The Room: “Building cyber resiliency and emulation capabilities through threat modelling.”
https://tryhackme.com/room/threatmodelling
Task 2: Threat Modelling Overview
2.1. What is a weakness or flaw in a system, application, or process that can be exploited by a threat?
vulnerability
2.2. Based on the provided high-level methodology, what is the process of developing diagrams to visualise the organisation’s architecture and dependencies?
Asset Identification
2.3. What diagram describes and analyses potential threats against a system or application?
attack tree
Task 3: Modelling with MITRE ATT&CK
3.1. What is the technique ID of “Exploit Public-Facing Application”?
T1190
3.2. Under what tactic does this technique belong?
Initial Access
Task 4: Mapping with ATT&CK Navigator
4.1. How many MITRE ATT&CK techniques are attributed to APT33?
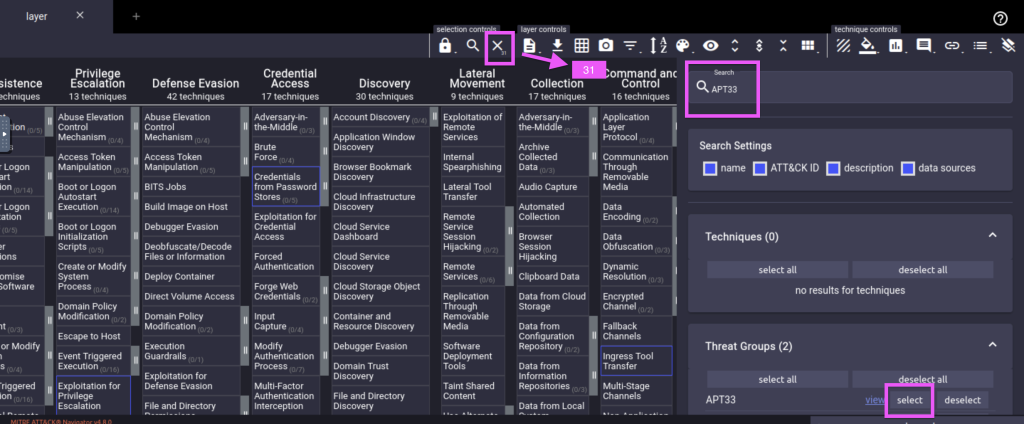
31
4.2. Upon applying the IaaS platform filter, how many techniques are under the Discovery tactic?
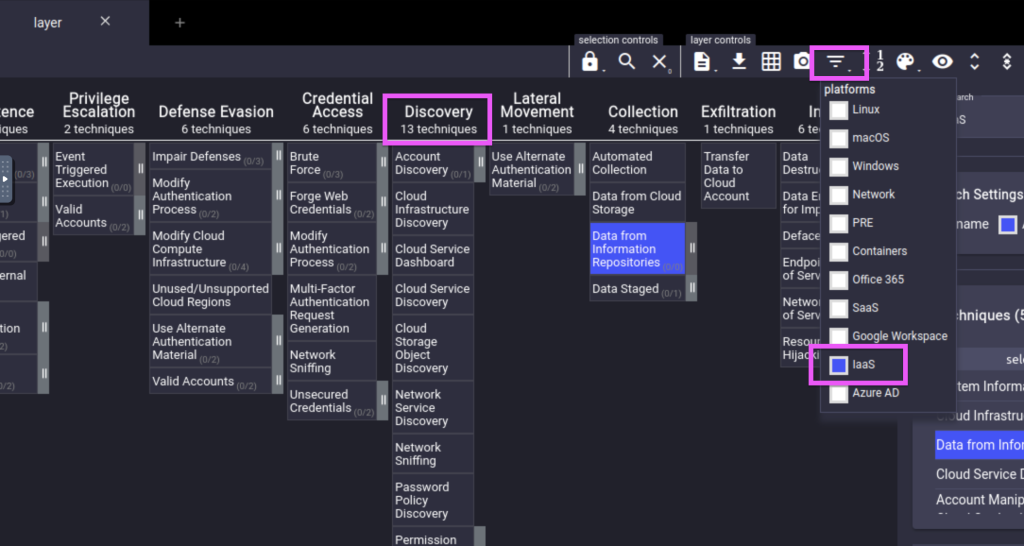
13
Task 5: DREAD Framework
5.1. What DREAD component assesses the potential harm from successfully exploiting a vulnerability?
Damage
5.2. What DREAD component evaluates how others can easily find and identify the vulnerability?
Discoverability
5.3. Which DREAD component considers the number of impacted users when a vulnerability is exploited?
Affected Users
Task 6: STRIDE Framework
6.1. What foundational information security concept does the STRIDE framework build upon?
CIA Triad
6.2. What policy does Information Disclosure violate?
Confidentiality
6.3. Which STRIDE component involves unauthorised modification or manipulation of data?
Tampering
6.4. Which STRIDE component refers to the disruption of the system’s availability?
Denial of Service
6.5. Provide the flag for the simulated threat modelling exercise.
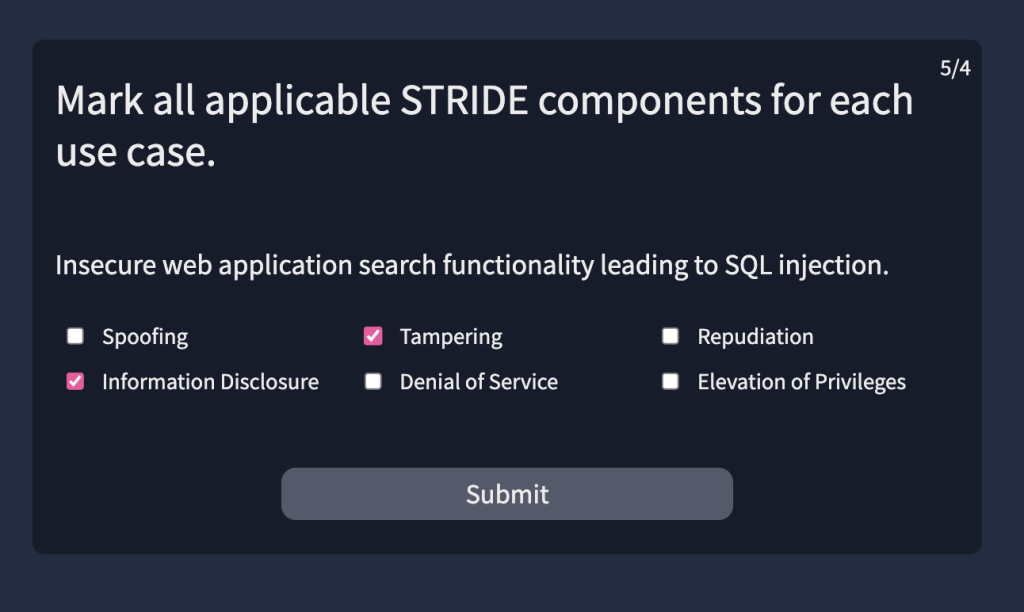
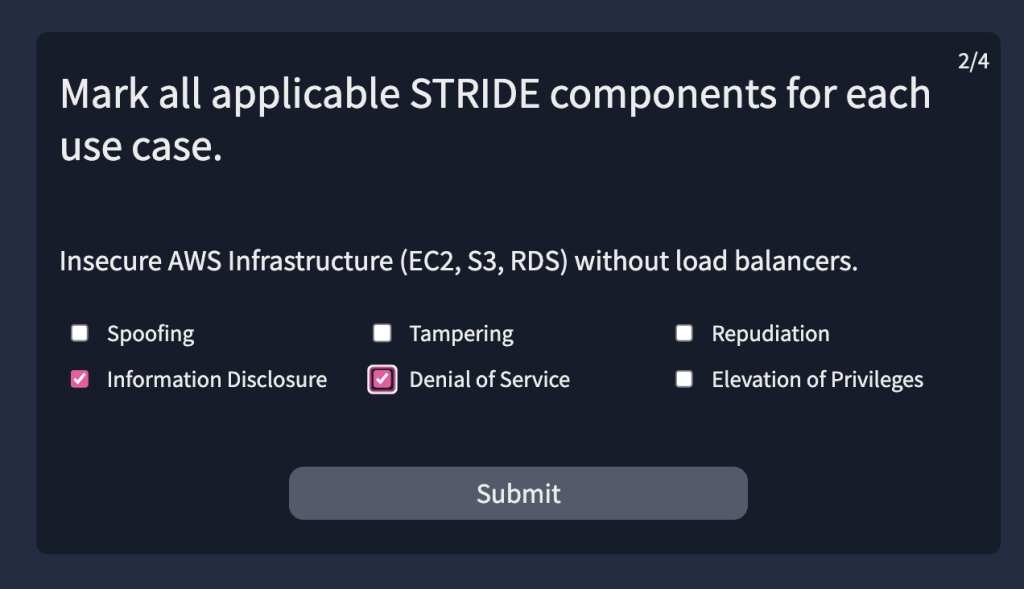
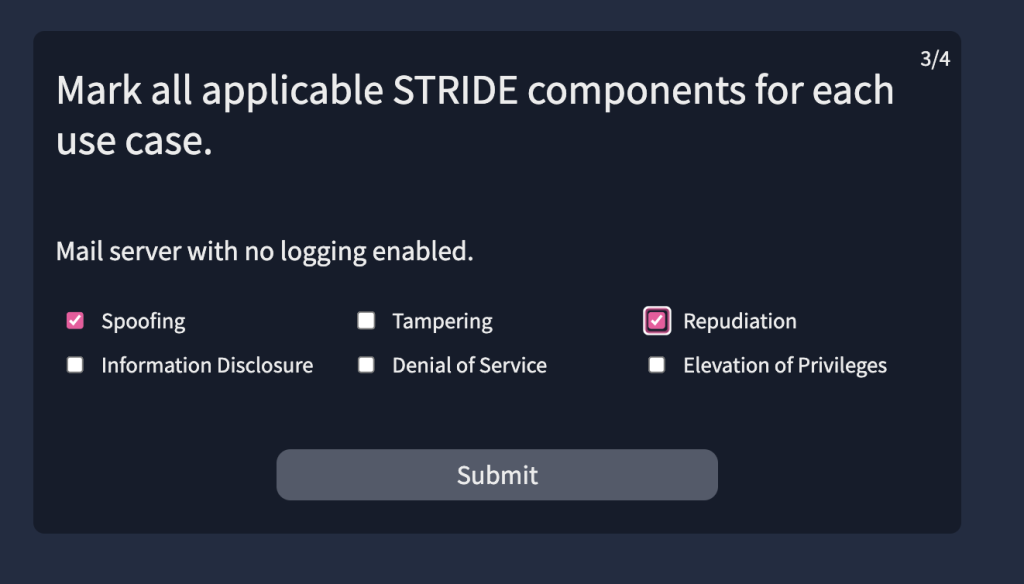
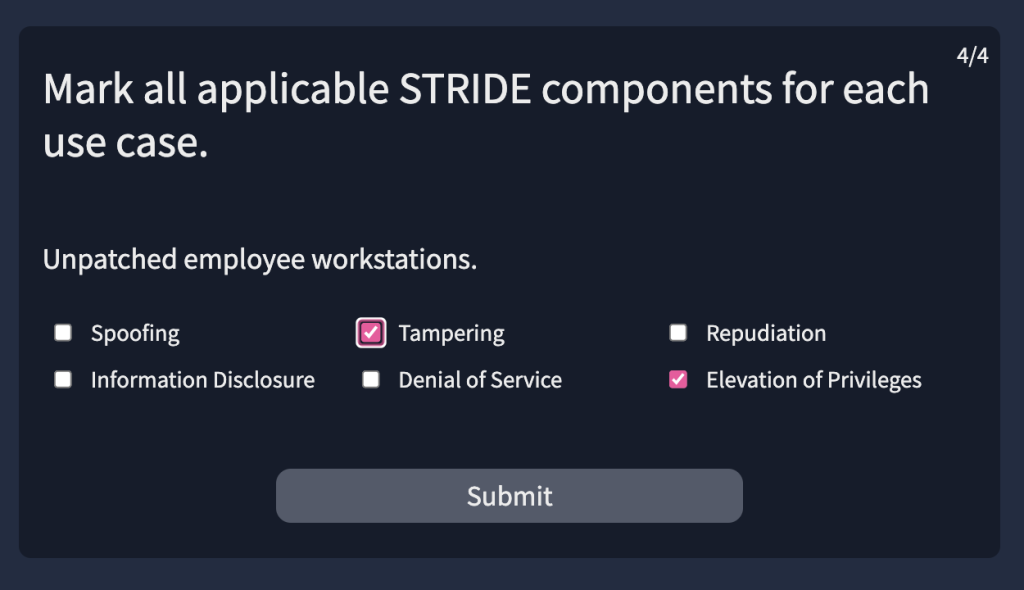
THM{*******************}
Task 7: PASTA Framework
7.1. In which step of the framework do you break down the system into its components?
Decompose the Application
7.2. During which step of the PASTA framework do you simulate potential attack scenarios?
Analyse the Attacks
7.3. In which step of the PASTA framework do you create an inventory of assets?
Define the Technical Scope
7.4. Provide the flag for the simulated threat modelling exercise.
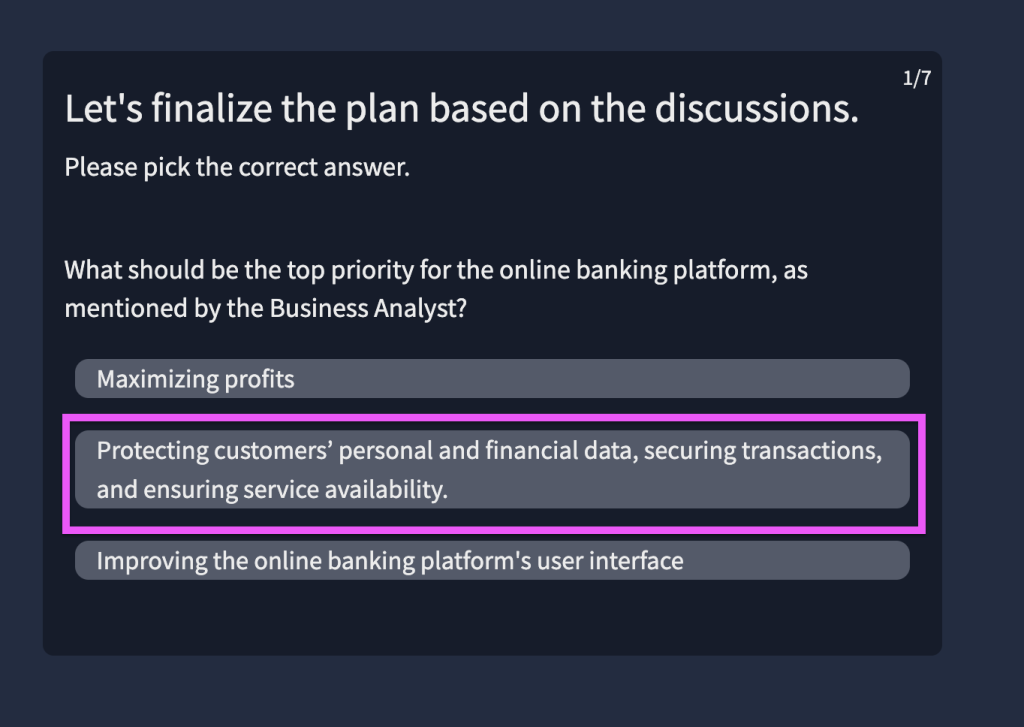
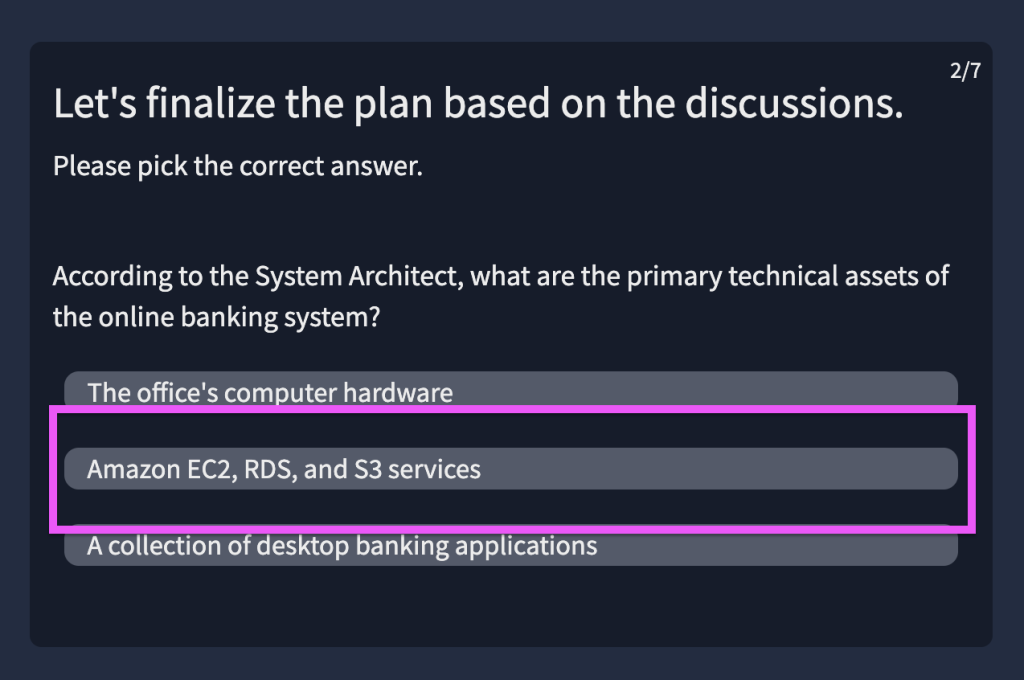
THM{****************************}

Hello, I am Aleyna Doğan. I work as a Sr. Cyber Threat Intelligence Analyst. In my blog, we write blog posts that my friends and I want to share. Have a good read.

