Questions
1. What is the name of the webshell that was used by Mayor Malware?
The Kubernetes cluster is started using Minikube. The output shows that the cluster has been successfully started and configured by default. We check the status of the pods running in the ‘wareville’ namespace. It may be necessary to check a few times. We notice that a command has been executed in the pod.

Investigate Logs:
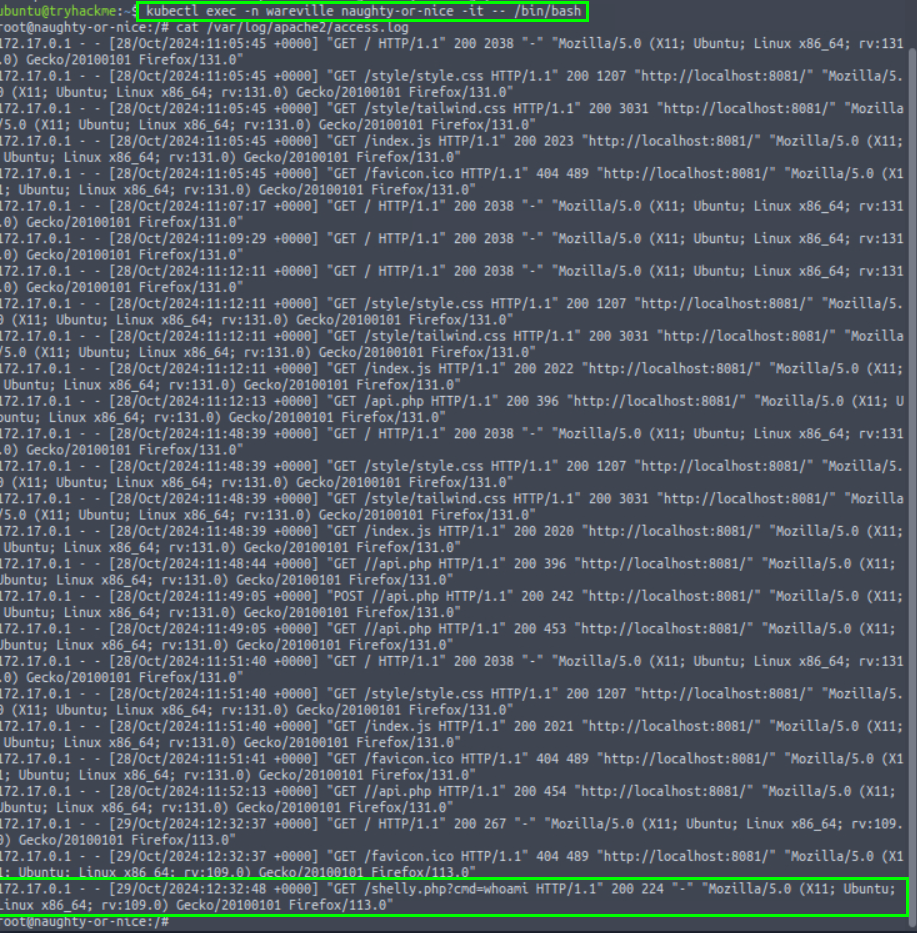
Then, to check the Apache access logs, the command cat /var/log/apache2/access.log is entered. One particular entry stands out in the logs: GET /shelly.php?cmd=whoami.
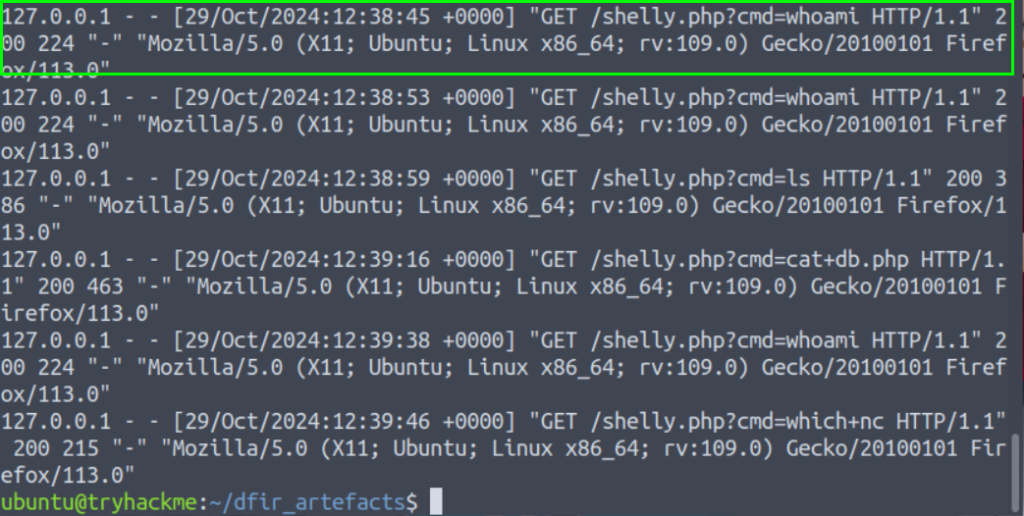
shelly.php
2. What file did Mayor Malware read from the pod?

db.php
3. What tool did Mayor Malware search for that could be used to create a remote connection from the pod?
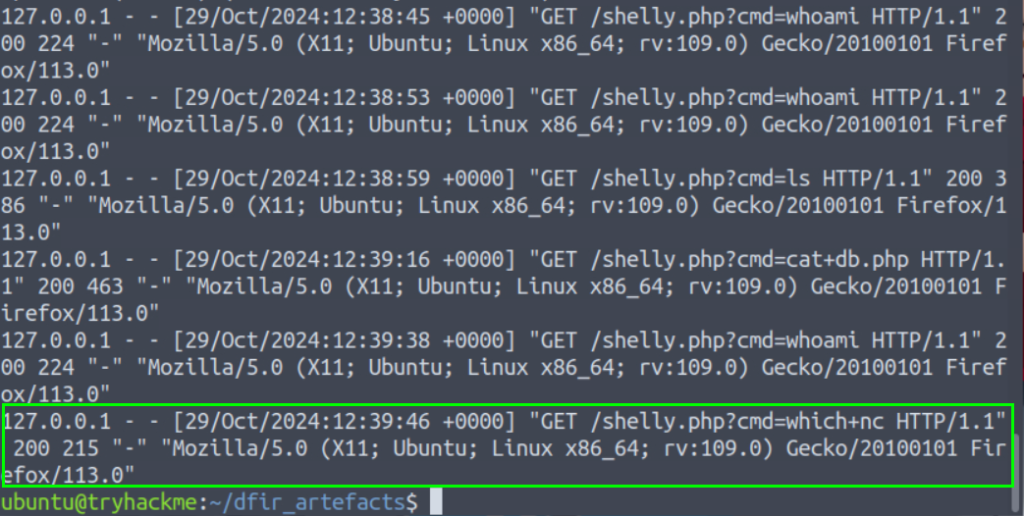
nc
4. What IP connected to the docker registry that was unexpected?
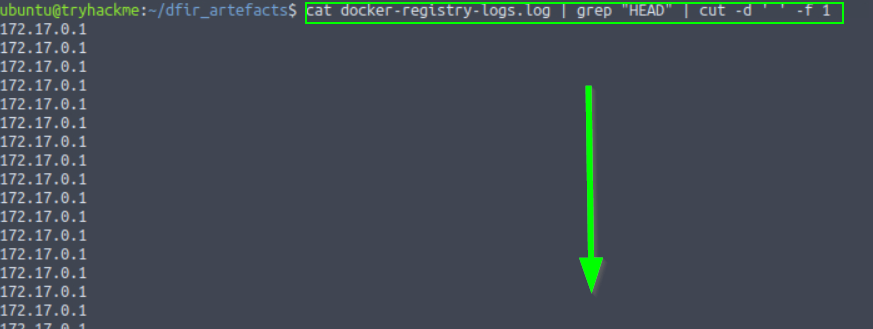

10.10.130.253
5. At what time is the first connection made from this IP to the docker registry?
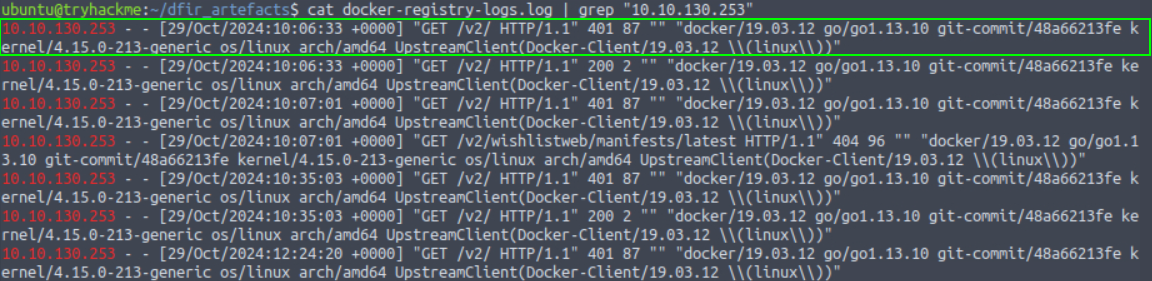
29/Oct/2024:10:06:33 +0000
6. At what time is the updated malicious image pushed to the registry?
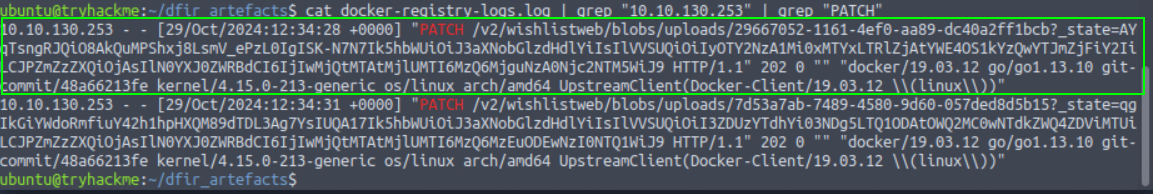
29/Oct/2024:12:34:28 +0000
7. What is the value stored in the “pull-creds” secret?