The Room: “Learn techniques for securing and protecting network devices from potential threats and attacks.”
https://tryhackme.com/room/networkdevicehardening
Task 2: Common Threat and Attack Vectors
2.1. The device that is used to control and manage network resource is called?
Network device
2.2. A threat vector that includes disruption of critical devices and services to make them unavailable to genuine users is called?
Denial of Service
Task 3: Common Hardening Techniques
3.1. Suppose you are configuring a router; which of the following could be considered an insecure protocol:
A: HTTPS
B: FTP
C: SSH
D: IPsec
B
3.2. The protocol for sending log messages to a centralised server for storage and analysis is called?
Syslog
Task 4: Hardening Virtual Private Networks
4.1. Update the config file to use cipher AES-128-CBC. What is the flag value linked with the cipher directive?
Just open the file using nano command and the answers are here.
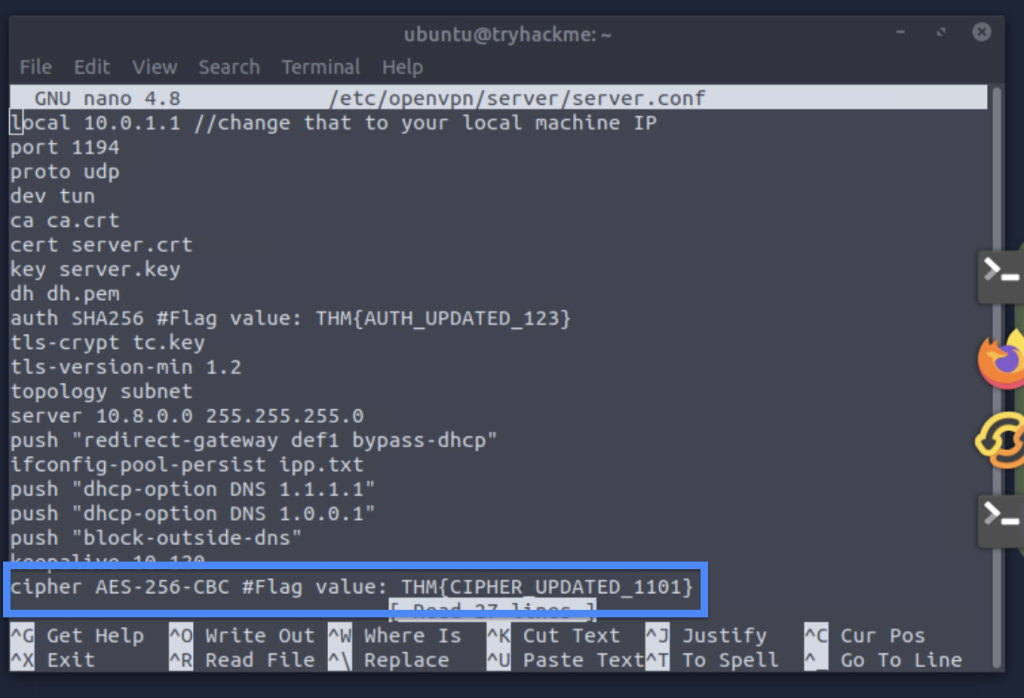
THM{CIPHER_UPDATED_1101}
4.2. Update the config file to use auth SHA512. What is the flag value linked with the auth directive?
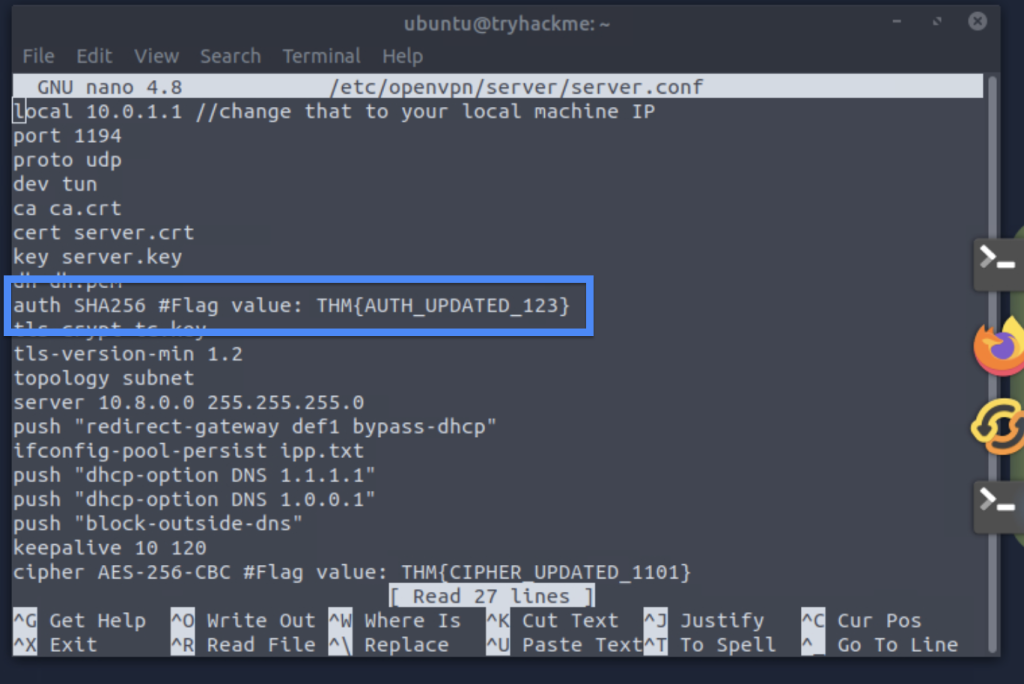
THM{AUTH_UPDATED_123}
4.3. As per the config file, what is the port number for the OpenVPN server?
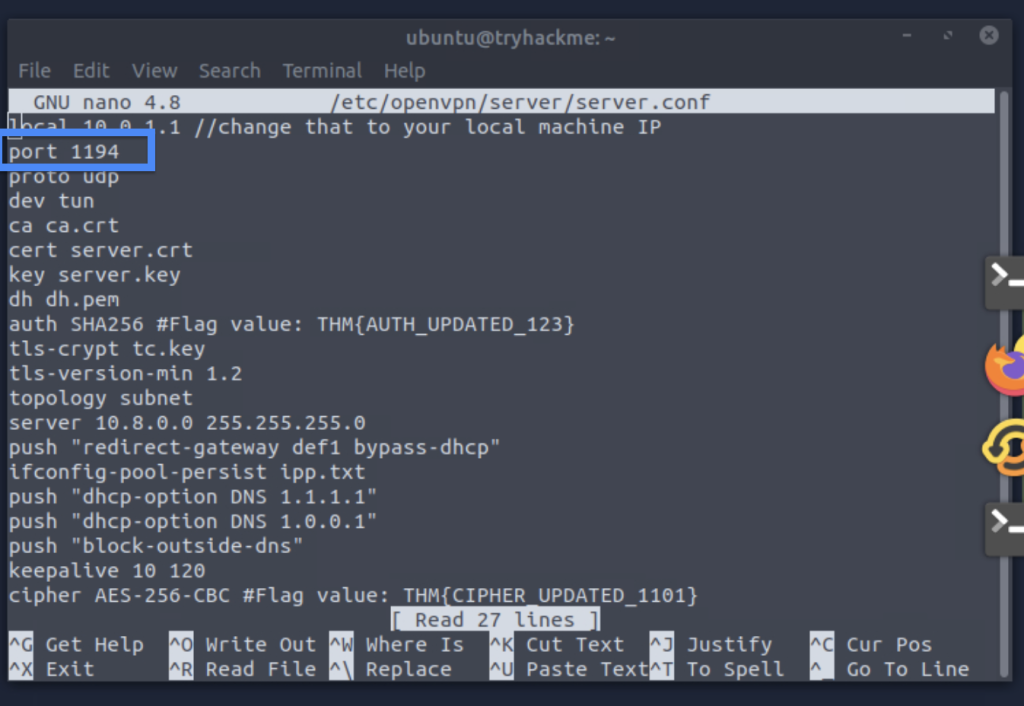
1194
Task 5: Hardening Routers, Switches & Firewalls
5.2. What is the default SSH port configured for OpenWrt in the attached VM?
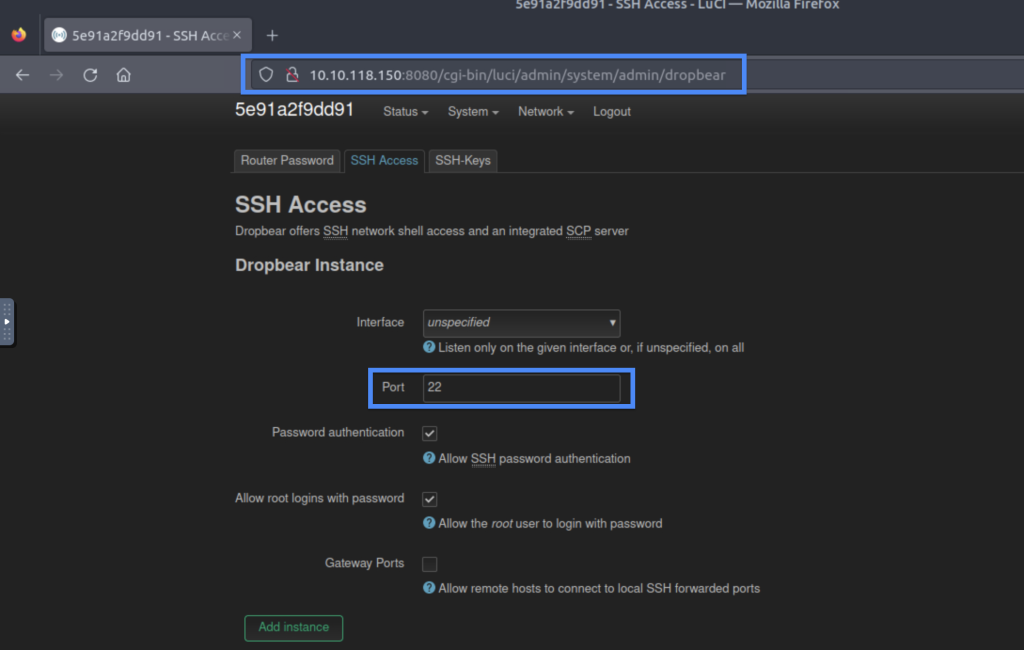
22
5.3. Go through the General Settings option under the System tab in the attached VM. The administrator has left a special message in the Notes section. What is the flag value?
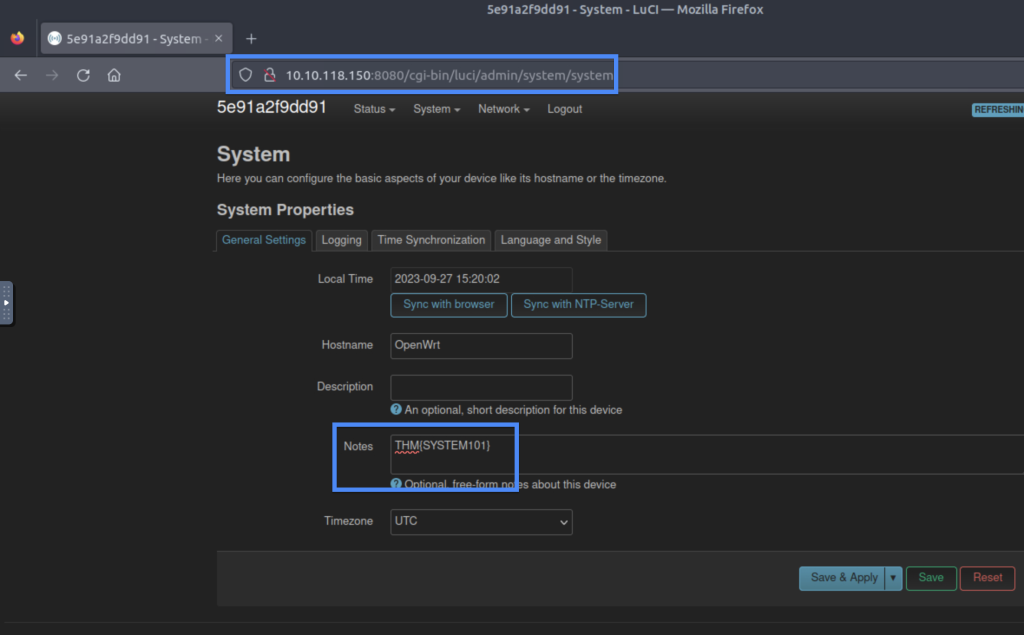
THM{SYSTEM101}
5.4. What is the default system log buffer size value for the OpenWrt router in the attached VM?
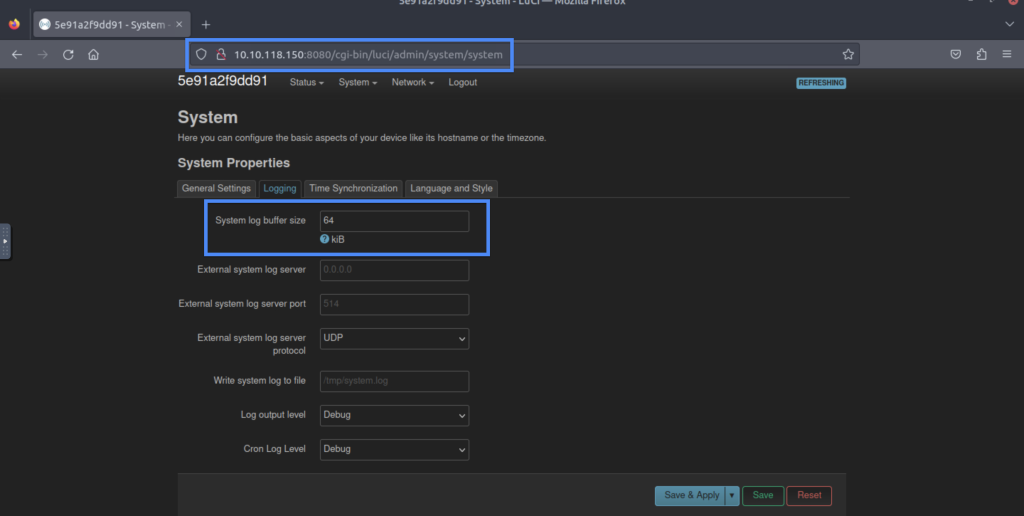
64
5.5. What is the start priority for the script uhttpd?
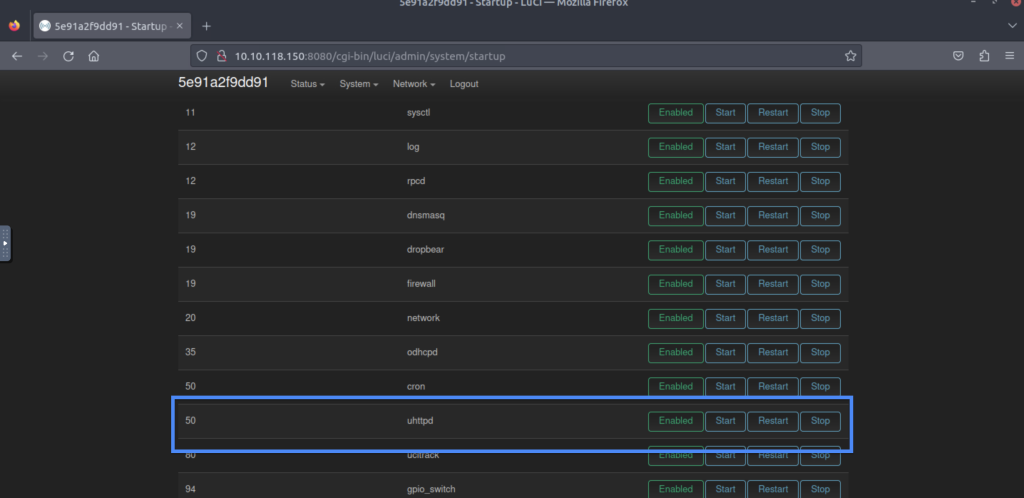
50
Task 6: Hardening Routers, Switches & Firewalls – More Techniques
6.1. What is the name of the rule that accepts ICMP traffic from source zone WAN and destination zone as this device?
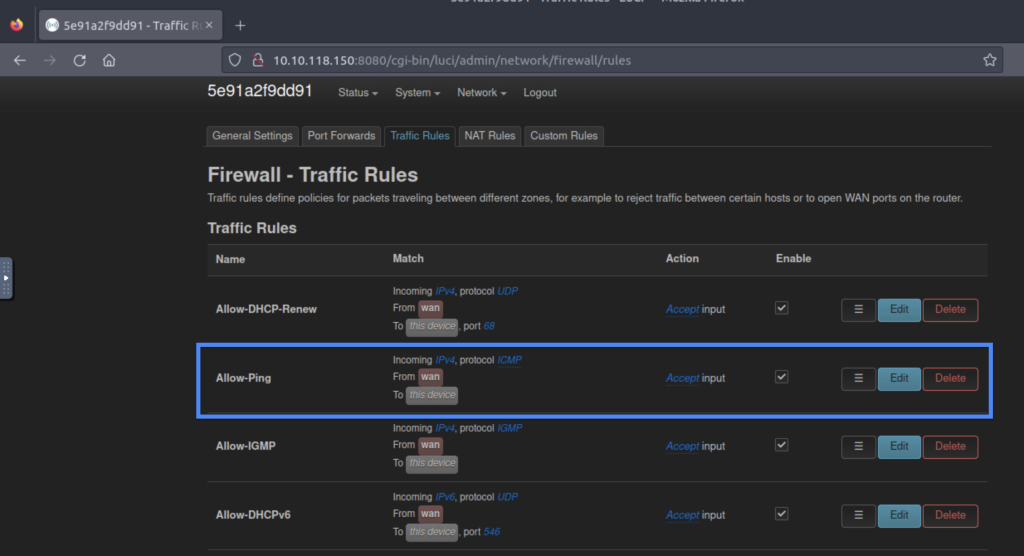
Allow-Ping
6.2. What is the name of the rule that forwards data coming from WAN port 9001 to LAN port 9002?
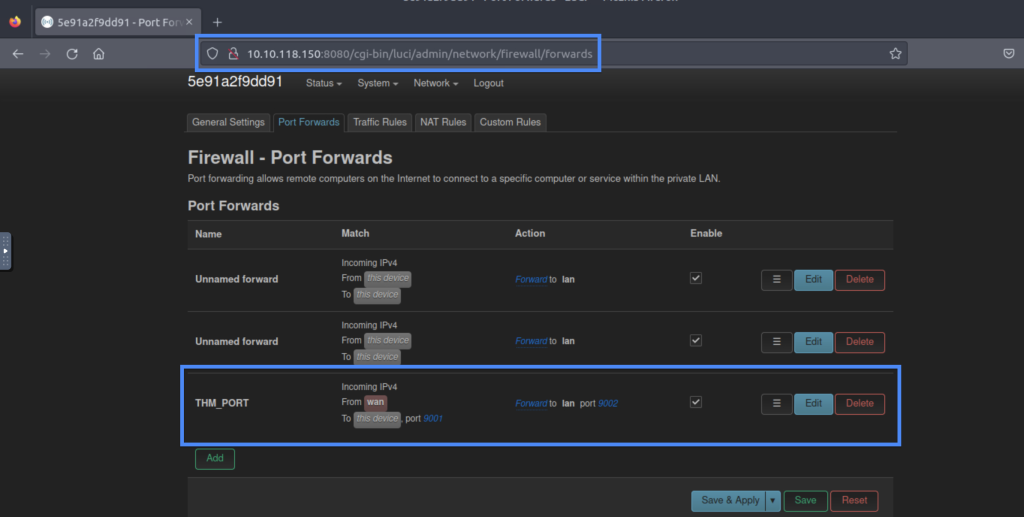
THM_PORT
6.3. What is the version number for the available apk package?

2.12.2-1
Task 7: Important Tools for Network Monitoring
7.1. Are network monitoring tools capable of detecting bandwidth bottlenecks? (yea/nay)
yea

Hello, I am Aleyna Doğan. I work as a Sr. Cyber Threat Intelligence Analyst. In my blog, we write blog posts that my friends and I want to share. Have a good read.

