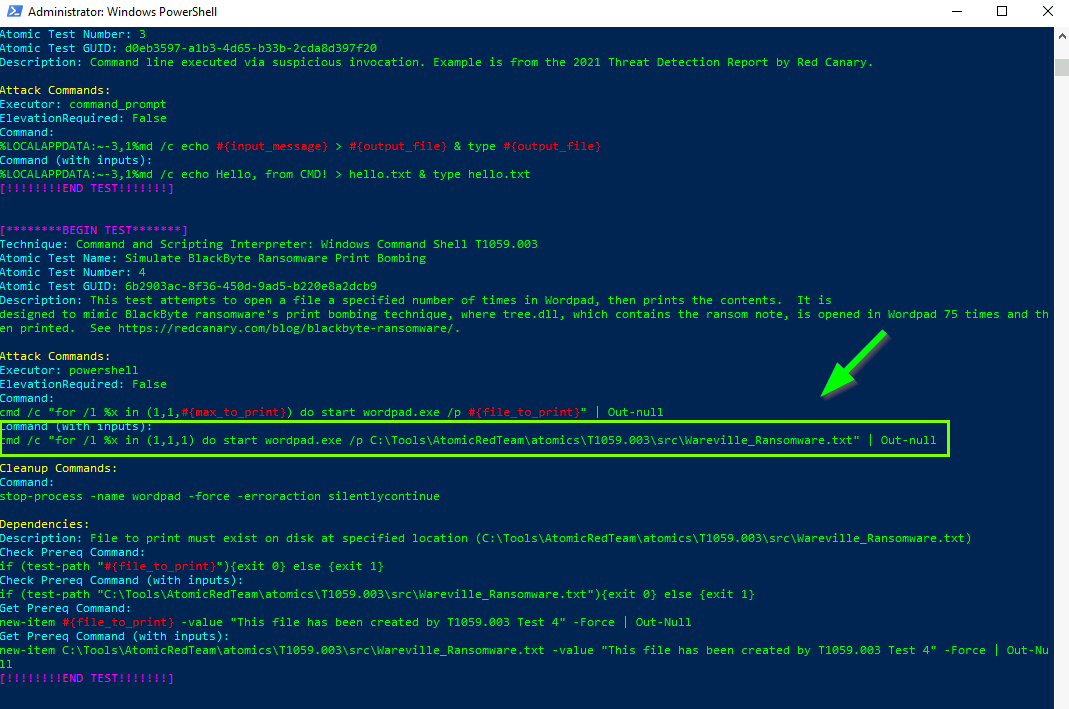
Wareville_Ransomware.txt
6. What is the flag found from this Atomic Test?
Invoke-AtomicTest T1059.003
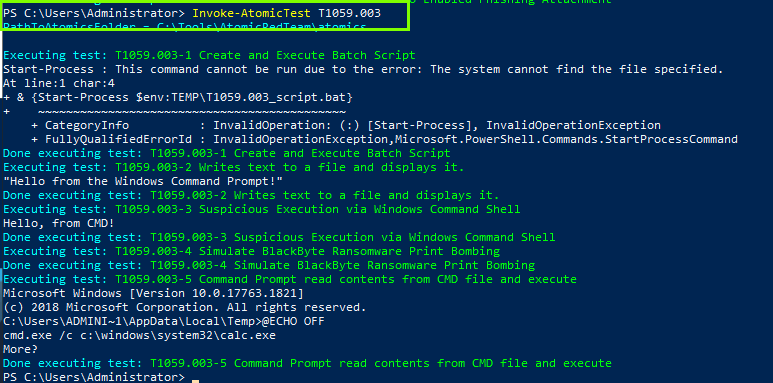
After running the command a calculator opens and we need to save a pdf file. Save and open the file with the name we want and we get the result.