The Room: “Learn how to use NetworkMiner to analyse recorded traffic files and practice network forensics activities.”
https://tryhackme.com/room/networkminer
Task 4: Tool Overview 1
4.1. What is the total number of frames?
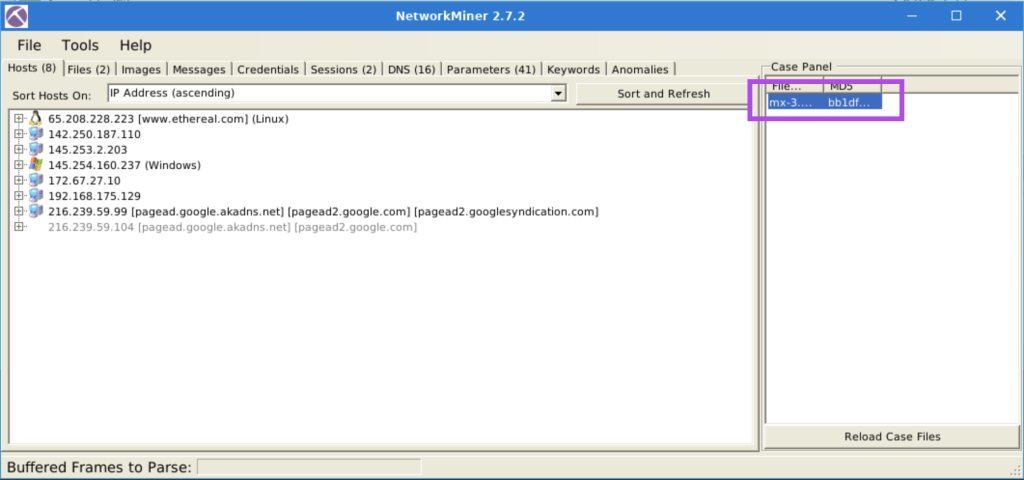
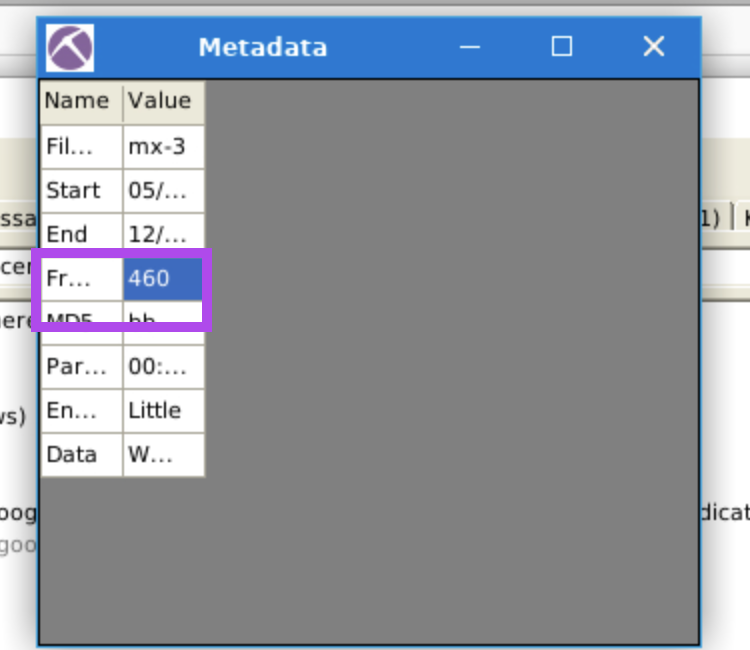
460
4.2. How many IP addresses use the same MAC address with host 145.253.2.203?
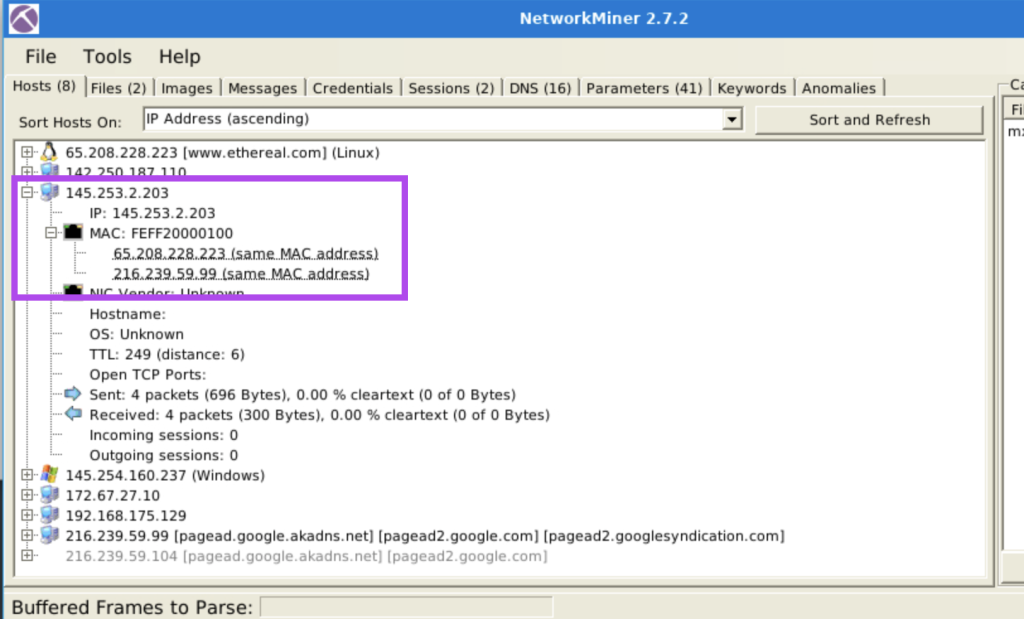
2
4.3. How many packets were sent from host 65.208.228.223?
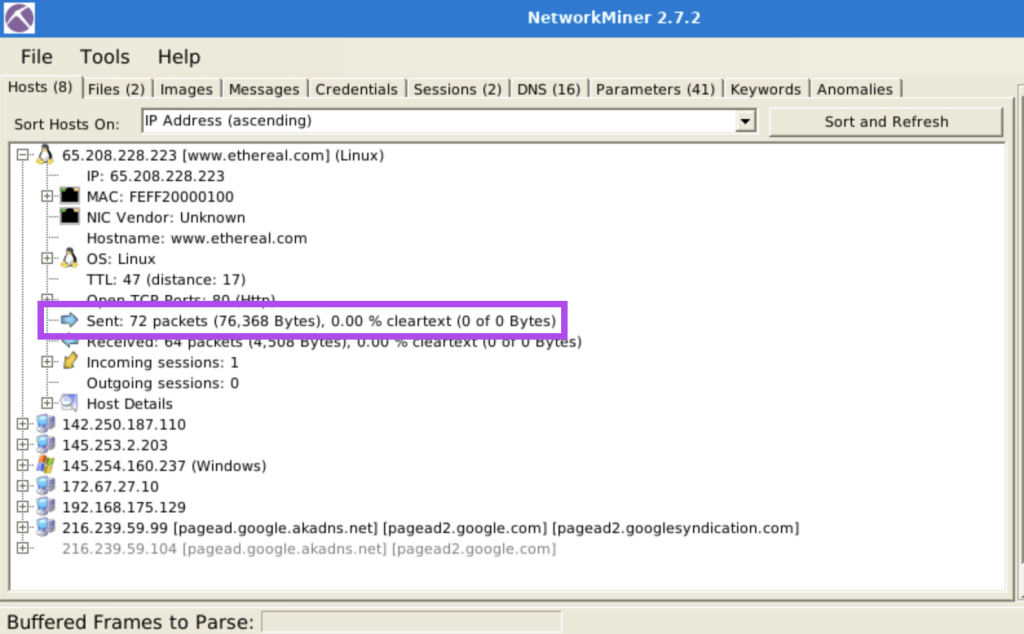
72
4.4. What is the name of the webserver banner under host 65.208.228.223?
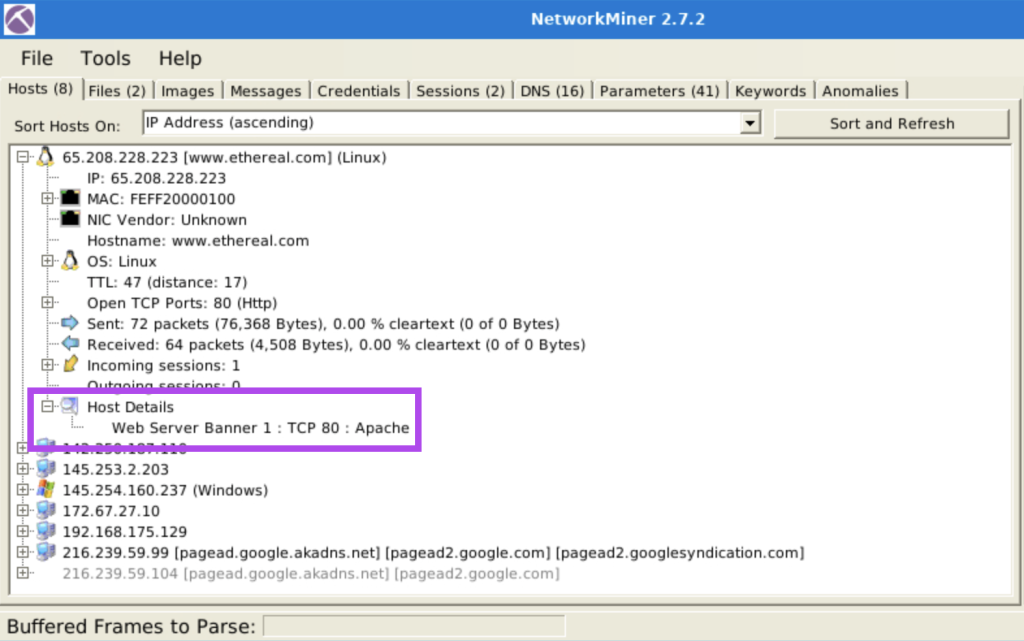
Apache
4.5. What is the extracted username?
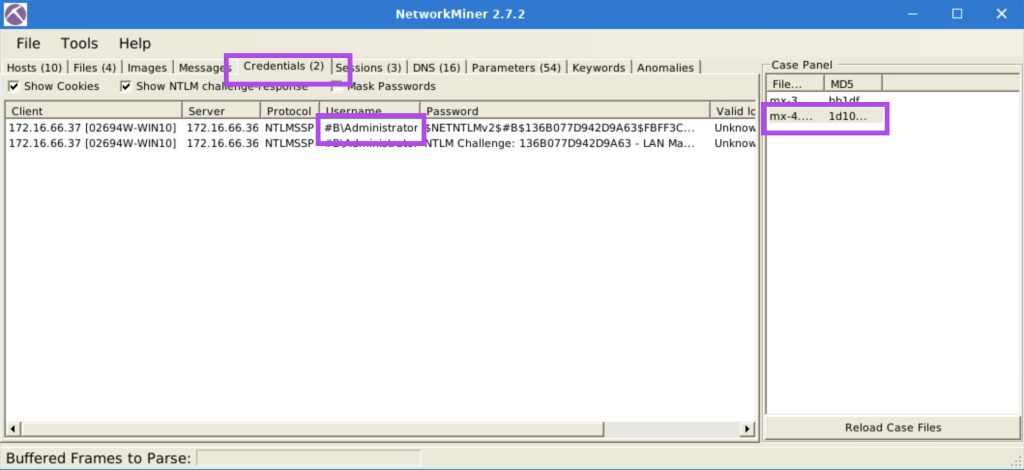
B\Administrator
4.6. What is the extracted password?
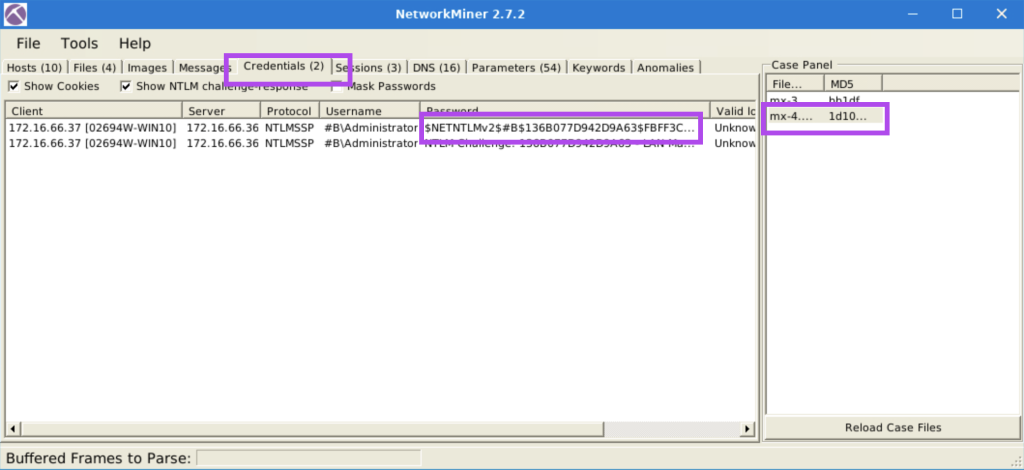
$NETNTLMv2$#B$136B077D942D9A63$FBFF3C253926907AAAAD670A9037F2A5$01010000000000000094D71AE38CD60170A8D571127AE49E00000000020004003300420001001E003000310035003600360053002D00570049004E00310036002D004900520004001E0074006800720065006500620065006500730063006F002E0063006F006D0003003E003000310035003600360073002D00770069006E00310036002D00690072002E0074006800720065006500620065006500730063006F002E0063006F006D0005001E0074006800720065006500620065006500730063006F002E0063006F006D00070008000094D71AE38CD601060004000200000008003000300000000000000000000000003000009050B30CECBEBD73F501D6A2B88286851A6E84DDFAE1211D512A6A5A72594D340A001000000000000000000000000000000000000900220063006900660073002F003100370032002E00310036002E00360036002E0033003600000000000000000000000000
Task 5: Tool Overview 2
5.1. What is the name of the Linux distro mentioned in the file associated with frame 63075?
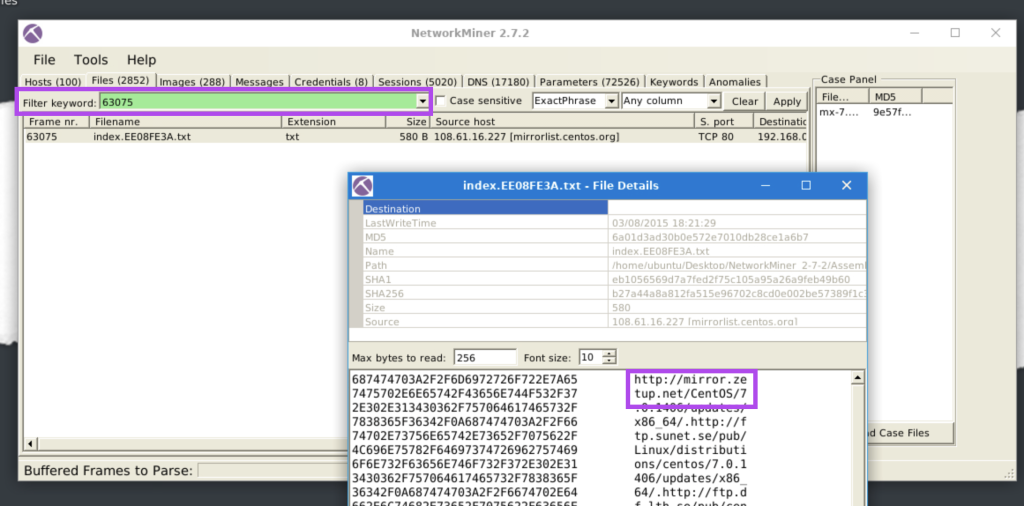
Centos
5.2. What is the header of the page associated with frame 75942?
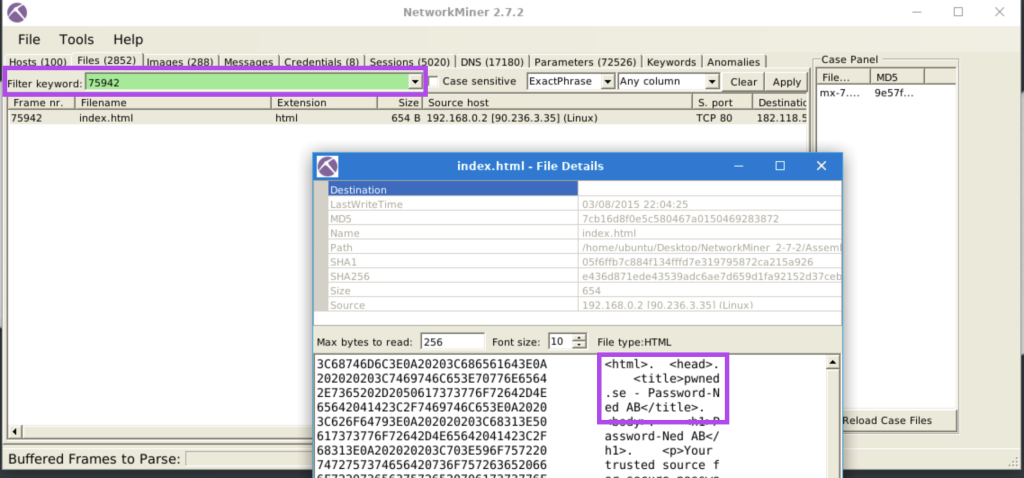
Password-Ned AB
5.3. What is the source address of the image “ads.bmp.2E5F0FD9.bmp”?
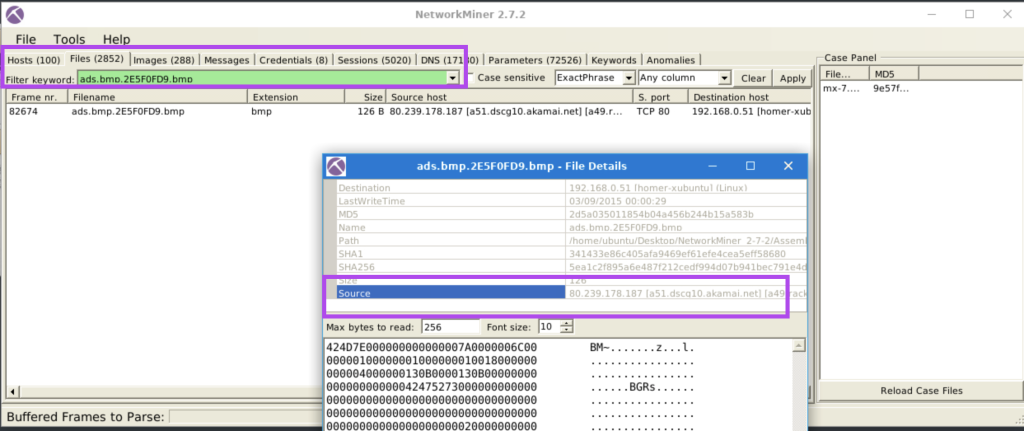
80.239.178.187
5.4. What is the frame number of the possible TLS anomaly?
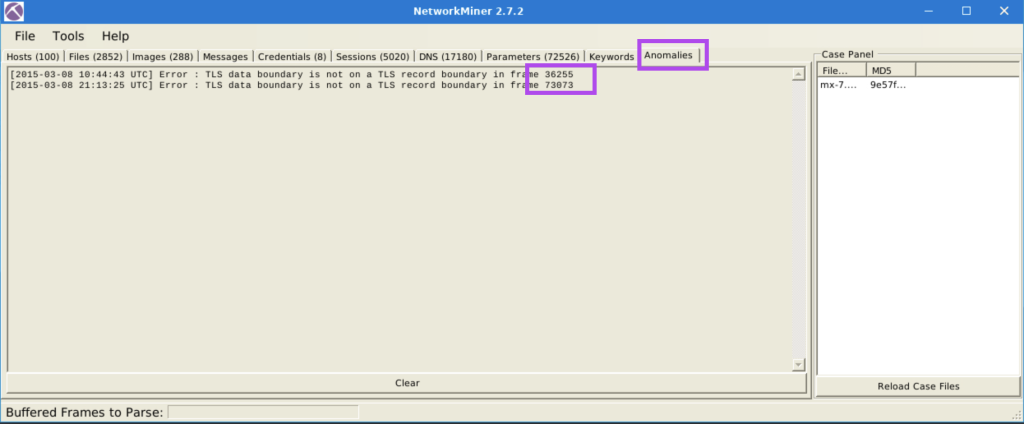
36255
5.5. Look at the messages. Which platform sent a password reset email?
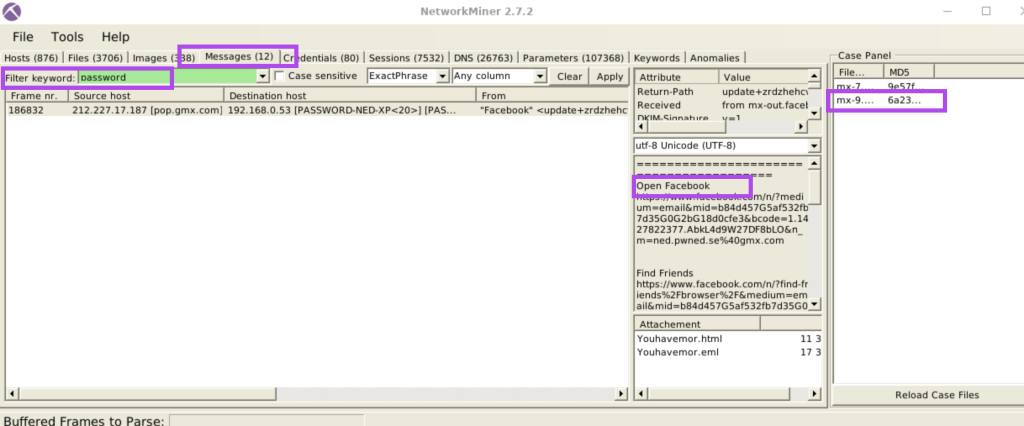
5.6. What is the email address of Branson Matheson?
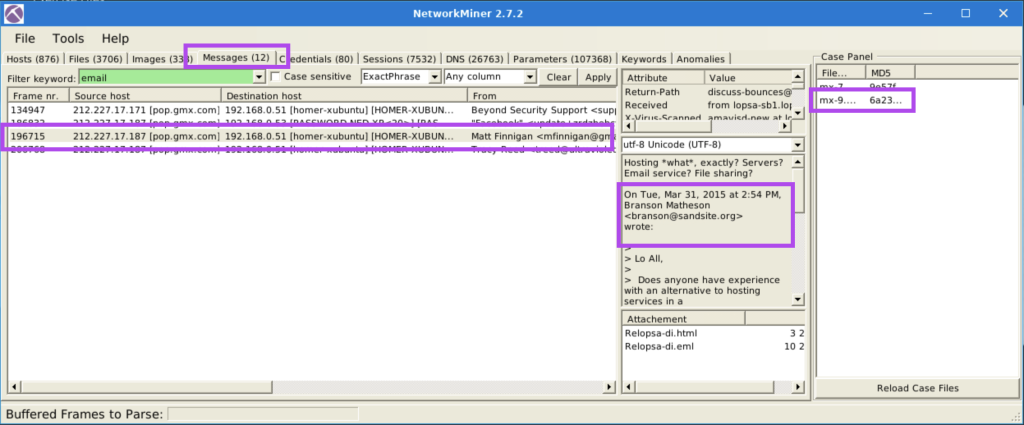
branson@sandsite.org
Task 6: Version Differences
6.1. Which version can detect duplicate MAC addresses?
2.7
6.2. Which version can handle frames?
1.6
6.3. Which version can provide more details on packet details?
1.6
Task 7: Exercises
7.1. What is the OS name of the host 131.151.37.122?
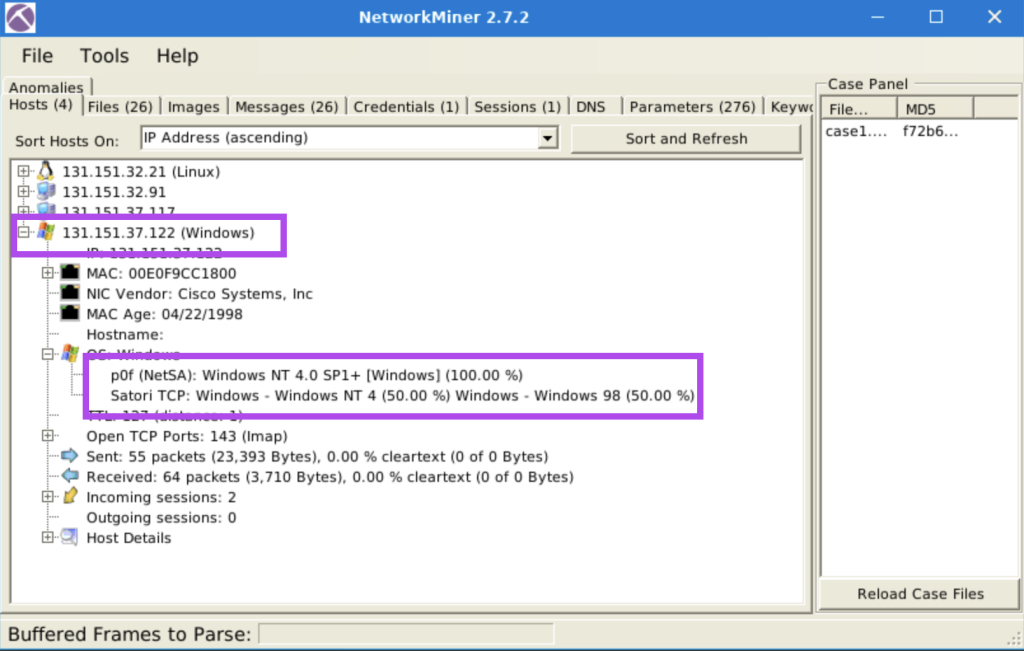
Windows – Windows NT 4
7.2. Investigate the hosts 131.151.37.122 and 131.151.32.91.
How many data bytes were received from host 131.151.32.91 to host 131.151.37.122 through port 1065?
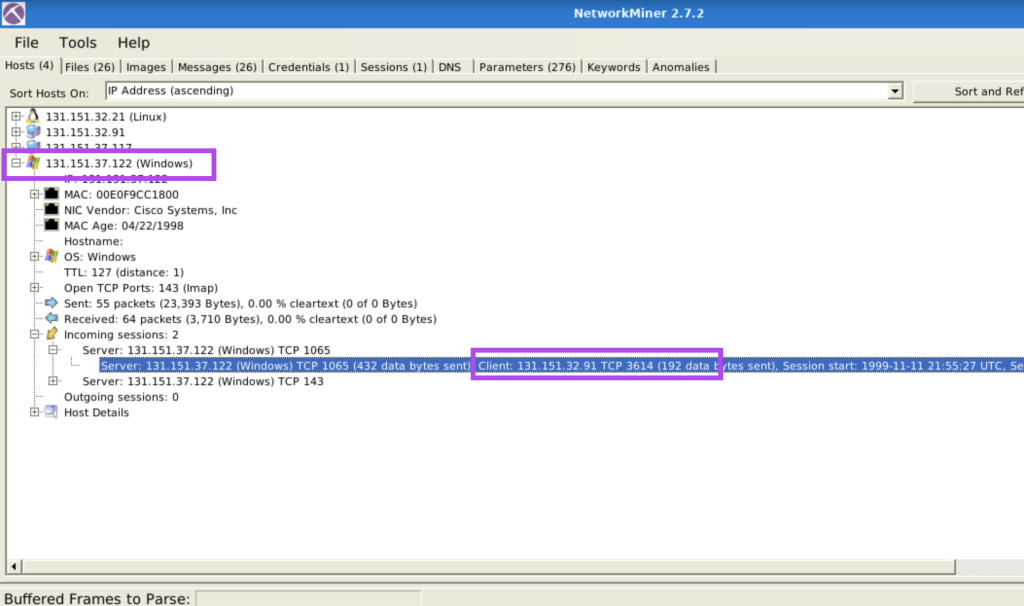
192
7.3. Investigate the hosts 131.151.37.122 and 131.151.32.21.
How many data bytes were received from host 131.151.37.122 to host 131.151.32.21 through port 143?
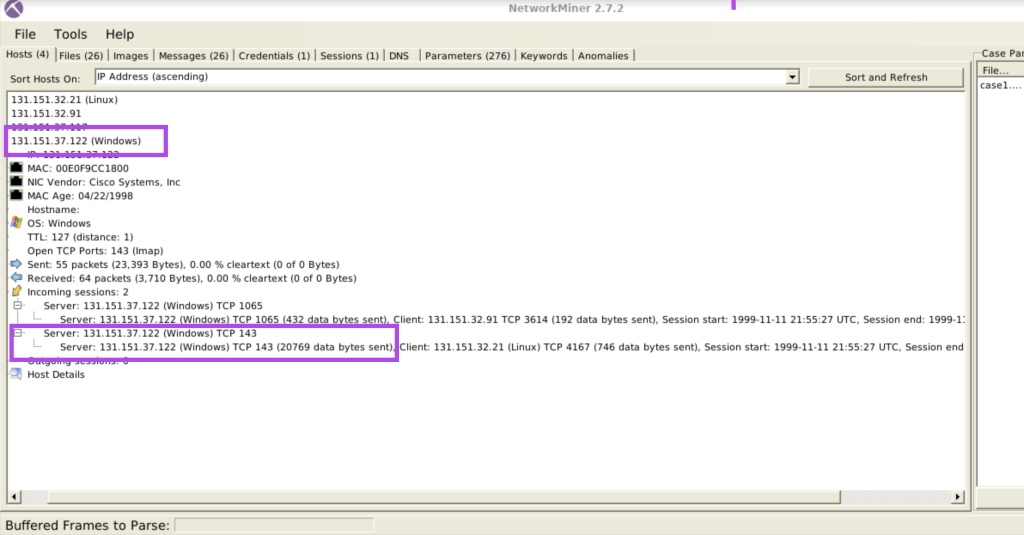
20769
7.4. What is the sequence number of frame 9?
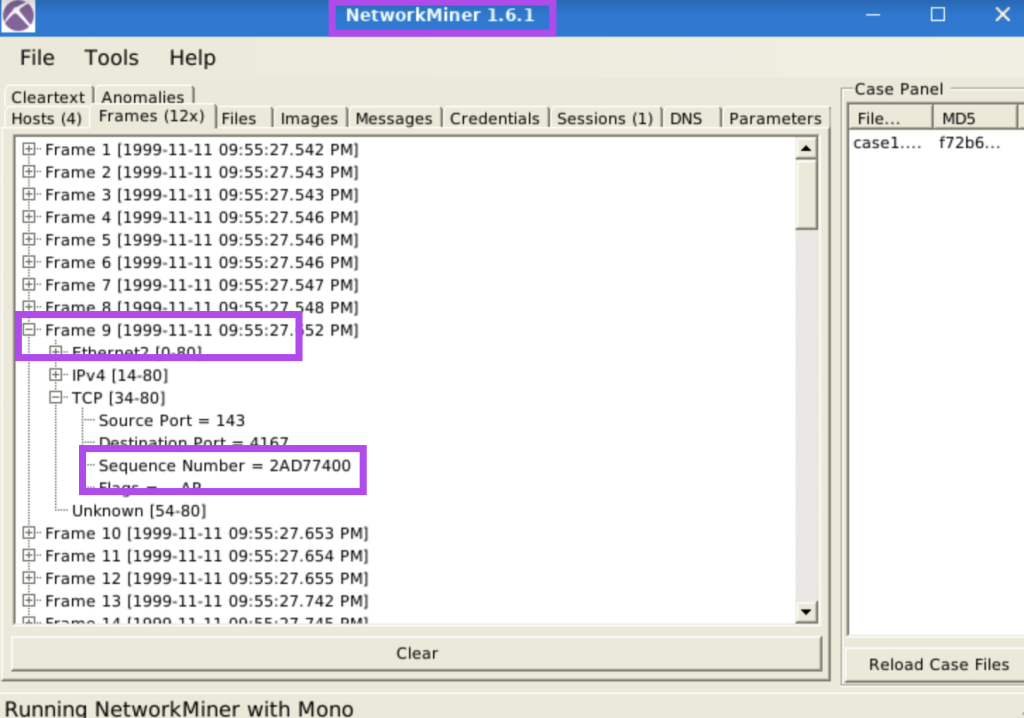
2AD77400
7.5. What is the number of the detected “content types”?
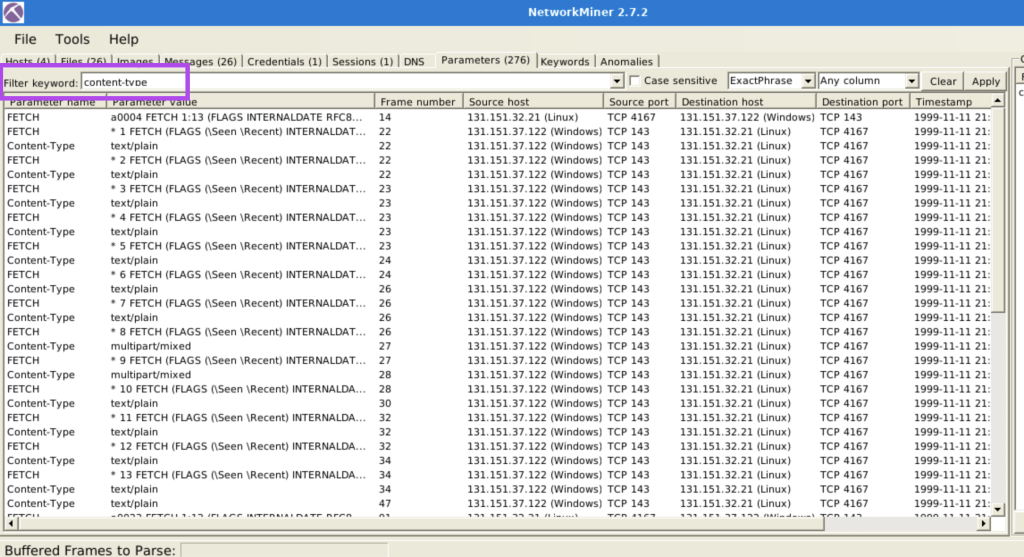
2
7.6. What is the USB product’s brand name?
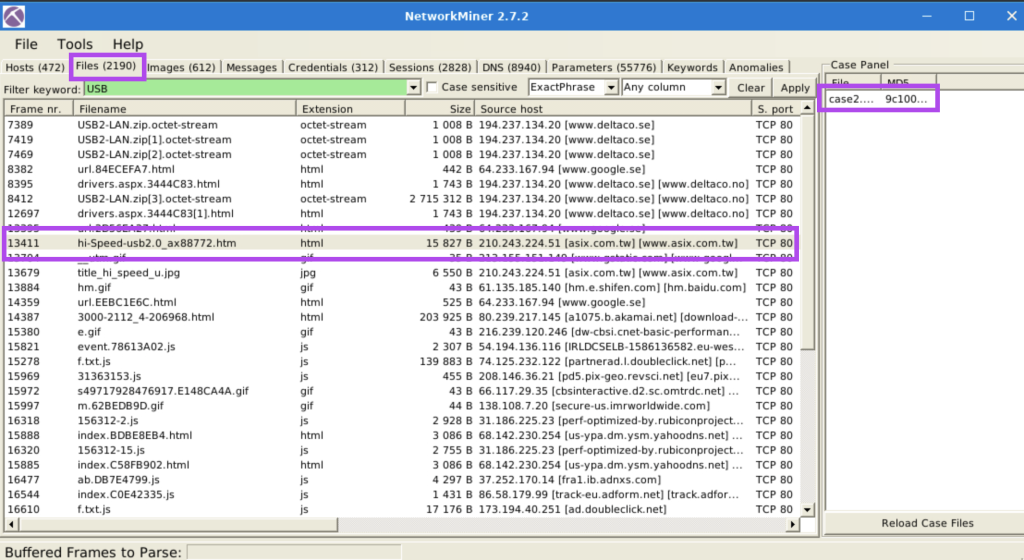
asix
7.7. What is the name of the phone model?
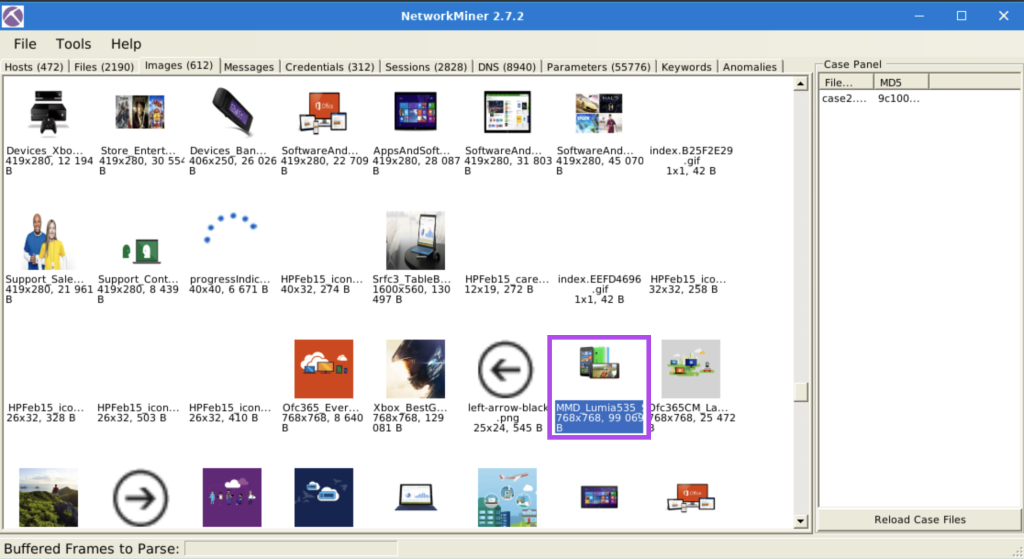
Lumia 535
7.8. What is the source IP of the fish image?
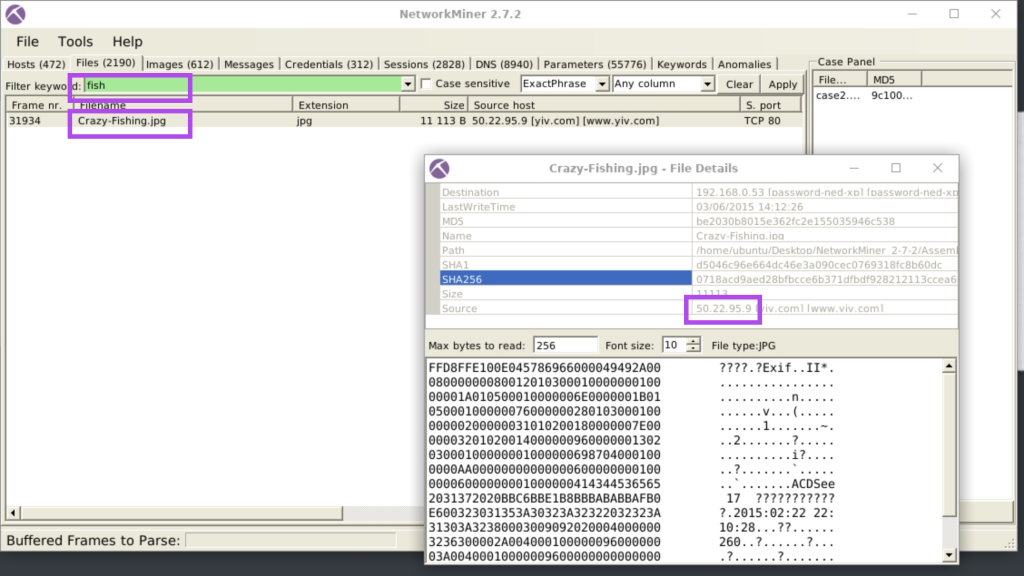
50.22.95.9
7.9. What is the password of the “homer.pwned.se@gmx.com”?
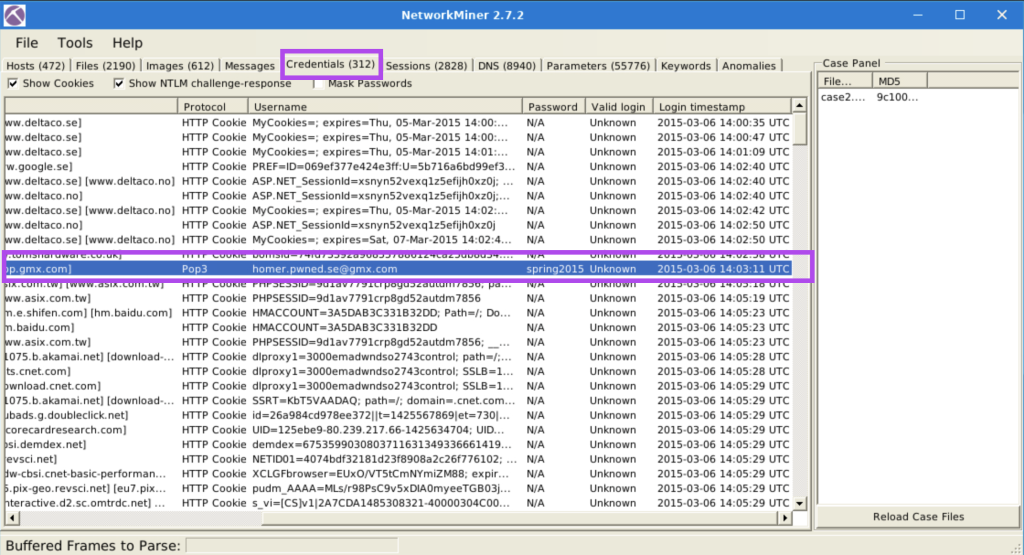
spring2015
7.10. What is the DNS Query of frame 62001?
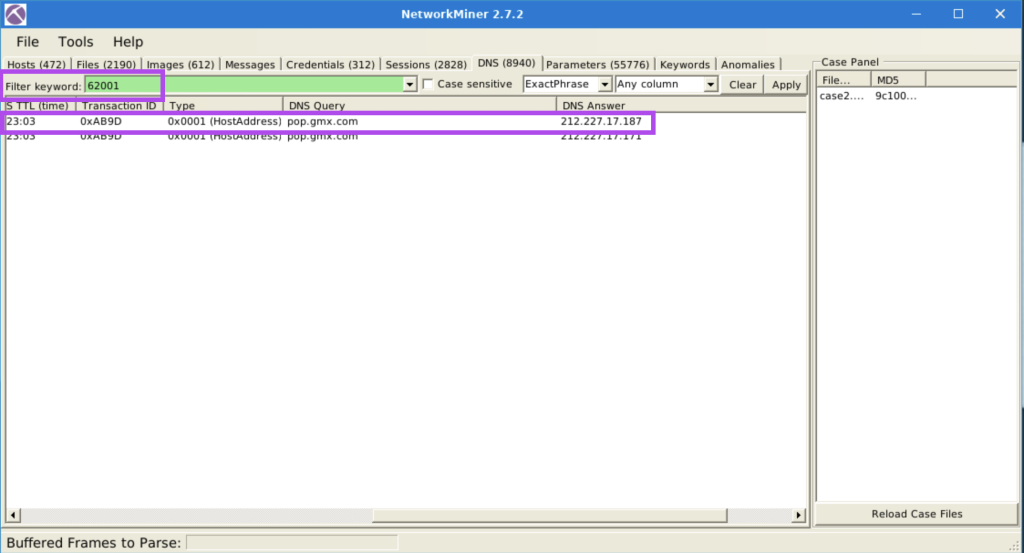
pop.gmx.com


[…] Click for different Tryhackme Writeups and Cyber Security Articles admin […]