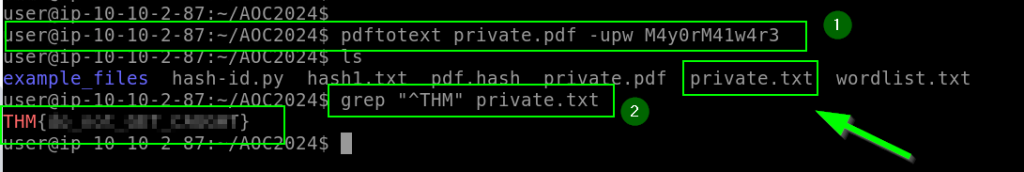
Questions
1. Crack the hash value stored in hash1.txt. What was the password?
To crack a hash, the first step is to identify its type. For this, we use the hash-id tool. This tool analyzes the provided hash and suggests possible hash types, which helps us choose the correct cracking method.
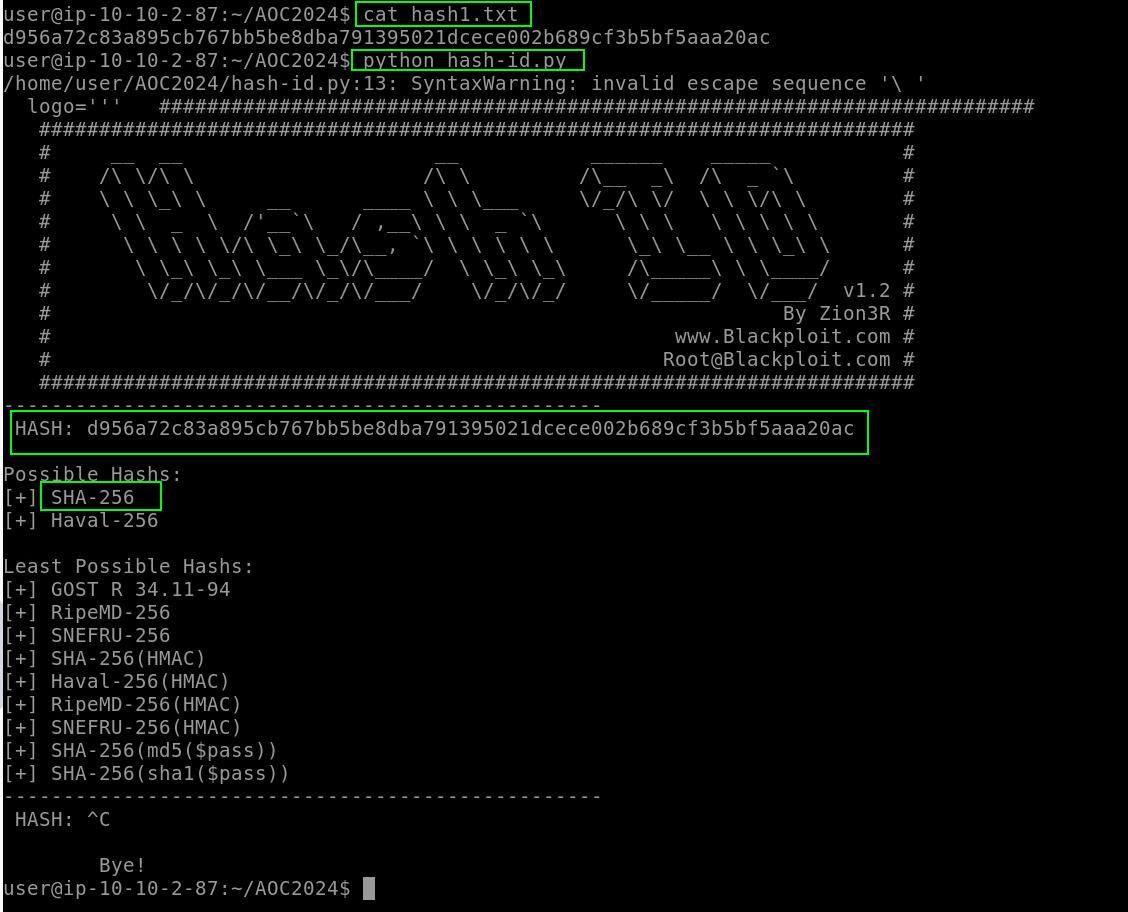
Based on the output, the hash type was most likely identified as SHA-256. To crack the hash, we use John the Ripper with the command:
john –format=raw-sha256 –wordlist=/usr/share/wordlists/rockyou.txt hash1.txt.
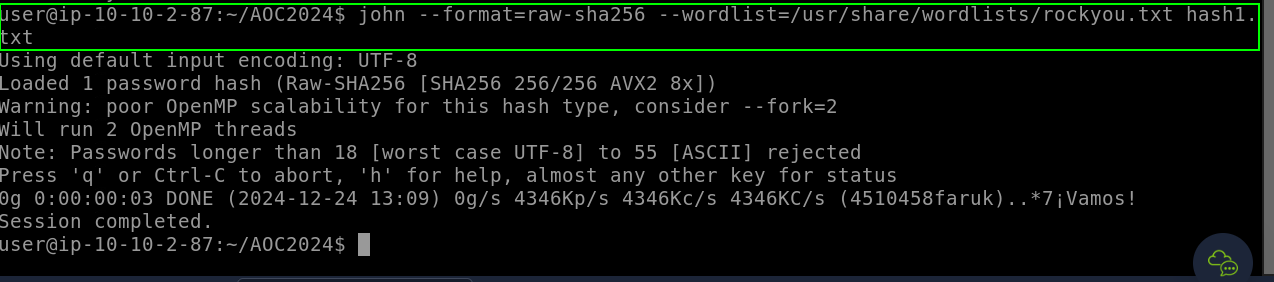
In this attempt, the wordlist failed to crack the hash, indicating that the hash represents a more complex password. The –rules=wordlist option applies modifications to each word in the wordlist (e.g., letter substitution, adding numbers). Using this method, the hash was cracked, and the password was discovered.

fluffycat12
2. What is the flag at the top of the private.pdf file?
To crack a PDF with John, we first convert the PDF into a hash. To guess the PDF password, we need to create a custom wordlist (which is already available in the connected directory).
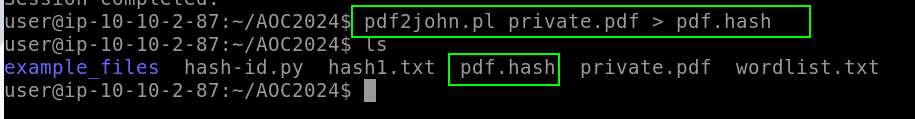
To crack the PDF password with John:
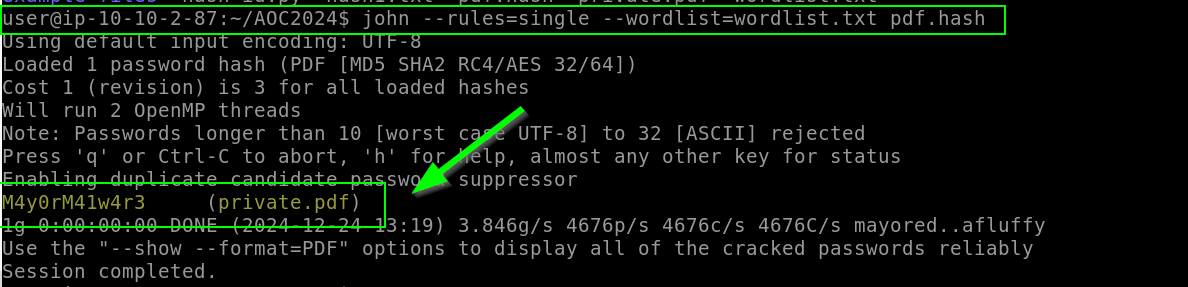
To extract the content of a password-protected PDF file as plain text: