Questions
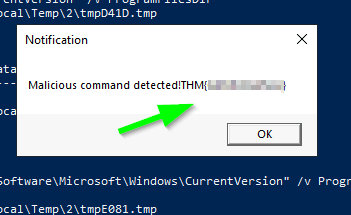
1. What is the flag displayed in the popup window after the EDR detects the malware?
We open powershell and go to the directory to run the YARA rule in the example.
cd C:\Tools
.\JingleBells.ps1
We go to the location of the MerryChristmas.exe file, execute it (by clicking on it twice) and wait for the YARA rule to run.

The YARA rule gives us the flag in a box.
2. What is the flag found in the malstrings.txt document after running floss.exe, and opening the file in a text editor?
Floss is a powerful tool for uncovering obfuscated or hardcoded strings used by malware. We go to the directory to execute the command.
cd C:\Tools\FLOSS\
floss.exe C:\Tools\Malware\MerryChristmas.exe |Out-file C:\tools\malstrings.txt
- floss.exe C:\Tools\Malware\MerryChristmas.exe
- Floss scans the binary file MerryChristmas.exe, which is likely a piece of malware.
- It analyzes and extracts any hardcoded or hidden strings within the binary file.
- | (Pipe Operator):
- The pipe (|) symbol redirects the output of one command as the input for another command.
- Here, it takes the strings extracted by Floss and passes them to the next command.
- Out-File C:\tools\malstrings.txt
- This saves the results from Floss into a file named malstrings.txt.
- File location: C:\tools\malstrings.txt.
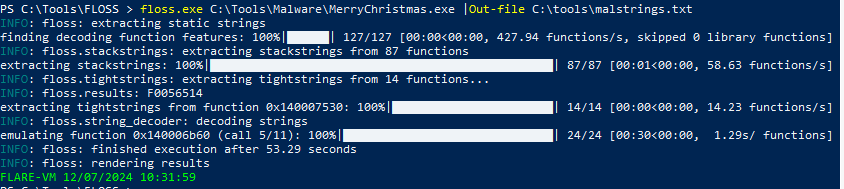
Open the malstrings.txt file
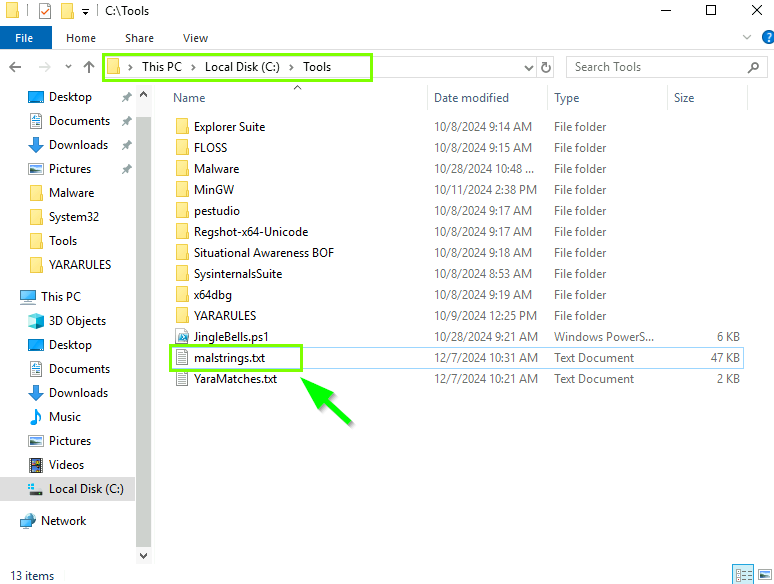

Sysmon
A tool from Microsoft’s Sysinternals suite that continuously monitors and logs system activity.It captures detailed information about:
- Process creation: When a new process is started.
- Network connections: Any connections made by the system.
- File changes: Any modifications or creations of files.
Sysmon is useful for tracing malware behavior as it records these activities persistently across reboots.
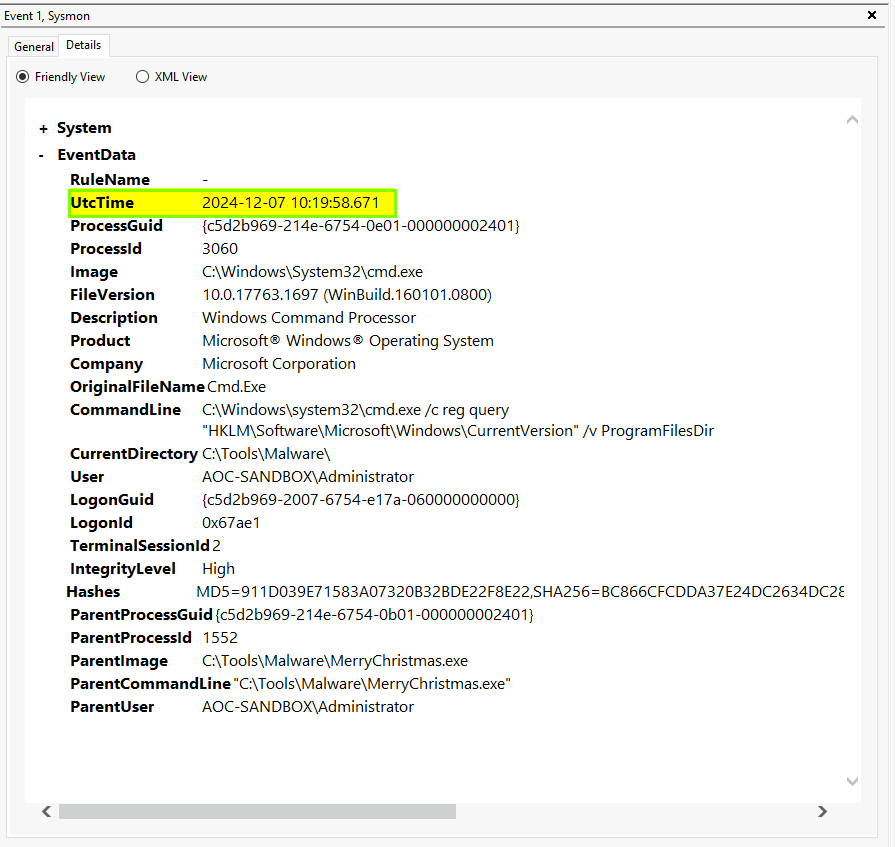
A YARA rule is applied to identify event ID 1 in Sysmon logs.
- Event ID 1: Represents “Process Created.”
The rule detects a suspicious registry query:
get-content C:\Tools\YaraMatches.txt

- Event Record ID: 127916: This uniquely identifies the suspicious event.
- Command Line: Shows the exact command that was executed by the malware.
- YARA Result: Indicates the detected artifact.
To focus on the specific event identified by YARA: Open Windows Event Viewer.
Navigate to:
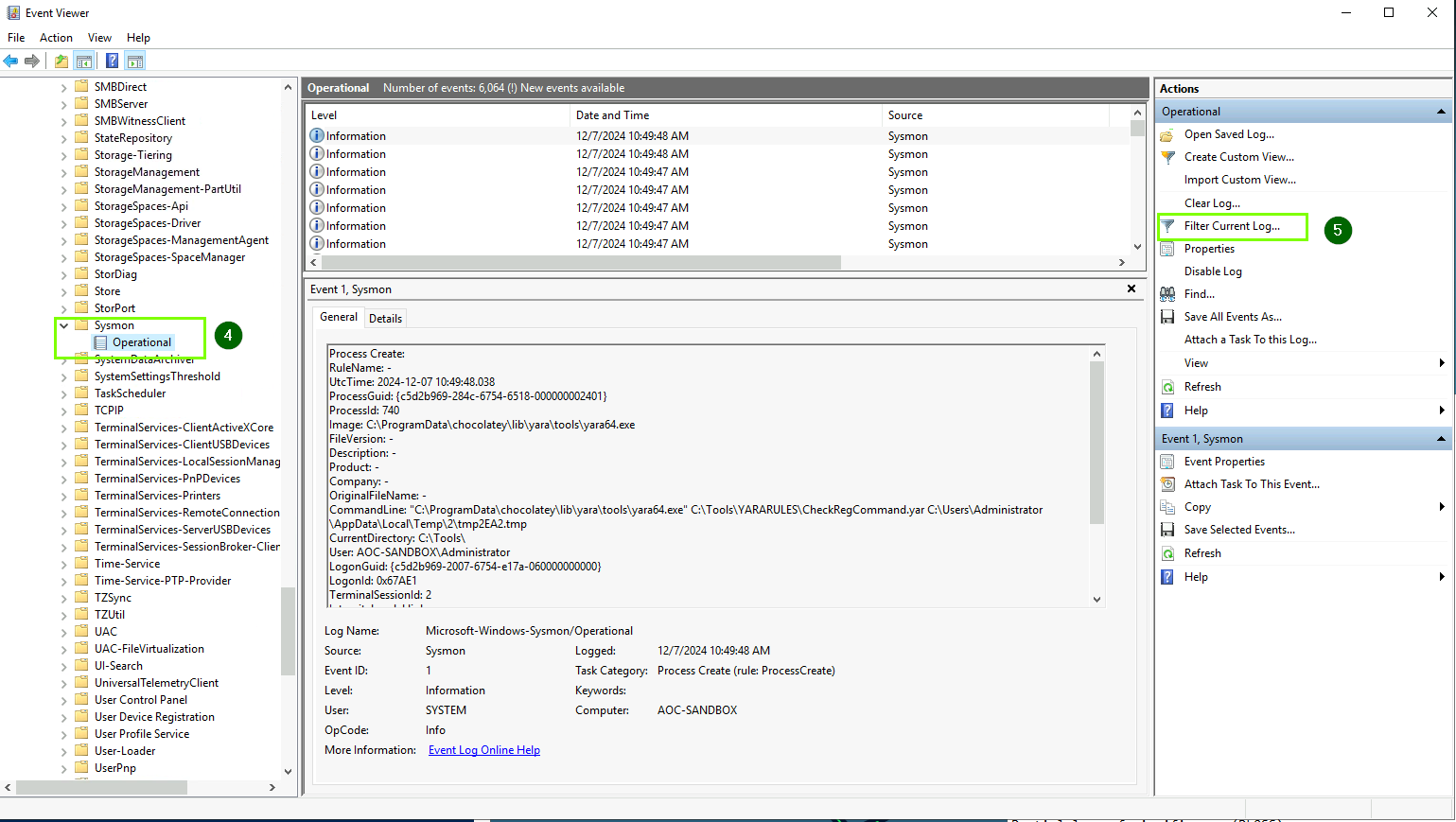
- Applications and Services Logs → Microsoft → Windows → Sysmon → Operational.
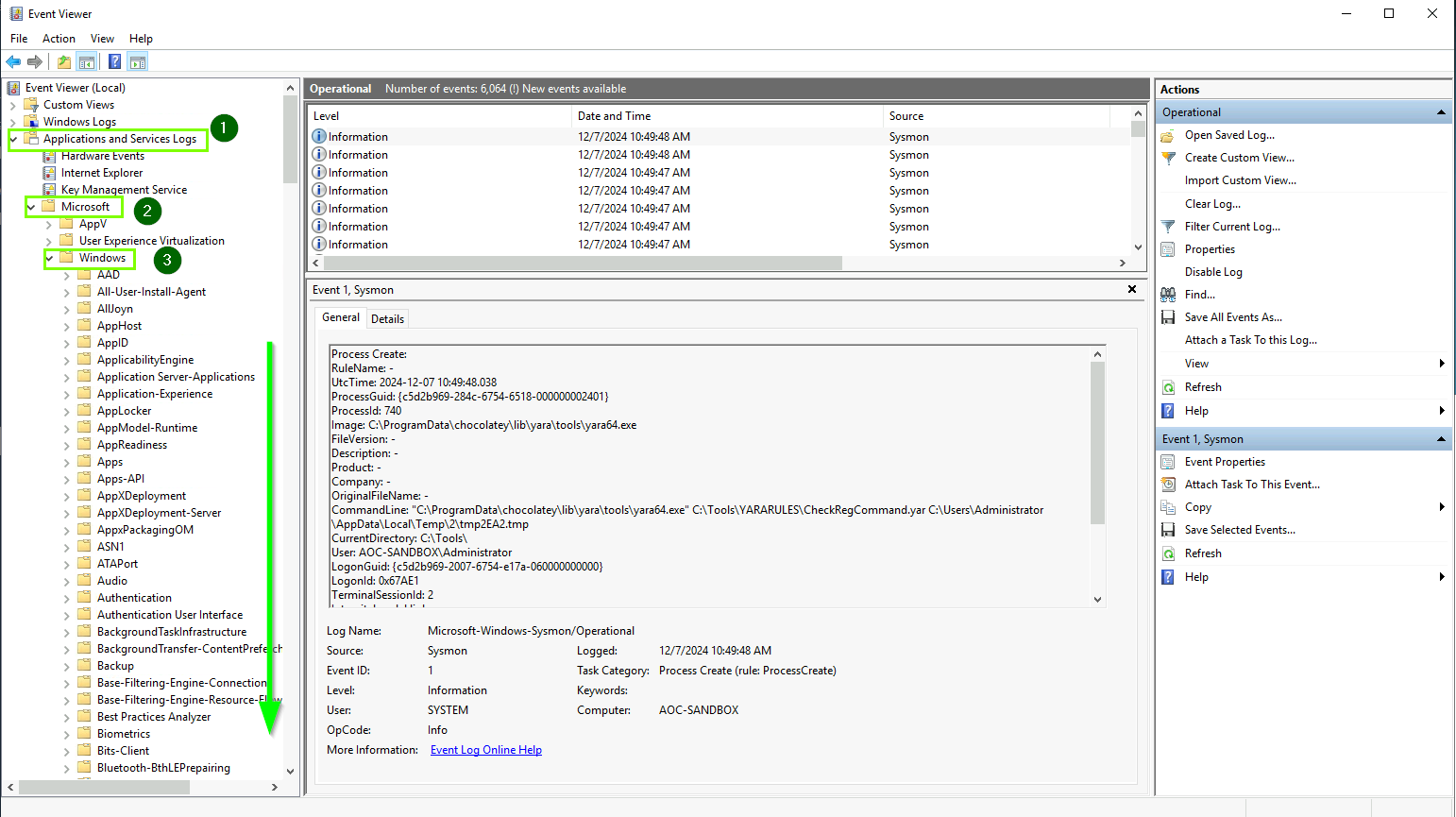
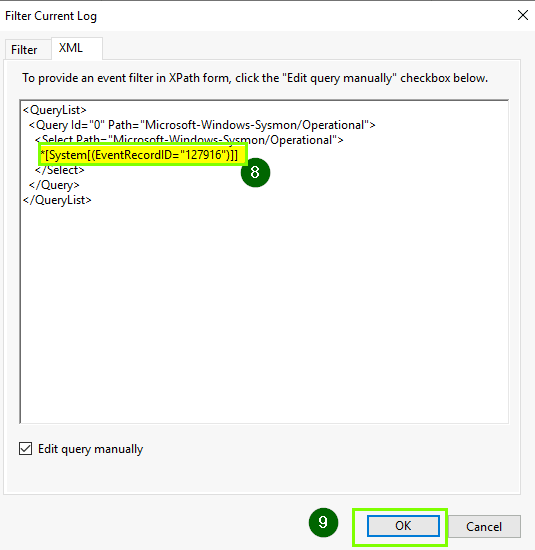
On the right side, click Filter Current Log.
In the filter window, go to the XML tab, and check Edit query manually.
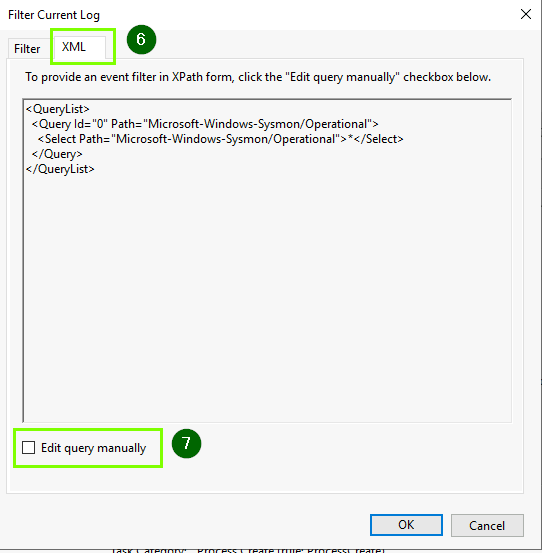
Replace 127916 with the Event Record ID from the YARA match. Click OK to apply the filter.
ParentImage:
- Shows the parent process that spawned the malicious process.
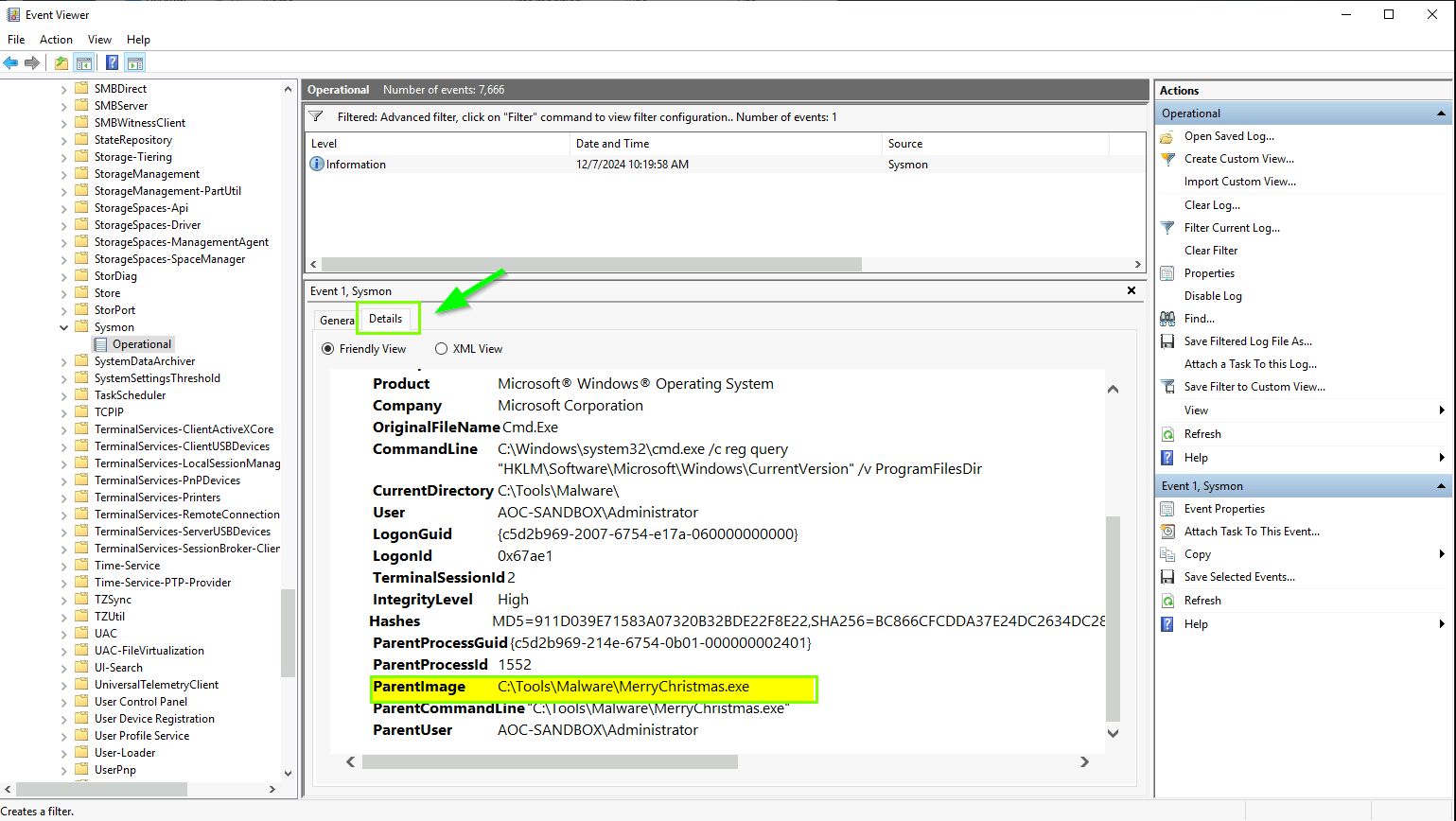
ParentProcessId and ProcessId:
- Unique identifiers for the parent and child processes.
- These IDs can be used to trace related activities in other logs.

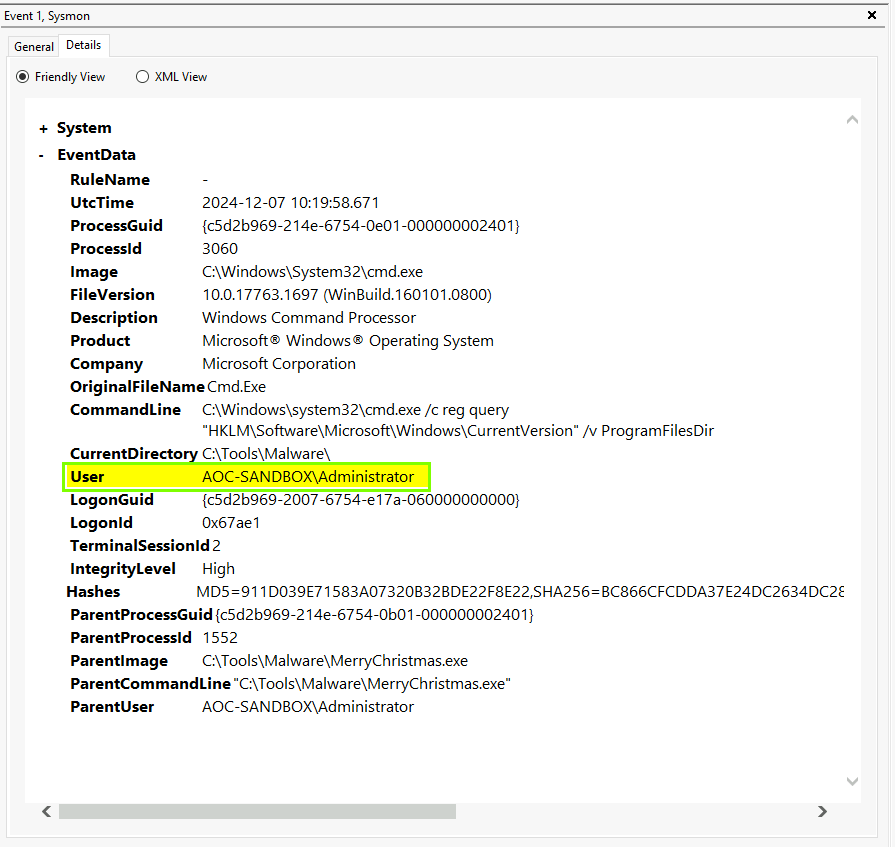
User:
- Identifies which user or privilege level was used to execute the process.
- Malware may use hidden accounts or elevated privileges.
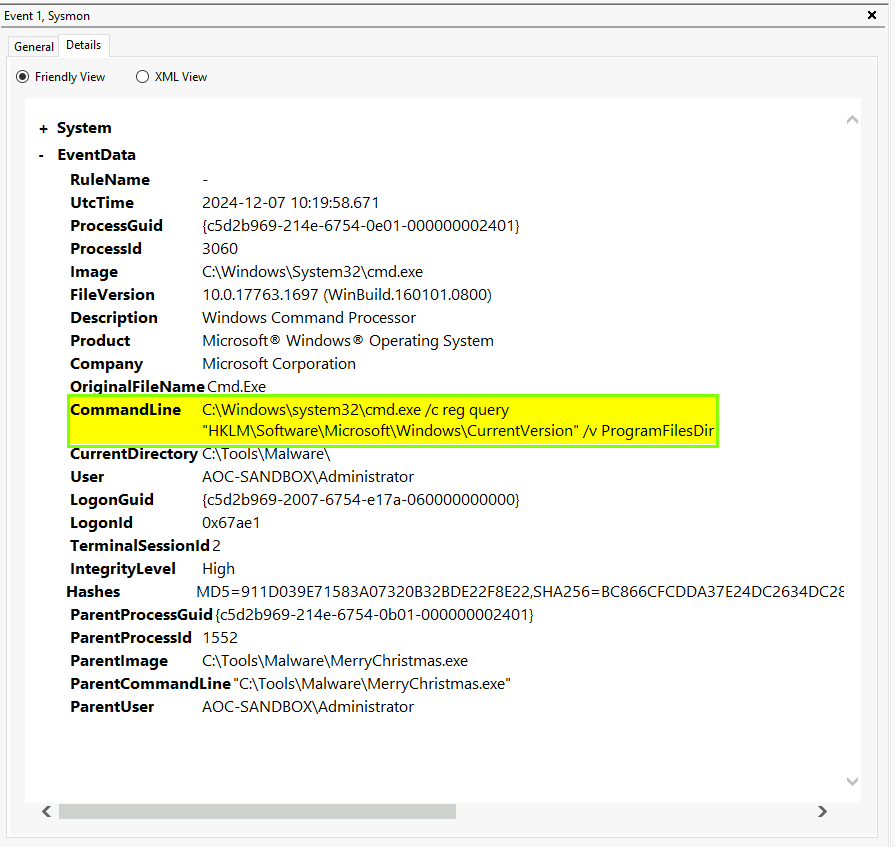
CommandLine:
- The exact command executed by the malware.
- Helps in identifying its purpose or functionality.
UtcTime:
- The timestamp of when the event occurred.
- Useful for creating a timeline of the malware’s activity and focusing your investigation.