The room: “Learn about the essential tools for passive reconnaissance, such as whois, nslookup, and dig.”
https://tryhackme.com/room/passiverecon
Task 2 : Passive Versus Active Recon
2.1. You visit the Facebook page of the target company, hoping to get some of their employee names. What kind of reconnaissance activity is this? (A for active, P for passive)
P
2.2. You ping the IP address of the company webserver to check if ICMP traffic is blocked. What kind of reconnaissance activity is this? (A for active, P for passive)
A
2.3. You happen to meet the IT administrator of the target company at a party. You try to use social engineering to get more information about their systems and network infrastructure. What kind of reconnaissance activity is this? (A for active, P for passive)
A
Task 3 : Whois
3.1. When was TryHackMe.com registered?
whois TryHackMe.com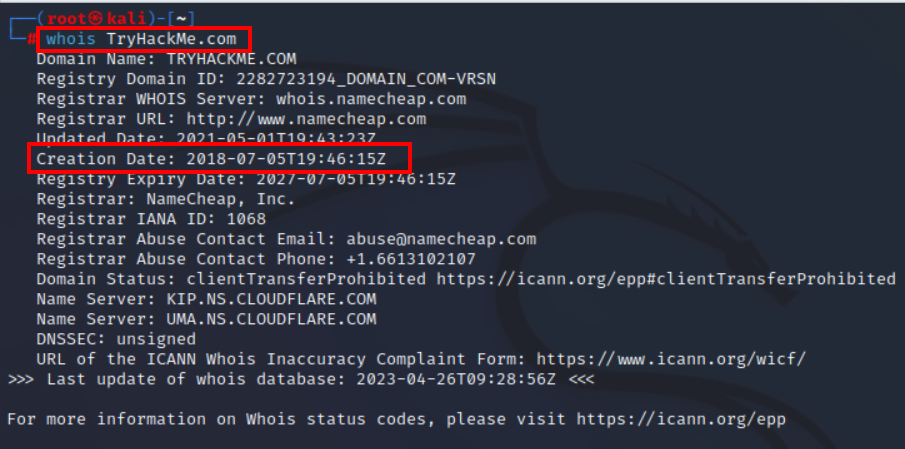
20180705
3.2. What is the registrar of TryHackMe.com?
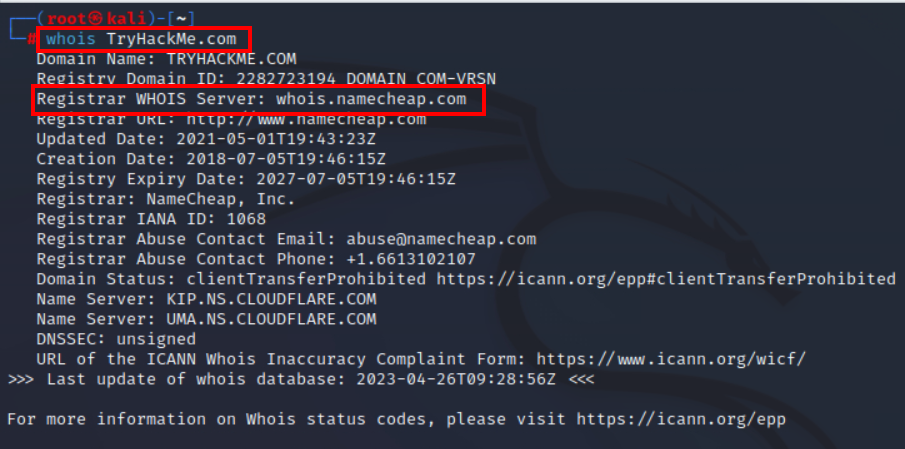
namecheap.com
3.3. Which company is TryHackMe.com using for name servers?
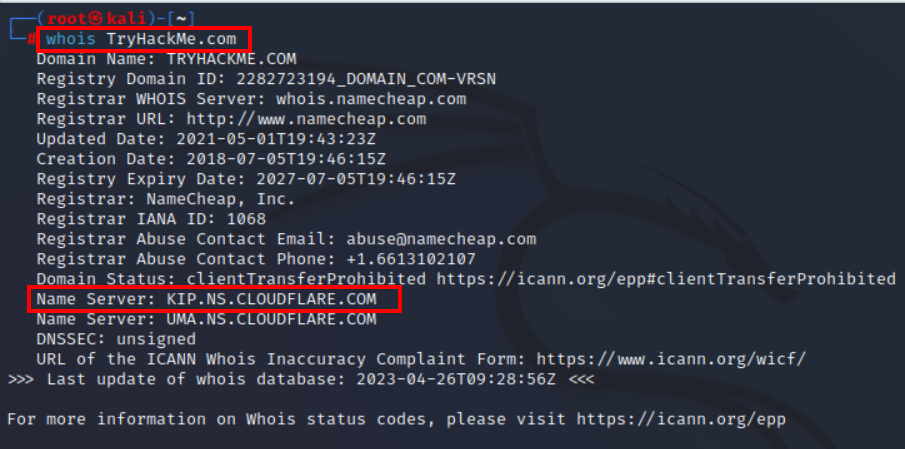
CLOUDFLARE.COM
Task 4 : nslookup and dig
4.1. Check the TXT records of thmlabs.com. What is the flag there?
nslookup -type=TXT thmlabs.com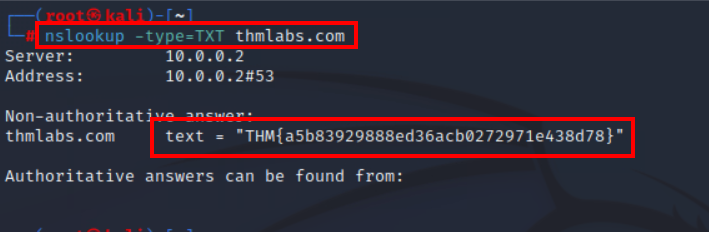
THM{a5b83929888ed36acb0272971e438d78}”
Task 5 : DNSDumpster
5.1. Lookup tryhackme.com on DNSDumpster. What is one interesting subdomain that you would discover in addition to www and blog?
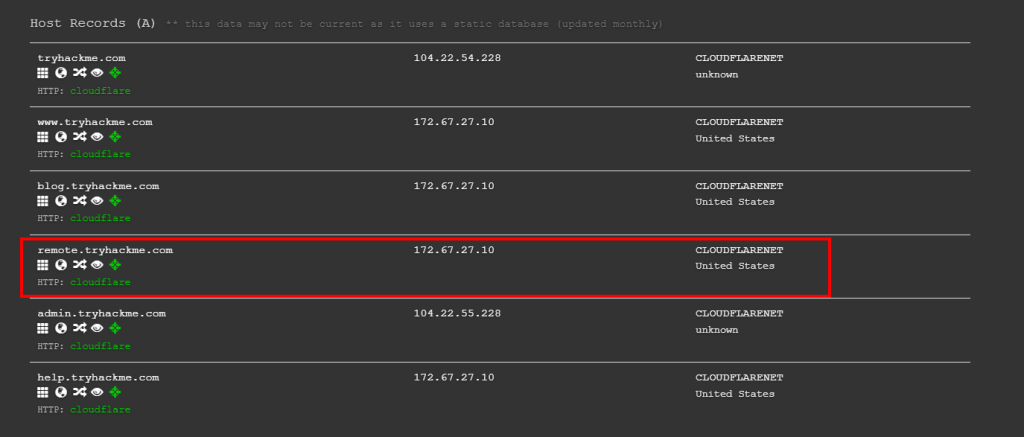
remote
Task 6 : Shodan.io
6.1. According to Shodan.io, what is the 2nd country in the world in terms of the number of publicly accessible Apache servers?
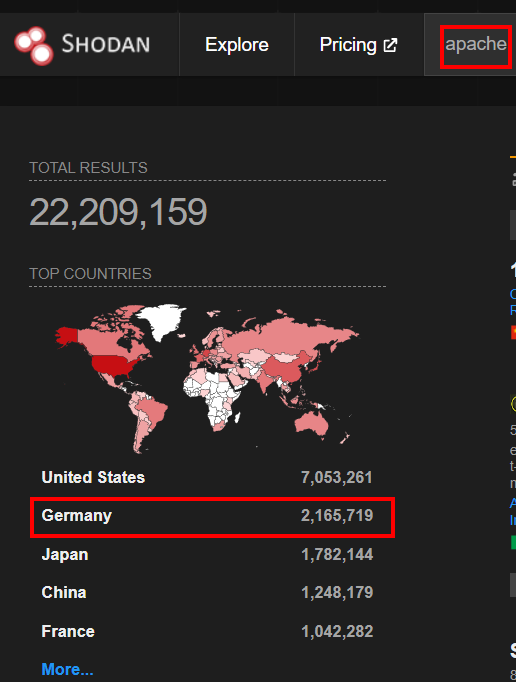
germany
6.2. Based on Shodan.io, what is the 3rd most common port used for Apache?
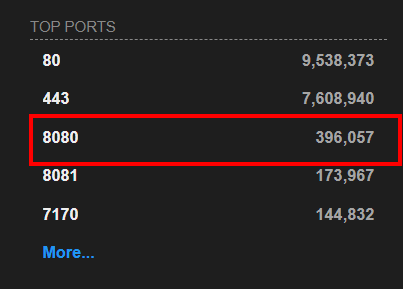
8080
6.3. Based on Shodan.io, what is the 3rd most common port used for nginx?
8888
a

