The Room: “Learn in-depth how nmap TCP connect scan, TCP SYN port scan, and UDP port scan work.”
https://tryhackme.com/room/nmap02
Task 2: TCP and UDP Ports
2.1. Which service uses UDP port 53 by default?
DNS
2.2. Which service uses TCP port 22 by default?
SSH
2.3. How many port states does Nmap consider?
6
2.4. Which port state is the most interesting to discover as a pentester?
open
Task 3: TCP Flags
3.1. What 3 letters represent the Reset flag?
RST
3.2. Which flag needs to be set when you initiate a TCP connection (first packet of TCP 3-way handshake)?
SYN
Task 4: TCP Connect Scan
4.1. Launch the VM. Open the AttackBox and execute nmap -sT MACHINE_IP via the terminal. A new service has been installed on this VM since our last scan. Which port number was closed in the scan above but is now open on this target VM?
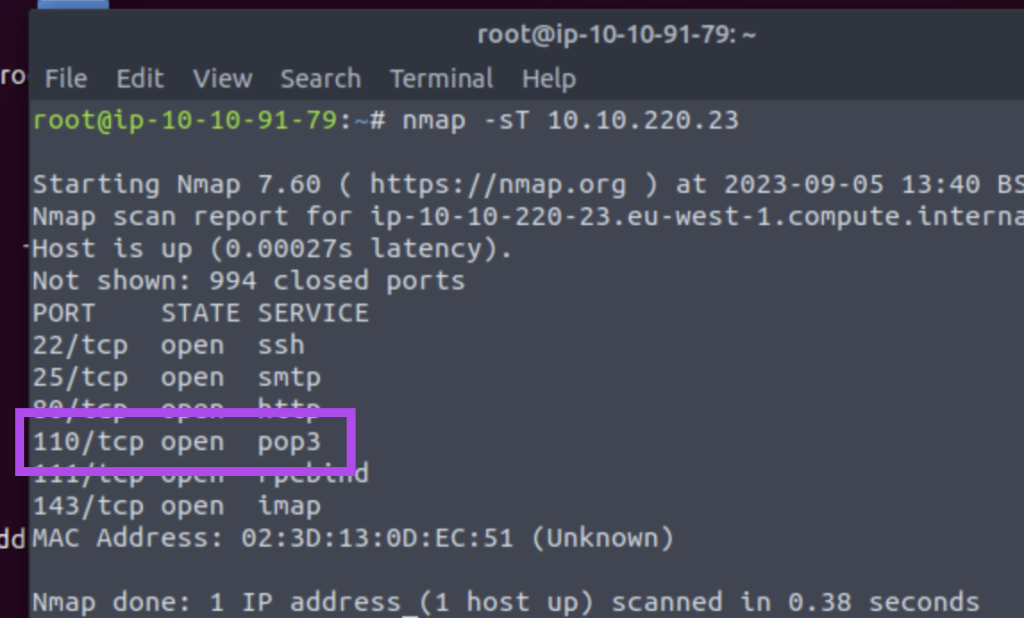
110
4.2. What is Nmap’s guess about the newly installed service?
pop3
Task 5: TCP SYN Scan
pop3
5.1. Launch the VM. Some new server software has been installed since the last time we scanned it. On the AttackBox, use the terminal to execute nmap -sS {TARGET_IP}. What is the new open port?
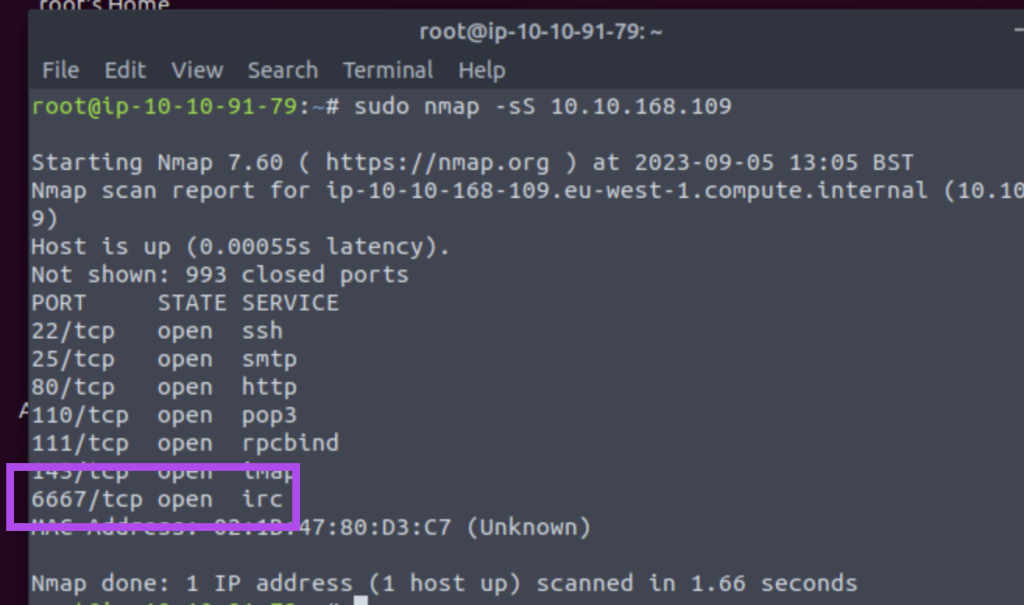
6667
5.2. What is Nmap’s guess of the service name?
irc
Task 6: UDP Scan
6.1. Launch the VM. On the AttackBox, use the terminal to execute nmap -sU -F -v {TARGET_IP}. A new service has been installed since the last scan. What is the UDP port that is now open?
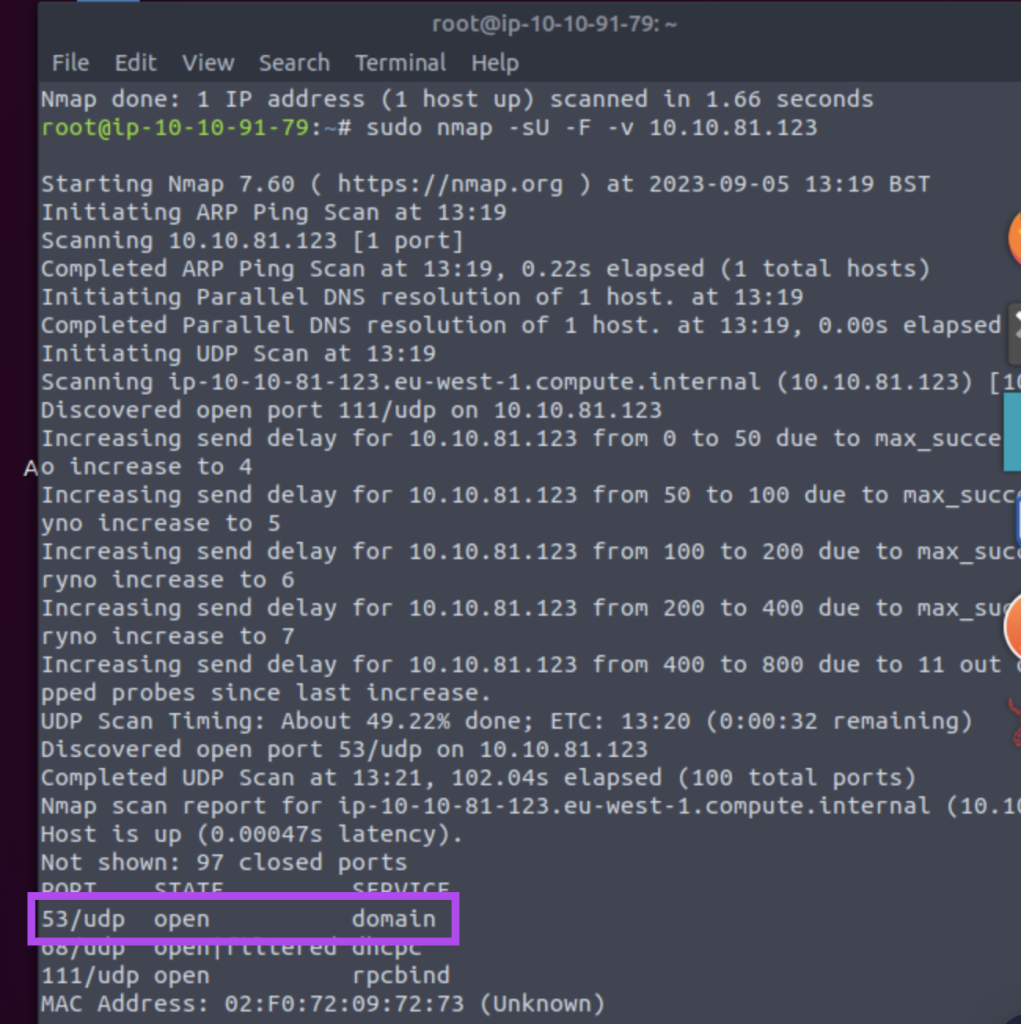
53
6.2. What is the service name according to Nmap?
domain
Task 7: Fine-Tuning Scope and Performance
7.1. What is the option to scan all the TCP ports between 5000 and 5500?
-p5000-5500
7.2. How can you ensure that Nmap will run at least 64 probes in parallel?
–min-parallelism=64
7.3. What option would you add to make Nmap very slow and paranoid?
-T0


[…] Click for different Tryhackme Writeups and Cyber Security Articles admin […]