Questions
1. BLUE: Where was the web shell uploaded to?
Answer format: /directory/directory/directory/filename.php
- Date and Time Range: We need to select a specific time range from the date and time selection section at the top (October 3, 2024, 11:30 – 12:00). This is done to display only the logs from this specific time period.
- Filtreleme (Filtering):
NOT response: 404: 404 hata kodu olan yanıtları hariç tutarız.NOT clientip: 10.9.254.186 and NOT clientip: ::1: There are three IP addresses present in the data. Analyzing all IP addresses at once would be time-consuming, so I prefer to examine them one by one. For now, I want to focus on the IP address10.11.83.34, which is why I exclude10.9.254.186and::1.
- Selected Fields: From the “Selected fields” section on the left, we choose the fields necessary for the analysis. The following fields were selected, along with their purposes:
- message: Contains detailed log information, helping us understand the context of each request.
- _id: Acts as a unique identifier for each log entry, useful for pinpointing specific logs.
- request: Shows the requested resource or endpoint, essential for analyzing user activity or potential threats. (This section is important for the question.)
- response: Indicates the HTTP response code, helping identify errors or suspicious behavior (e.g., 200, 404).
- clientip: Displays the IP address of the requester, crucial for tracking sources of activity or detecting anomalies.

/media/images/rooms/shell.php
2. BLUE: What IP address accessed the web shell?

10.11.83.34
3. RED: What is the contents of the flag.txt?
This command adds a line to the system’s /etc/hosts file. The added line associates the name frostypines.thm with the IP address 10.10.220.228. This means that when the domain name frostypines.thm is used, the system will redirect it to the IP address 10.10.220.228.

When we analyze the logs, we can see the admin page URLs. We can directly access the http://frostypines.thm/admin/ page.

We are creating a shell file for ourselves. The code is the one provided on TryHackMe.

We upload our shell file to the http://frostypines.thm/admin/add_room.php page.

In the inspect section, we retrieve the URL where the uploaded file is located.

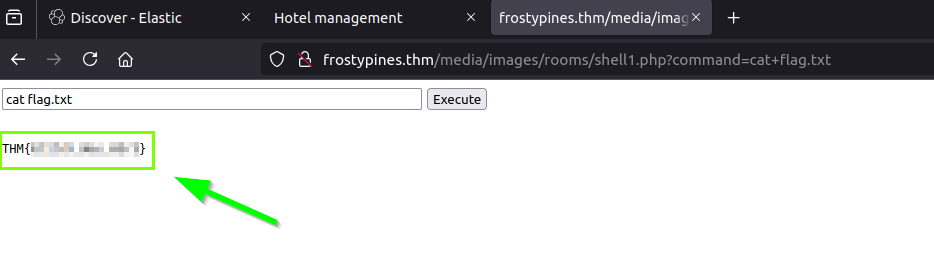
To test, we run the ls command, and in the output, we see the flag.txt file

We use the cat flag.txt command to display the file’s contents.