The room: “Learn how to utilise Threat Intelligence to improve the Security Operations pipeline.”
https://tryhackme.com/room/threatintelligenceforsoc
2.1. How many unique IP addresses were provided in the IOC list?
We need to remove duplicates from the IP list given to us. We can use many tools such as Excel, Dcode, etc. to remove duplicates. Removing duplicate IP addresses leaves 11 unique IP addresses.
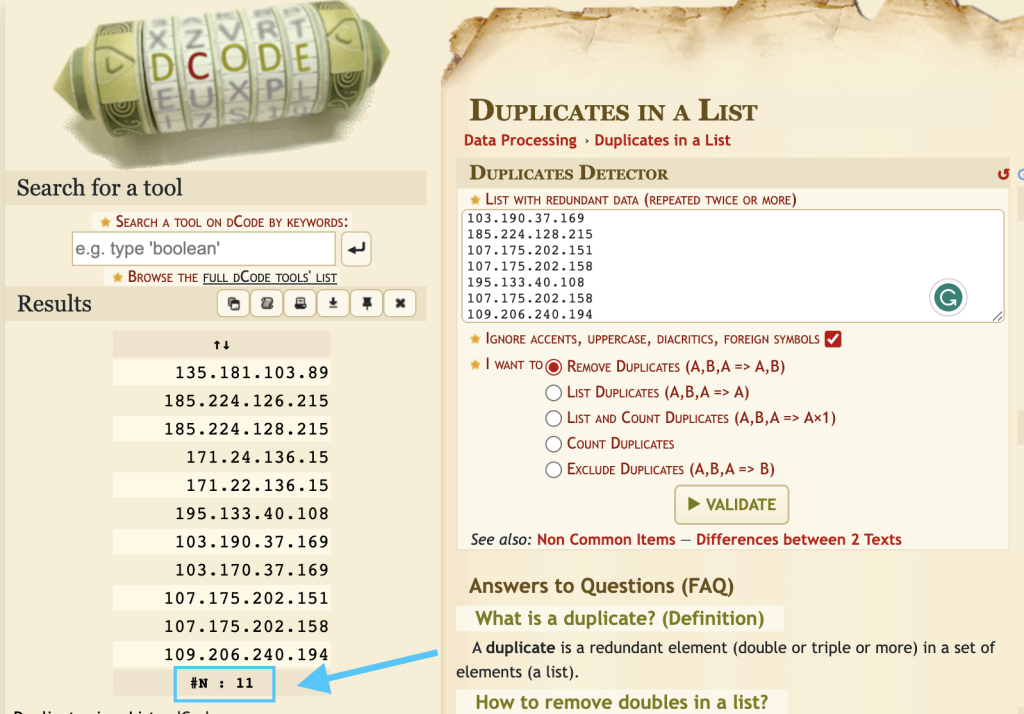
11
2.2. Based on the set of IOCs, how many IOC hits were discovered in the logs?
We write an elastic search query with the given IOC list. We can use uncoder.io, which Lab also recommends, but the query rights are limited and I prefer to write my own instead. After doing our query, we detected 48 IOCs in the logs as a result
destination.ip:(“135.181.103.89” OR “185.224.126.215” OR “185.224.128.215” OR “171.24.136.15” OR “171.22.136.15” OR “195.133.40.108” OR “103.190.37.169” OR “103.170.37.169” OR “103.190.37.169” OR “185.224.128.215” OR “107.175.202.151” OR “107.175.202.158” OR “195.133.40.108” OR “107.175.202.158” OR “109.206.240.194”)
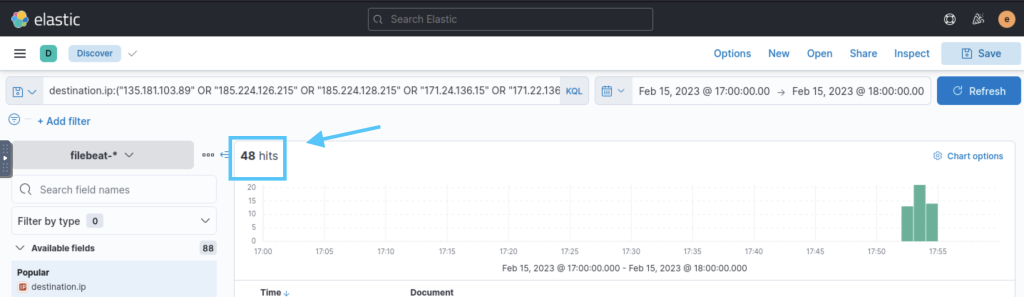
48
2.3. Out of the total number of IOCs, how many unique IP addresses were discovered in the logs?
Since we want to get details about the IPs we enter, we examine the destination.ip visualization.
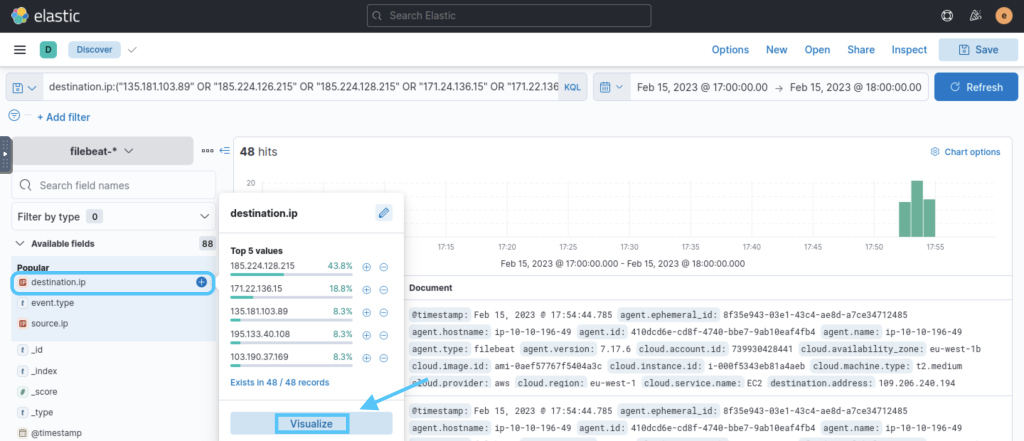
As can be seen from the destination.ip visualization, there are 7 IPs for 48 IOCs.
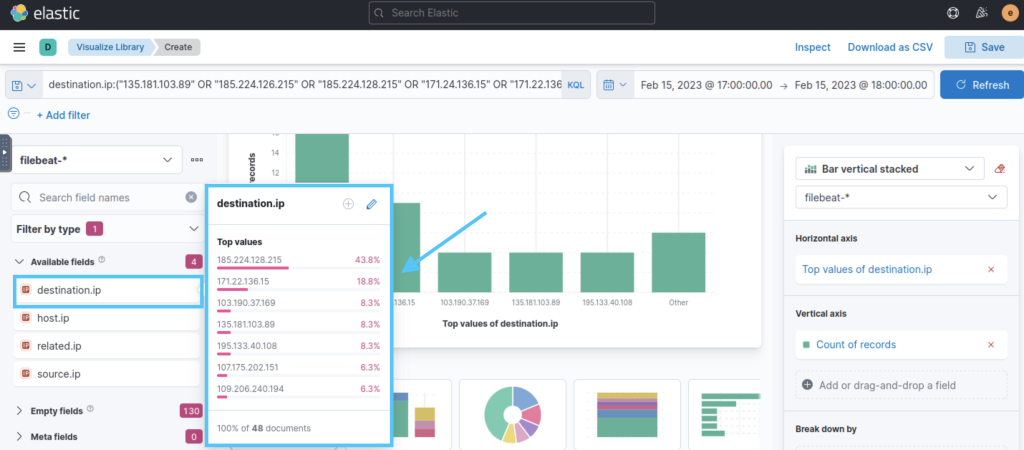
7
2.4. How many connections were made to 185[.]224[.]128[.]215?
Again, on our visualization page, we look at how many detections were made in the specified IP range.
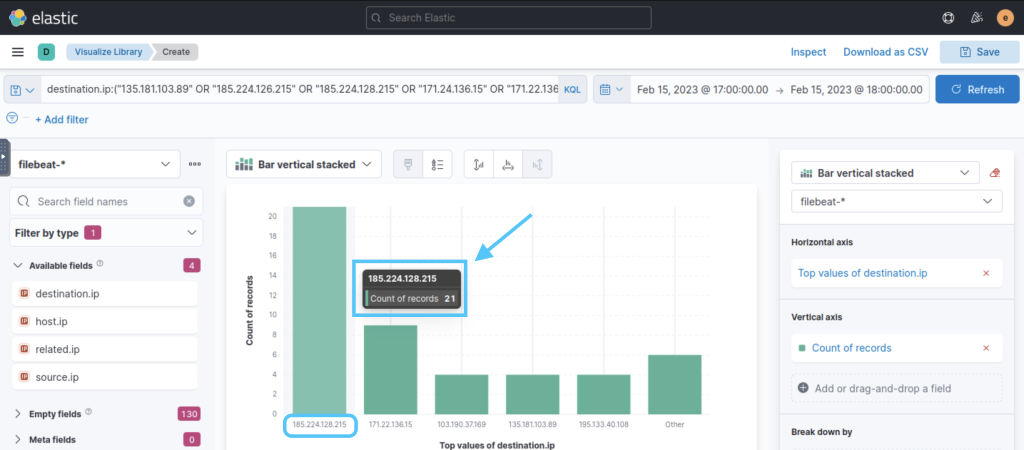
21
2.5. What is the IP address of the compromised host?
When we examine the logs for the hostname, we can find the address in the “agent.hostname” section.
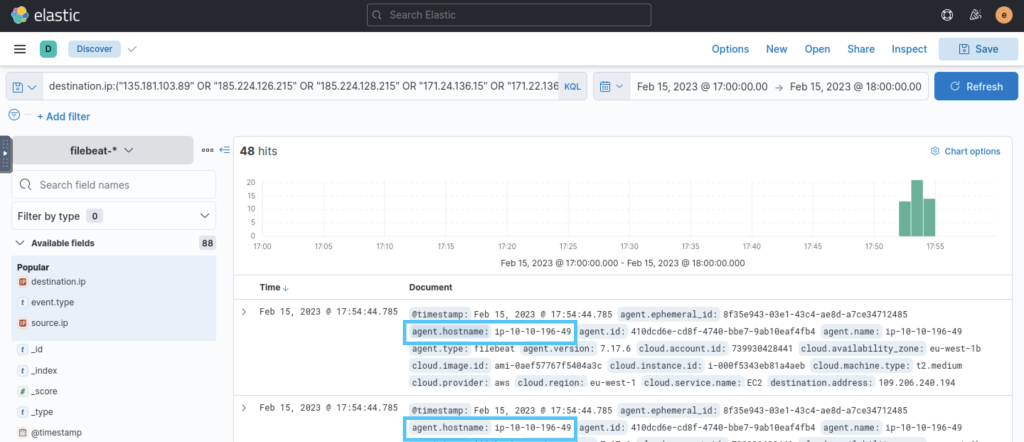
10.10.196.49
2.6. What is the destination port of connections made to 107[.]175[.]202[.]151?
We can search for the destination port on the left side. When we look at the search, we see that the same port is used in 48 results.
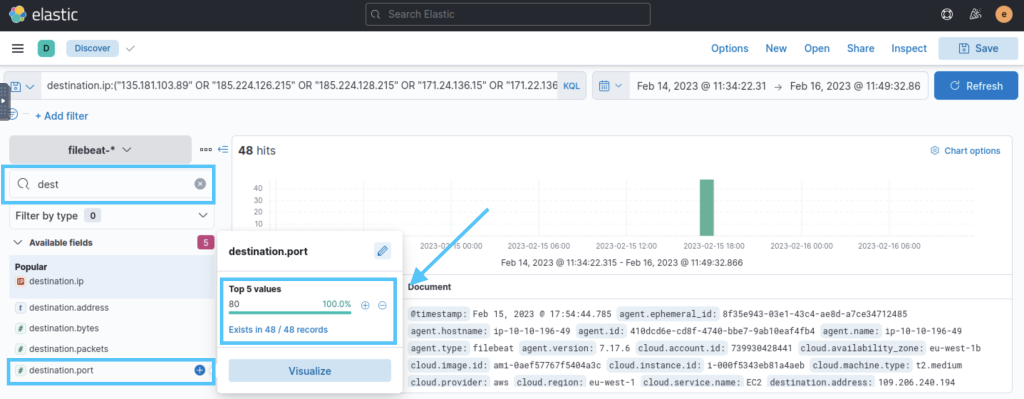
80
3.1. How many DNS queries to agrosaoxe[.]info have been created?
We use the dns.question.name:agrosaoxe.info query and get the result
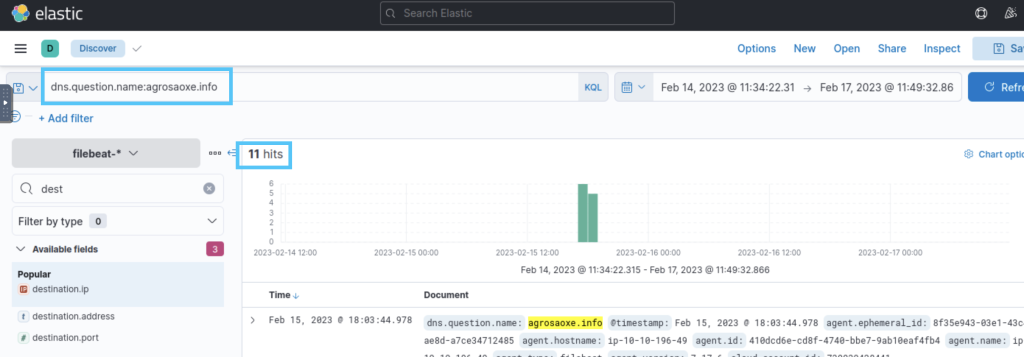
11
3.2. Before deploying the sinkhole configuration, what IPv4 addresses are resolved by agrosaoxe[.]info? (format: IPs in ascending order)
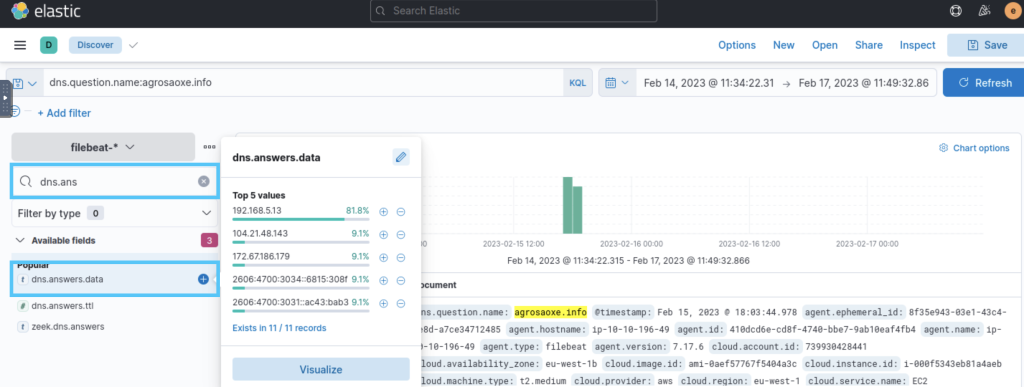
104.21.48.143,172.67.186.179
3.3. What is the IP address used for DNS Sinkhole?
dns.answers.data:”192.168.5.13″
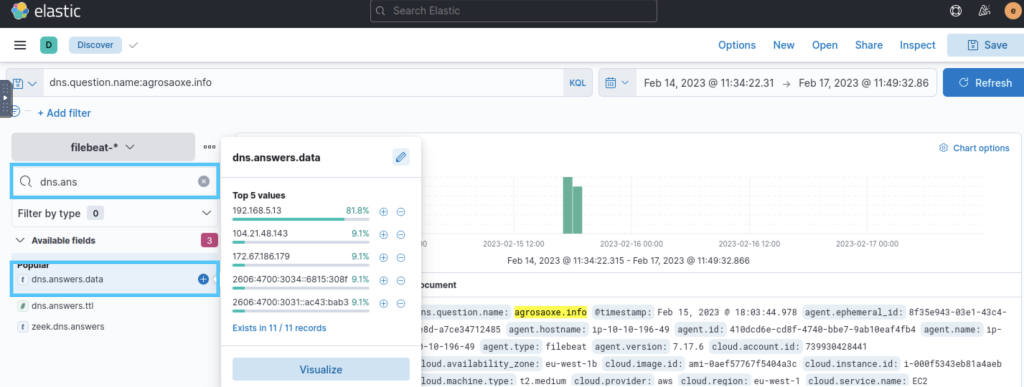
192.168.5.13
3.4. How many hits were caused by connections to sinkholed domains?
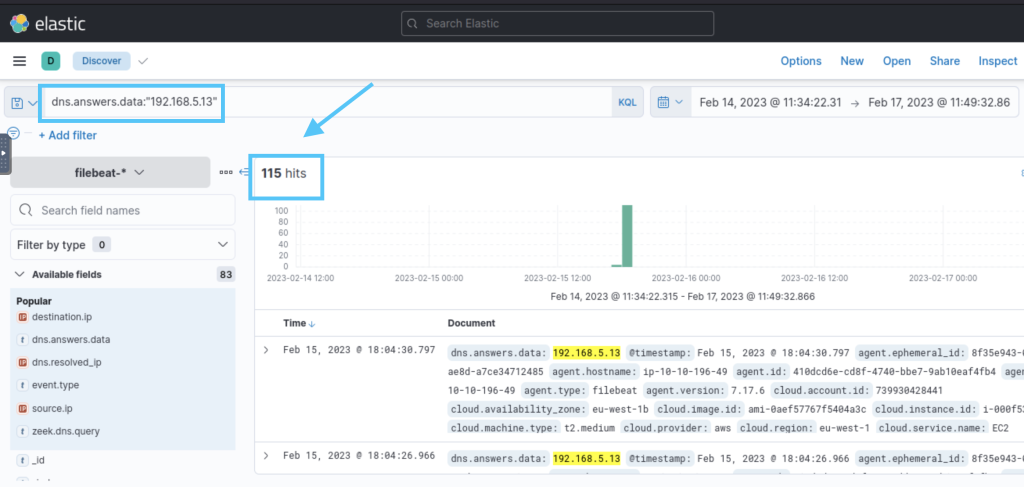
115
3.5. How many unique domains have been sinkholed?
The visualization shows that there are 12 unique domains.
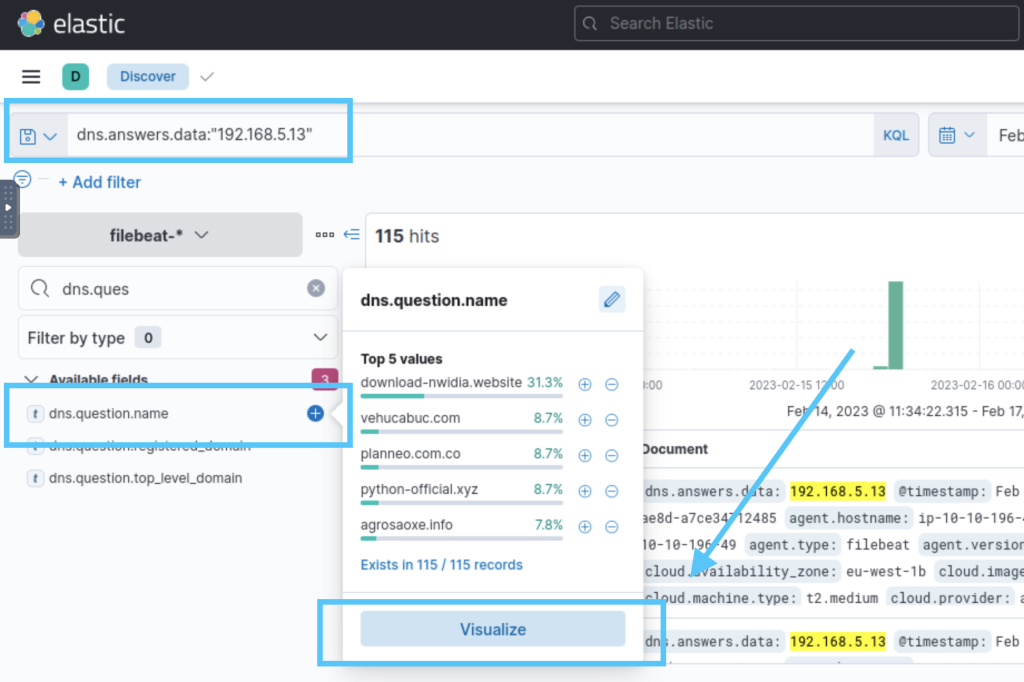
12
4.1. What is the value of the alert field in the converted ElastAlert rule?
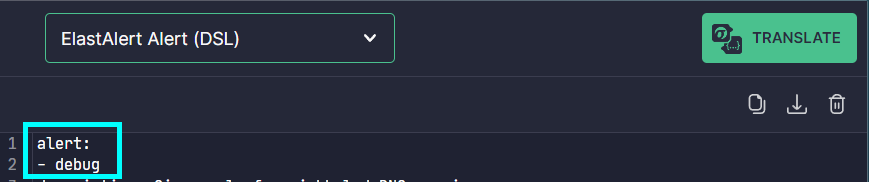
debug
4.2. How many alerts were generated by the rule?
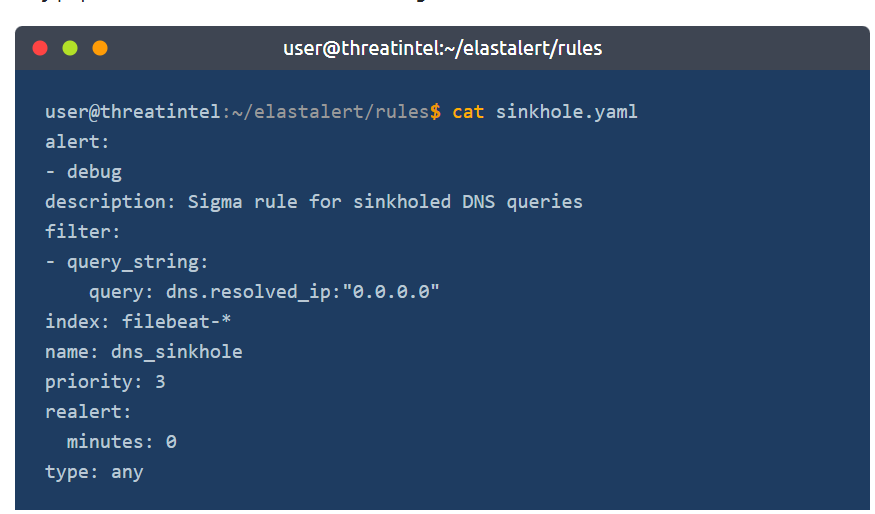
We change the contents of the sinkhole.yaml file in ~/elastalert/rules with nano.
user@threatintel:~/elastalert$ elastalert –start 2023-02-16T00:00:00 –verbose 2>&1 | tee outputt.txt command to run the programme
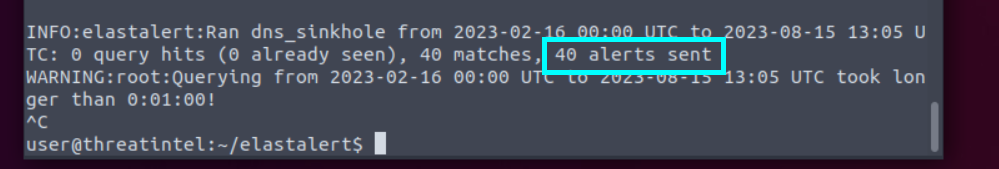
40
4.3. How many alerts were generated by the rule?
cat output.txt | grep “registered_domain” | sort –unique | wc -l
command to find the domains. The result is 6, but the answer is 7, unfortunately I could not understand the mistake I made.
7
4.4. What is the sinkholed domain that has .ru TLD?
cat resultt.txt | grep “registered_domain” | sort –unique
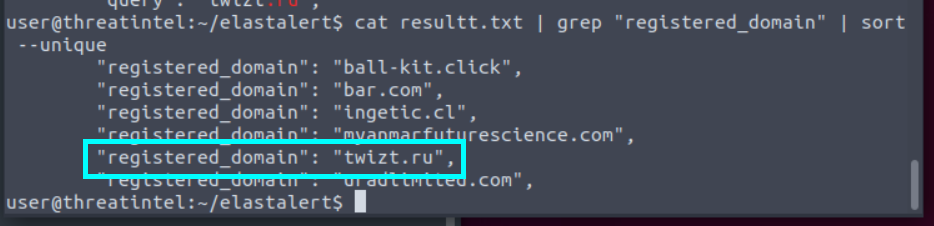
twizt.ru


[…] Click for different Tryhackme Writeups and Cyber Security Articles admin […]